Blue is a color we love but can’t Keep!

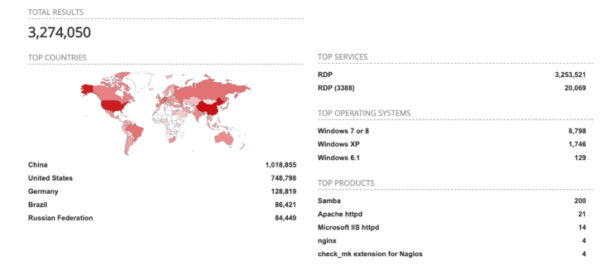
Recent reports this year revealed nearly 1 million computer systems are still vulnerable and exposed to BlueKeep in the wild. These systems are still easy targets for an unauthenticated attacker (or malware) to execute code leveraging this patchable vulnerability. Because so many systems are still vulnerable, Qualys has added its BlueKeep dashboard directly into the product, so you can more easily track and remediate this vulnerability.
Why is BlueKeep So Critical?
The BlueKeep vulnerability announced earlier in 2019 allows attackers to run arbitrary program code on victims’ computers. The vulnerability is found in Remote Desktop Services – formerly known as Terminal Services – which affects some older versions of Windows. The Remote Desktop Protocol (RDP) itself is not vulnerable. This vulnerability is pre-authentication and requires no user interaction which makes it capable to widespread attacks because attackers can use automated tools for attacks as this vulnerability is “wormable.” This means an attack could spread itself automatically across networks without any intervention by users, just as the WannaCry and Conficker worms have spread in the past.
Microsoft assigned it the highest severity level of Critical in its published guidance for customers, and in the US government’s National Vulnerability Database, the entry for CVE-2019-0708 is scored as 9.8 out of 10. Microsoft issued a blog post strongly recommending that users install its patches, including on those famous out-of-support operating systems such as Windows XP and Windows Server 2003.
Workarounds?
The following workarounds may be helpful but in all cases, Microsoft strongly recommends that you install the updates for this vulnerability as soon as possible even if you plan to leave these workarounds in place:
- Enable Network Level Authentication (NLA) on systems running supported editions of Windows 7, Windows Server 2008, and Windows Server 2008 R2You can enable Network Level Authentication to block unauthenticated attackers from exploiting this vulnerability. With NLA turned on, an attacker would first need to authenticate to Remote Desktop Services using a valid account on the target system before the attacker could exploit the vulnerability.

- Block TCP port 3389 at the enterprise perimeter firewall: TCP port 3389 is used to initiate a connection with the affected component. Blocking this port at the network perimeter firewall will help protect systems that are behind that firewall from attempts to exploit this vulnerability. This can help protect networks from attacks that originate outside the enterprise perimeter. Blocking the affected ports at the enterprise perimeter is the best defense to help avoid Internet-based attacks. However, systems could still be vulnerable to attacks from within their enterprise perimeter.
- Accounts that can be logged into via RDP require complex passwords (a long passphrase containing 20+ characters.
- Install two-factor authentication (2FA) and at a minimum require it on all accounts that can be logged into via RDP.
Tracking Impact and Remediation
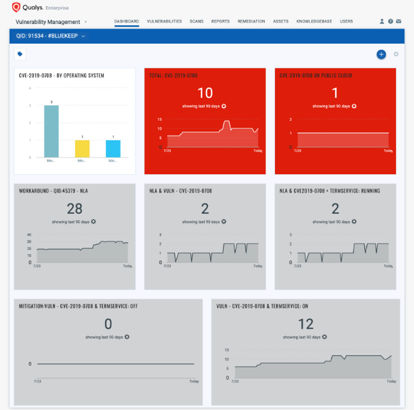
 The Qualys Cloud Platform enables you to continuously monitor for vulnerabilities and misconfigurations and get alerted for your most critical assets. Qualys signature and visualization team have teamed up and included an in-product BlueKeep dashboard for easy tracking and remediation. This dashboard has been included in Qualys Cloud Platform release 2.42 and can be found within the Dashboard templates library. It will automatically show your systems whether scanned internally, externally or on remote mobile computers with the groundbreaking Qualys Cloud Agent.
The Qualys Cloud Platform enables you to continuously monitor for vulnerabilities and misconfigurations and get alerted for your most critical assets. Qualys signature and visualization team have teamed up and included an in-product BlueKeep dashboard for easy tracking and remediation. This dashboard has been included in Qualys Cloud Platform release 2.42 and can be found within the Dashboard templates library. It will automatically show your systems whether scanned internally, externally or on remote mobile computers with the groundbreaking Qualys Cloud Agent.
The dashboard toolbox in Qualys Community has additional dashboards created by your SMEs and Product Management team that you can import into your subscription.
Remediating with Qualys Patch Management
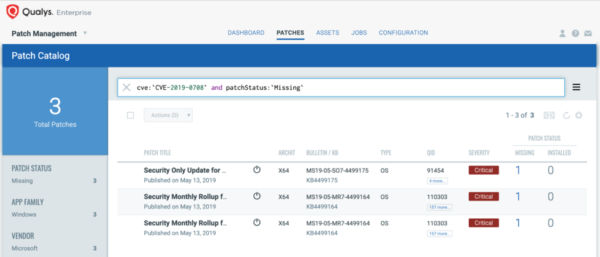
Customers using Qualys Patch Management with Cloud Agent can search for cve:`CVE-2019-0708` in the Patch Catalog, and click “Missing” in the side panel to locate and deploy patches to all affected Operating Systems, including Windows XP and Server 2003.
For emergency patching, you can create an on-demand job and target it at the “Cloud Agent” tag to cover all hosts. For continuous patching, a daily job can be created with a 24-hour “patch window” to ensure all hosts will continue to receive the required patches. This patch does require a reboot.
Targeting specific operating systems is not necessary. The Qualys Cloud Agent already knows which patch is needed for each host.
We should always keep in mind that adversaries don’t have to be extremely skilled in finding vulnerable systems. There are tons of scripts, tools and online search engines that can help narrow down and identify systems for reconnaissance and further the Cyber Kill Chain steps for exploitation.
Get Started Now
To start detecting and remediating this vulnerability now, sign up for a Qualys Suite trial.