QID Spotlight: Enhanced Oracle Java Discovery

Update May 3, 2021: Qualys has released new Information Gathered QID 45488 to report running Oracle Java instances. This QID will help customers to identify Oracle Java instances which are actively running and in use at the time of remote scan or agent scan on Unix/Linux operating systems.
QID 45488: Running Oracle Java Instances Enumerated
– Signature Version: VULNSIGS-2.5.168-2 and later
– Manifest Version: 2.5.170.5-4 and later
Update March 5, 2021: To help with overall risk assessment, the reporting of Oracle Java QIDs is being updated to indicate if the detected Oracle Java instance was found via the default or enhanced discovery method. See details below.
Update December 15, 2020: This blog is updated with the FAQ section for customers to get more insight into QID details.
Original Post: Securing Java instances has become critical for organizations because Java’s wide use as an open-source component in applications has made it a captivating target for attackers.
According to a recent research, Java is the most common programming language used by developers with 90% of all Fortune 500 companies making use of the technology. It has therefore become critical for organizations to identify and secure Java installations in their environments.
Building on Qualys’ ability to discover and secure middleware technologies, a recent update to the vulnerability signature library adds discovery of Oracle Java instances in non-standard locations. Qualys now provides comprehensive visibility into all Oracle Java instances in both standard and non-standard locations, their current vulnerabilities, and what you must do to protect them.
Current Capabilities and Enhancements
One of the biggest challenges in today’s dynamic environment for security teams is identifying applications installed in non-standard locations.
The current method for discovering Java in Qualys VMDR QID signatures is based on detecting installation via the PATH environment variable. Although this approach provides customers accurate and quick discovery of a wide variety of technologies, it has limitations with respect to finding applications in non-standard locations.
