Continuous Monitoring and Beyond

As security professionals, we struggle with the high volume of data we need to sort through while trying to parse out the critical alerts that are important for us to take immediate action upon. Being at the forefront of innovation for the past 20 years, Qualys offers 20 plus solutions which all reside in a single platform allowing you to conduct assessments, analyze, prioritize and respond quickly and effectively through our VMDR and Multi-Vector EDR product lines.
Today, I would like to focus on how you can easily create focused monitoring rules. I highly suggest you explore Continuous Monitoring to help focus on actions for your teams leveraging additional capabilities within the Qualys platform.
Continuous Monitoring (CM) is a security practice often confused with auditing. But there is a clear difference between the two. Continuous security monitoring (to be most specific) can help reduce auditing costs and accelerate the launch of new services. As a network security control measure, Continuous Monitoring is designed to scale and be integrated into an effective cyber-defense strategy. Continuous Monitoring provides a unique approach to any security team big or small. It enables you to proactively identify and address potential issues by monitoring for changes to your systems before they can be compromised and turn to breaches by getting email alerts.
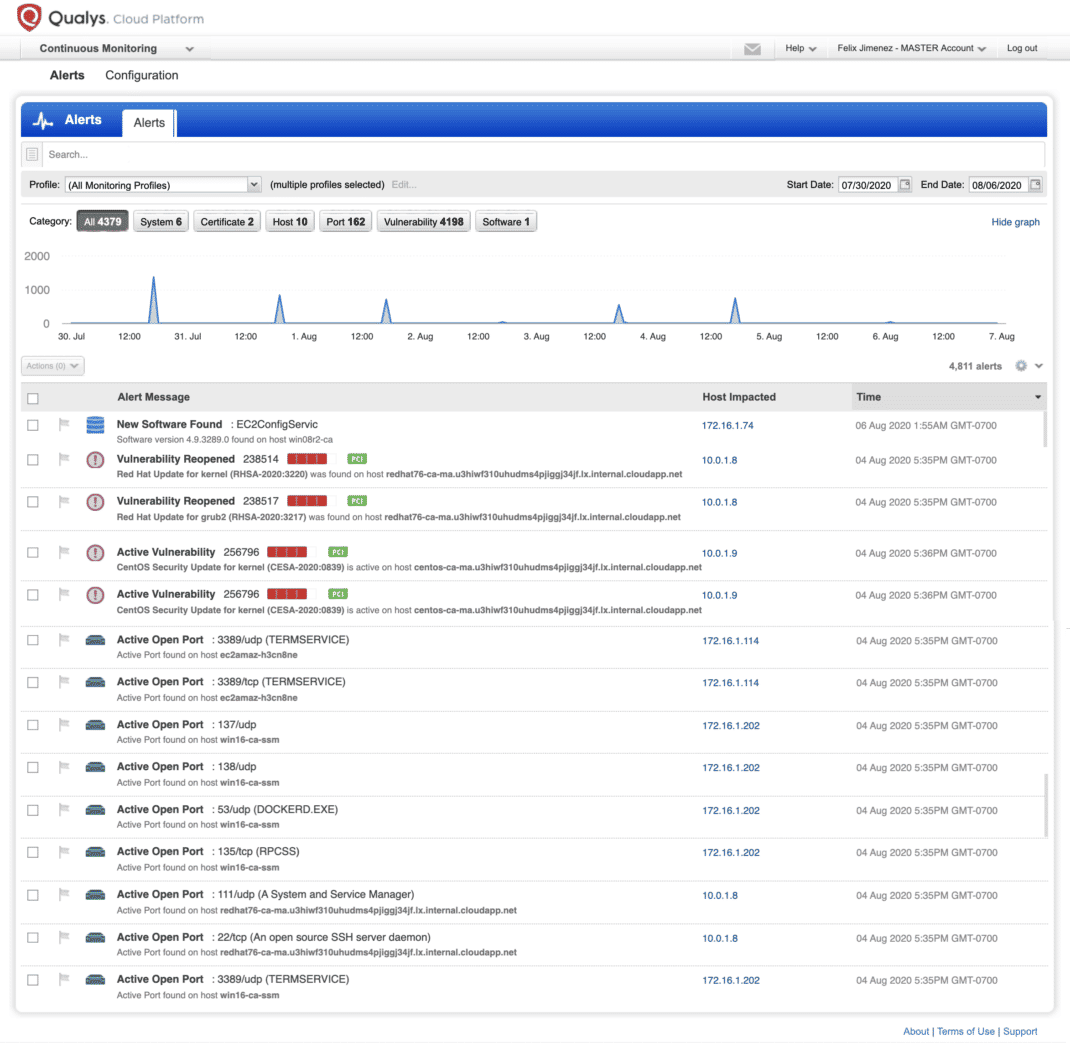
Here are my top five simple use cases around continuous security that I have used and found helpful.
