Introducing CyberSecurity Asset Management 2.0 with Natively Integrated External Attack Surface Management

Qualys is introducing Qualys CyberSecurity Asset Management 2.0, which now delivers natively integrated External Attack Surface Management (EASM) to enable Cybersecurity teams to identify any and all assets visible on the internet, including previously unknown assets and any potential security issues… before attackers find them.
Read the CSAM 2.0 Press Release
Challenges of Managing the Modern External Attack Surface
Your attack surface is dynamic. Assets come and go, and your infrastructure configuration changes to adapt to your business needs. Many assets become visible on the Internet unintentionally, giving you no visibility into the “unknown unknowns”. Often these are assets managed by subsidiaries, acquisitions, or other partners.
Read the Blog: What is External Attack Surface Management?
The proliferation of “Shadow IT”—unsanctioned technologies and applications deployed without IT oversight— has accelerated attack surface sprawl across corporate networks as more teams adopt new cloud services and development processes, sometimes without proper authorization, either to innovate or as part of their digital transformation.
Believe it or not, many IT and Cybersecurity professionals still depend on spreadsheets to maintain an inventory of their externally facing assets. Often, different teams within the same organization will have their own spreadsheet of their managed assets and may rarely share this information. This approach is just not scalable, not only because the assets and their configurations are ever-changing, but also because spreadsheets are not automatically updated with new assets.
A configuration management database (CMDB), when up to date and accurate, is a good source for business context for known assets. It has valuable information that enables Cybersecurity teams to understand asset criticality and function, business, and technical ownership. But again, that is only for known assets and CMDBs are typically not updated in real-time.
Independent external attack surface monitoring solutions provide a limited perspective to Cybersecurity teams, as these solutions typically lack the inside-out security and configuration context of the assets. Furthermore, since they need to manage the end-to-end security program over all their assets, these tools do not fulfill this requirement.
With the limited perspective they present, there are no workflows to help the Cybersecurity team fully manage the security and compliance program on these assets, which should include assessing, prioritizing remediating issues to mitigate risk.
Some organizations attempt to utilize multiple consoles across asset management, vulnerability and patch management, IP management, CMDB, and other siloed external attack surface management (EASM) tools. It can be a manual, inefficient process to try to correlate information across these tools. However, managing multiple consoles and spreadsheets is not scalable or sustainable. It creates an unnecessary overhead, and valuable time is wasted that could be used by Cybersecurity teams to focus on closing security gaps. Fundamentally, it leads to higher TCO.
What Cybersecurity Teams Need from EASM Solutions
Cybersecurity teams need to continuously monitor their external attack surface, track changes, and receive notifications when new, unknown assets, or critical issues are found. They want to reduce the threat from “unknown unknowns” as much as possible. This could include workloads running on public clouds, IoT devices, abandoned IP addresses, and services enabled by Shadow IT.
They need to reduce the unnecessary attack surface as much as possible.
This means that if an externally facing asset or its configuration is not necessary for the business, then it should be shut down. For this reason, Cybersecurity teams want to automatically associate and add context to assets related to their organization, no matter where the asset is hosted or by whom. Most of all, Cybersecurity teams want to know if an attacker’s reconnaissance will find a path to their organization’s crown jewels before they know about it. They want to know their exposed vulnerabilities and risks from exploits, attack vectors, the ease/difficulty of exploitation, and the remediation complexities to correct their exposure.
Qualys CSAM 2.0 Takes a Fresh Approach to EASM
By including External Attack Surface Management in Qualys CyberSecurity Asset Management 2.0, we are tilting the playing field against attackers and giving added advantage to cybersecurity practitioners.
