Microsoft Windows TCP/IP Remote Code Execution Vulnerability (CVE-2020-16898) – Automatically Discover, Prioritize and Remediate Using Qualys VMDR®

On October 13, 2020, Microsoft fixed a critical remote code execution vulnerability in the Windows TCP/IP stack for handling ICMPv6 Router Advertisement packets. While Microsoft ranks this vulnerability as “Exploitation More Likely,” we may see a proof-of-concept released soon. The security issue has received a critical severity rating score of 9.8 based on the CVSS v3 scoring system.
Vulnerability Details:
McAfee Advanced Threat Research released a test script to demonstrate Denial of Service that causes immediate BSOD (Blue Screen of Death); however, it could potentially lead to remote code execution and is capable of being weaponized into a chain reaction allowing attacks to spread from one vulnerable machine to another (wormable).
IPv6 router advertisement packet with a RDNSS (Recursive DNS Server) option, if maliciously crafted, can remotely trigger tcpip.sys file of Windows OS, leading to a DoS attack. The vulnerability occurs due to parsing ICMPv6 messages incorrectly by tcpip.sys driver. The logical flaw in tcpip.sys can be exploited into buffer overflow by adding more bytes to memory stack. As the vulnerability lies within the router advertisement packet of ICMPv6 Neighbor Discovery Protocol, it is also known as “Bad Neighbor.”
Affected products:
- Windows 10 Version 1709
- Windows 10 Version 1803
- Windows 10 Version 1809
- Windows 10 Version 1903
- Windows 10 Version 1909
- Windows 10 Version 2004
- Windows Server 2019
A complete list of affected devices is available on Microsoft’s October 2020 security advisory.
Identification of Assets using Qualys VMDR
The first step in managing vulnerabilities and reducing risk is identification of assets. Qualys VMDR makes it easy to identify Windows systems.
operatingSystem: "Windows 10" OR operatingSystem: "Windows Server 2019"
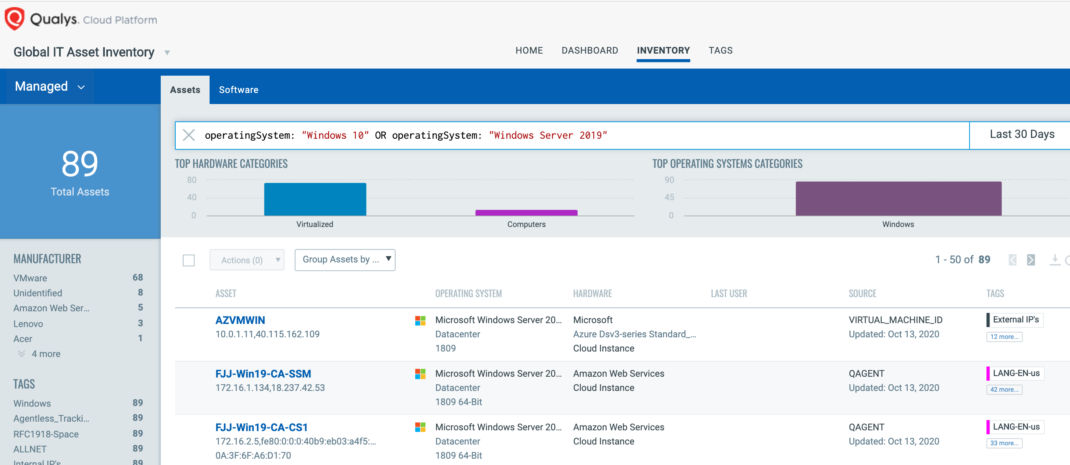
Once the hosts are identified, they can be grouped together with a ‘dynamic tag’, let’s say – “CVE-2020-16898”. This helps in automatically grouping existing hosts with this vulnerability as well as any new hosts that spins up in your environment. Tagging makes these grouped assets available for querying, reporting and management throughout the Qualys Cloud Platform.
Discover TCP/IP Stack “CVE-2020-16898” Vulnerability
Now that hosts with CVE-2020-16898 are identified, you want to detect which of these assets have flagged this vulnerability. VMDR automatically detects new vulnerabilities like Windows TCP/IP Stack vulnerability based on the always updated Knowledgebase.
