Securing Red Hat Enterprise Linux CoreOS in Red Hat OpenShift with Qualys
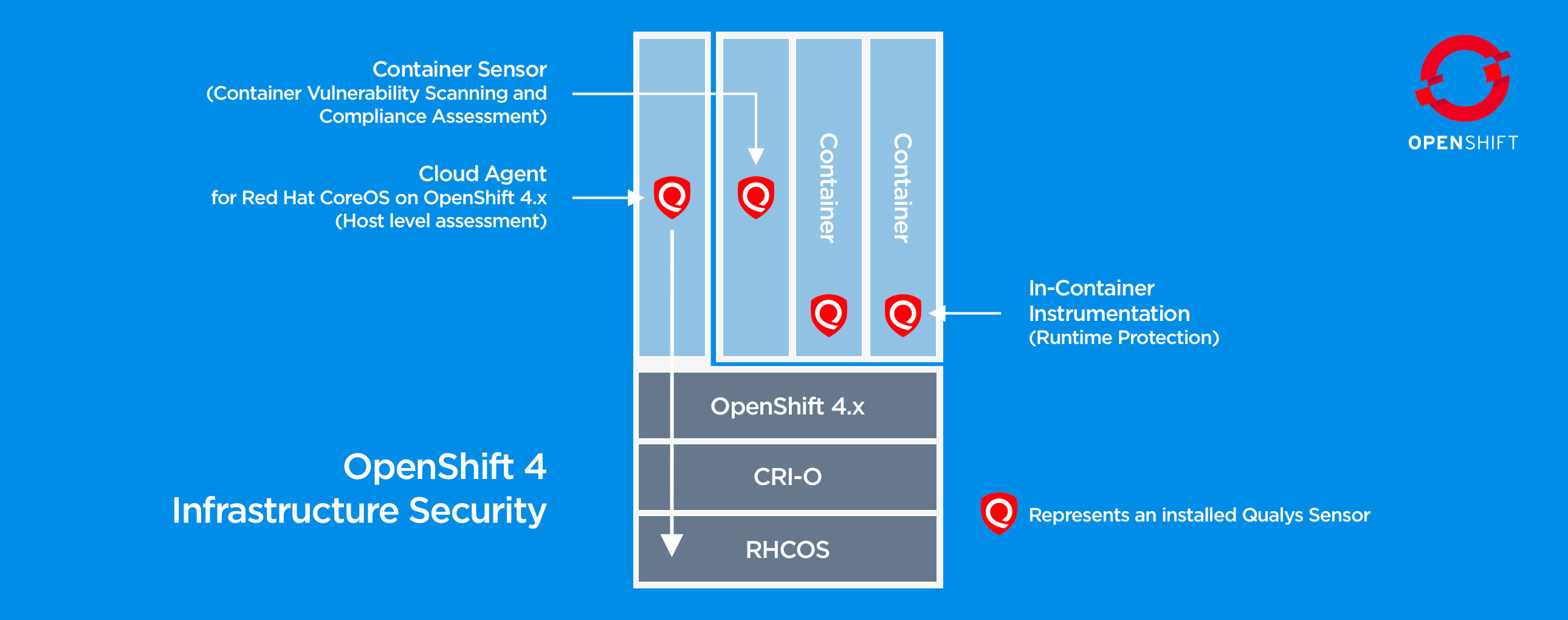
Qualys full-stack security for Red Hat OpenShift adds visibility, actionable intelligence, and security auditing for Red Hat Enterprise Linux CoreOS, the operating system that underpins OpenShift deployments for running containers securely. With this new offering, Qualys is now the first and only solution with the ability to scan directly into Red Hat Enterprise Linux CoreOS in Red Hat OpenShift, so you can manage and reduce risk at both the host OS and container levels. Built on the Qualys Cloud Platform, Qualys’ solution seamlessly integrates with customers’ vulnerability management workflows, reporting and metrics to help reduce risk.