Our fully integrated External Attack Surface Management capability enables:
- Discovery: Automatically discover your assets exposed to the internet, including ones from your subsidiaries, mergers, and acquisitions
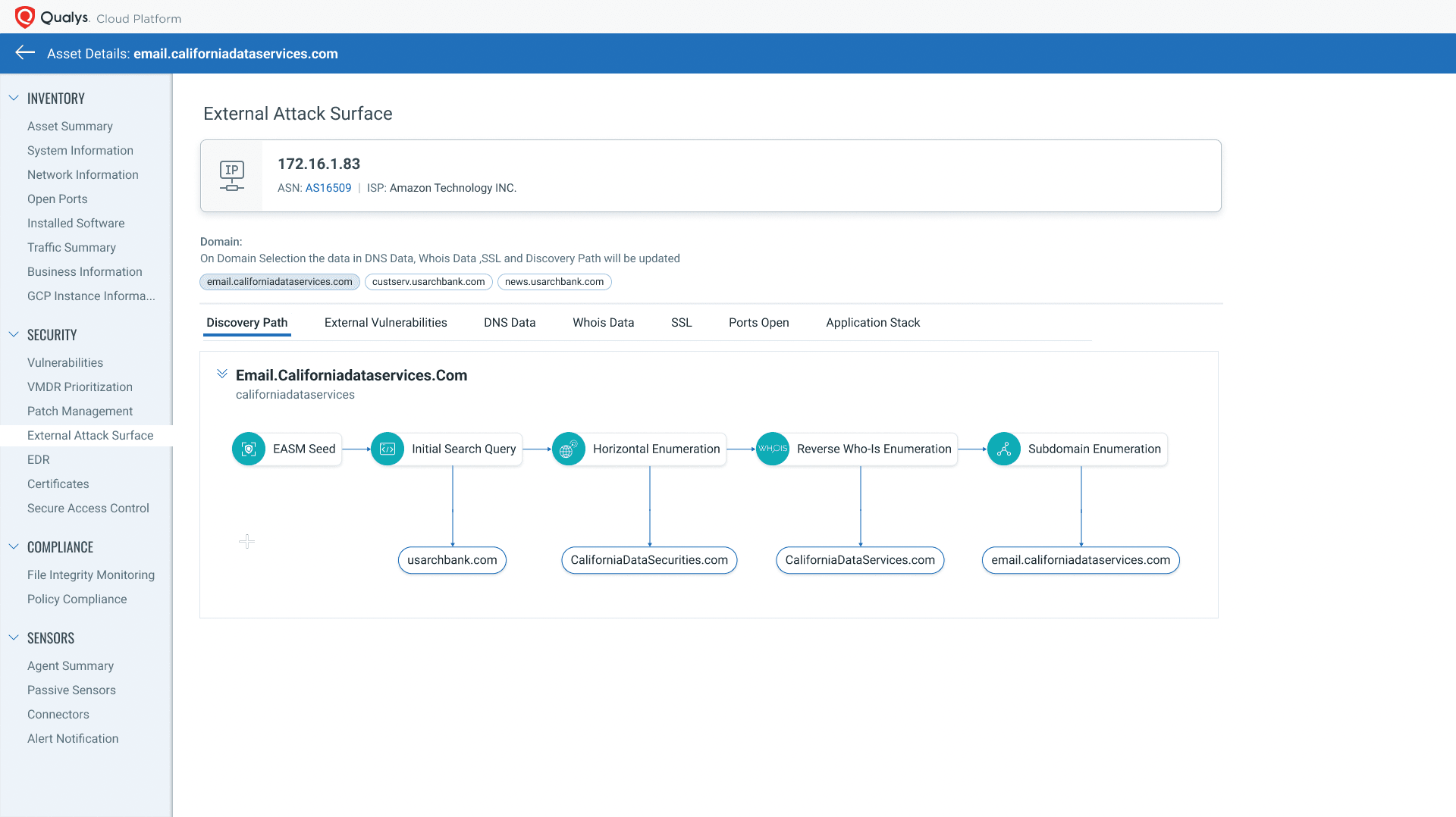
- Attribution: Understand asset attribution by showing how an asset is discoverable on the internet and how it’s associated to your organization
- Business Context: Understand the context of each asset, including when and how it was created, by providing information such as DNS and WHOIS records
- Continuous Risk Assessment: Know asset configuration/misconfiguration, including unsanctioned open ports, unapproved services and application stacks, and expired or expiring SSL certificates; See potential vulnerabilities with automated lightweight scans and integration with sources like Shodan
- Real-time Visibility: Gain visibility of previously unknown or unmanaged assets by correlating with your existing inventory within Qualys CSAM, to identify previously missing assets
- Risk Mitigation: Activate and orchestrate Qualys full vulnerability scans through one-click automated workflow to confirm vulnerabilities on new assets, and then prioritize to rapidly remediate risk
