Qualys Policy Compliance Plugin for Jenkins Now Available
Various factors may introduce vulnerabilities in a product during its lifecycle, resulting in a drift from the required compliance status. Hence, it is of utmost importance that security is baked into the product at every stage of development and possibilities of security gaps are ruled out. CI/CD integration in the product lifecycle establishes a consistent and automated way to build, package, and test applications; thereby, ensuring that the security parameters are a part of each delivery.
The new Qualys Policy Compliance Scanning Connector, a native plugin for Jenkins, empowers DevOps teams to automate secure configuration assessment into their CI/CD processes. By automating and integrating configuration assessment in this manner, application and workload security is accomplished earlier in the CI/CD pipeline. The DevOps teams can ensure that golden images conform to organizational, industry, regulatory and other security standards and eliminate security flaws originating from insecure configuration before they are ever exposed in production.
Safeguard Your DevOps Pipeline with Qualys
Integrating Qualys Policy Compliance in addition to vulnerability scanning in the DevOps CI/CD pipeline provides comprehensive assurance of systems’ security and integrity from the start. As developers start work on building images, they can automatically assess the images for compliance. Assessment is done for the underlying operating system along with any middleware application servers running on top of it. Any identified misconfiguration, vulnerabilities, and application weaknesses must be resolved before the images can be passed for production. Once approved, these images can be replicated in the production environment. Compliance scanning in the CI/CD pipeline ensures that baseline/golden images are hardened before being used to spin up workloads.
Workloads that get spun up using the golden images either on premises or in the cloud can be continuously monitored for changes by baking in the Qualys Cloud Agent into the images.
User-Friendly Design and Features to Facilitate Automation
The plugin is available in Jenkins under Manage Plugins and is easy to configure and use. It supports both pipeline and freestyle projects. A Qualys Policy Compliance subscription with API access is required. The user credentials are saved after the first login. Even the Pass/Fail criteria for builds is simple and can be specified with the help of the options provided. A build can be failed by state and criticality of the control and authentication result. A failed build can be fixed from Jenkins without users having to log in to the Qualys console.
Users can choose which Qualys shared platform your organization is using, and the correct URL will automatically be used. We currently have seven shared platforms around the globe. Please note if your organization is using a Qualys PCP (private cloud platform), then you’ll still need to enter the API server URL.

Discover & Assess Middleware Application with OS Scan
The plugin leverages the Policy Compliance APIs to automate assessment functions. This means that you don’t need to know the intricacies of launching scans. After entering valid Qualys credentials, the plugin automatically retrieves the list of applicable Option profiles, and you can just select the applicable option profile and then choose the desired policies including middleware applications. Auto-discovery is performed for supported technologies during the scan. You can also optionally create a specific authentication record. You don’t need to enter the ID, just select the desired one from the list.

Fail the Build Automatically
One of the best new features of the plugin is the ability to specify pass/fail criteria for the build based on scan results. You can specify the criteria for a build to be failed, which can be easily configured based on a combination of control state and criticality as shown in the following screenshot.
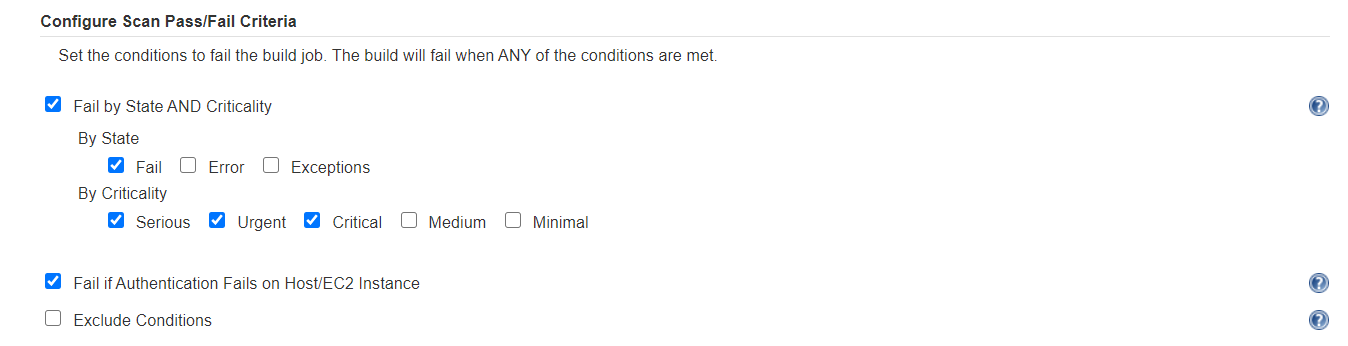
Scan Results, in the Plugin
Once the scan has finished, the plugin provides an option to view summary-level scan results. You’ll quickly be able to see the overall compliance, scan duration, whether the scanner successfully authenticated to the app, as well as failed count for each severity level. You’ll also see the specific criteria that was triggered (if any) which caused the build to fail. Easily navigate to the control that caused the build to fail by simply clicking on the number in the Controls causing Build Failure widget.