You can see all your impacted hosts for this vulnerability tagged with the ‘CVE-2020-16898’ asset tag in the vulnerabilities view by using this QQL query:
vulnerabilities.vulnerability.qid:91686
This will return a list of all impacted hosts.
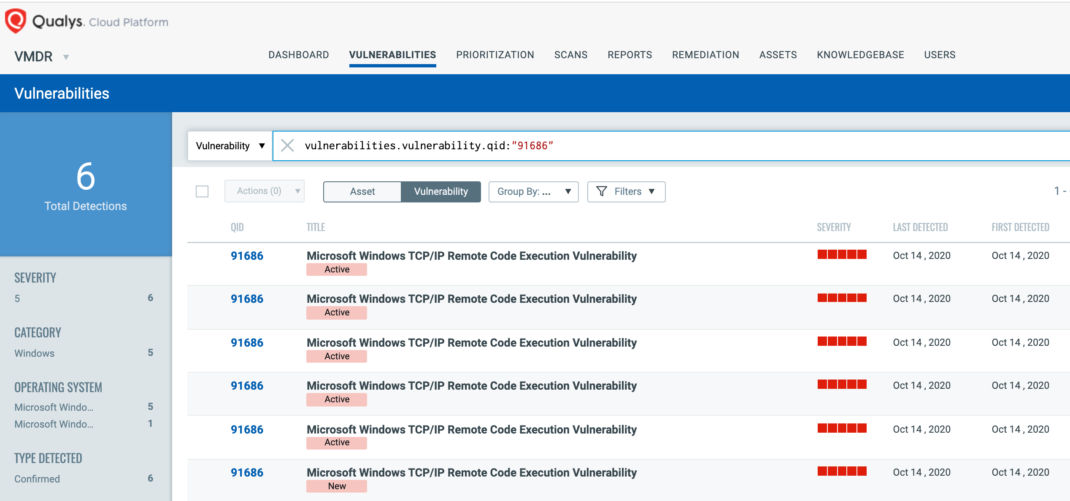
QID 91686 is available in signature version VULNSIGS-2.5.6-3 and above and can be detected using authenticated scanning or the Qualys Cloud Agent manifest version 2.5.6.3-2 and above.
Along with the QID 91686, Qualys released IG QID 45468 to help customers track assets on which “ICMPv6 RDNSS” is disabled in the Windows TCP/IP settings.
QID 45468 : Microsoft Windows TCP/IP ICMPv6 RDNSS Disabled
Using VMDR, the Windows TCP/IP Stack vulnerability can be prioritized for the following real-time threat indicators (RTIs):
- Remote Code Execution
- Easy Exploit
- Denial of Service
- High Data Loss
- High Lateral Movement
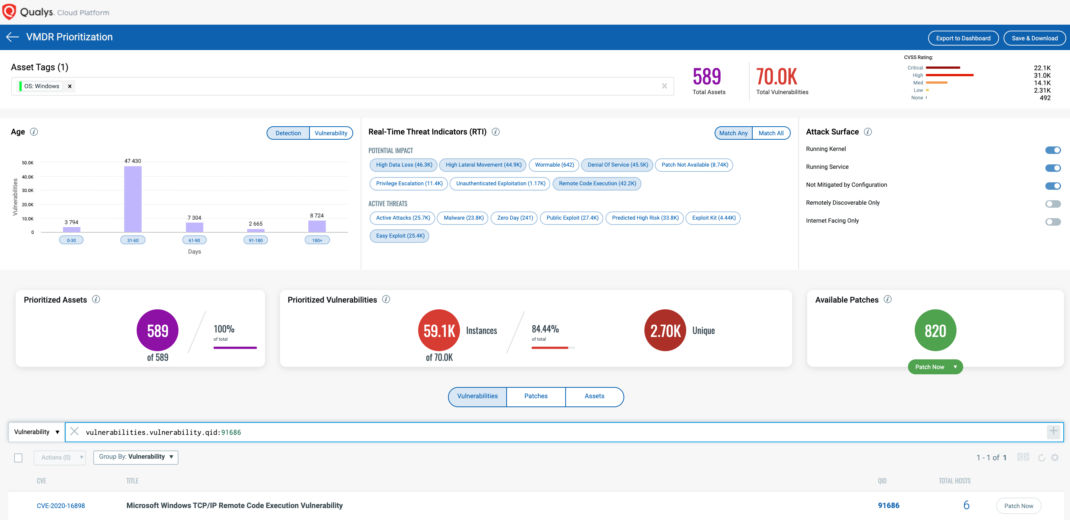
VMDR also enables you to stay on top of these threats proactively via the ‘live feed’ provided for threat prioritization. With ‘live feed’ updated for all emerging high and medium risks, you can clearly see the impacted hosts against threats.