Security Challenges
Traditionally, vulnerability detection and threat management for apps or services delivered via containers has been difficult and impractical to achieve, due to the lack of comprehensive detection and assessment of threats at both the container and host levels. Container deployments face these security challenges:
- Lack of Asset Visibility
Inventory is the first step in securing any assets, and with Red Hat Enterprise Linux CoreOS it’s no different. Without a consolidated inventory including information such as installed packages, open ports, users and hardware, it’s nearly impossible to secure what you don’t know. - No Actionable Intelligence
Red Hat provides detailed Red Hat Security Advisories for OpenShift with Common Vulnerabilities and Exposures (CVE) and package information. Without the proper tools, determining the scope of impact in an automated fashion with actionable results is not possible. - Need for Security Auditing
Heavily regulated industries such as PCI require strict adherence to inventory management, patch verification, and security coverage, which is not possible without repeatable inventory management, vulnerability management, and reporting processes.
How Qualys Solves These Challenges
These security challenges can be addressed with the help of Qualys.
1. Unparalleled Visibility
Qualys Global AssetView, available to anyone at no charge, gives you a single view of all your OpenShift clusters including masters, workers and infrastructure nodes.
Or upgrade to CyberSecurity Asset Management (CSAM) to get enriched detail about each node’s hardware configuration, installed packages, open ports and cloud provider metadata when running in the public cloud.
Then inspect your assets and their enriched metadata in Qualys CSAM as shown below:
Install Qualys Cloud Agent
Install and configure Qualys Cloud Agent on your assets running Red Hat Enterprise Linux CoreOS in OpenShift to start collecting and managing inventory data. Sign up to get the new Cloud Agent or download it from your Qualys subscription.
Because Qualys Cloud Agent for Red Hat Enterprise Linux CoreOS in Red Hat OpenShift runs as a container, installation is easy and doesn’t require modifications to the host, opening ports, or dealing with credentials. Watch how to install it in just a few easy steps:
