How Risk-Based Remediation Drives Smarter Vulnerability Management with Qualys VMDR 2.0
According to the recently released Verizon DBIR report, vulnerability exploitation continued to be one of the top three attack vectors exploited by bad actors in 2021 to break into organizations. As of this writing, it’s only June, but more than 10,000 vulnerabilities have already been disclosed in 2022, according to the National Vulnerability Database (NVD). As if that weren’t bad enough, the rate of increase of ransomware attacks last year was more than the last five years combined.
The resources required to patch all these vulnerabilities have not kept up with the pace at which vulnerabilities are disclosed and exploited. This is a big problem for even the largest enterprise.
Add to these sobering statistics the fact that the correct remediation path is not always straightforward. In some cases, patching a vulnerability can require deploying a patch, making a configuration change, or both. Either of these actions can introduce operational risk. IT teams responsible for ensuring systems are always up and running rightfully want to vet these changes before they go live.
Unfortunately, all these decisions introduce delays in the remediation process – which is exactly what hackers and attackers are counting on.
For example, DearCry Ransomware that spread through the ProxyLogon (CVE-2021-26855) vulnerability exploited unpatched instances in IT environments within a mere seven days after the vulnerability was disclosed. According to an analysis completed by the Qualys Research Team, most organizations took more than eight days to remediate ProxyLogon. Some took even longer, taking on even more risk.
Prioritize Risk and Boost Remediation with TruRisk™ Scores in VMDR 2.0

Qualys VMDR 2.0 introduces TruRisk scores that help organizations prioritize vulnerabilities based on risk ratings that weigh multiple factors such as exploit code maturity, exploitation in the wild, and multiple other factors that accurately measure risk.
Cybersecurity teams can now efficiently prioritize vulnerabilities by focusing first on the riskiest vulnerabilities to their own specific and unique environment. Instead of prioritizing vulnerabilities based on CVSS score alone, VMDR 2.0 with Qualys TruRisk helps customers focus on the much smaller and more manageable set of vulnerabilities that are currently exploited by threat actors and have no or limited mitigating controls applied in the customer’s environment. This helps enterprises large and small be more efficient with their remediation campaigns and focus first on remediating the riskiest vulnerabilities to their business.
Free Trial
Qualys VMDR: Get Started wth a 30-day Free trial
Automate Vulnerability Remediation with TruRisk Scores for Faster Action
A key step in any remediation workflow is good communication between the vulnerability management (VM) team and the remediation team. The VM team analyzes and prioritizes risk across all known vulnerabilities. The remediation team researches and finds the relevant patches and configuration changes required to address the VM list. However, these two teams use different products and different terminology. The VM team understands the risk and QIDs. The remediation team understands patches.
In some cases, patching alone is required to remediate a security risk (i.e. QID). In other cases, merely patching is not enough; a registry key change is also required to remediate the QID. Organizations spend valuable time mapping their prioritized list of vulnerabilities against the patches and/or configuration changes required in their environment to remediate. Using multiple tools in this process further complicates and slows MTTR.
To solve this problem, Qualys VMDR 2.0 allows the VM team to select the vulnerabilities flagged as the highest risk by TruRisk and create a job that’s ready to be deployed for the remediation team. As part of any job, Qualys maps the selected vulnerabilities to the right patches and configuration changes required to remediate them specific to the organization’s unique environment. This allows the remediation team to focus on the core actions of testing and deploying the right patches and configuration changes against their assets. Thus, all the extra time and effort required using two separate tools are eliminated.
Proactive automation can further speed up the process of detection, prioritization, and remediation. For some assets, this entire process can be automated with VMDR 2.0. For example, a zero-touch automation job can be created to patch non-mission critical assets that will automatically execute as soon as a new vulnerability with a Qualys Detection Score >90 is detected. This automation instructs Qualys Patch Management to find the right patches and automatically deploy them to the asset. Both teams benefit from automation of an MTTR process that’s proactive and faster to address newly discovered vulnerabilities with the highest risk to their environment.
Get Faster Results with Integrated Patch Management for Effective Remediation
When we introduced Qualys VMDR back in 2020 we understood that enterprises were struggling with patch management, and so we introduced an integrated solution which helped organizations patch faster than ever before.
Recently, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) released its list of the most exploited vulnerabilities. Qualys VMDR syncs with this list and maps all vulnerabilities flagged by CISA to their relevant QIDs.
Using this data, Qualys ran an anonymized analysis to understand the average number of days it takes our customer organizations to remediate CISA flagged vulnerabilities. As part of the analysis, we compared organizations that use a single product (VMDR with Qualys Patch Management) to help bridge the gap between vulnerability discovery by Security teams and remediation by IT Operations… to organizations that use two separate products.
The results in the table below emphasize the importance of an enterprise simplifying and automating its detection, prioritization, and remediation processes. On average, organizations that use Qualys VMDR + Patch Management remediate vulnerabilities 35% faster than organizations that use separate tools. Even better, with some vulnerabilities the difference can be 63% faster with a combined solution.
Here’s the detailed analysis:
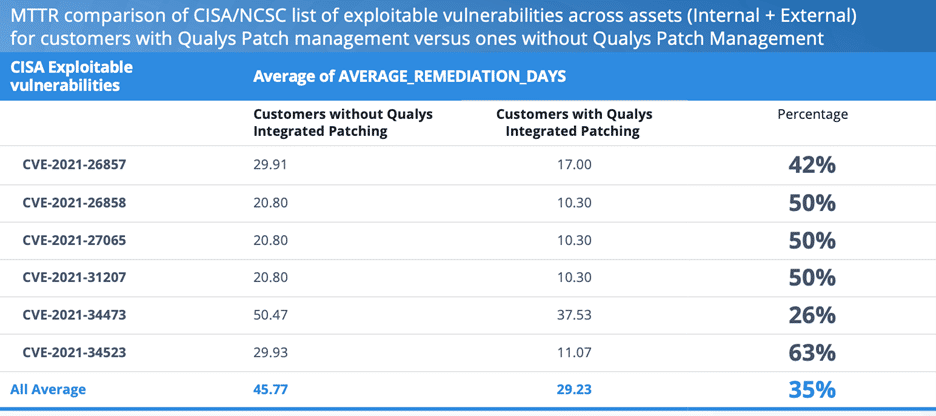
Many organizations continue to struggle with vulnerability remediation workflow. By adopting a single unified solution for both vulnerability management and patch management, enterprises both large and small can reduce their average remediation time significantly and improve their security posture as a result.
Qualys Patch Management is built into the Qualys Cloud Agent, so any current Qualys VMDR customer can easily enable patch management capabilities. There is no need to install new software or make any network changes.
To try this integrated patch management approach with the newly released VMDR 2.0, sign up for a trial.