Auto-Discover and Secure Middleware Instances in Your Environment
Enterprise middleware plays a critical role in bringing together many moving parts within an organization, ensuring efficient collaboration, seamless integration and interoperability. A systematic evaluation of middleware architectures is important to thoroughly assess the overall security and compliance posture of an organization. According to the data breach report published by Security magazine, more than 30% of breaches that took place in the 2019 and early 2020 were due to open or unsecured middleware applications.
High profile vulnerabilities, open ports, exposed APIs, misconfigurations or use of default configurations, and various other factors such as keeping unnecessary services enabled or not hiding or masking error information can lead to intrusions and security breaches. In such scenarios, organizations face many challenges in securing the middleware instances in their environment.
Even though the causes that lead to cyberattacks are well known, organizations often fall prey simply because they may not be aware of the weaknesses in their asset management system. Eliminating the “you-don’t-know-what-you-don’t-know” factor would save a lot of organizations from data breaches.
Gain Visibility into Your Middleware Assets
One of the biggest challenges in today’s dynamic environment for security teams is visibility of assets where middleware technologies are running. Qualys Global IT Asset Inventory uses hybrid data collection sensors such as network scanners and cloud agents to acquire real-time, continuous visibility into middleware assets. This revolutionary approach enables the discovery and inventory of all running middleware technologies, even from their custom locations, for multiple instances, with meta data ranging from versions to execution paths. Once discovered, all the assets with running instances of middleware technologies are dynamically tagged, classified and activated for Qualys Policy Compliance for configuration and security hygiene assessment.
The asset tagging functionality of the Qualys Cloud Platform eases the task of discovery, classification and organization of assets.
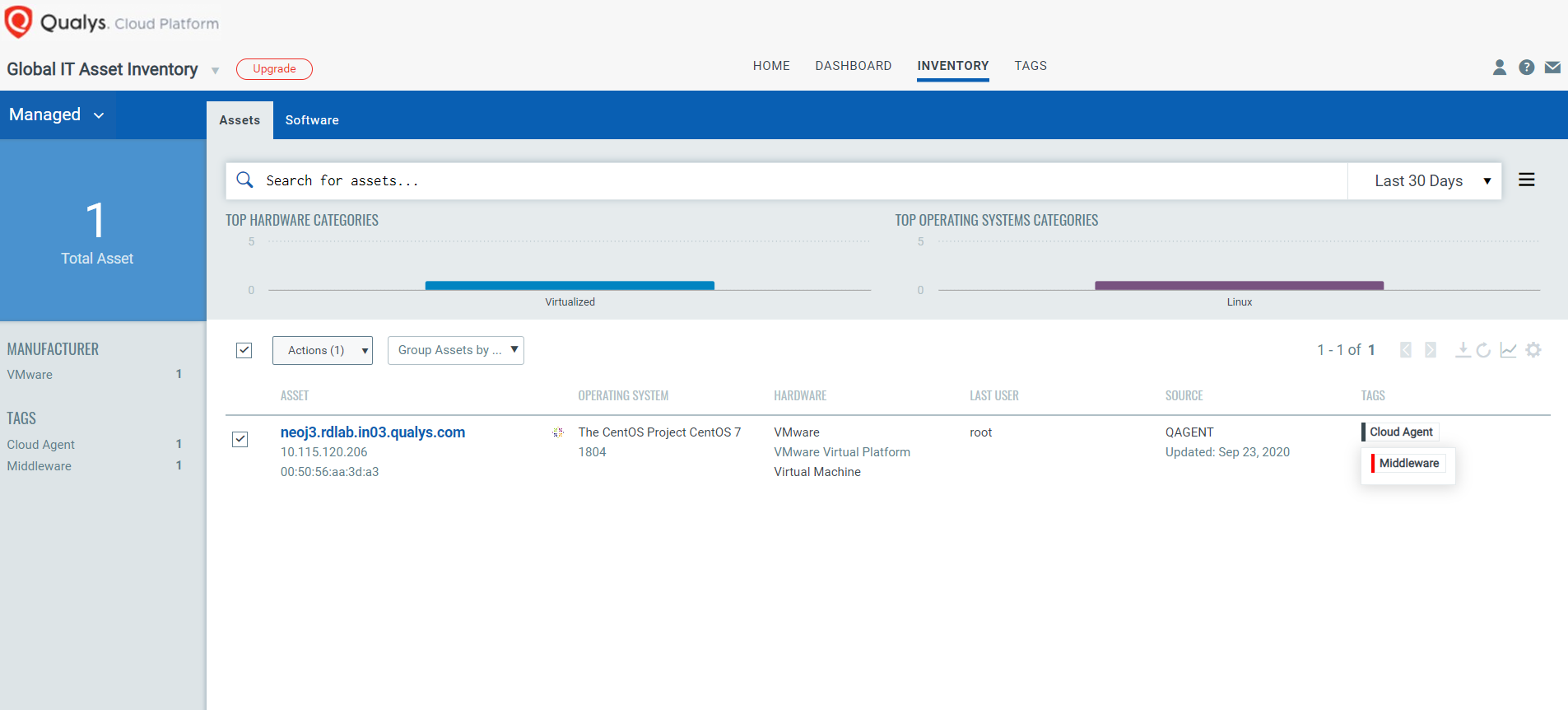
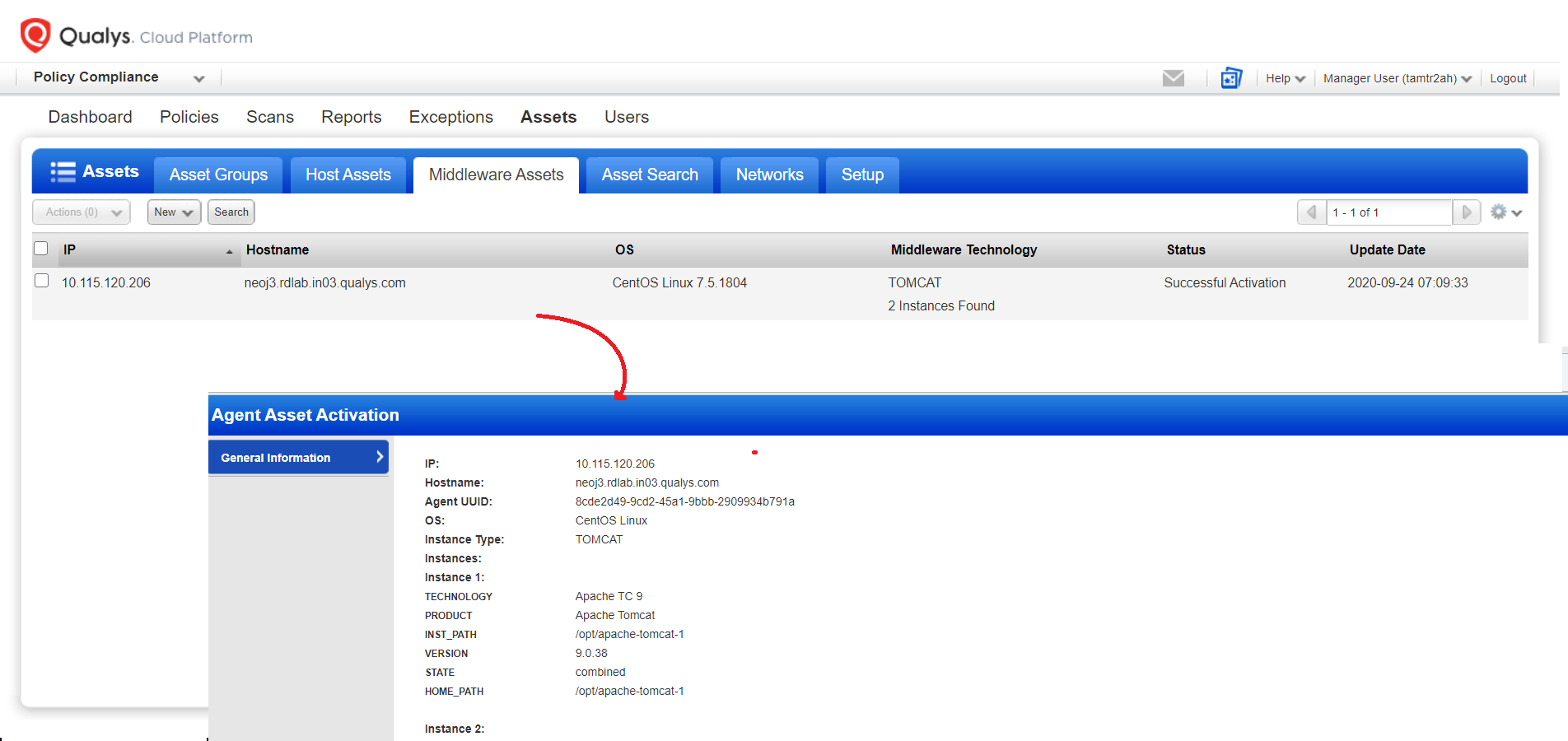
Leveraging the existing Cloud Agent and without requiring any user action, the auto-discovery feature gives you the ability to identify not just the active services or applications (default ports), but extended information about the applications that are installed and running across your network. For example:
- Installation paths and files of applications
- Version information of applications
Assess the Security and Compliance Posture of all Middleware Assets in Your Network
Once you have a comprehensive asset inventory for middleware, the next obvious requirement is to assess them for their security and compliance posture. Qualys Policy Compliance (PC) with its out-of-the-box security policies helps in detecting improperly configured settings& and other security loopholes.