New Host
Monitor any new assets discovered during the course of a vulnerability scan.
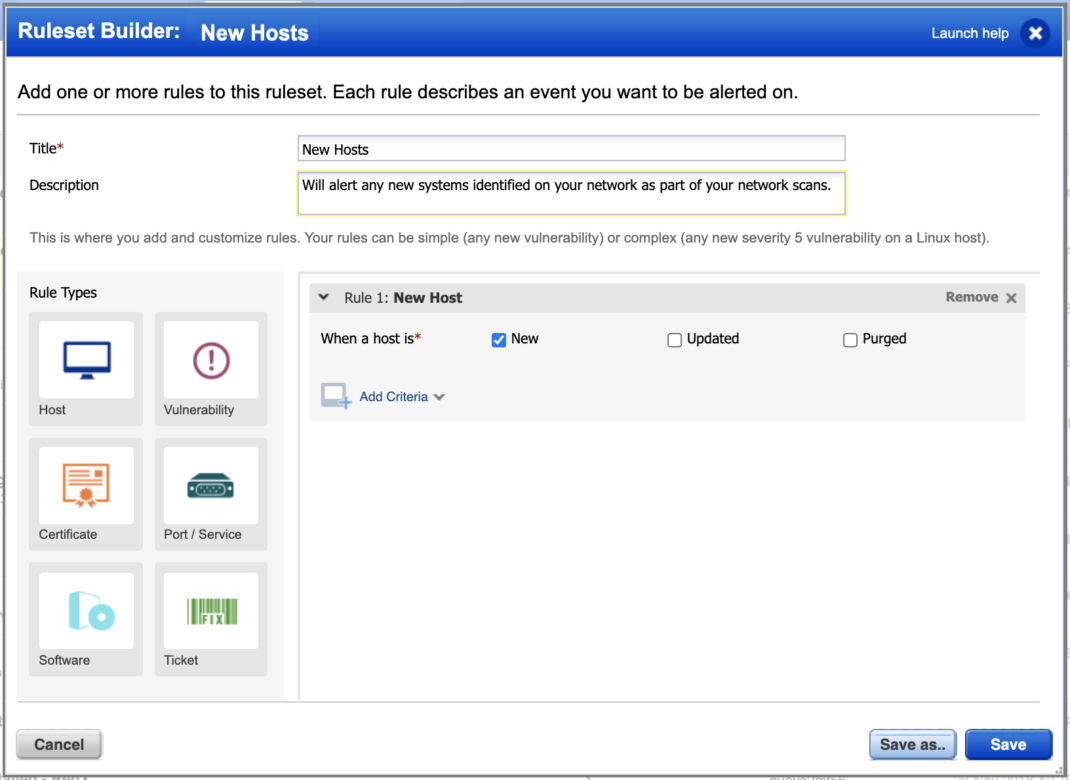
Questions such as “what type of asset is it”, “where is it communicating to”, “is it managed or unmanaged” arise. As part of the promise Qualys made to make everything visible in a single pane of glass, you can answer these questions, and more, with Global IT Asset inventory which allows you to see this and more through our VMDR solution with unlimited passive scanners. We decided to make our Global IT Asset Inventory app free of charge so that everyone around the world can benefit.
Malware
Monitor any assets with vulnerabilities that could be exploited and are related to Malware. But then the question is, do I have malware in my environment?