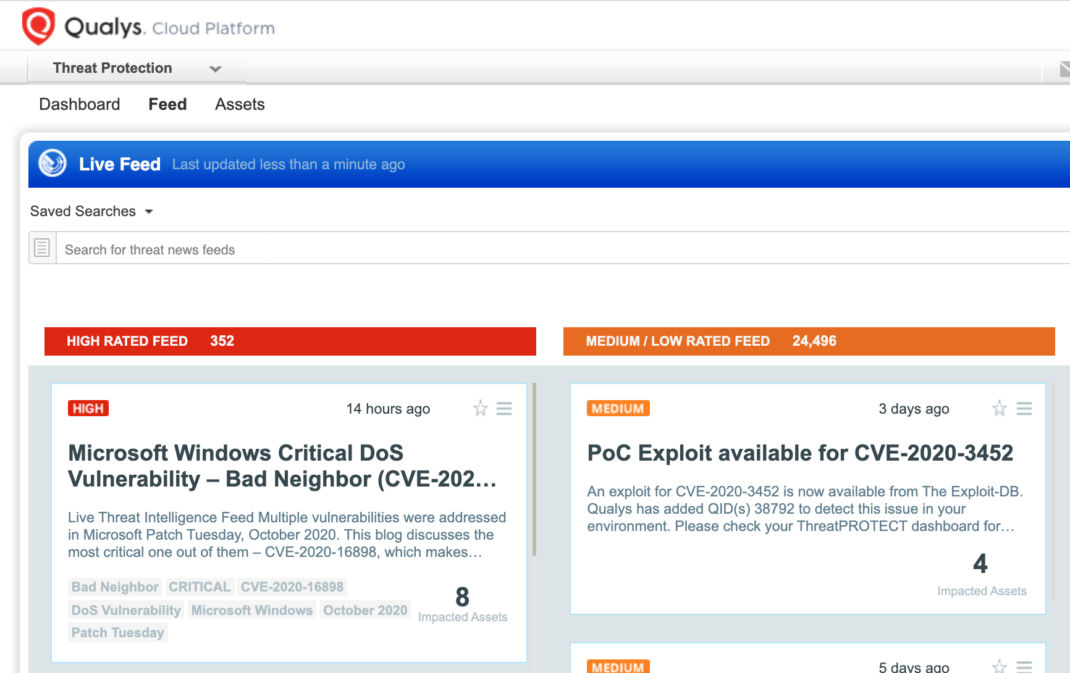
Simply click on the impacted assets for the Bad Neighbor threat feed to see the vulnerability and impacted host details.
Response by Patching and Remediation
VMDR rapidly remediates the Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select “cve: CVE-2020-16898” in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches in one go for hosts grouped together by a tag – CVE-2020-16898.