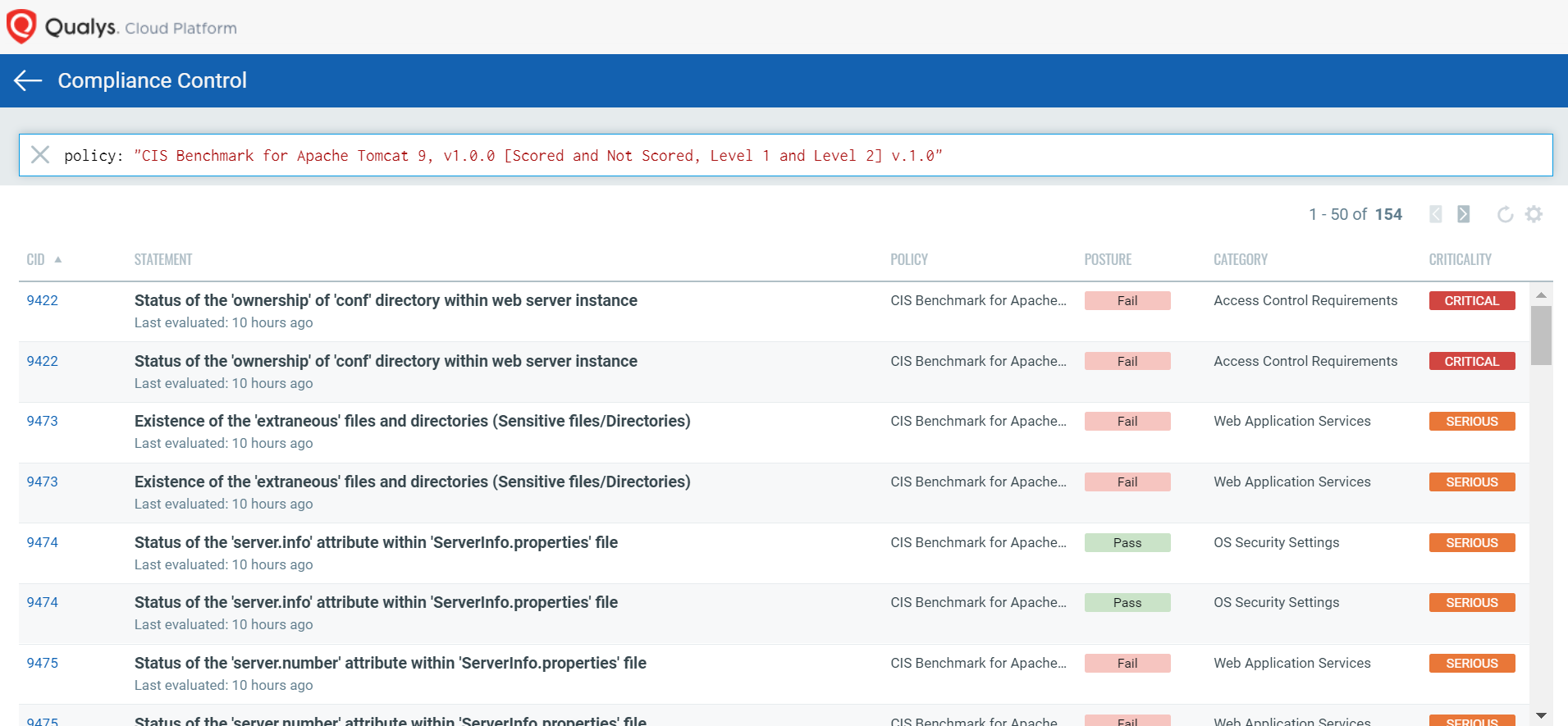
With the help of the meticulously designed CIS-certified policies and additional advanced security controls specifically crafted to secure middleware technologies from malicious attacks, organizations can harden their middleware assets against new threats. You can import the required middleware technology policies from the Qualys Policy Library and assign your asset tags to quickly get visibility into the security configuration posture.
