Award-winning Qualys Vulnerability and Compliance Solution now available on IBM zSystems & LinuxONE Page

Table of Contents
- Customers Existing Security Challenges
- Complete Qualys security solution is now available on IBM zSystems and LinuxONE
- Asset Management for IBM zSystems and LinuxONE
- Vulnerability Management and Risk Prioritization for IBM zSystems and LinuxONE
- Policy Compliance Assessments for IBM zSystems and LinuxONE
- Hybrid Coverage now includes Robust IBM Mainframe Systems
- Get Started
Today’s modern IBM mainframe is central to hybrid cloud environments, valued by two-thirds of the Fortune 100 as a highly secured platform for running mission-critical workloads. Not surprisingly, according to a recent IBM commissioned study by Celent, it is estimated that 70% of global bank cards and payment transactions run on IBM zSystems.
With this dependence on IBM zSystems for global payment transactions and the rise of modern, sophisticated cyber threats and ransomware attacks, increasing regulatory mandates, and exposure of data out of mainframes to hybrid cloud environments, organizations must act to decisively protect critical data, systems, and applications from compromise and implement robust security measures.
The global average data breach cost increased by 2.6% to USD 4.35 million in 2022, the highest since 2016. Not surprisingly, security system complexity, cloud migration, and compliance failures are among the top three factors associated with the highest net increase in the average cost.
Interesting Fact: Did you know that the average data breach lifecycle – the time elapsed between the first detection of the breach and its containment – was 277 days.
Leading organizations accelerating hybrid cloud transformation in today’s hyper-connected world need a holistic approach to IT security and compliance. It has become imperative to have a comprehensive security solution to automate the full spectrum of vulnerability management and compliance protection of these critical systems.
Customer’s Existing Security Challenges
- Increased Attack Surface — To modernize mainframes and increase the accessibility of these computational giants, there has been an increase in connectivity options like Secure Shell (SSH), Customer Information Control System (CICS), FTP, HTTP, etc. All these expand the attack surface of the mainframes. The lack of a single source of truth for listing all vulnerabilities in the mainframes and insufficient skill sets lead to gaps in shielding mainframes against known as well as zero-day vulnerabilities. Apart from the vulnerabilities in the baseline operating system, the vulnerable applications running on mainframes and the possibility of DDoS attacks on these crucial applications call for hardened configurations and continuous assessments.
- Disjointed view of security postures using point solutions — If an organization’s legacy solutions don’t provide a consolidated view of its data resources and constantly changing IT environment, the organization is unlikely to meet its security and regulatory requirements.
- Challenges with Remote scanning — It is often not feasible to perform authenticated scans on any of these servers because of the criticality of the data they process. Similarly, performance is a crucial factor in these real-time processing systems which means that the overhead of scanning them is too high.
- Manual audit and Customized script methods are not scalable — Many organizations are not assessing their mainframes and Db2 databases for vulnerability management and configuration compliance, or if they are, they are doing so manually. Manual audit methods are not scalable, and time-consuming; organizations may lack the resources to update the scripts. Most auditors do not accept manual reports for security posture.
Complete Qualys security solution is now available on IBM zSystems and LinuxONE
Organizations are looking for a trusted and reliable solution to assess vulnerabilities and compliance in their environment and review the results, all from a single platform. Qualys Cloud Platform is now available for IBM zSystems and LinuxONE, for organizations looking for a comprehensive, accurate, trusted, and reliable solution that supports their hybrid zSystems environments. Qualys, with its single agent and platform, has risen to meet that challenge, providing award-winning and time-tested vulnerability management, policy compliance, and asset management capabilities to help protect customers’ IBM zSystems environments. Qualys Cloud Platform on IBM zSystems alleviates organizations and auditors from the daunting task of interpreting and mapping regulatory requirements, which are usually designed for distributed systems, to the mainframe.