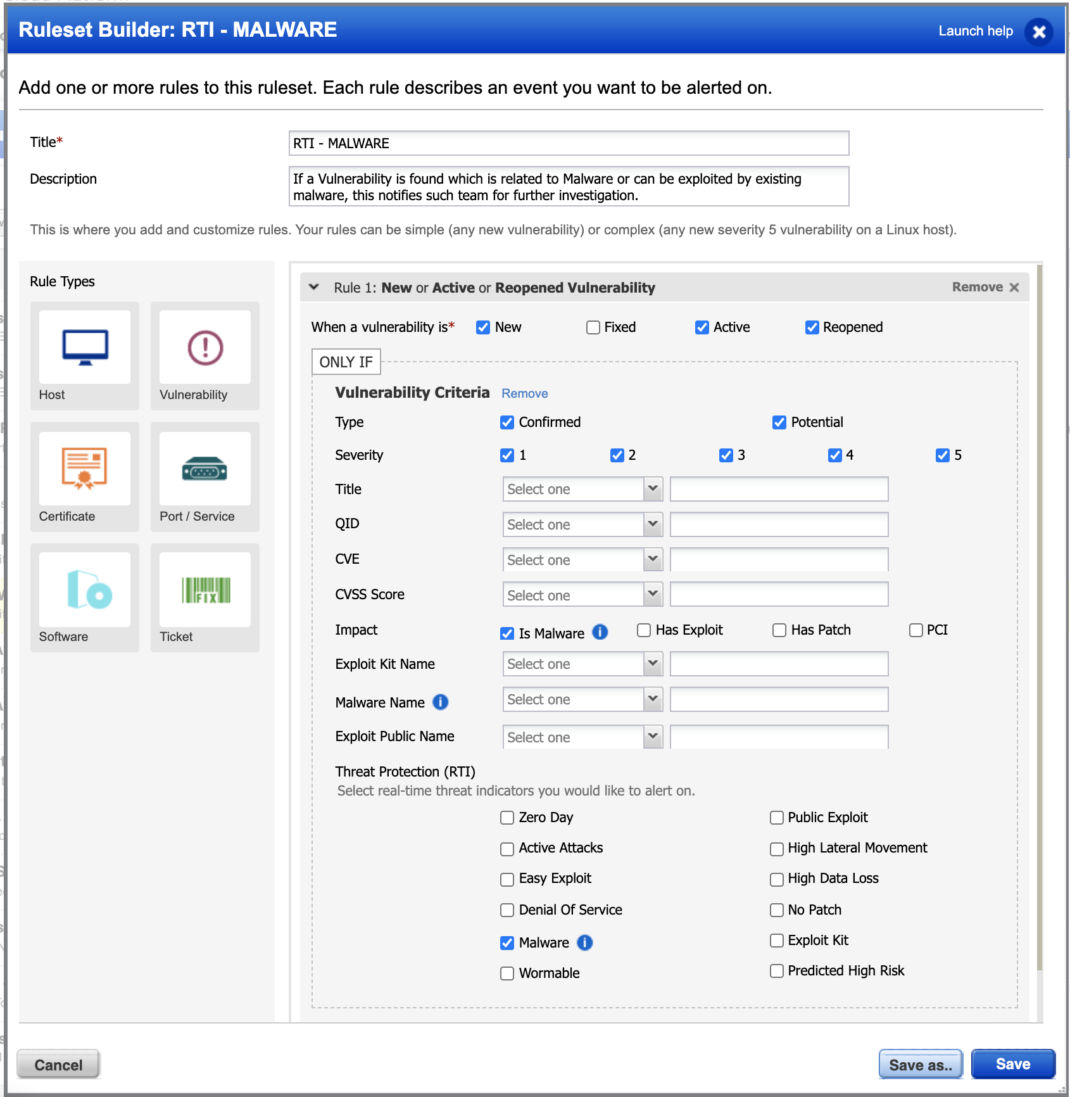
You can also build widgets in EDR to focus on Malware related IOCs.