With the enhanced discovery of Oracle Java instances, VMDR QID signatures add the capability to discover Oracle Java instances using OS utilities like ‘find’ (to discover Java binaries on the file system), ‘locate’, ‘whereis’, ‘which’, and ‘update-alternatives’ (to identify the system paths for Java), and by checking if a running process was started using Java. We then extract the underlying version after verifying the installation is an Oracle Java instance. The enhancement is optimized to consider timeouts so that it doesn’t negatively impact systems.
The following existing QIDs are being updated as part of this enhancement: 119956, 120274, 120443, 120443, 120604, 120799, 120832, 45188, 120879, 120970, 121061, 105490, 121279, 121515, 121712, 122007, 122362, 122741, 123168, 123519, 105618, 123714, 124169, 124567, 124882, 370087, 370161, 370280, 370371, 370469, 370610, 45285, 45286, 370727, 45301, 370887, 105750, 371079, 371265, 371528, 371749, 105801, 372013, 372163, 372333, 372508, 373156, 373540, 105412
Gain Visibility into Oracle Java Assets
Start by identifying middleware technologies running in your environment. Qualys Global IT Asset Inventory allows you to gain visibility into Oracle Java assets using hybrid data collection sensors such as network scanners and cloud agents.
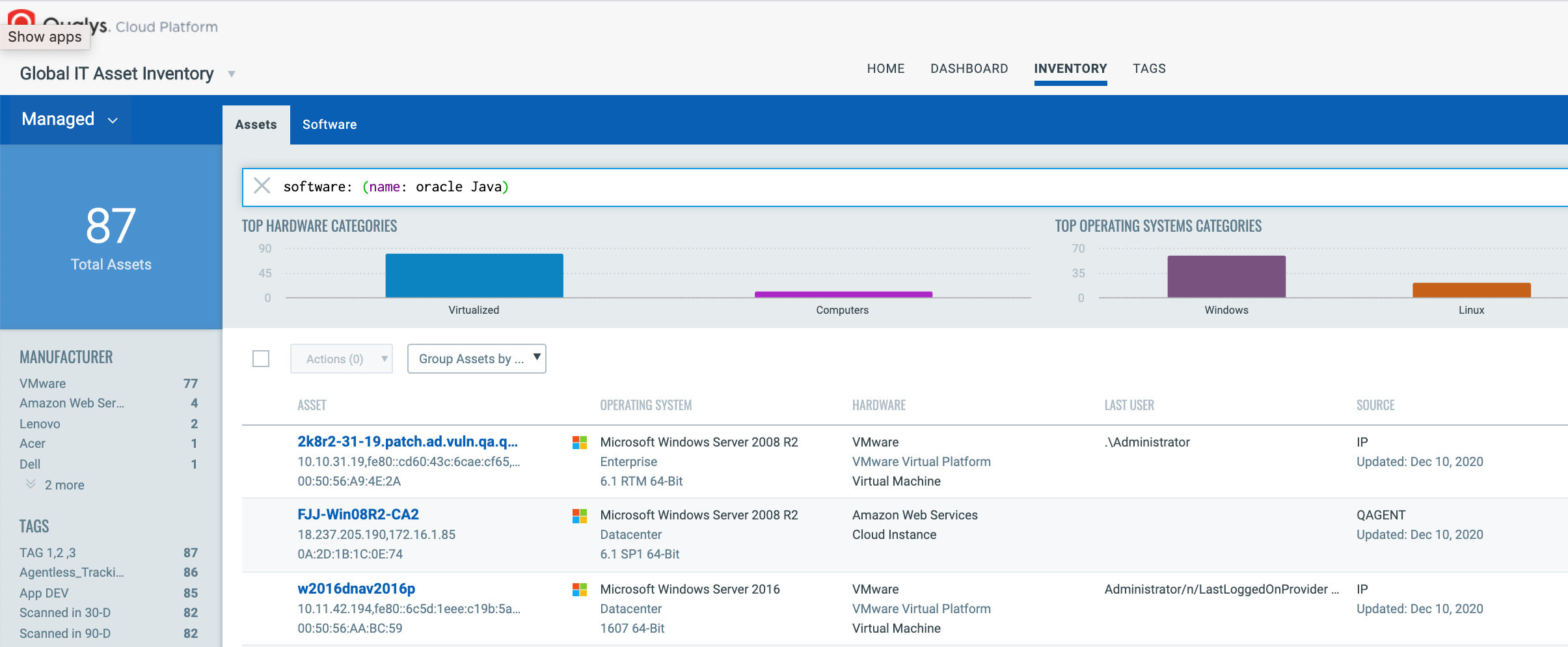
Once the hosts are identified, they can be grouped together with a ‘dynamic tag’, let’s say “Oracle Java”. This automatically groups existing hosts running Oracle Java as well as any new hosts running Oracle Java that spin up in your environment. Tagging makes these grouped assets available for querying, reporting and management throughout the Qualys Cloud Platform.
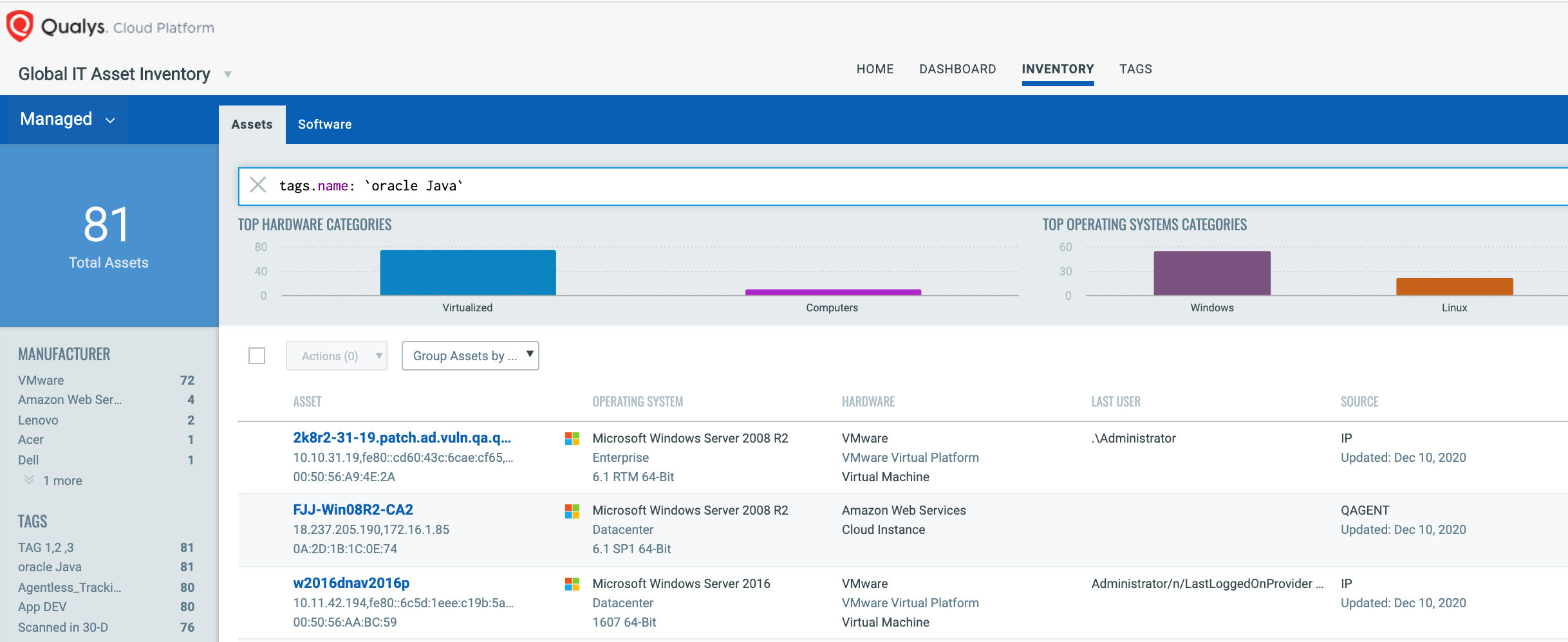
Discover Oracle Java Vulnerabilities
You can see all your impacted hosts for Oracle Java vulnerabilities for existing QIDs using this QQL Query:
vulnerabilities.vulnerability.qid: [119956, 120274, 120443, 120443, 120604, 120799, 120832, 45188, 120879, 120970, 121061, 105490, 121279, 121515, 121712, 122007, 122362, 122741, 123168, 123519, 105618, 123714, 124169, 124567, 124882, 370087, 370161, 370280, 370371, 370469, 370610, 45285, 45286, 370727, 45301, 370887, 105750, 371079, 371265, 371528, 371749, 105801, 372013, 372163, 372333, 372508, 373156, 373540, 105412]
Customers may also notice some older closed detections may reopen as more Oracle Java installations are discovered on their hosts.