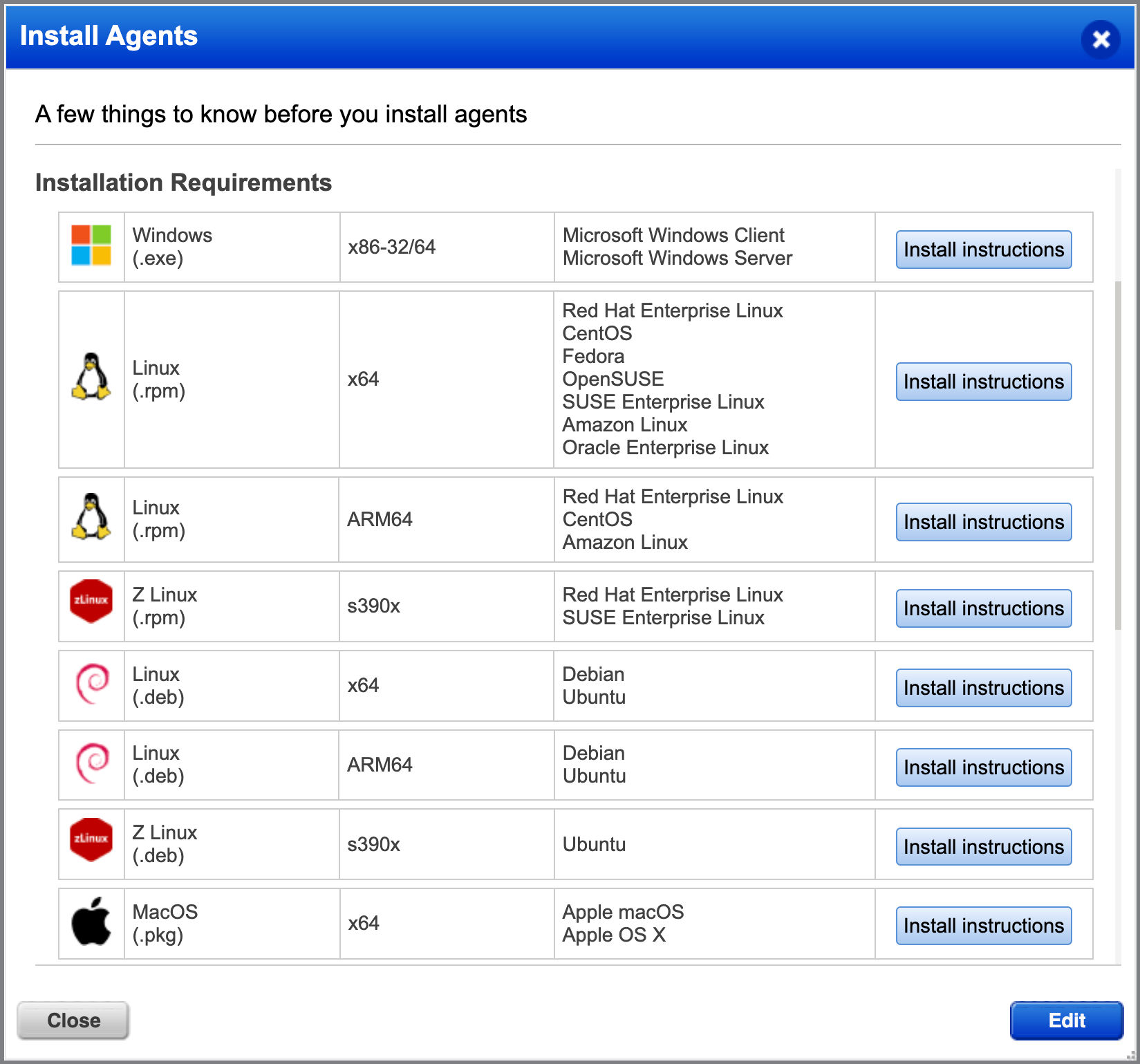
It allows security teams/mainframe owners to leverage the lightweight Qualys Cloud Agent to:
- Complete an up-to-date inventory of all their zSystems, the applications they are running, their End of Life/Service and identify security tooling blind spots – if only authorized software & processes running on them
- Gain a real-time view of all critical vulnerabilities and configuration hygiene based on CIS & DISA STIG benchmarks, along with TruRisk impacting the zSystems and applications based on threat indicators, attack surface and six sigma 99.99966% vulnerability scan detection accuracy.
- Know exact remediations to reduce risk with patch guidance
- Report Compliance against industry standards and mandates such as PCI-DSS, ISO, NIST and more.
The Cloud Agent Platform is designed for the agent and platform to work in concert to provide a high level of accuracy and fidelity, low end-to-end processing times, and minimal resource impact on the asset. The agent is designed to capture the operating system’s metadata, installed applications, and system configurations as needed by the different activated service modules and upload the metadata to the platform for analysis, correlation, reporting, and alerting. The agent only uploads deltas which keep network usage extremely low.
