FedRAMP ConMon – Efficiently & Effectively Managing SLAs for RA-5d Requirement
Are you a FedRamp-certified organization looking to more effectively maintain your FedRAMP status? There are tools available to help simplify the process and while the process involves some terminology, it is easily understood as outlined below. Additionally, it is supported by pre-built dashboards in the Qualys Cloud Platform that help organizations meet SLAs for required remediations.
Maintaining ATO
Once a FedRAMP authorization (ATO) has been granted, it must be maintained through Continuous Monitoring (ConMon) by the Cloud Service Provider (CSP) according to the assessment and authorization process. Performing ongoing security assessments of deployed security controls in a Cloud Services Offering (CSO) determines their effectiveness with respect to new exploits, attacks and changes planned or unplanned that occur over the system’s life. To maintain FedRAMP authorization, a CSP must monitor and assess their security control environment on a regular basis and demonstrate that the security posture of their service offering is continuously acceptable.
The effectiveness of a CSP’s continuous monitoring capability supports ongoing authorization and reauthorization decisions. Security-related information collected during continuous monitoring is used to make updates to the security authorization package. Updated documents provide evidence that FedRAMP baseline security controls continue to safeguard the system as originally planned.
Remediating Vulnerabilities
One key aspect of the ConMon is the SLAs for remediating vulnerabilities in the environment. These are part of the RA-5d control and outlined in the CSP Continuous Monitoring Strategy Guide. CSPs must mitigate all discovered vulnerabilities within the following timeframes:
- High-risk vulnerabilities within 30 days
- Moderate-risk vulnerabilities within 90 days
- Low-risk vulnerabilities within 180 days
CSPs must send their Reviewer updated artifacts every 30 days to show evidence that outstanding high-risk vulnerabilities have been mitigated. The risk is based on CVSS v3 base score. If a certain vulnerability doesn’t have CVSS v3 base score, then CVSS v2 base score should be used, and if that is not available the risk score provided by the vendor is acceptable.
Identifying Required Remediations to Meet SLAs
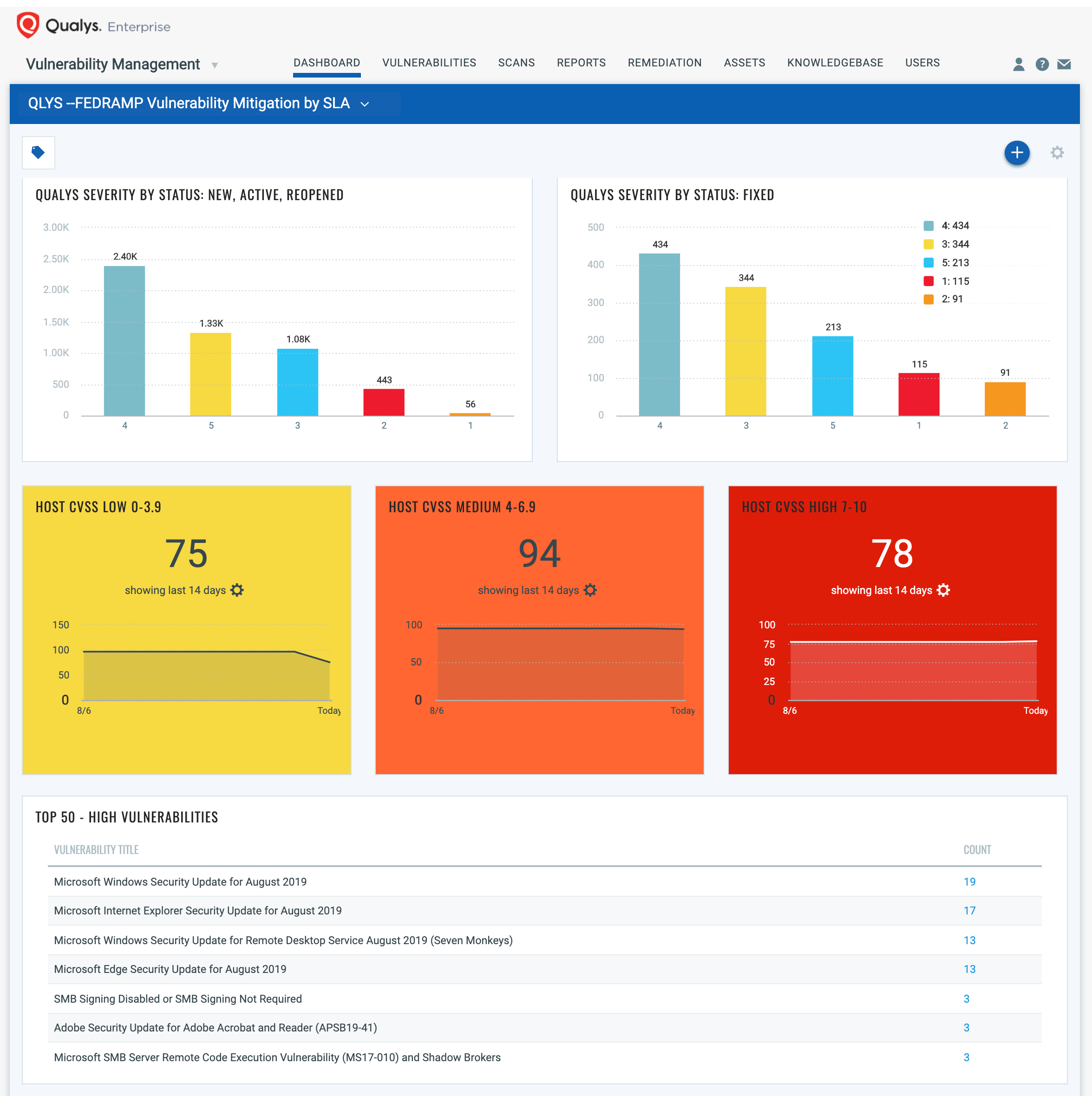
To help Qualys customers efficiently and effectively track and meet these SLAs, Qualys is publishing the FedRamp Vulnerability Mitigation by SLA dashboard partially shown below (see full dashboard). The dashboard makes it easy to identify high-priority vulnerabilities (with high CVSS 3 Base Scores) and to track remediation. The dashboards give visibility into the status of vulnerabilities by severity and the length of time they have been open, making it clear the actions needed to meet SLAs.