Detect Unauthorized Processes Making Changes in Your Environment with Qualys File Integrity Monitoring
With the average cost of a data breach exceeding $3.5 million as per Cost of a Data Breach Report, almost all organizations these days adopt stringent policies in order to safeguard their confidential business and customer information. Strong RBAC-driven systems have certainly made it difficult for attackers to gain unauthorized access. However, malicious programs masked as genuine ones can compromise your environment, sneak their way into your databases, and can even allow unauthorized parties to access and/or view information.
Streamlined and Automated Incident Management
Qualys File Integrity Monitoring (FIM) provides you with a streamlined and automated incident management process and helps you take proactive actions towards securing your environment when anomalies are detected. At times, the users carrying out an operation may be authorized; but the process itself may be unauthorized or compromised, which may easily result in a security violation. To protect your organization from such security loopholes, Qualys FIM provides you with features such as alerts and notifications for events that may be unauthorized. These alerts are instantly triggered upon undesirable or seemingly malicious activities, so that you can take appropriate action.
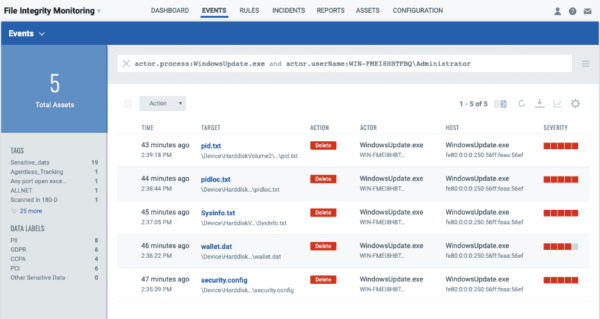
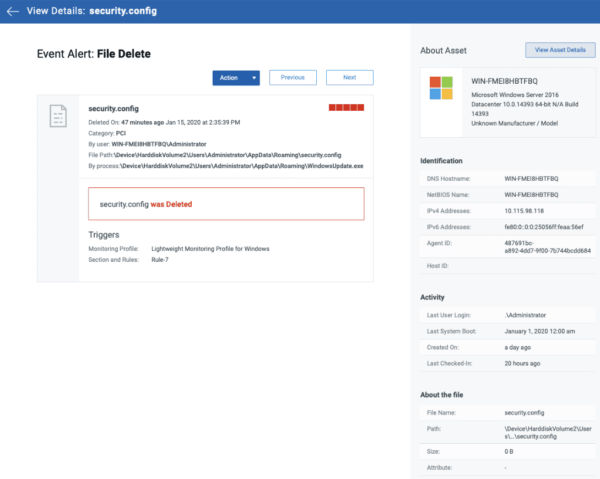
Let’s take the example of Unauthorized Windows Update Activity during a Windows Update and how Qualys FIM can help you stay in control of security and integrity of your data. From FIM’s perspective, a Windows Update is often whitelisted or ignored as it generates a lot of events that may be expected as well as valid. Attackers usually take advantage of this fact and introduce malware masked as a valid-looking process during this period. A good use case in this scenario is windowsupdate.exe. It might look like a valid Windows Update executable similar to various other valid processes such as TiWorker, Windows-KB, wuauclt.exe, cleanmgr, MRT-KB, sihclient and so on. However, in reality, windowsupdate.exe is a malicious program that has been designed to steal sensitive information from a computer. Any process or activity, which may come across as valid but may not be so, must be taken into consideration for security reasons. One may take a look at the activities triggered by such processes to decide whether they are valid or malicious.
Qualys FIM enables you to track the changes made by such malicious processes as soon as they occur.
With Qualys FIM, you receive real-time updates about each such event that is detected, complete with granular details such as who-what-when-where about the changes as shown in the following screenshot.
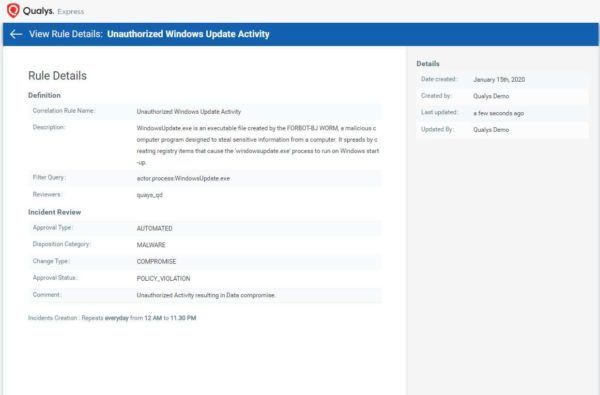
You can also create correlation rules, which are triggered upon events of interest. Correlation rules drastically cut down the volume of data that needs to be monitored and offer you flexibility in creating event groups by associating one or multiple factors into one unit. Qualys FIM provides predefined queries for correlation rules and you can also choose to create custom rules by using QQL queries.
Following is an example of correlation rule created to capture the unauthorized Windows Update activity.
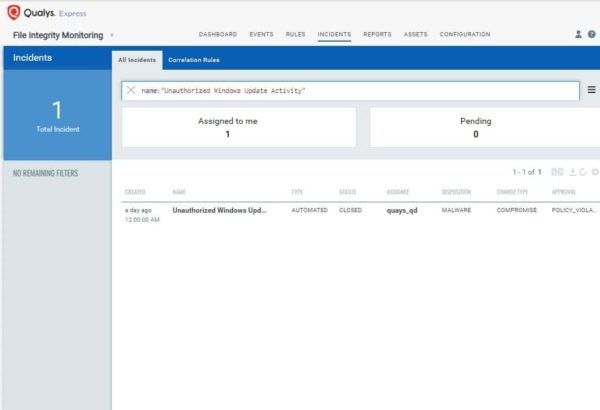
An alert is sent to the authorized users as soon as the correlation rule is triggered by an incident, thus uncovering the infection and helping you to decide on the appropriate countermeasures to stop an attack.
Refer to the screenshot below for the incident that is created for this activity.
At this point, you may leverage the other Qualys modules such as Qualys Vulnerability Management and Qualys Policy Compliance to intervene and take necessary action.
Staying on Top of Detections
Qualys File Integrity Monitoring helps you identify the source of an attack with all required details. If you are able to quickly spot an intruder in your environment, you can act faster to remove any suspected malicious code. Being on top of detections will not only lower the amount of valuable data being lost during an attack, it will also minimize the overall risk by reducing the attack surface area.