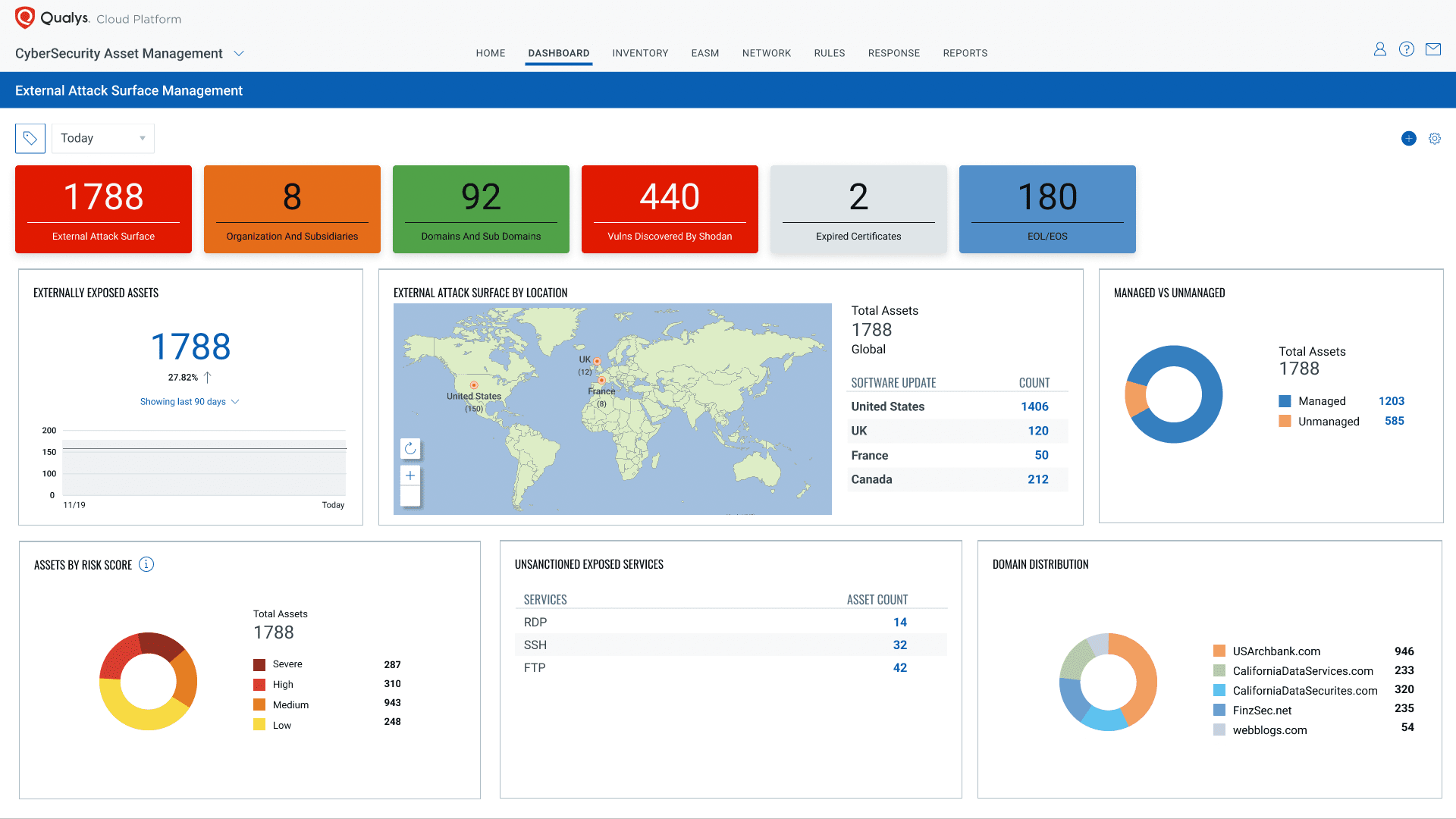
Because EASM is an extension to Qualys CSAM, it supports and enhances the same great features as it does for your internal/managed assets:
- Automatically categorize your assets and add your own context with dynamic, rule-based tagging
- Synchronize bidirectionally with your CMDB, keeping your CMDB up-to-date and enriching Qualys with business metadata such as owners, business application, and criticality
- Easily keep your compliance teams informed with out-of-box, customizable reporting
- Provide a 360-degree view of your assets, security, and compliance posture with Unified Dashboards
- Configure rule-based alerts to notify teams through their preferred notification channels
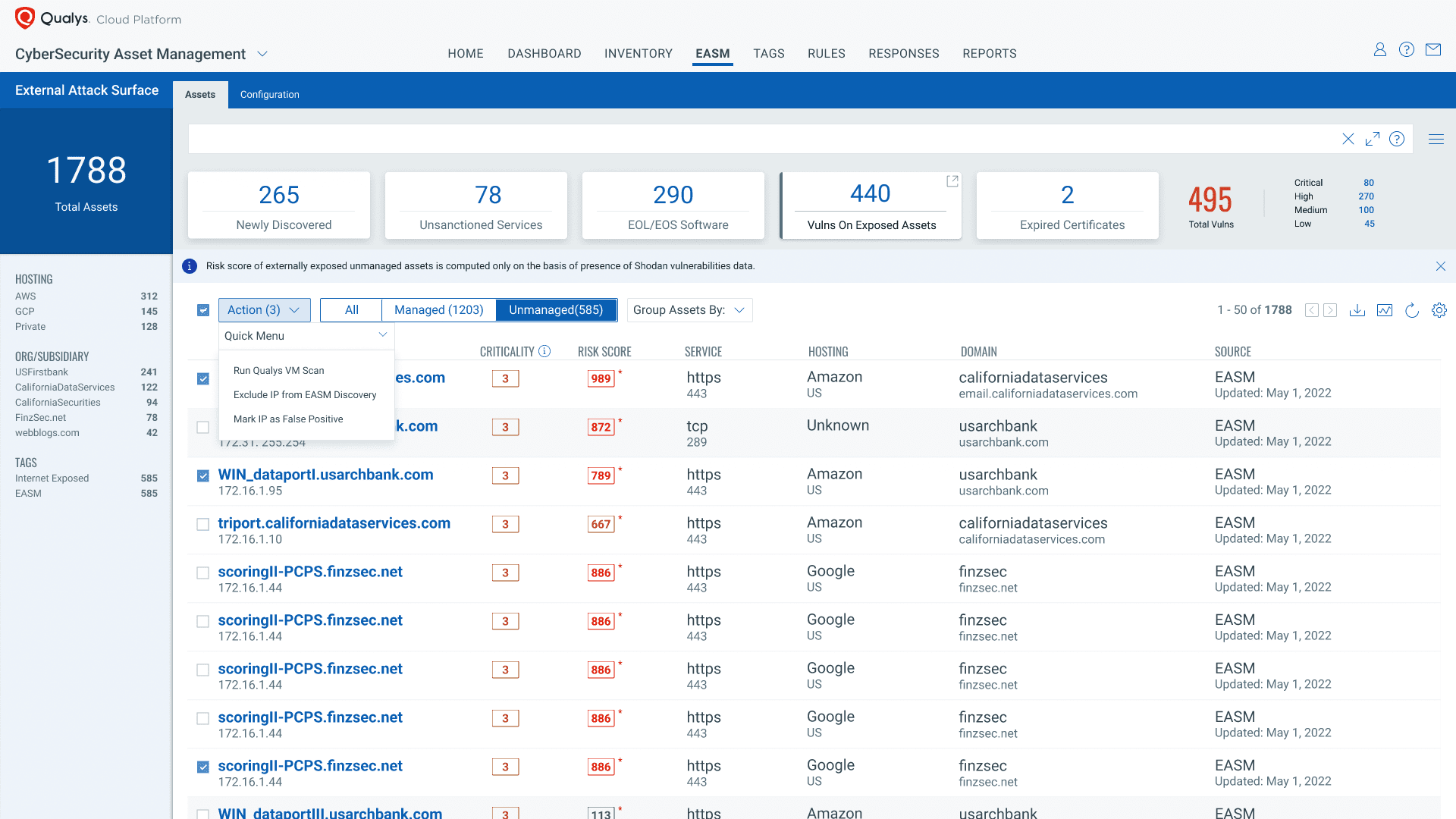
It’s easy to start discovering your External Attack Surface with CSAM 2.0. All you need to do is activate the service and validate your root org or domain. The EASM service will then start discovering your assets exposed to the internet. It finds your subsidiaries, performs horizontal and vertical domain and subdomain enumeration, and correlates WHOIS and DNS records to accurately attribute assets to your organization. Finally, it frequently monitors changes such as new open ports and services, expiring certificates, or new vulnerabilities.