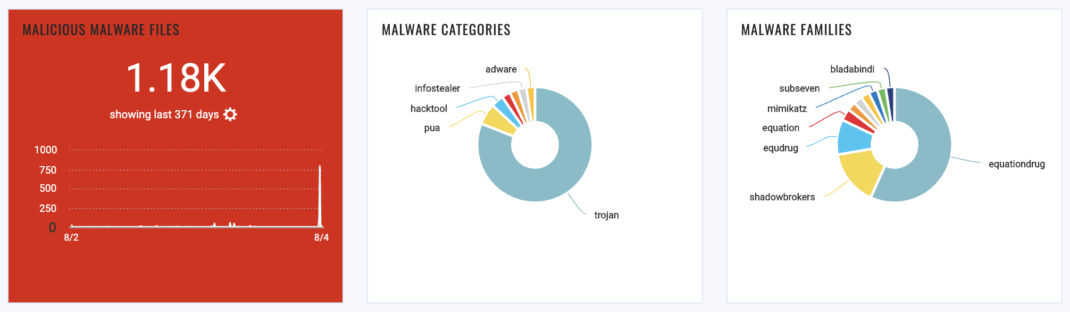
Endpoint Detection and Response EDR will enable you to see if you have malware, as well as unwanted or potential activities leading to IOCs within your environment. Through a dashboard widget or EDR alert rule, you will be empowered to take action and quarantine, kill, or delete malicious files.
Top 20 Hacked Ports
Monitor any ports you would like that are important to you and get notified as part of their state.
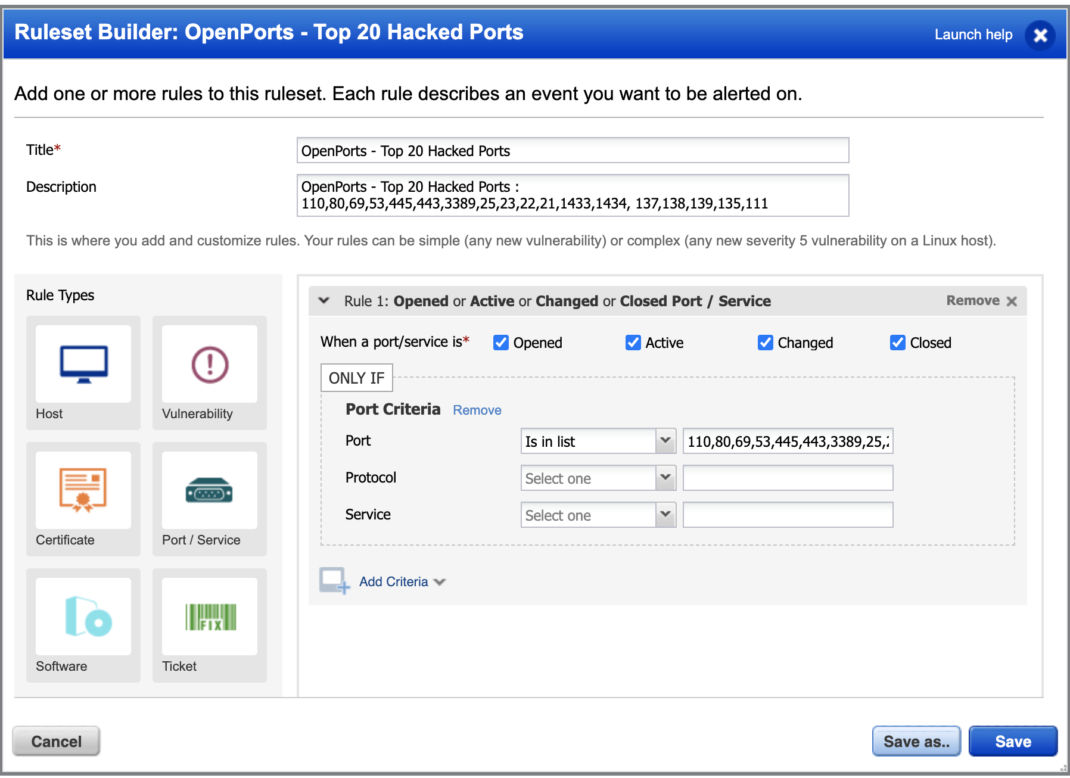
You can also build a widget within a dashboard and see all open ports for a group of assets or a specific asset.
SSH Running on a Non-Standard Port
Monitor any ports and services which are not on their standard defined port.