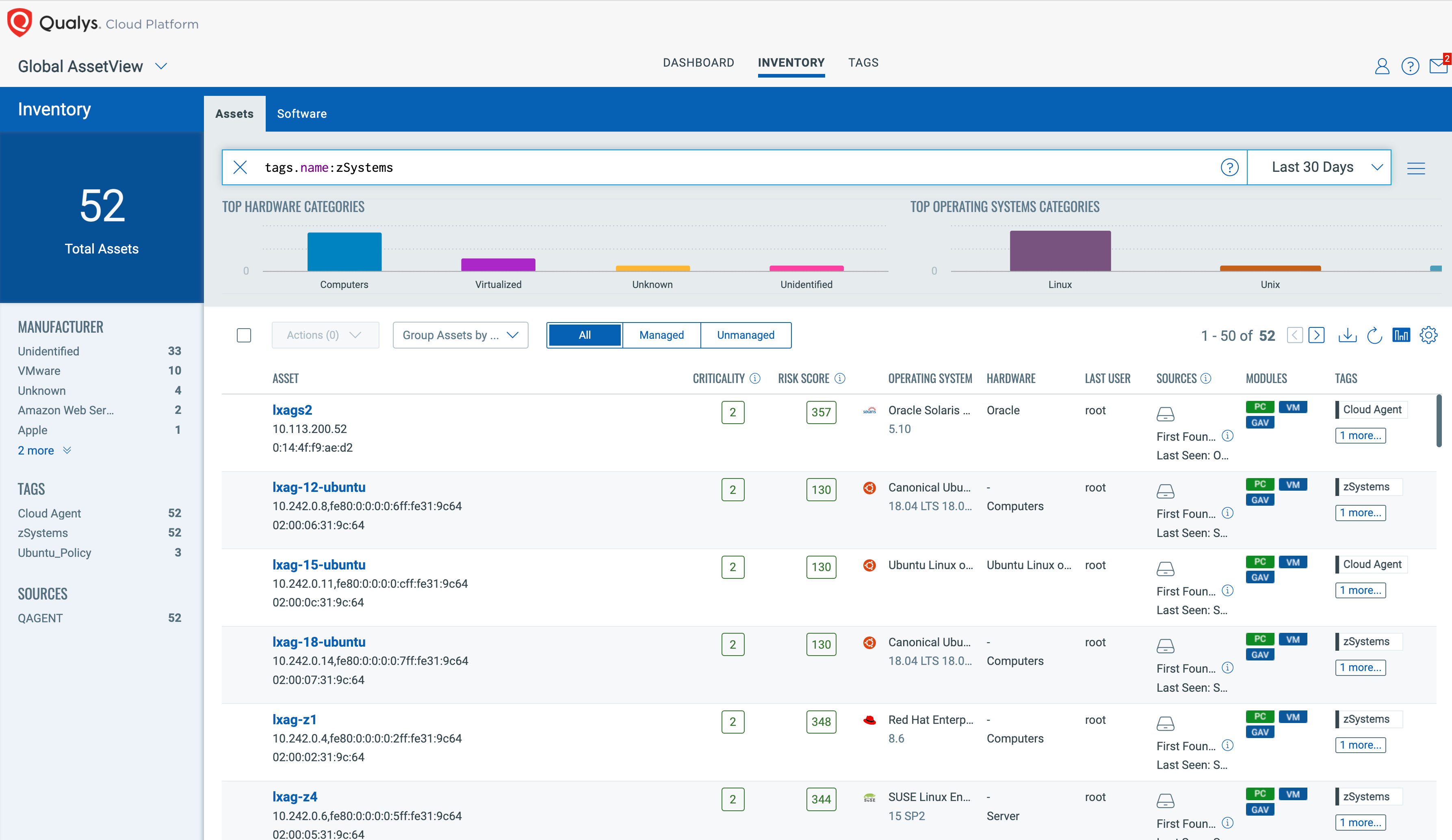
Asset Management for IBM zSystems and LinuxONE
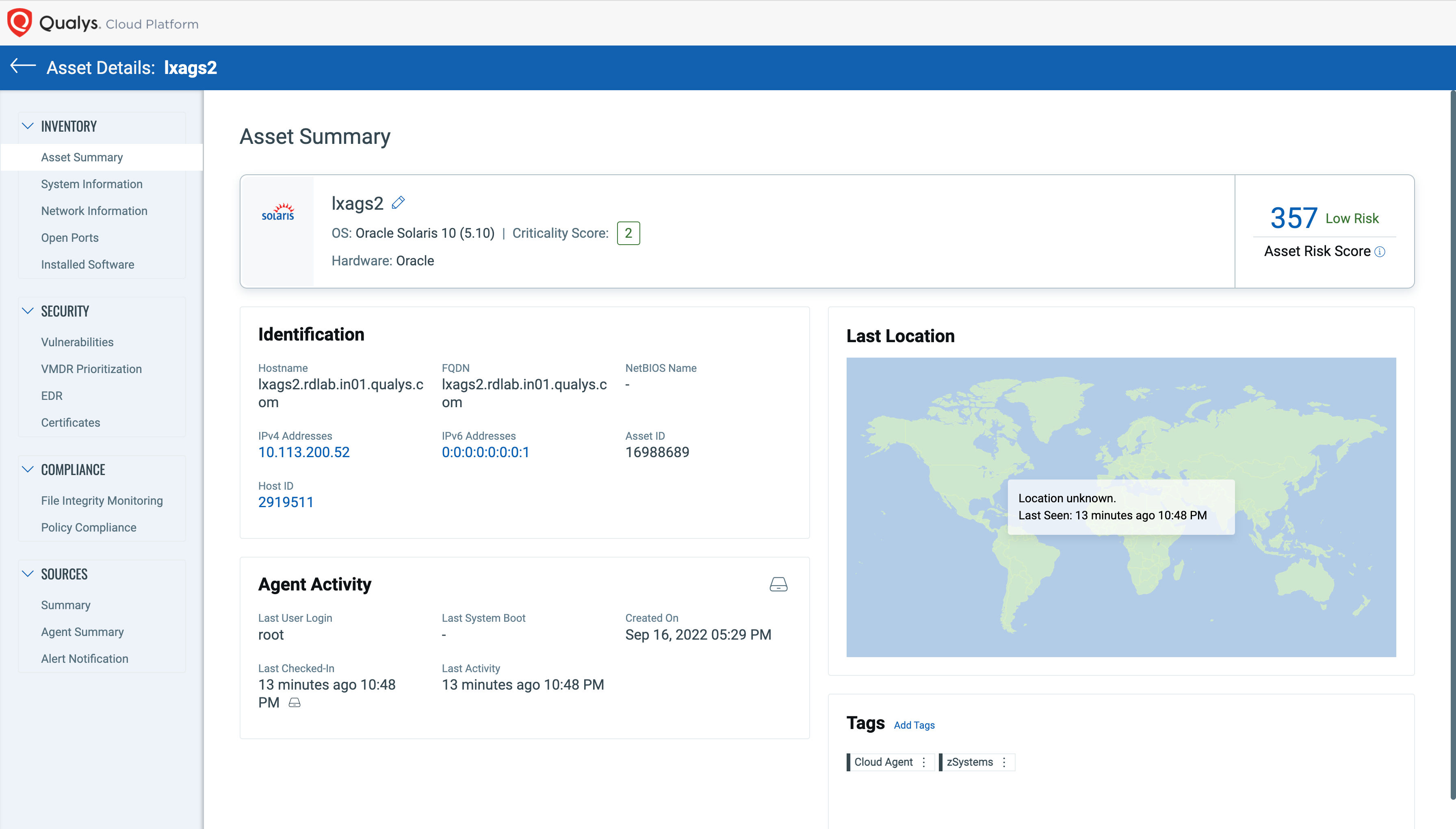
With Qualys CyberSecurity Asset Management (CSAM) on IBM zSystems and LinuxONE, security leaders can get a comprehensive view of their inventory, making it easy to identify all IBM zSystems assets, with context and business criticality. CSAM enables you to monitor and reduce tech debt with real-time EOL/EOS software tracking compliant with CISA guidelines. You may identify all assets running on s390x architecture using QQL as osArchitecture:s390x.