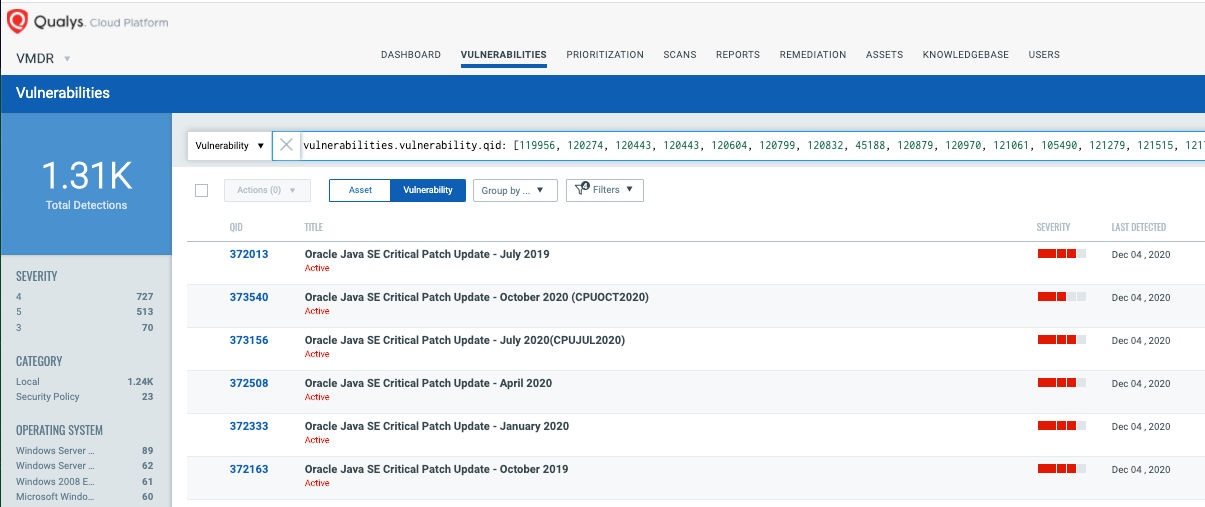
Oracle Java QID changes are available in vulnerability signature version VULNSIGS-2.5.54-4 and above.
For customers using scanning, authenticated scanning is required to access system data used in this detection. For customers using Qualys Cloud Agent, it is required to use Cloud Agent version 2.4.0.x or later running manifest version 2.5.54.3-2 and above.
In addition, Qualys released IG QID 48157 to help customers identify which assets have Oracle Java instances running in their environment along with multiple Java instance versions on those assets.
