Boost Security with These Gartner-Recommended Projects
Is your security team struggling to decide which projects will slash risk the most without breaking the bank? If so, we believe your security leaders can end analysis paralysis by perusing Gartner’s “Top 10 Security Projects for 2019” report. As its title states, the report recommends ten security projects for 2019, and the projects selected are supported by technologies available today, address the changing needs of cybersecurity and support what Gartner calls a CARTA (Continuous Adaptive Risk and Trust Assessment) strategic approach through risk prioritization.
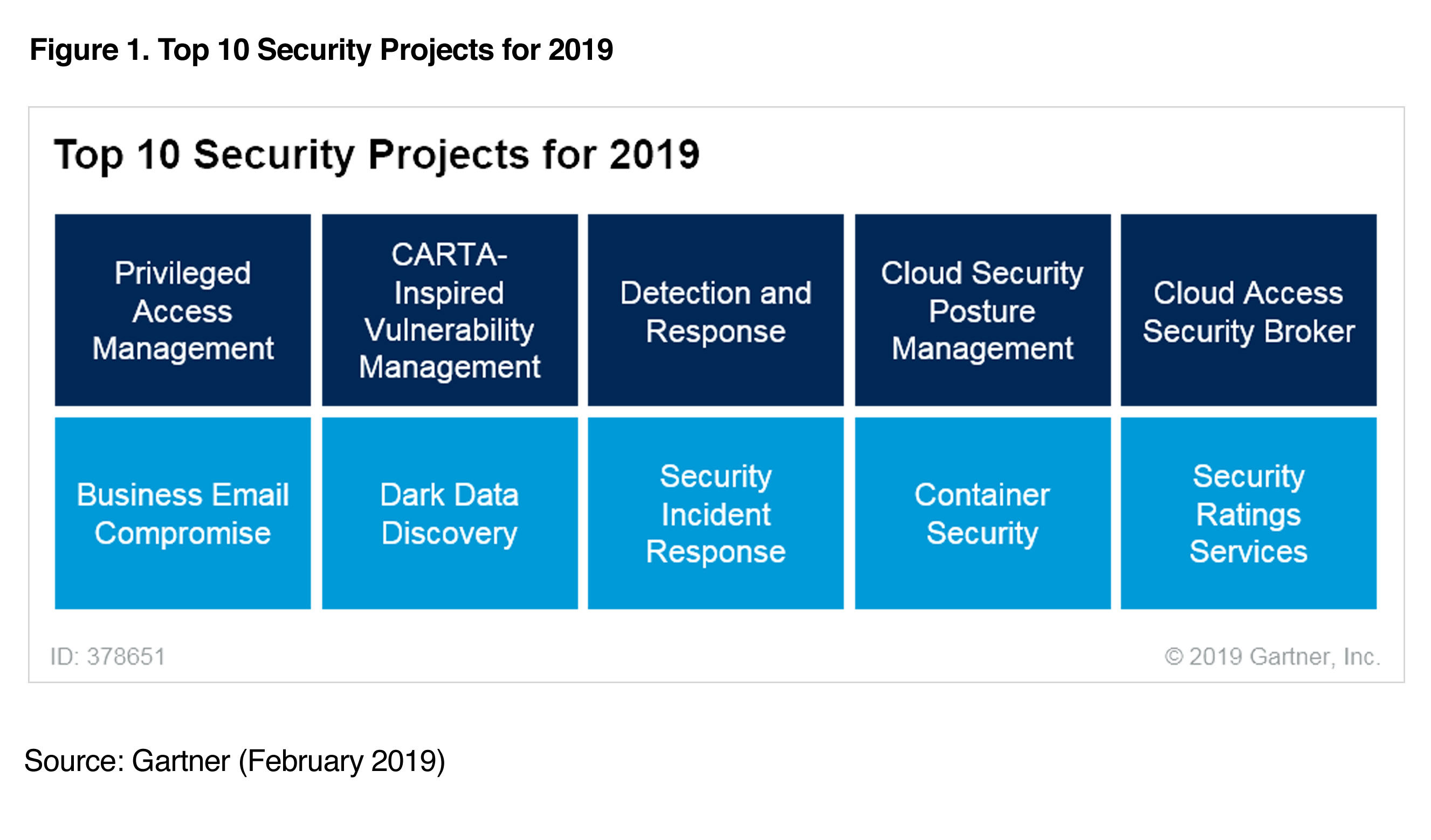
Below we highlight five of the projects, provide Gartner’s take, offer our opinion, and explain how Qualys can help you implement them.