CSAM enables a rigorous cyber risk management process based on the automatic correlation of discovered assets, associated vulnerabilities found, and their degree of direct impact on the customer’s unique business.
Once the assets are identified, they can be grouped with dynamic tags. Dynamic tagging makes the grouped assets much easier to efficiently manage, query, and report throughout the Qualys Cloud Platform.
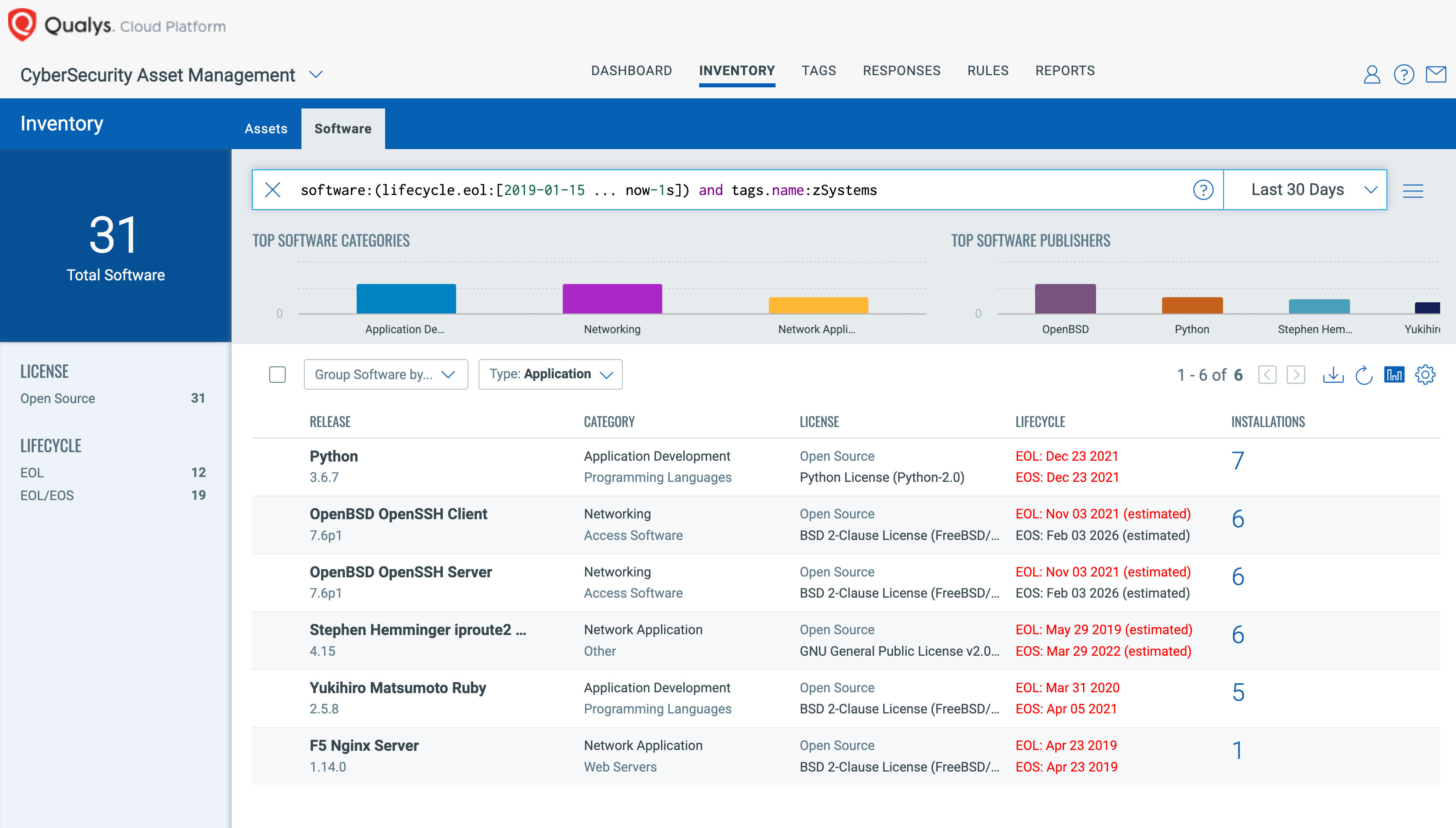