QID 48157 : Oracle Java Version Detected
Previous Reporting of Oracle Java QID 371528
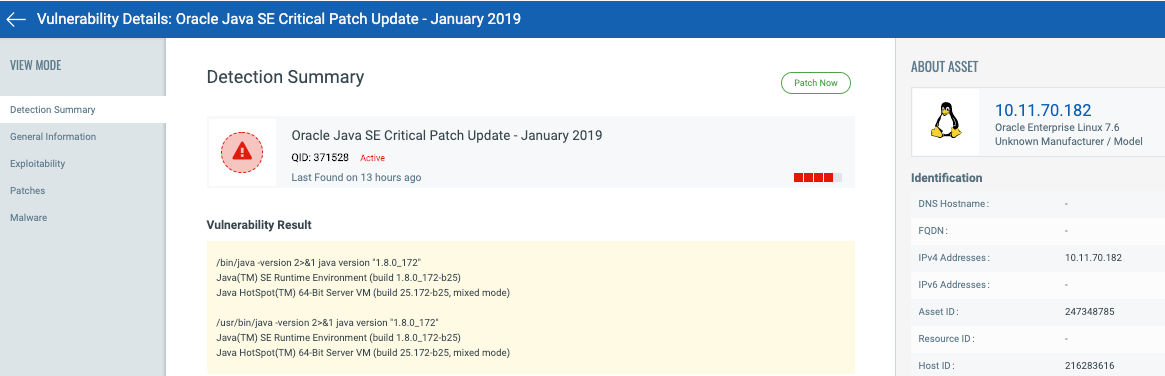
New Updated Reporting of Oracle Java QID 371528
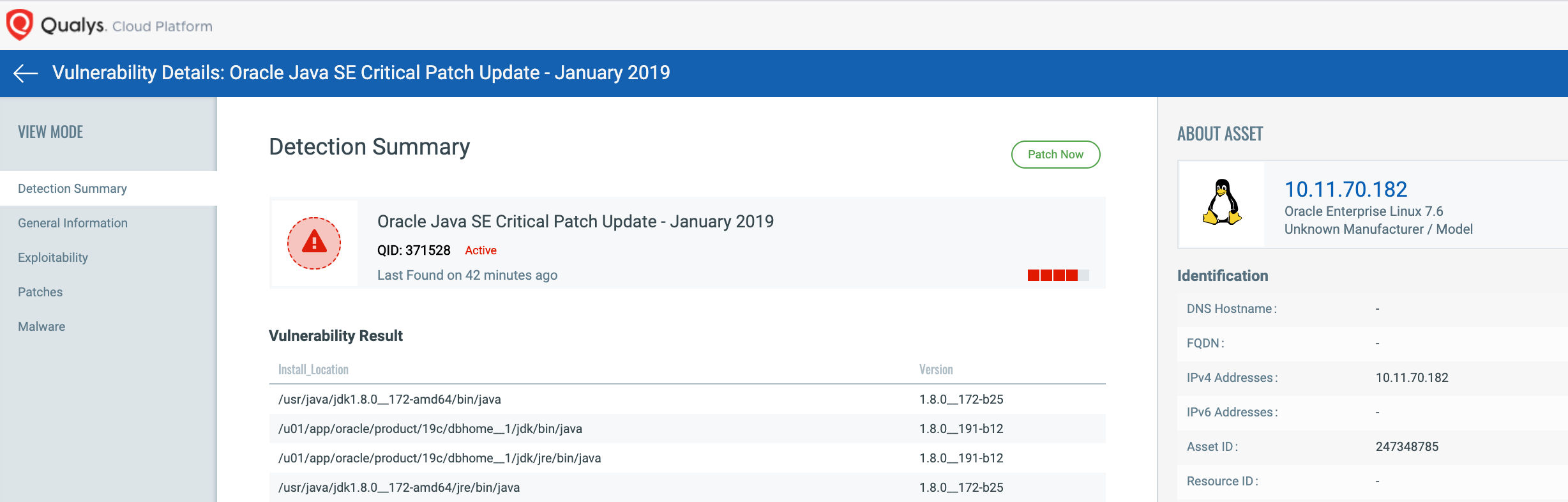
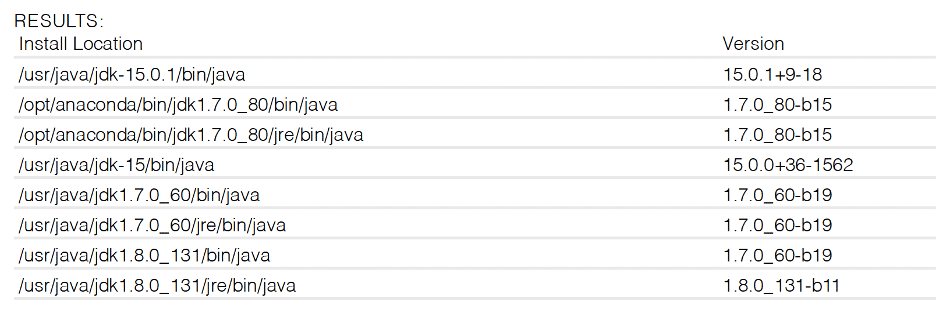
As seen above, the new reports show additional Oracle Java instances and more detail about those instances. Instead of showing two installations (i.e. the sym links /usr/bin/java and /bin/java) in prior reports, the updated reporting now shows four Oracle Java installations and includes install location and Oracle Java version.
Get Started Now
Start your Qualys VMDR trial to automatically identify, detect and patch vulnerabilities detected in all of your Oracle Java instances.
Learn more about Oracle authenticated scanning.
Frequently Asked Questions (FAQ):
Q: What caused the increase in Oracle Java detections?
A: On December 10, the Qualys research team released an update to its signatures to detect Oracle Java instances installed in non-standard locations. As a result of this change, customers saw an increased number of Oracle Java vulnerabilities being reported in their environment negatively impacting their year-end compliance posture reporting.