CARTA-Inspired Vulnerability Management
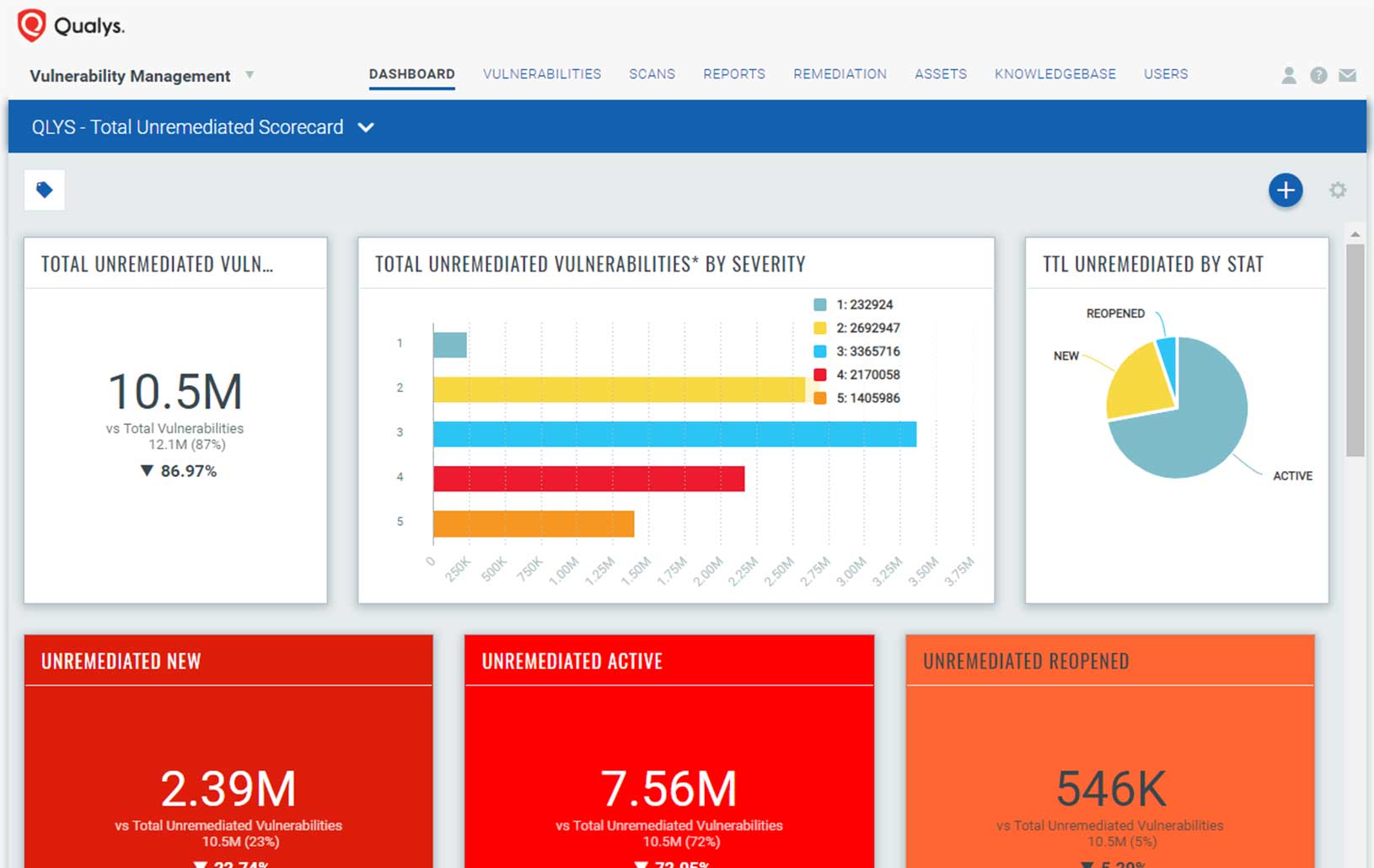
Gartner’s take: “Vulnerability management is a foundational part of information security operations. However, few organizations properly do the basics of vulnerability management with a high degree of fidelity, and many often assume vulnerability and patch management to be interchangeable. IT security operations cannot keep up with the sheer quantity of vulnerabilities. Security teams cannot patch everything, but can significantly reduce risk by prioritizing their vulnerability management efforts.”