Identify Your Assets
If you don’t already have an inventory of your OpenShift assets, you can run a discovery scan against Information Gathered QID 48140 : Red Hat OpenShift Cluster Nodes Enumerated to identify instances of OpenShift in your environment.
2. Actionable Intelligence
The Qualys Vulnerability Signature team automates the development of detections to quickly assess your OpenShift environment for vulnerabilities using Red Hat Security Advisories.
Red Hat and Qualys are working together to ensure new and critical vulnerabilities are identified and packages are available for your teams to apply fixes and mitigate threats.
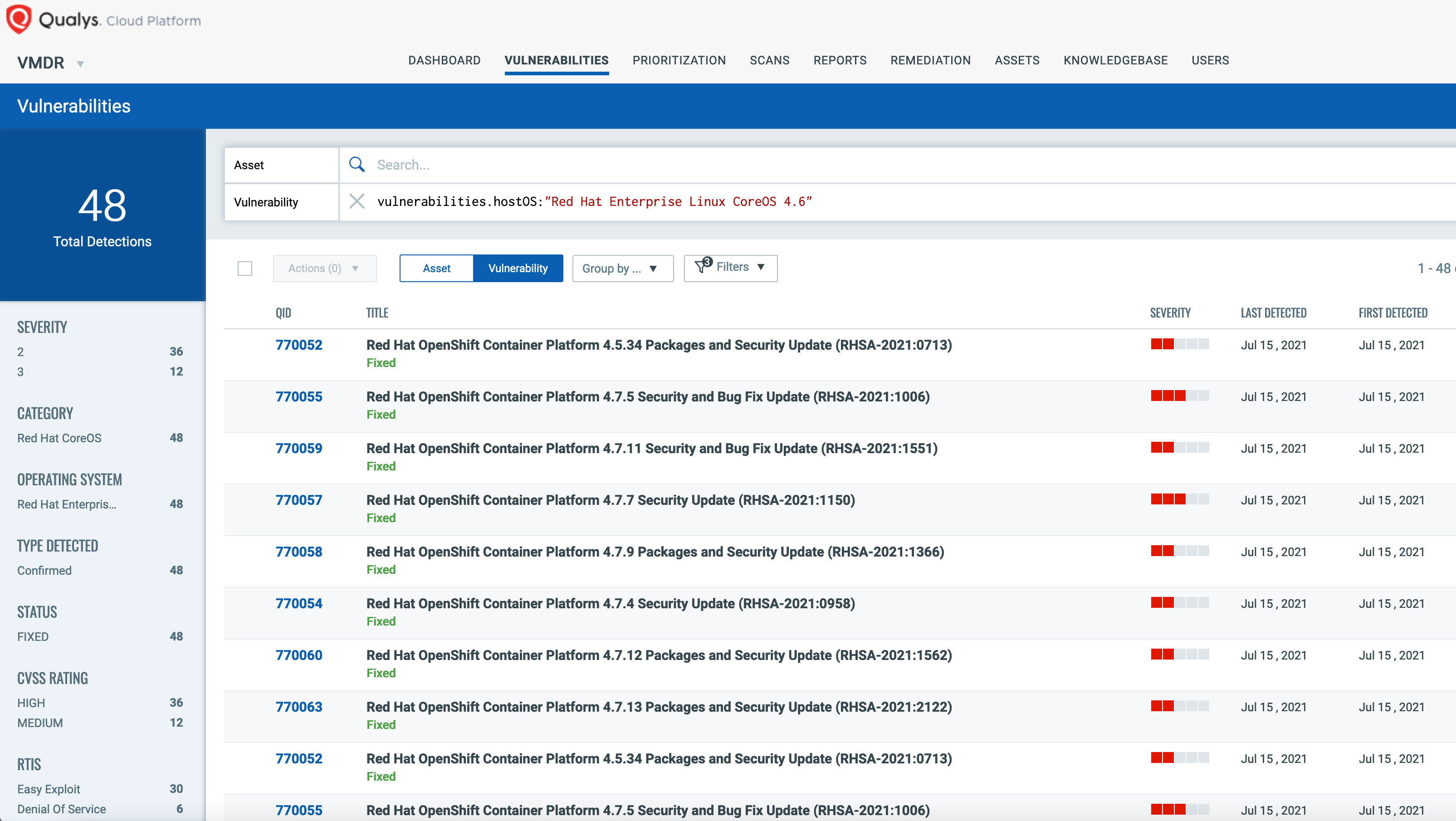
Qualys enhances advisories by giving actionable intelligence. Remediation teams know the specific vulnerable package(s) and the required package(s) to be upgraded. Additionally, Qualys provides impact and CVEs details to help prioritize and report to senior management. See an example below:
Vulnerability Coverage
To date, Qualys has been able to deliver extensive coverage of Red Hat Security Advisories (RHSAs) on OpenShift as shown in this breakdown of Qualys detections (QIDs) by RHSA published year and OpenShift version:
| RHSA Year | OpenShift Version | Qualys Detection (QID) Count |
|---|---|---|
| RHSA-2019 | 4.1 | 9 |
| RHSA-2019 | 4.2 | 1 |
| RHSA-2020 | 4.1 | 3 |
| RHSA-2020 | 4.2 | 8 |
| RHSA-2020 | 4.3 | 9 |
| RHSA-2020 | 4.4 | 6 |
| RHSA-2020 | 4.5 | 3 |
| RHSA-2020 | 4.6 | 4 |
| RHSA-2020 | 4.7 | 1 |
| RHSA-2021 | 4.4 | 2 |
| RHSA-2021 | 4.5 | 5 |
| RHSA-2021 | 4.6 | 4 |
| RHSA-2021 | 4.7 | 7 |
| Grand Total: | 62 |
Secure Your Containers
Qualys Container Security discovers, tracks and continuously secures containers from build to runtime. Security teams can implement a comprehensive container security program with a single solution that includes vulnerability management, and detection and response across the build-ship-run container pipeline.
See for yourself as part of a Qualys Cloud Platform free trial.
3. Security Auditing
With the availability of Qualys support for Red Hat Enterprise Linux CoreOS on Red Hat OpenShift, you can use the power of the Qualys Cloud Platform to generate reports for security auditors and demonstrate your full inventory of OpenShift clusters, verify patching, and document security coverage.