Q: Why were the changes implemented?
A: The Qualys research team updated Oracle Java vulnerability detection logic to give our customers better visibility into vulnerable instances of Oracle Java installed in non-standard locations, which were previously difficult to identify.
Q: Which Oracle Java QID’s were impacted by this update?
A: The following QIDs were impacted as part of this change:
119956, 120274, 120443, 120443, 120604, 120799, 120832, 45188, 120879, 120970, 121061, 105490, 121279, 121515, 121712, 122007, 122362, 122741, 123168, 123519, 105618, 123714, 124169, 124567, 124882, 370087, 370161, 370280, 370371, 370469, 370610, 45285, 45286, 370727, 45301, 370887, 105750, 371079, 371265, 371528, 371749, 105801, 372013, 372163, 372333, 372508, 373156, 373540, 105412
Q: What options are available to exclude the Oracle Java QID’s from reporting?
A: Two options to exclude QID’s.
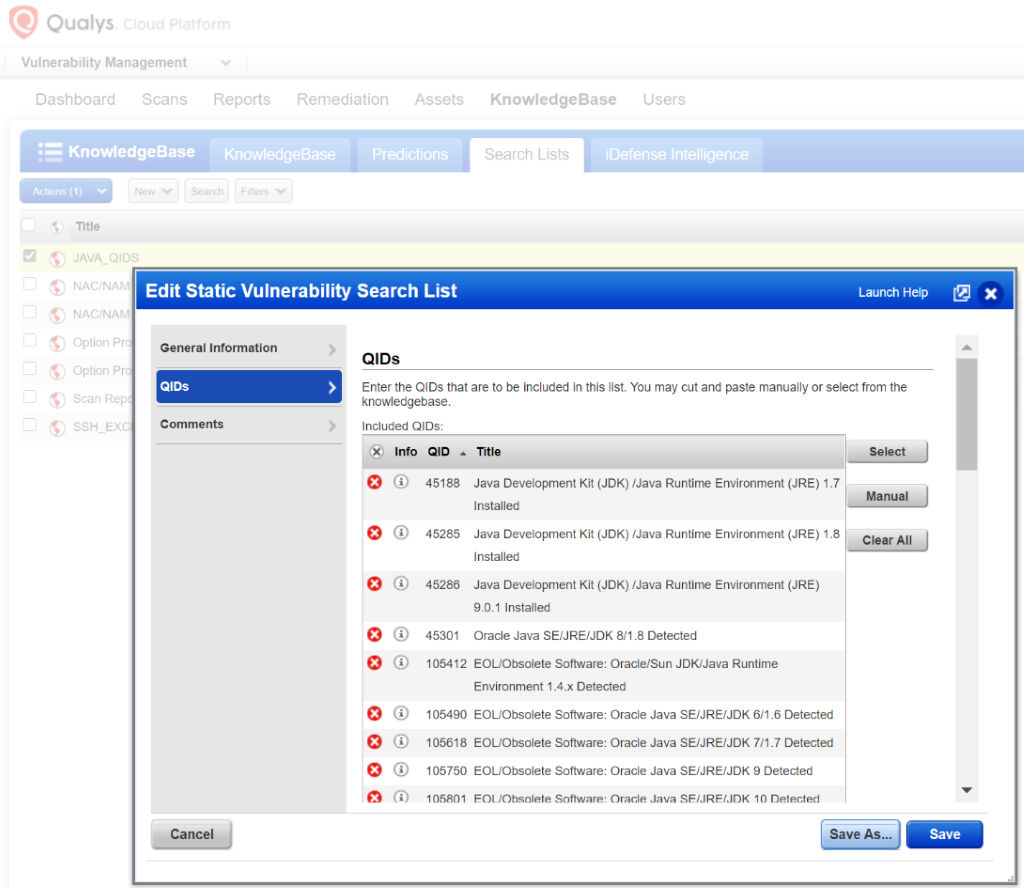
- Use a Static Search List to filter out Java QID’s from reporting.
In the next section, we’ll cover multiple options to filter out the list of Java QID’s impacted by this update.