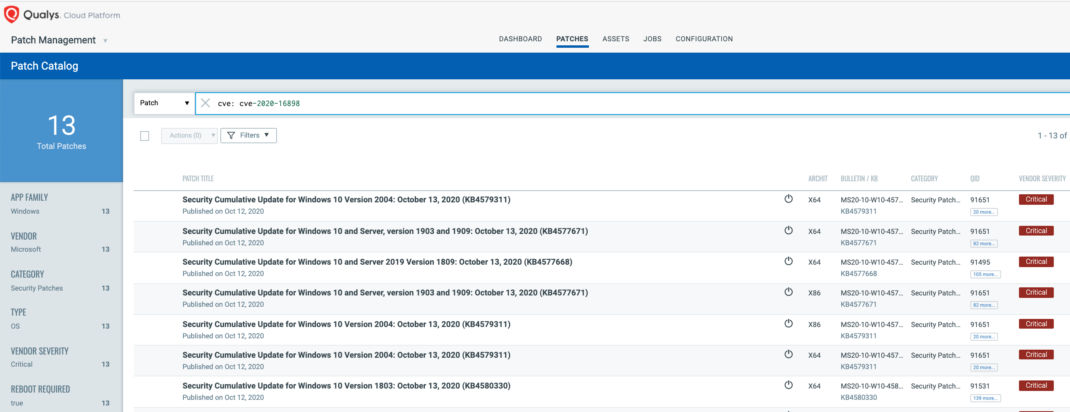
For proactive, continuous patching, you can create a job without a Patch Window to ensure all hosts will continue to receive the required patches as new patches become available for emerging vulnerabilities.
Users are encouraged to apply patches as soon as possible.
Configuration management adds context to overall vulnerability management
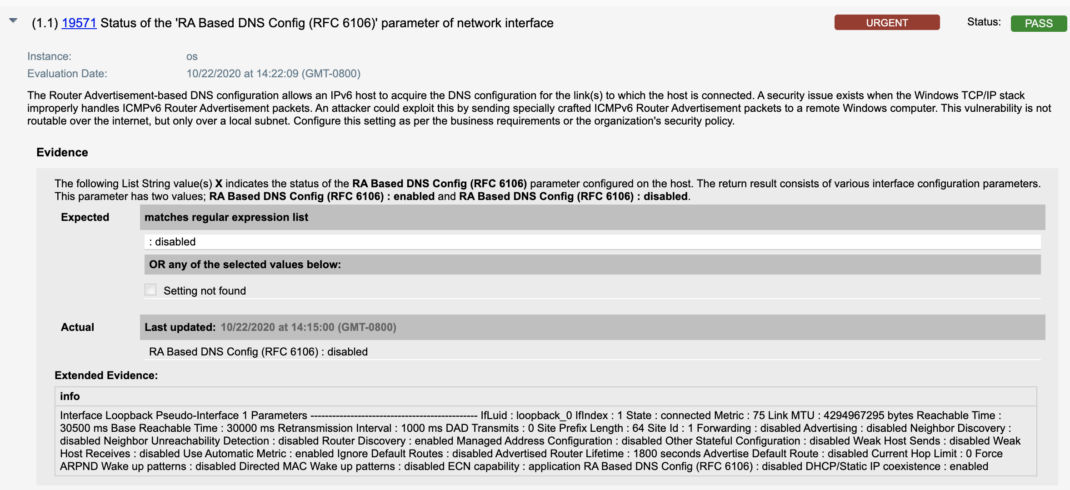
With Qualys Policy Compliance module of VMDR, you can automatically discover the status of RA (Router Advertisement) based DNS Configuration Setting.
- Qualys Control ID – 19571 “Status of the ‘RA Based DNS Config (RFC 6106)’ parameter of network interface” would be evaluated to check the status of RA Based DNS Config is disabled in the result section as shown below:
Mitigation
As per the advisory, the following mitigations should be done apart from patching the installments:
- Disable ICMPv6 RDNSS. (only available for Windows 1709 and above.)
netsh int ipv6 set int *INTERFACENUMBER* rabaseddnsconfig=disable
- Additionally, ICMPv6 Router Advertisements can be blocked or dropped at the network perimeter.
Users are advised to review their Microsoft Windows installations with Microsoft’s October 2020 security advisory mentioned above.
Get Started Now
Start your Qualys VMDR trial for automatically identifying, detecting and patching the high-priority Windows TCP/IP Stack RCE vulnerability CVE-2020-16898.
References
https://github.com/advanced-threat-research/CVE-2020-16898
https://www.mcafee.com/blogs/other-blogs/mcafee-labs/cve-2020-16898-bad-neighbor/
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-16898