Free Trial
Qualys CyberSecurity Asset Management Trial
Qualys CSAM 2.0 + Qualys VMDR 2.0: an Integrated Approach
The combination of the latest versions of Qualys VMDR and Qualys CSAM provides an integrated approach to assessing and reducing cyber risk. Qualys customers and other enterprises can enjoy the benefits of combining the attack surface management capabilities of CSAM 2.0 with the vulnerability management, detection, and response inherent in Qualys VMDR 2.0.
This allows you to quickly bring your full attack surface under management through network scans or the Qualys Cloud Agent. Once the asset is scanned and managed with Qualys sensors, organizations can continuously gather comprehensive asset inventory data, apply business criticality and risk context, detect security gaps like unauthorized or end-of-life software, and respond with appropriate actions to mitigate risk.
Qualys CSAM 2.0 with External Attack Surface Management natively integrates with Qualys VMDR 2.0. This enables teams to accurately quantify and prioritize cyber risk and quickly respond to vulnerabilities and misconfigurations. VMDR with Qualys TruRiskTM automatically assesses multiple factors such as asset criticality, location, found vulnerabilities/misconfigurations, any risk mitigation controls applied on the asset, vulnerability exploit code maturity, evidence of active exploitation, and many more factors. These are all applied to deliver multiple risk scores. Qualys TruRisk quantifies an organization’s true risk so that IT and Cybersecurity teams can focus on what’s important.
Since this is all integrated within the Qualys Cloud Platform, Cybersecurity teams can easily transition from discovering unknowns to fully inventorying all aspects of these assets. Qualys then puts them into a proper security context, assessing them for vulnerabilities and misconfigurations, so you can prioritize risks and rapidly remediate, all from a single, unified platform.
Availability
The newly announced EASM capability is currently in early preview, available to all existing Qualys customers with a CSAM subscription. Qualys customers can contact their Technical Account Manager (TAM) or Customer Support to get this functionality enabled. If your enterprise is interested in evaluating Qualys CSAM 2.0, we invite you to learn more about CSAM and to sign up for your own 60-day free trial.