Below is an example of where to create your search list:
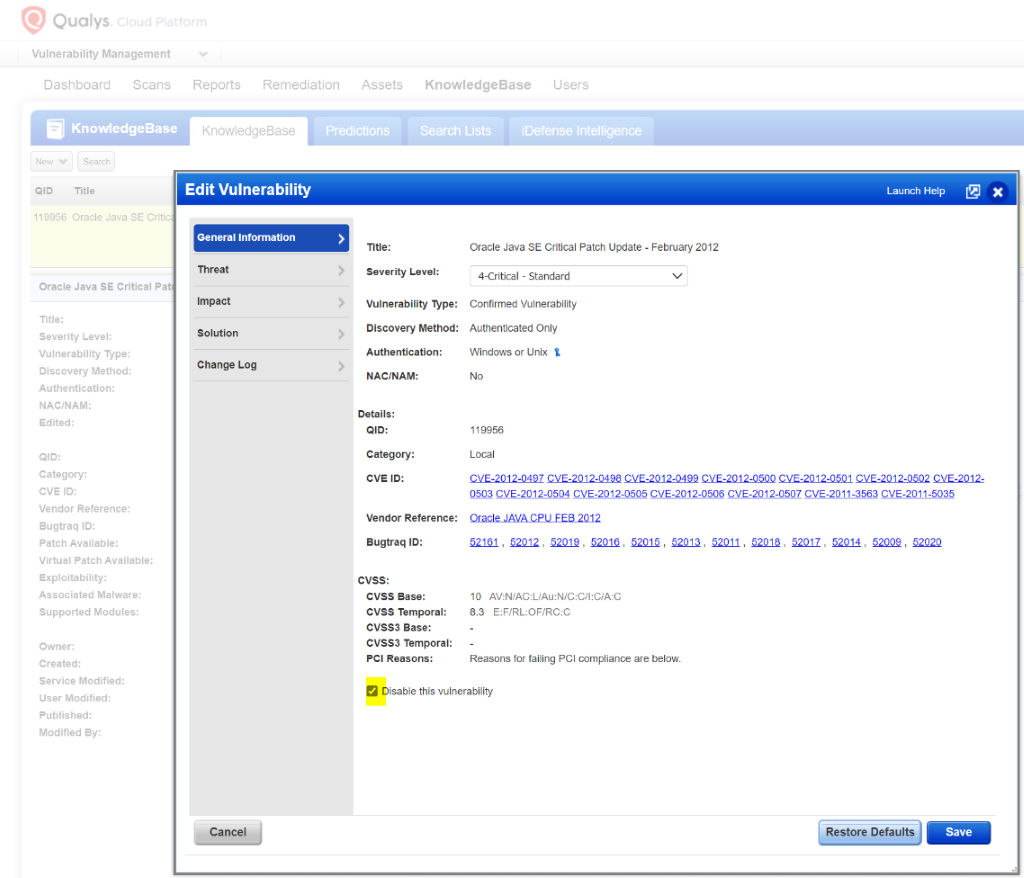
- Temporarily disable the list of Java QIDs in the KnowledgeBase.
a. All Reporting through UI, and API will exclude the QID’s unless they are explicitly included.
b. Enable the QID’s once you are ready to process data.
c. Below is an example of temporarily disabling the vulnerability.
Q: What options in reporting and widgets are available to identify or filter out these detections?
A: There are multiple options to identify and filter out Oracle Java detections.
- Filter detections using Exclude QIDs from the reporting UI
Customers can choose to temporarily exclude findings from these QIDs using Report Templates and search lists to reduce impact on end of year reporting metrics.
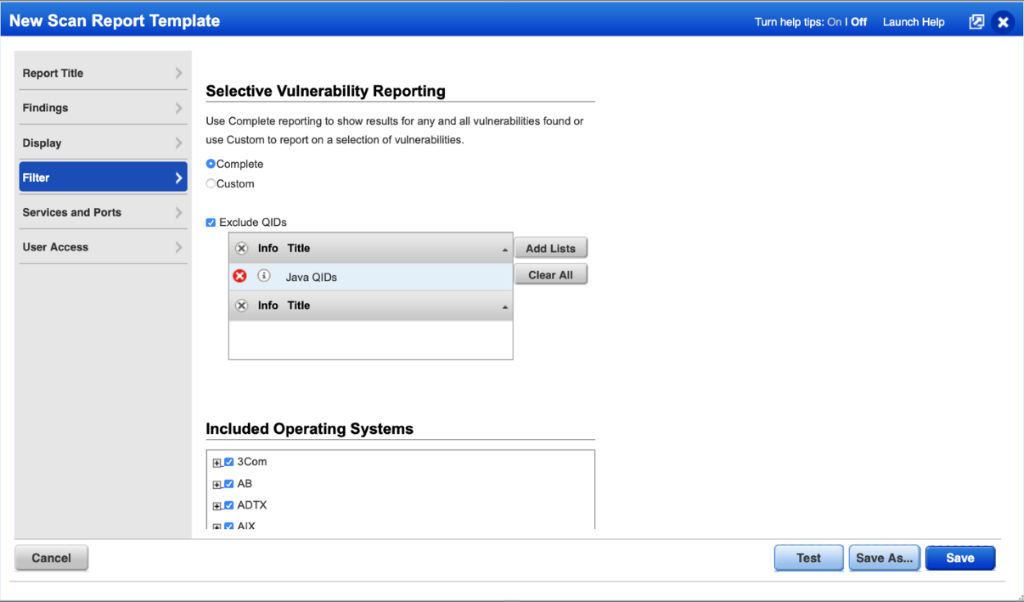
- Filter detections using the API
Use the API to call the report created above to exclude the QIDs.
https://www.qualys.com/docs/qualys-api-vmpc-user-guide.pdf
(refer to pg. 475 & 513)
- Use Remediation Policies and Report Templates to exclude QIDs
Review the following videos to exclude the QIDs using remediation policies.