To make it easier for customers to track agents in a single pane of glass in their subscriptions, we have created the Agent Health dashboard, which you can download and import into your subscription. The tags created for grouping IBM zSystems and LinuxONE can be added to customize the dashboard exclusive for them.Unified Dashboard allows executive management to monitor, on a high level, every facet of the organization’s security effort.
Vulnerability Management and Risk Prioritization for IBM zSystems and LinuxONE
With VMDR 2.0 (Vulnerability Management Detection, and Response) with TruRiskTM, organizations with IBM zSystems get a comprehensive risk-based vulnerability management solution that identifies and prioritizes vulnerabilities and assets based on risk to enable the remediation of vulnerabilities at scale. Qualys has an extensive detection library of 8000+ CVE IDs that exist specifically on zSystems. Some examples of high criticality known vulnerabilities covered by Qualys are Log4j, PwnKit, Dirty Pipe, Samba, RCEBaron, Samedit, and more.
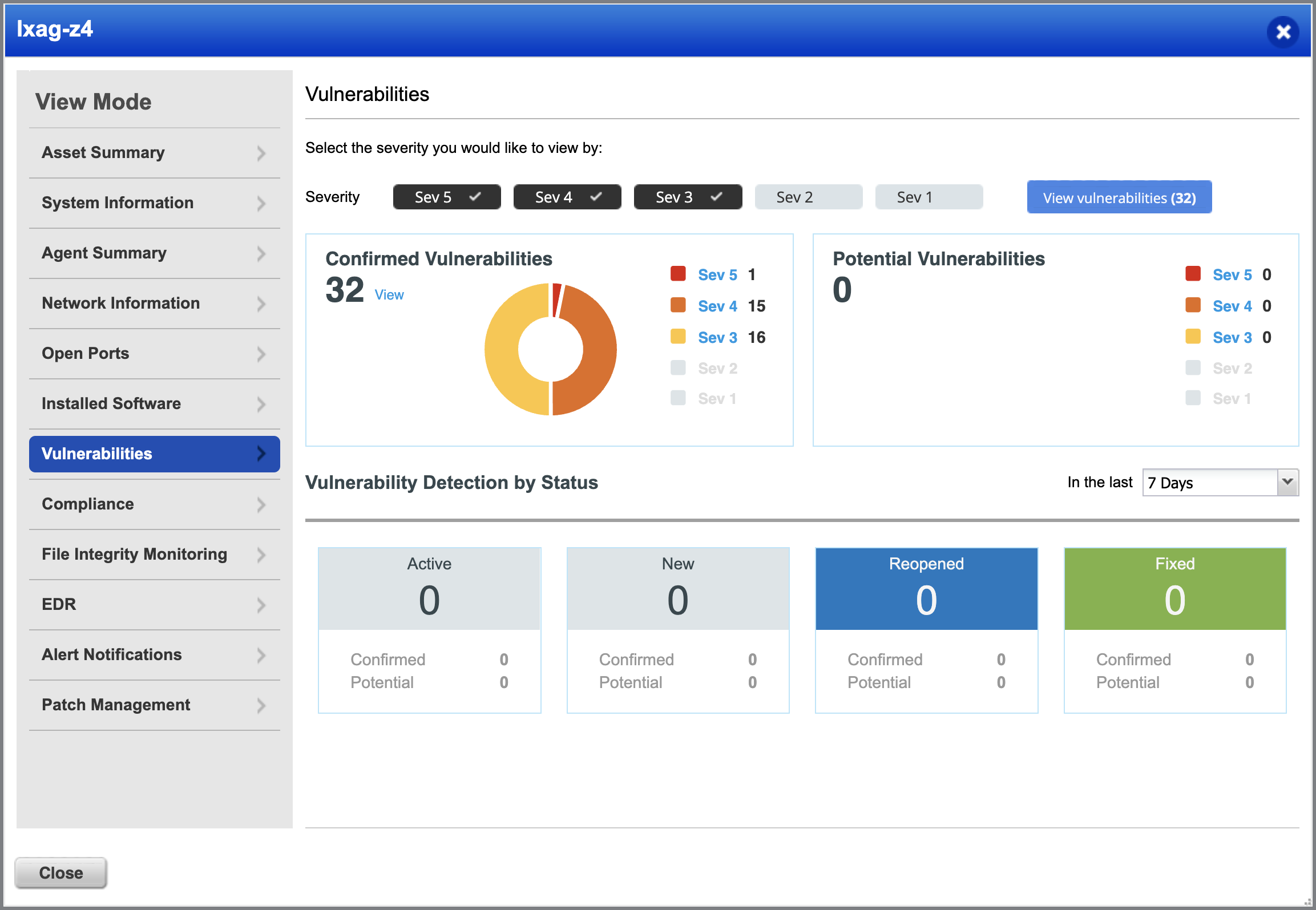