How Qualys can help
With Qualys, organizations can have a comprehensive and integrated breach-prevention program that’s cloud-based and covers the full vulnerability lifecycle:
- A full, continuously updated and detailed inventory of all IT assets, wherever they reside
- Unparalleled vulnerability detection and assessment accuracy to continuously detect and protect against attacks, anytime, anywhere
- Precise threat prioritization to identify what to remediate first
- Solid patch management to streamline remediation for all your IT assets
Detection and Response
Gartner’s take: “SRM leaders who have accepted that there is no such thing as perfect protection and are looking for endpoint-, network- or user-based approaches for advanced threat detection, investigation and response capabilities should consider a detection and response project.”
How Qualys can help
Despite your best prevention efforts, breaches will happen, so you need a detection and response solution. With Qualys, organizations can detect indicators of compromise via a solution that’s cloud based, scalable, and precise. Qualys integrates endpoint detection, behavioral malware analysis, and pre-defined threat hunting techniques that incorporate a continuous view of an asset’s vulnerability posture along with suspicious activity monitoring. With Qualys, security analysts and incident responders can correlate endpoint activity with threat intelligence, network alerts, and sandbox analysis to quickly determine exactly when and where a compromise took place.
Cloud Security Posture Management

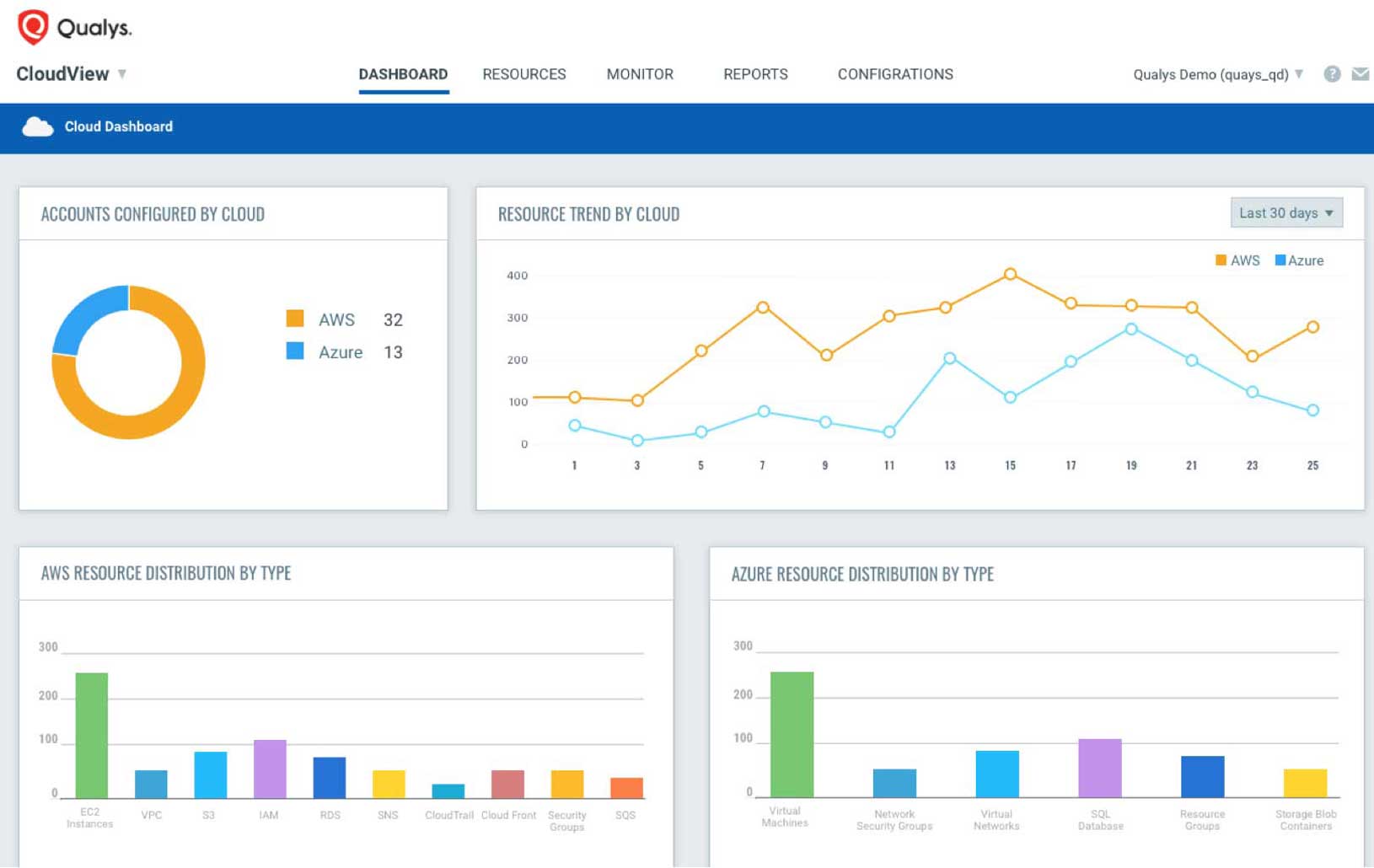
Gartner’s take: “Nearly all successful attacks on cloud services are the result of customer misconfiguration, mismanagement and mistakes. High levels of automation and user self-service in public cloud infrastructure as a service (IaaS) and platform as a service (PaaS) have magnified the importance of correct cloud configuration and compliance. SRM leaders should invest in cloud security posture management (CSPM) processes and tools to proactively and reactively identify and remediate these risks.”
How Qualys can help
Qualys has native integrations with the major public cloud platforms, including Google Cloud, Microsoft Azure, Amazon AWS, Alibaba Cloud and Oracle Cloud, to help customers:
- identify, classify, and monitor assets and vulnerabilities;
- comply with internal and external policies;
- prioritize vulnerability remediation;
- and automatically find and eradicate malware infections on your websites.
In addition, you can generate a continuously updated inventory of your public cloud workloads and infrastructure, as well as continuously monitor and assess your cloud assets and resources for misconfigurations and other mistakes.
