Verizon’s DBIR Highlights Key Drivers of Security Risk

It’s that time of the year when Verizon updates us on the latest trends in the global threat landscape with its Data Breach Investigations Report (DBIR). The findings in this year’s report are based on data provided by more than 70 sources (including Qualys) about more than 41,000 security incidents, including more than 2,000 confirmed data breaches, across a variety of geographies (over 80 countries) and industries. A privileged observation point indeed.
While the very informative 78-page report touches on a wide range of areas, I’ll focus on three that are particularly relevant for Qualys customers:
- Who are hackers’ preferred targets, and why
- The importance of reducing both the time it takes to discover security problems, such as vulnerabilities or breaches, and the time it takes to fix them
- How lack of visibility, human error and careless misconfigurations heighten organizations’ security risks
Read on to learn more about the evolution (or is it “EVILution”) of the threat landscape in the past year, and find out about recommended actions.
Who are the victims?
Almost half of the breaches involved small business victims. This can have multiple explanations. Small businesses usually have weaker security due to fewer resources and less technical knowledge. They are also an attractive target because, as part of supply chains, they can be a conduit for hackers into the networks of larger companies.
From a vertical industry perspective, sectors including government, healthcare and finance were hit hard, which underlines attackers’ appetite for the sensitive, confidential data that companies in these industries hold, and that can be sold or leveraged for larger attacks.
Time to discovery, time to patch
A concerning finding is that more than half of the breaches took months to discover. This signals that IT and security teams still struggle to have full visibility over IT environments that are being digitally transformed and are thus becoming hybrid and more distributed. You can’t monitor, assess, defend or protect what you do not see.
Here’s an interesting set of graphs from the report, showing the breach timelines:
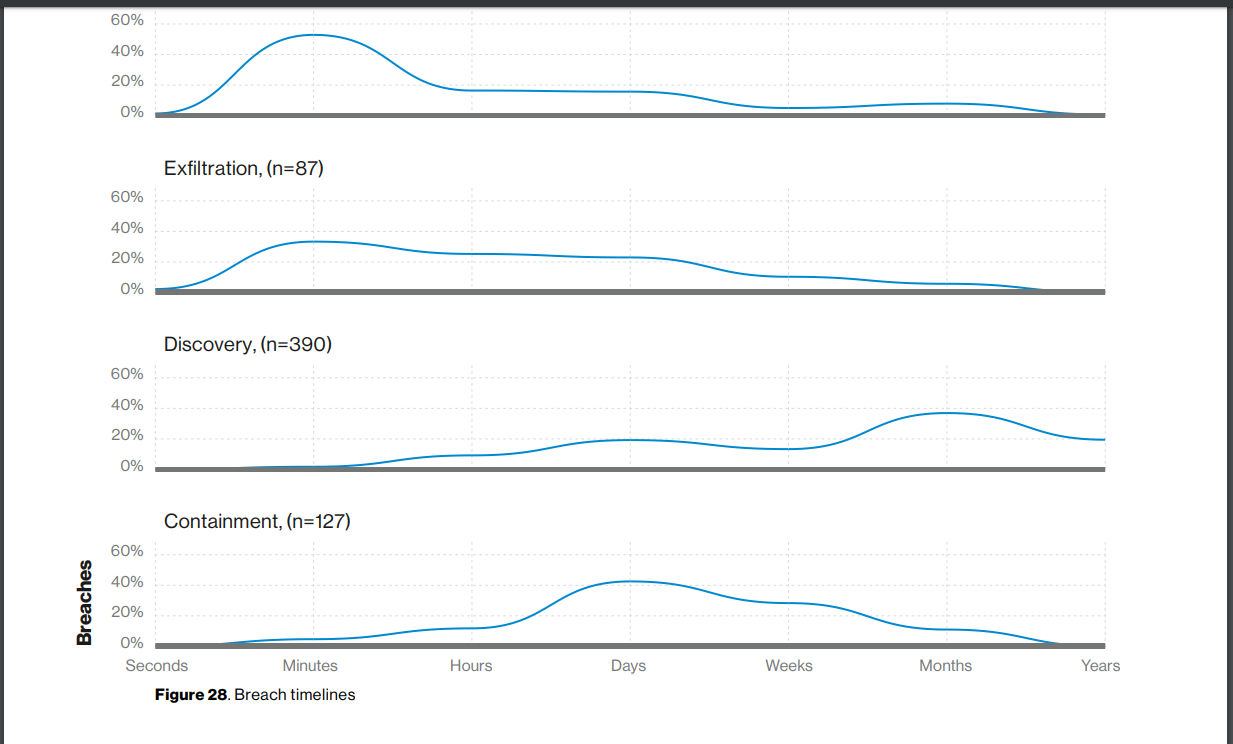
The graphs above show that while compromise and exfiltration happen in a matter of minutes to days, discovery sometimes takes days in the best of cases, but often it takes weeks if not months or years. And after discovery is done, you need to spend time, effort and resources on containment.