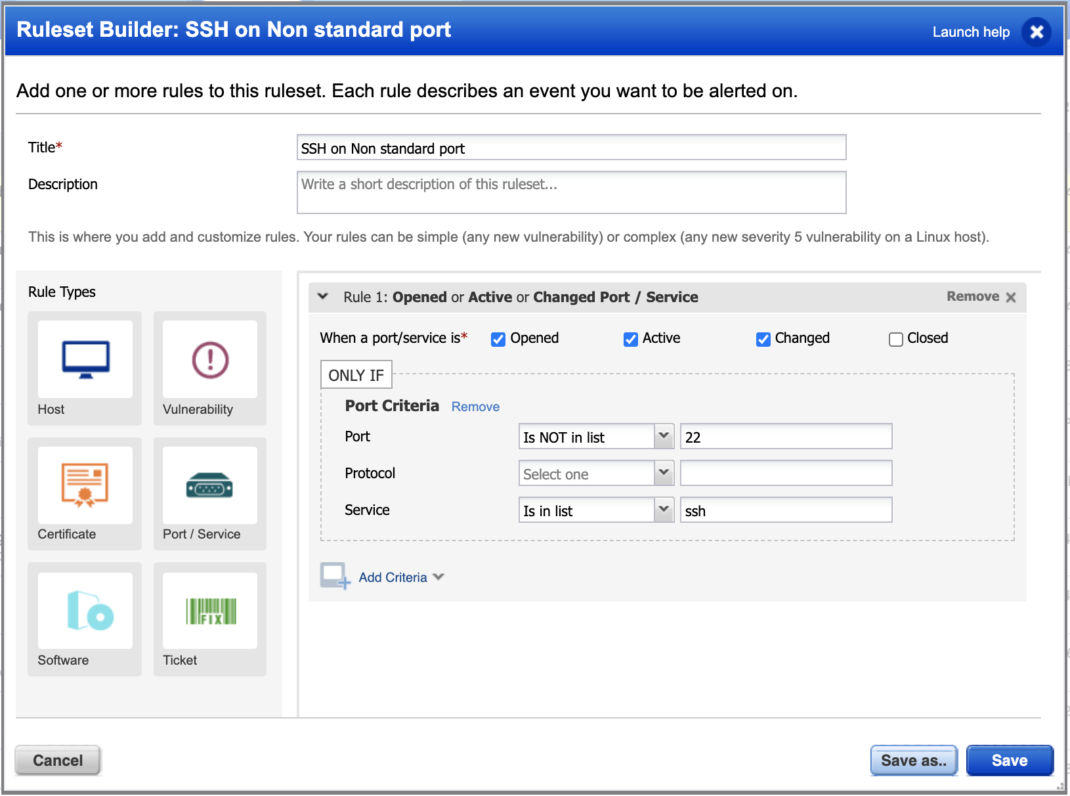
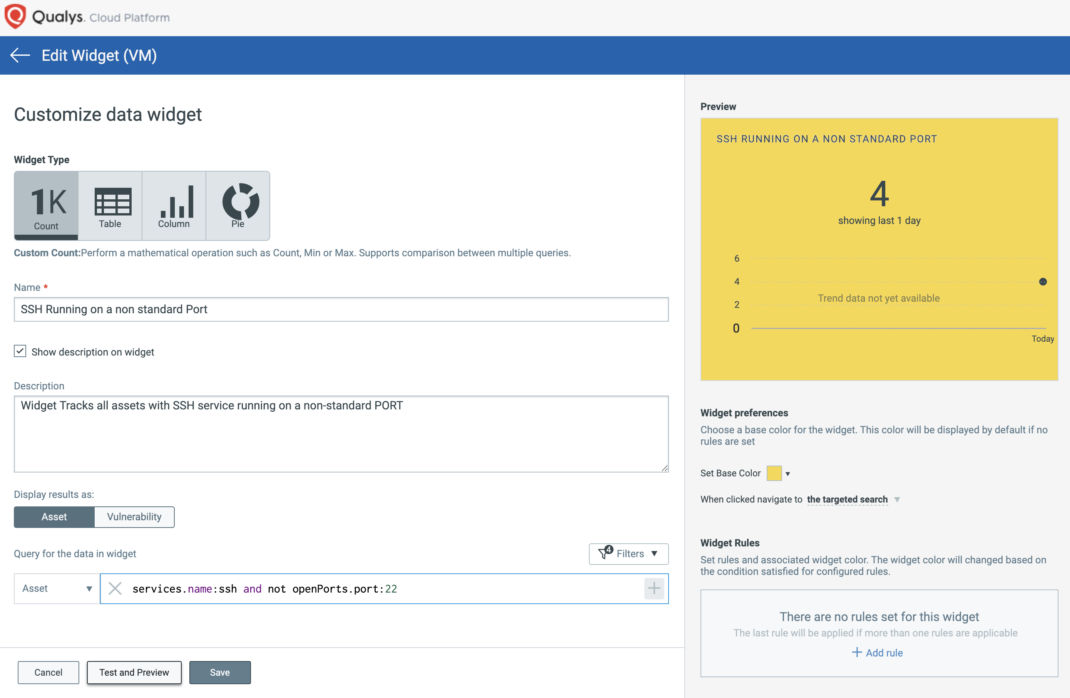
You can also build a widget within a dashboard to see which assets have SSH on a non-standard port.