Moreover, with Qualys you can integrate testing into your entire CI/CD (continuous integration / continuous delivery) DevOps pipeline. Code is automatically tested and then re-tested following fixes, ensuring that you release hardened containers, images and web applications into production. Once your code is in production, Qualys can continuously monitor it for any changes, and notify you of detected issues that need to be fixed.
Container Security
Gartner’s take: “Technical professionals tasked with securing containers must harden the continuous integration/continuous delivery (CI/CD) pipeline so that all containers are scanned for vulnerabilities and configuration issues automatically in development, before being allowed to be released into production.”
How Qualys can help
Developers are embracing container technology because it boosts speed, agility, and flexibility in app development and delivery, making it popular for microservices and among DevOps teams — but it also creates security and compliance challenges.
Qualys provides a comprehensive solution for visibility and control of the entire lifecycle of containerized apps — the build, ship and runtime stages. It monitors and protects containerized applications from the inside, by collecting granular behavior data about the application, providing deep visibility and enforcing normal application behavior for runtime protection. That way, Qualys’ container security solution gives security teams continuous discovery, tracking, and protection of containers in DevOps pipelines and deployments at any scale.
Security Rating Services
Gartner’s take: “As digital transformation matures, the risks associated with complex ecosystems become an integral part of the business. It is no longer just about the internal security and risk posture of an organization, but about the posture of suppliers, regulators, customers, business partners and platforms.”
How Qualys can help
Security Rating Services (SRS) gather data only from external sources, so Qualys believes they should be complemented with practices such as security questionnaires, in order to obtain more complete risk assessments. Qualys automates business-process control assessments that are conducted via security questionnaires. These assessments poll third parties on things like their regulatory compliance and data security. Qualys automates, centralizes and streamlines this entire process, including survey design, questionnaire distribution, response monitoring, data aggregation and report generation. It provides unparalleled accuracy, speed and scale, letting you quickly and precisely identify compliance gaps among third parties — as well as internally among your own staff.
Read the full report!
We invite you to download the Gartner report, which has many more details and project ideas for your security team, including:
- Privileged Access Management
- Business Email Compromise
- Dark Data Discovery
- Security Incident Response
- Cloud Access Security Broker
(Gartner, Top 10 Security Projects for 2019, Brian Reed, Neil MacDonald, Peter Firstbrook, Sam Olyaei, Prateek Bhajanka, 11 February 2019)