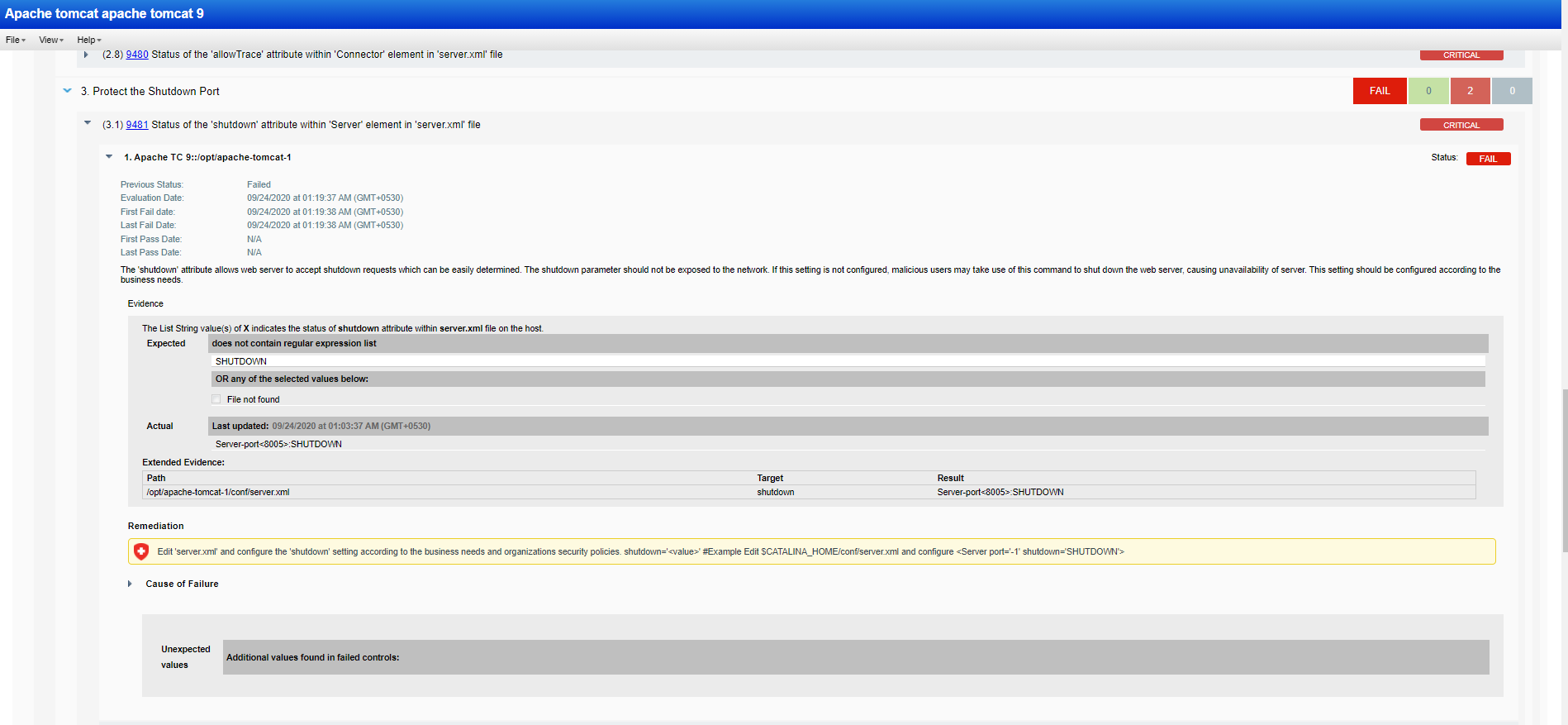
Qualys PC’s support for middleware technologies spans across web servers as well as business collaboration tools, operating systems and browsers to help eliminate any security blind spots of leveraging these technologies. The wide range of support includes web servers such as IBM WebSphere, Apache Tomcat, Apache HTTP Server, WebLogic, IBM HTTP Server, and JBoss EAP, which are supported across various OS platforms. The support also extends browsers and productivity tools such as Microsoft Office applications, which are the most commonly used applications in any organization.