– Remediation Policies
– Report Templates
Q: What changes will be made to Oracle Java QID reporting in March 2021?
Further expanding on the enhancements to Oracle Java QIDs described above, Qualys is updating its reporting to add visibility into the type of detection that identified the Oracle Java instance.
Customers will be able to identify if an Oracle Java instance was detected via Default discovery, which indicates it was found in a standard location using the original detection method that checks the PATH system variable; or via Enhanced discovery, which indicates it was found in a non-standard location using the new method introduced in December 2020.
The updated reporting will help in risk assessment by making it clear to security teams which Oracle Java instances were newly identifiable since the introduction of enhanced discovery.
Reporting for Oracle Java QIDs in the current format
Reporting for Oracle Java QIDs showing the new Detection Type column
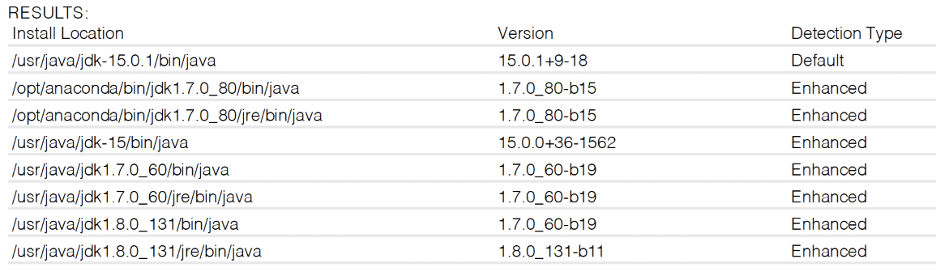
As seen in the above screenshots, a new “Detection Type” column will be added in the reporting section of the QIDs. Depending on the method of discovery, each instance will be classified with one of the below values:
- Default refers to the original detection logic before December 2020 that checks via the PATH variable.
- Enhanced refers to the new detection logic added in December 2020 and checks in non-standard locations.
Update March 23, 2021: These changes are live on all shared platforms:
- Vulnerability signature version: VULNSIGS-2.5.140-2
- Manifest version: lx_manifest-2.5.140.3-2
- Cloud Agent version: 2.4.0.x or later
Q: How can I track these changes through a Dashboard in VMDR?
A: With Qualys Unified Dashboard, you can track Java vulnerabilities, impacted hosts, their status and overall management in real time. Enable trending so you can keep track of these vulnerability trends across your environments.
Dashboard: Java QIDs and All Java Vulnerabilities!
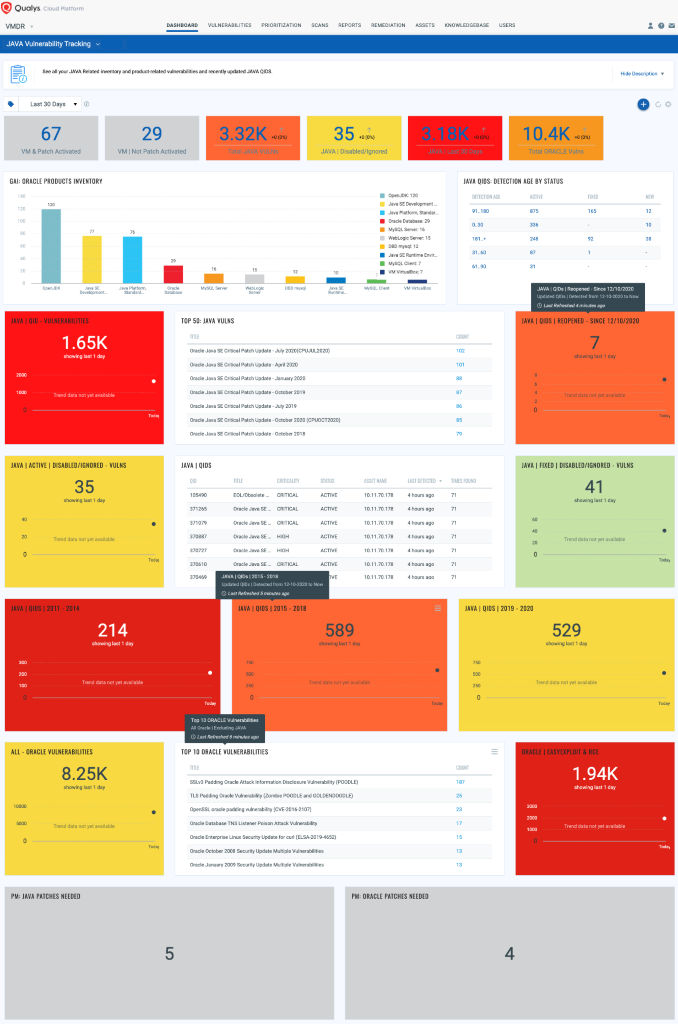
Q: How would this change impact status of QIDs detected with old detection logic?