About Red Hat OpenShift
Red Hat OpenShift is a certified Kubernetes distribution and supported Kube platform with built-in enterprise security designed for enterprises to build, deploy, run and manage intelligent applications securely at scale in a hybrid cloud environment. Red Hat believes security must be continuous throughout the stack using a defense-in-depth approach to protect all layers of the stack holistically.
In addition to the great features Kubernetes provides, Red Hat OpenShift adds additional support and services focused on security. It all starts with a container-optimized operating system in Red Hat Enterprise Linux CoreOS, and continues with other security features like SELinux, multitenancy, Security Context Constraints, identity and access management, RBAC, data encryption, FIPS mode, compliance and file integrity, vulnerability management, network segmentation, and threat detection and response. Of course, these supported features are all provided through Red Hat’s supply chain of trusted content and backports.
Why Red Hat Enterprise Linux CoreOS?
Red Hat Enterprise Linux CoreOS is built from Red Hat Enterprise Linux, which provides several security features like SELinux, Linux namespaces, CGroups, Capabilities and Read Only Mounts. Additionally, Red Hat Enterprise Linux CoreOS is an immutable, minimalist operating system with transactional updates. The operating system always boots into a known good state, similar to how container images are managed and deployed. Immutability ensures the cluster is the single source of truth for provisioning the right configurations and versions of the operating system, enabling repeatability and auditability for your nodes.
An Additional Layer of Security
Red Hat’s layered defense-in-depth approach to security includes Red Hat’s ecosystem of security partners who extend and enhance the security capabilities of Red Hat OpenShift. For this reason, Red Hat is collaborating with Qualys to offer more complementary security capabilities you can integrate and automate to extend and enhance your security posture to manage your risk.
Learn More and Get Started
- Sign up today to download the Cloud Agent binary or download it directly from your Qualys subscription.
- Join Red Hat and Qualys for the webinar on August 16, 2021: Securing Red Hat Enterprise Linux CoreOS in Red Hat OpenShift with Qualys.
- Watch the Red Hat X podcast series: Red Hat and Qualys collaborates on the first Red Hat CoreOS scanner
- Read the press release: Qualys Collaborates with Red Hat to Enhance Security for the Container and Host Operating System for Red Hat OpenShift.
- Installation Guide
Frequently Asked Questions (FAQ’s)
What’s new?
With this announcement, Qualys enhances the security of the underlying Red Hat Enterprise Linux CoreOS in Red Hat OpenShift. This new capability complements the benefits of Qualys Container Security, which discovers, tracks and continuously secures containers from build to runtime. The combination provides full-stack security for Red Hat OpenShift, making this platform an ideal choice for running containers securely.
What are the support specifications for this release?
| Operation System: | Red Hat Enterprise Linux CoreOS in Red Hat OpenShift 4.x |
| Qualys Apps Supported: | Vulnerability Management Policy Compliance |
| Generally Available Date: | July 28, 2021 |
| Cloud Agent Version: | 3.5 |
How can I download Qualys Cloud Agent for Red Hat Enterprise Linux CoreOS in Red Hat OpenShift?
If you are a Qualys customer, the new Cloud Agent binary is available for download in the Cloud Agent app in your Qualys subscription.
If you are not a customer, please sign up for Qualys Cloud Agent for Red Hat Enterprise Linux CoreOS in Red Hat OpenShift to receive help getting started with Qualys, including downloading, installing and configuring the agent.
Is Qualys Policy Compliance supported?
Yes.
Do I need to have Qualys Container Security to scan my Red Hat Enterprise Linux CoreOS operating systems?
No. Although Qualys recommends coverage for both the host and container level, it is not a prerequisite.
Qualys Cloud Agent can discover and inventory assets running Red Hat Enterprise Linux CoreOS in OpenShift. With Vulnerability Management enabled, Qualys Cloud Agent also scans and assesses for vulnerabilities.
Where can I find documentation?
Cloud Agent for Red Hat Enterprise Linux CoreOS in Red Hat OpenShift Installation Guide
Contributors
Dave Meurer, Global Principal Solutions Architect, Red Hat