To see all the Qualys CIDs found during the scan, click All Controls on the left-hand panel. This presents the data in tabular format, which includes the pass/fail status of the controls, critical missing values, if any, and so on. For detailed scan results, including specifics about the control including remediation info, click the link on the Summary page to open the Scan Report (you will need to authenticate to the Qualys platform).
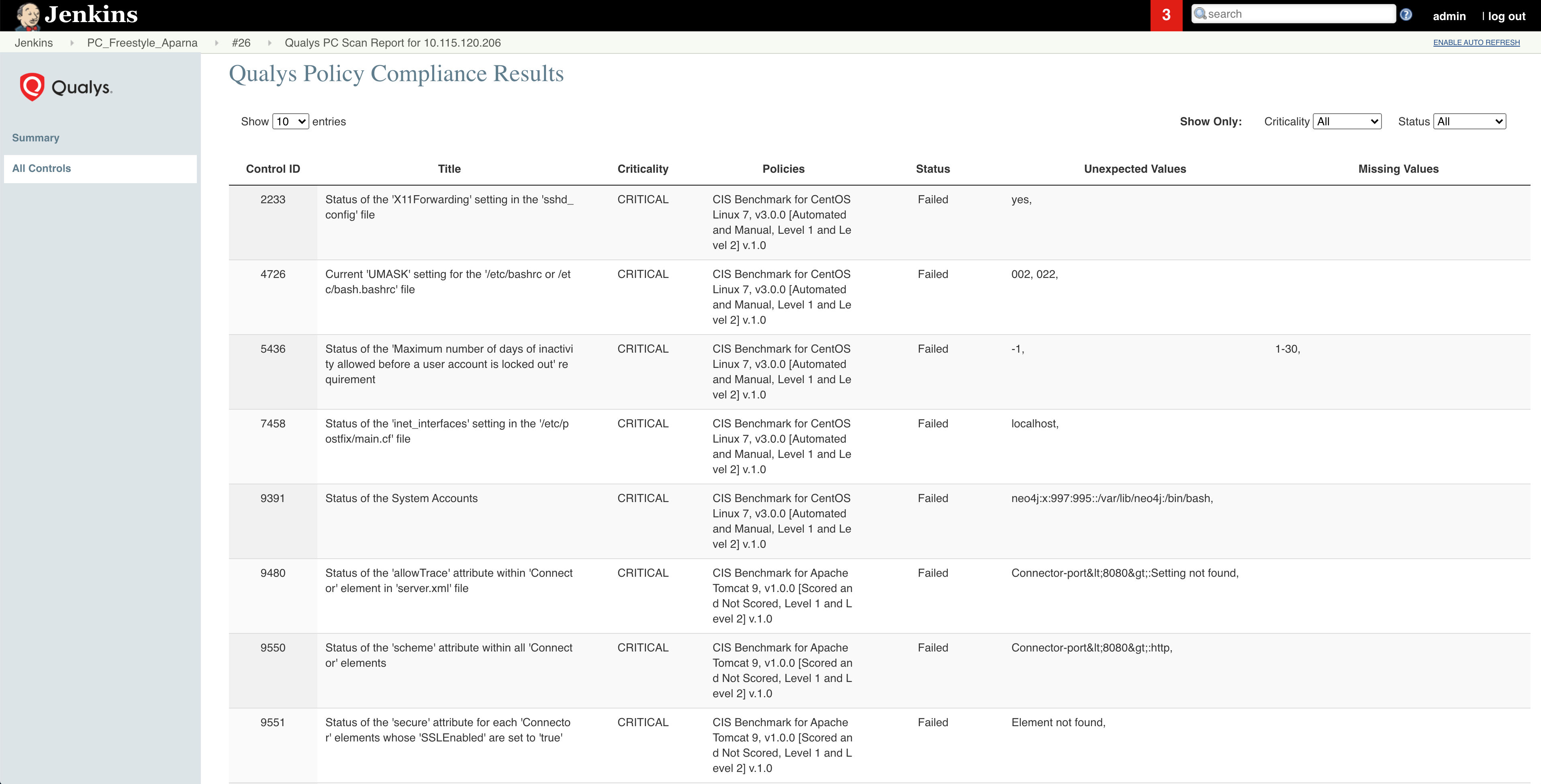
For more information, refer to Qualys Policy Compliance Scanning Connector for Jenkins User Guide.
Security in DevOps
The rapid pace of software development and organizations’ transition to a DevOps model require innovative approaches to security. With the Qualys Policy Compliance plugin, organizations can ensure that all security aspects are taken care of during entire product lifecycle starting from development of the base image through its deployment.