Query: services.name:ssh and not openPorts.port:22
PCI Compliance
Monitor any assets only for related PCI vulnerabilities.
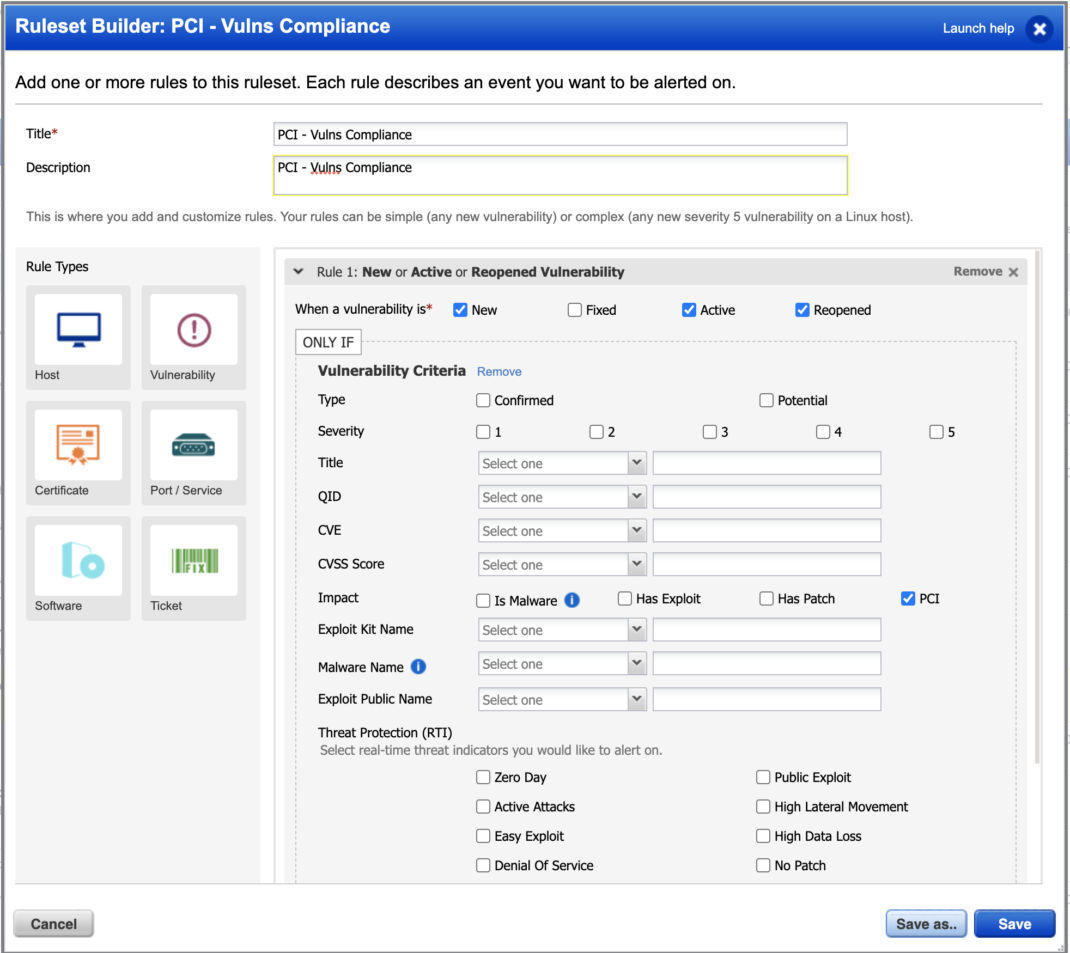
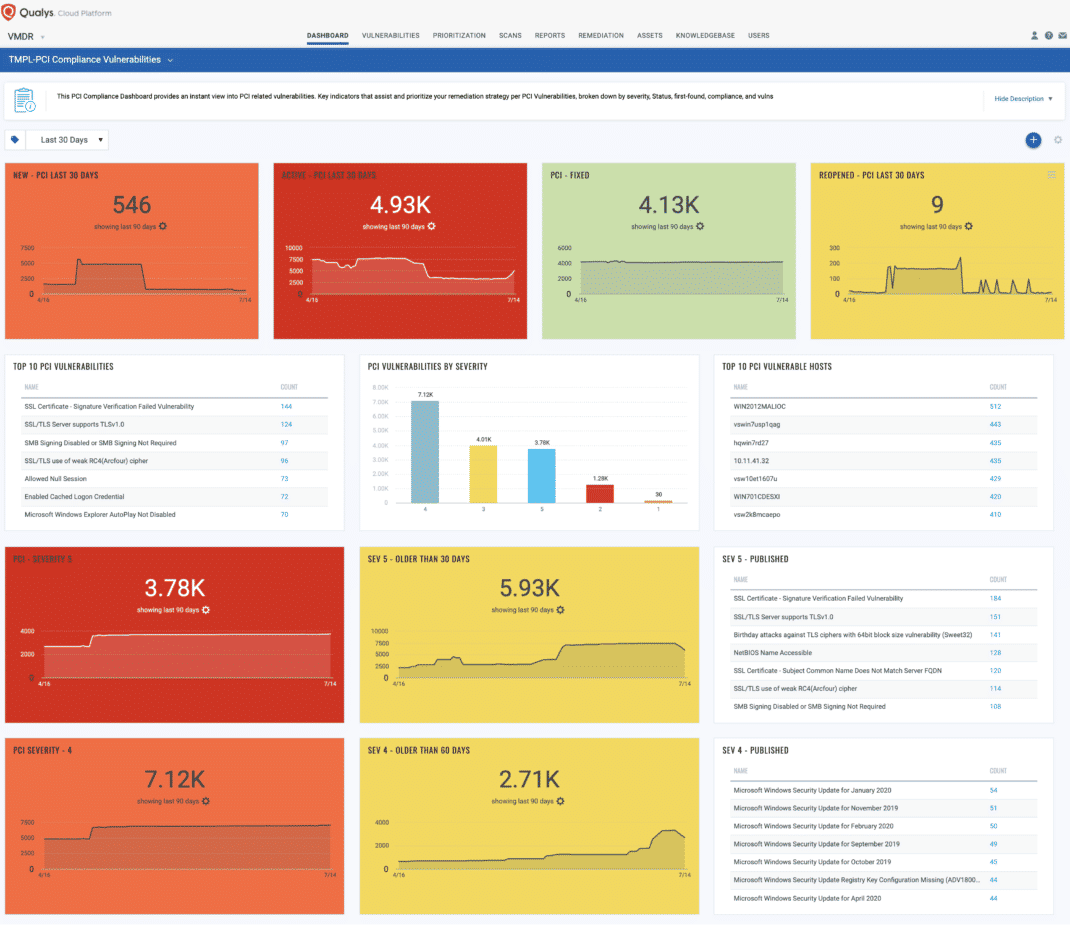
You can also build a dashboard to focus on PCI related vulnerabilities. See PCI Compliance Vulnerability Exposure Dashboard
Get Started Now
To start detecting, prioritizing, remediating, and take responsive actions in your organization now, get a Qualys Suite trial.
Contributors
Brian Canaday, Security Solutions Architect, Qualys
Felix, great list! Continuous Monitoring has a lot of great use cases. I’d like to offer up one that I see a lot of value in myself. CM allows you to alert on any vulnerability that has a “Re-opened” status. Re-opened vulnerabilities should be extremely rare. If vulnerabilities are being re-opened it likely means one of two things — 1.) There is an authentication issue with the scan/asset or 2.) A patch roll back has been applied or mitigating control has been overwritten and made the host more vulnerable. These are important changes to be notified about, as you can take immediate action to address before the root cause spreads through your environment and causes data discrepancies or further remediation reversion.