A: The QID status will continue to follow the standard QID status workflow.
Q: What impact would this change have on Java related QIDs on assets?
A: As a part of this change, newly ran reports could show more vulnerable Oracle Java instances than earlier. Customers may also notice some older closed detections may reopen as more Oracle Java installations are discovered on their hosts.
Q: Is it likely that with the enhanced discovery, scans will take longer and customers may need to adjust their scan schedules?
A: Yes it is possible, because we run find commands to discover Java instances on non-standard locations.
Q: Would this reopen older Oracle Java related QIDs?
A: Yes, if there are vulnerable instances on the hosts.
Q: Would I see a QID posted even if I have applied the patch ?
A: QID would be posted as long as there is at least one instance of Oracle Java which is not patched.
Q: I had applied a patch for a Oracle Java QID long time ago. Why is the QID now reopened?
A: With Oracle Java Extended Discovery we were able to identify more instance on the host and found at least one Oracle Java instance that was not patched.
Q: How do I resolve the Issue?
A: Please navigate to the “Vulnerability Result” section and check for all the Oracle Java “Install Location” paths. Apply the patches for vulnerable instances to resolve this issue.
Q: Were additional CVE’s added to old Oracle Java QIDs?
A: No CVEs were added/removed from QIDs as a part of Oracle Java Extended Discovery.
Q: Why is Oracle Java Enhanced Discovery logic added now?
A: The Qualys research team is continuously looking for better ways to identify and accurately report vulnerabilities. As part of this effort, we updated Oracle Java vulnerability detection logic to give our customers better visibility into vulnerable instances of Oracle Java installed in non-standard locations.
Q: How does the new Oracle Java Enhanced Discovery logic work?
A: These are the steps:
- Discover all Java instances (including non-standard locations) on the host. The discovery of Java instances is done using commands such as ‘find’, ‘locate’, ‘whereis’, ‘which’, ‘update-alternatives’, and checking for running Oracle Java processes.
- Once Java instances are discovered on the host, vendor information (Oracle) is verified using Java lib files ex: ‘<Java_Home>/lib/rt.jar’, and more.
- Finally, the Oracle Java version is extracted from the Java binary.
Q: How do I report inaccurate results?
A: File a support request, and inform your TAM as well.
Q: How will Qualys notify customers of similar changes in future?
A: Qualys research team will implement a 15-day notification process for any bulk modification of QIDs or significant changes to underlying QID detection logic for major applications.
See all notifications: https://notifications.qualys.com
Q: Will Qualys add similar detection support for other technologies?
A: Yes. Qualys research team plans to add similar detection capabilities for other technologies. The team will provide a 15-day notification before such changes are made live. In addition to that we will allow customers to opt-in into enhanced detection capabilities in future.
Hello Animesh, great article thank you.
Could you confirm to me whether there is any active supersedence with Java QIDs, as we typically see older QIDs drop off our lists as each new QID is released, but this year the April 2020 QID for Java SE seemed to stick, despite the fact that the July 2020 QID came along. Thanks
Hi,
What about others JVM (eg. openjdk, ibm j9, azul zing..)? There’s an “Enhanced Discovery logic” as the oracle one or not?
regards,
Fabrizio
Hello Animesh
The biggest challenge Oracle Java Extended Discovery it also reporting for the Oracle Database Software Binaries where JAVA/JDK/JRE are part of installations – Is there any Vulnerability Score or any separation to identify the associated risks – In normal IT industries support teams associated with DB will DBA teams and rest of the installation paths are managed by UNIX and other respective infrastructure teams – the challenge is creating respective treatments or remediation plans for reported vulnerabilities
Thanks
Hello Animesh
The biggest challenge Oracle Java Extended Discovery it also reporting for the Oracle Database Software Binaries where JAVA/JDK/JRE are part of installations – Is there any Vulnerability Score or any separation to identify the associated risks – In normal IT industries support teams associated with DB will DBA teams and rest of the installation paths are managed by UNIX and other respective infrastructure teams – the challenge is creating respective treatments or remediation plans for reported vulnerabilities
Thanks
Pavan
This is great article, we have systems where multiple QID’s are there for same file at same location
And qid are ranging from 2015 to 2022, for it should only report one qid for latest as all old are same and should get supersceded with latest patch. Please help why multiple qid for same file from same location
Thanks