With regards to vulnerabilities, 50% are fixed within 90 days after discovery, and 25% are fixed within 30 days. While this may seem efficient to many, I believe that it’s possible to do much better, especially if the remediation program is tightly integrated with the detection one.
The days when siloed, point solutions are used to address unique IT, security and compliance problems are over. Having heterogeneous products that don’t interoperate leads to delays and gaps, especially for breach prevention, where you need an integrated program that includes asset inventory, vulnerability management, threat prioritization and patch management.
Preferred tactics
Some form of hacking was used in 52% of the breaches, while malware infections accounted for 28%, and misuse by authorized users for 15%. Aside from a lack of visibility, these numbers highlight the need for strengthening compliance and reducing misconfigurations in digitally-transformed, hybrid IT environments that have elements such as cloud instances, containers, traditional data centers, a remote workforce and mobile devices.
According to Verizon, the most common insider threat is non-malicious employee error, rather than premeditated sabotage. “These are either by misconfiguring servers to allow for unwanted access or publishing data to a server that should not have been accessible by all site viewers. Please, close those buckets,” reads the report.
Another worrisome trend is the dominance of outsider threats, accounting for 69% of breaches, with ransomware being among most prevalent of this type of threat (used in 24% of incidents.) This highlights the importance of a strong vulnerability and remediation management program, to reduce the exposed vulnerable surface to attackers. To increase your security and your response speed, we recommend an emphasis on:
- remediation prioritization, so that you identify and fix right away the most critical threats to your organization
- distributed dynamic dashboarding across the organization’s departments, to empower situational awareness
- and transparent automation across the platforms composing IT and Security operations
Another finding that highlights the importance of a strong vulnerability management program is that exploiting vulnerabilities ranks third among the most popular hacking techniques, and that the primary hacking action vector in breaches are web applications.
A key for effective prioritization is the ability to consume cyber-threat intelligence data, and to use criteria like exploitability of a vulnerability, availability of a patch, and other real-time threat indicators correlated with your vulnerability information.
The report also highlights the importance policy compliance. For example, it identifies the top three causes for the large majority of the breaches as privilege abuse, data mishandling and unapproved workaround: three synonyms for lack of compliance.
Compliance is often regarded as the last thing to do on top of deployed projects. Rather, the correct approach would be to harmonize the collection and processing of IT, security and compliance data. That way, you create a single source of truth where data is visualized from multiple perspectives, based on the audience type. This will also help you reduce configuration errors.
Conclusion
It’s time for organizations to return to solid foundations for security and compliance. It all starts with a continuously updated IT asset inventory, and comprehensive detection of vulnerabilities and misconfigurations. Then you must prioritize your remediation work by correlating cyber threat indicators with your assets and their vulnerabilities. It’s also key to have an integrated patch management program to quickly fix your impacted assets.
Make sure all your assets — not just your on premises systems — are included in your scope of coverage: mobile devices, cloud workloads, containerized applications, DevOps pipelines, IoT systems and Operational Technology (OT) wares.
In all these tasks, Qualys can help.
(Marco Rottigni is Chief Technical Security Officer at Qualys)