As with remote workforce leveraging multiple browsers and user profiles on the organization’s devices, browser security is becoming critical than ever. Unlike other security and compliance tools out there which only checks the security hygiene of browsers based on default users and registry paths (HKLM), Qualys Policy Compliance automatically collects configuration data of all user profiles using browsers and endpoints along with their custom registry paths (HKU) using cloud agents and evaluates security for all users and settings and with one-click workflow can remediate the misconfigurations as well. This way your security teams can be confident that security for browsers on remote endpoints is hardened.
Dynamically Track Security Hygiene and Compliance via New Dashboard
The new dashboard provides single-pane-of-glass insight into the health and compliance of all endpoints with middleware instances. The enhanced dashboard with ‘Group by’ capabilities enables users to categorize the discovered middleware instances by hosts, which helps in having a better understanding of the vulnerable hosts as well as in tracking their compliance posture over time.
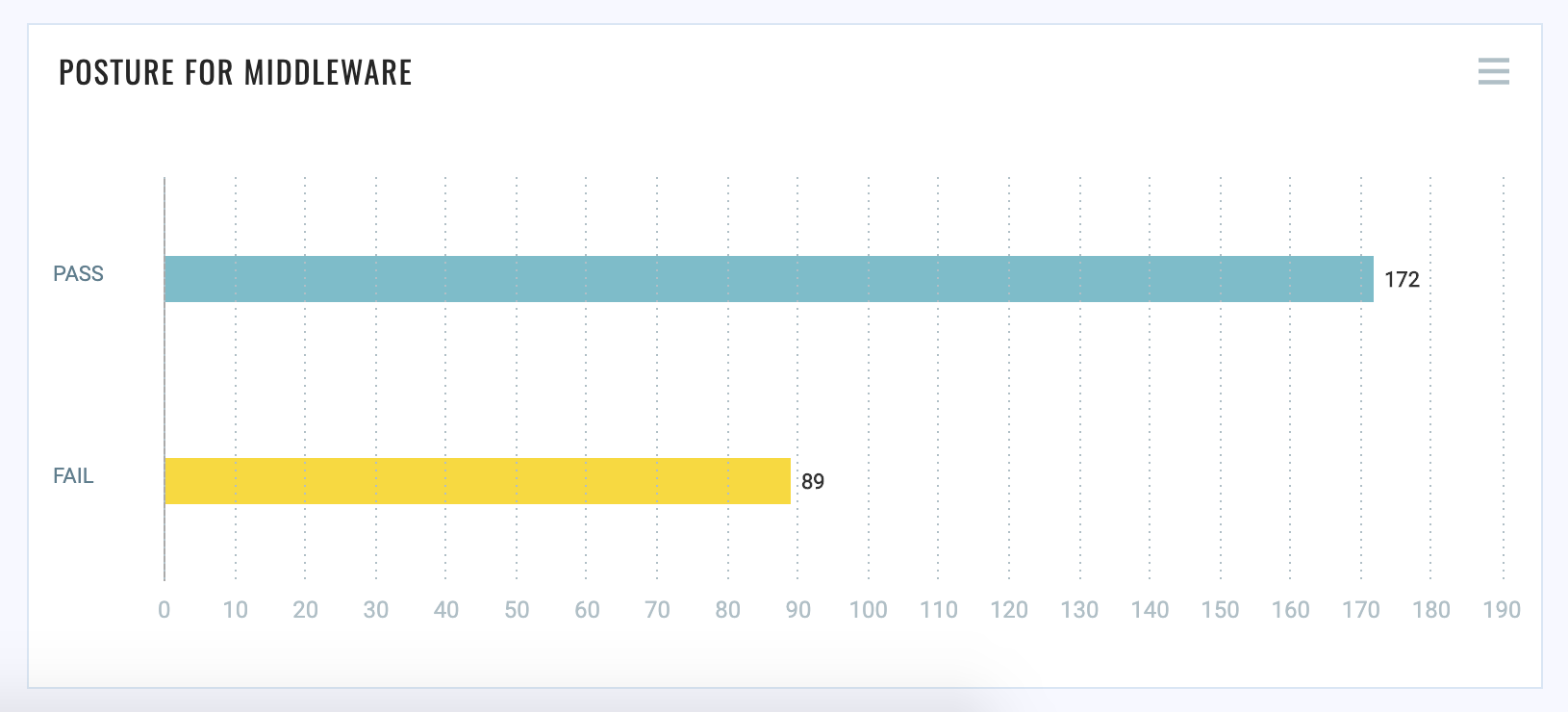
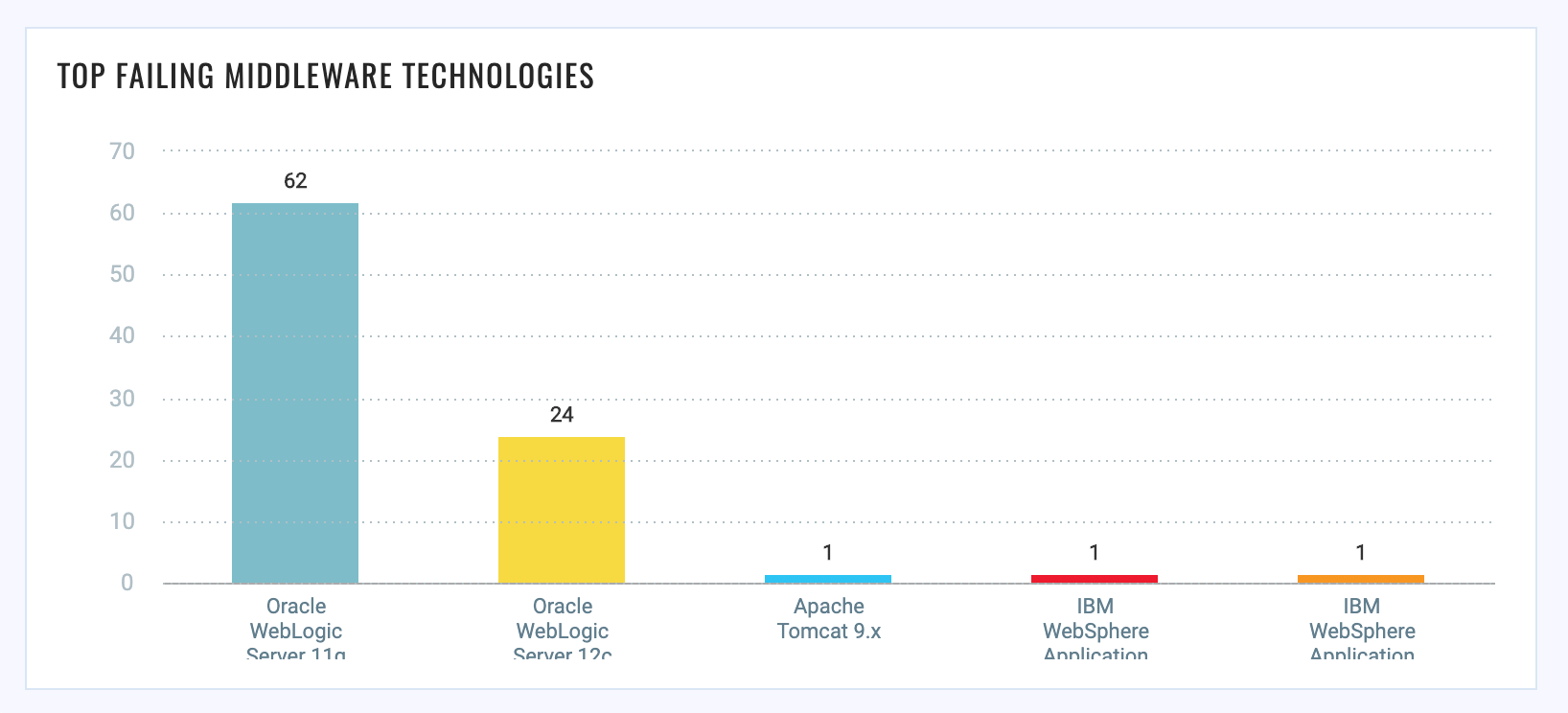
Thus, with the power of the Qualys Cloud Platform and the Qualys Cloud Agent, you can achieve an end-to-end solution right from auto-discovery of assets to creating conclusive reports about the posture of your middleware assets.
Conclusion
Some form of middleware is always being leveraged in all organizations – whether they are integrating or collaborating across divergent teams. Being well acquainted with the challenges that enterprises have to deal with, Qualys Policy Compliance has ensured that its support for middleware technologies is strengthened by granular details. With the help of its CIS-certified policies and system-defined controls for middleware, Qualys PC eliminates the probable security soft spots that often go unnoticed.
Very soon, Qualys will also add infrastructure-as-a-code or custom script-driven tools for remediation that will help address middleware misconfigurations from the UI itself. This unique solution will enable remediation for all auto-discovered active instances for weak settings in default as well as custom paths and significantly shrink the attack surface.