Qualys VMDR 2.0 gives organizations unprecedented insights into their risk posture and provides actionable steps to reduce risk. It also gives cybersecurity, and IT teams a shared platform to collaborate and the power to quickly align and automate workflows to respond to threats.
The vulnerabilities tab lets you track vulnerabilities based on assets, criticality, tags, and other factors to prioritize to provide greater agility and capabilities. With unified, customizable dashboards, you can quickly analyze compliance and security risk posture across the entire organization and its business units. Customizable widgets make it easy to drill down into the security posture of assets, identify drift from best practices, check assets’ health and prioritize remediation action to fix misconfigurations based on criticality and other factors.
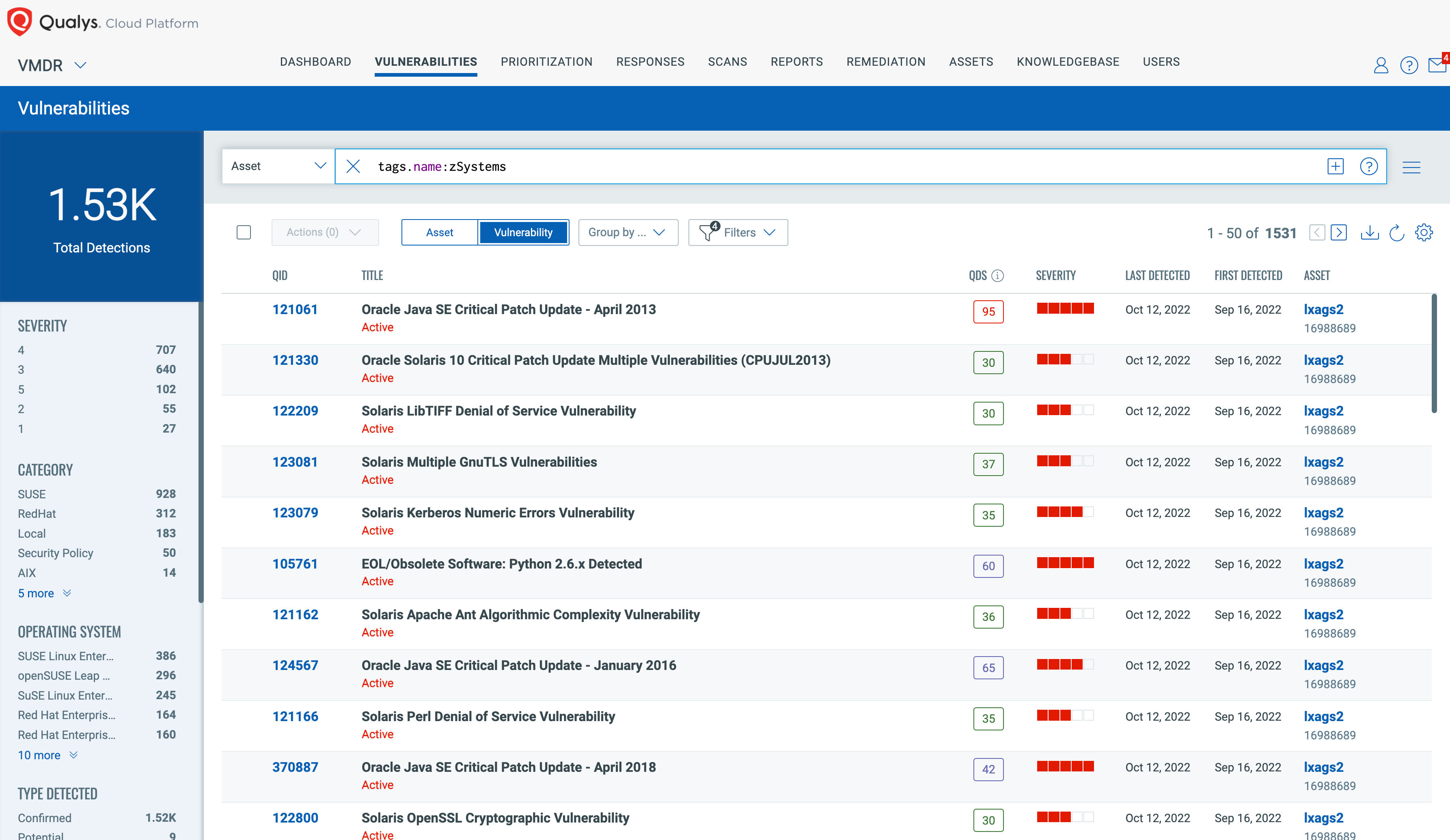
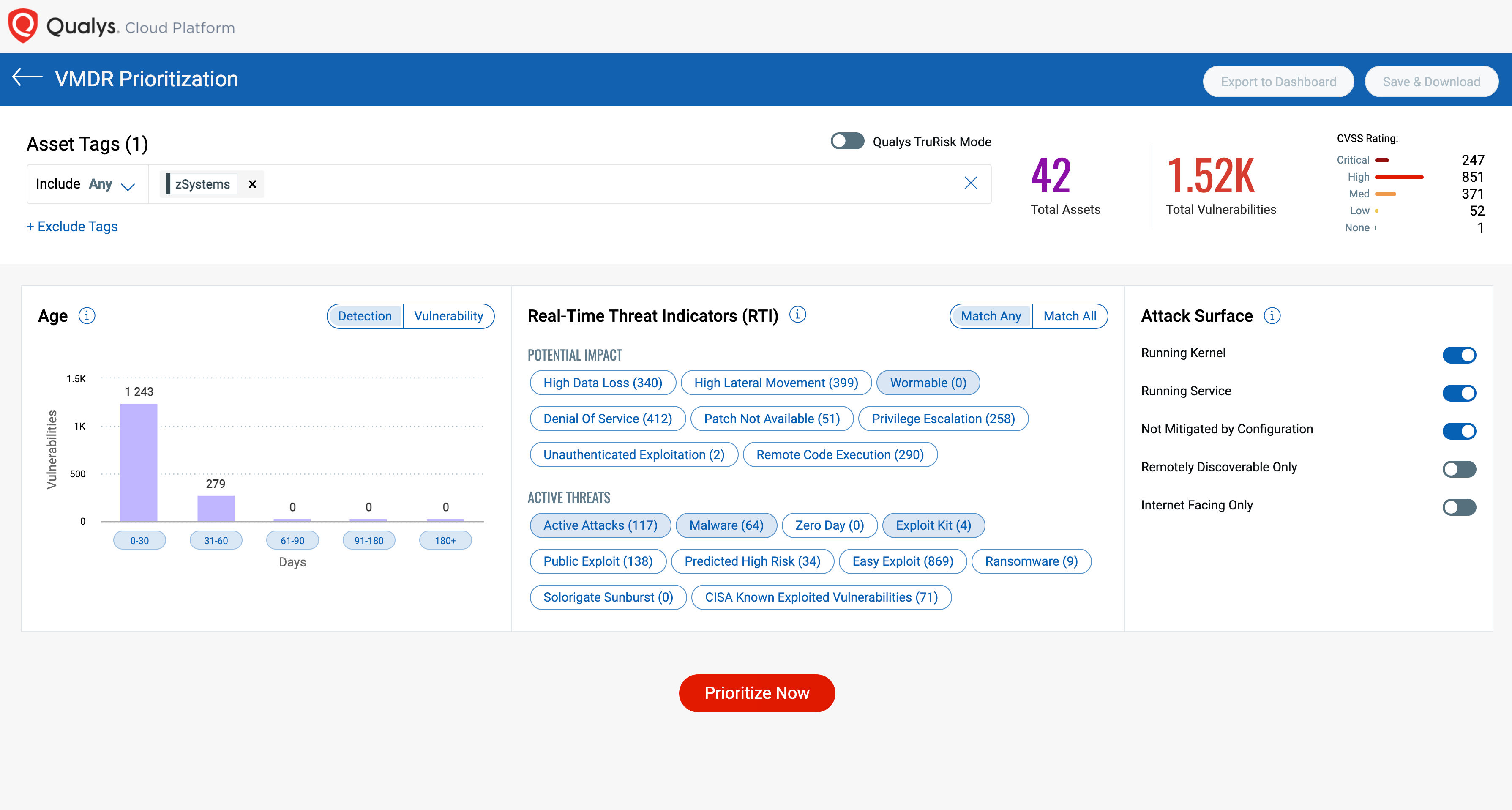
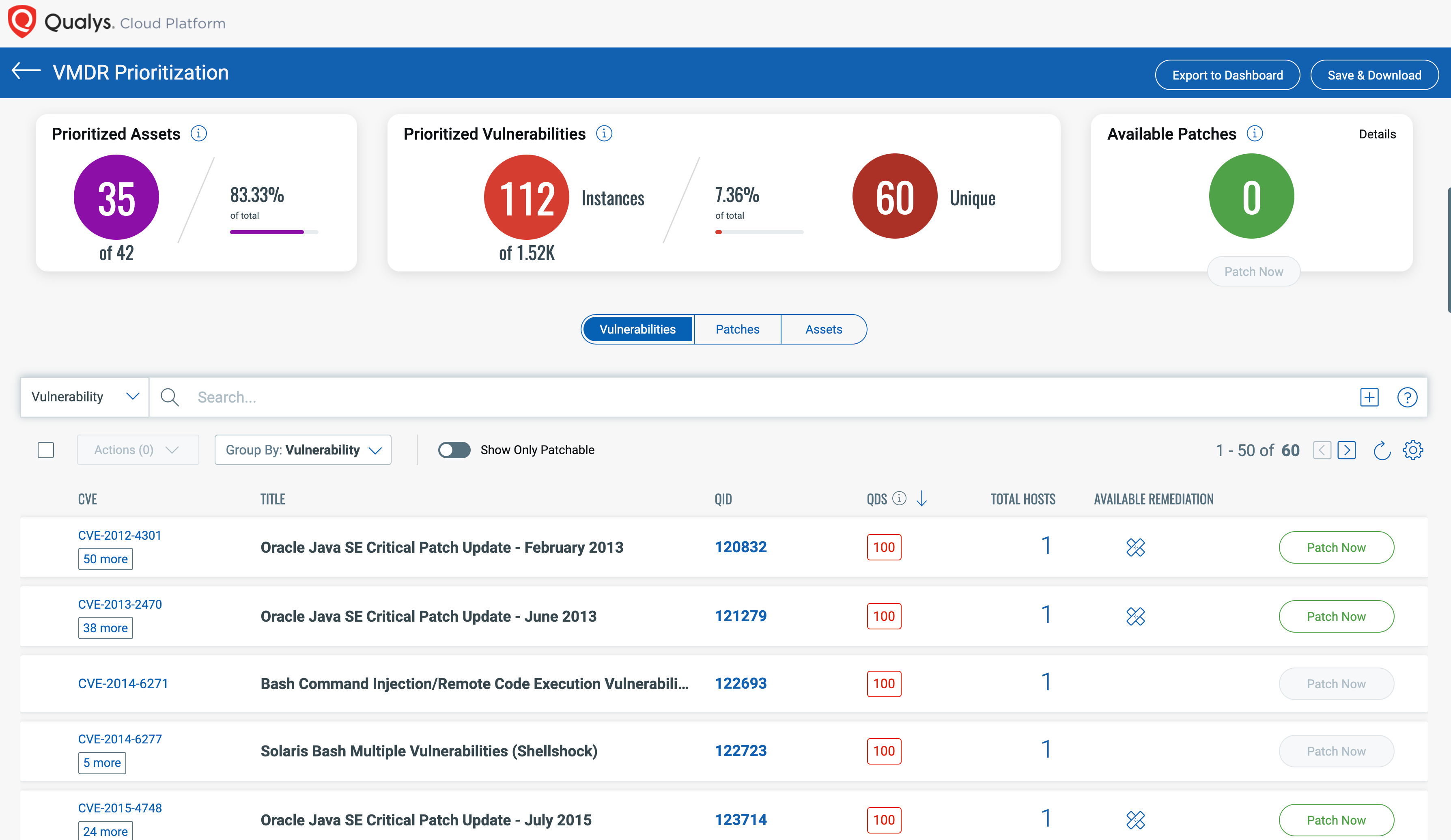
Policy Compliance Assessments for IBM zSystems and LinuxONE
With Qualys Policy Compliance (PC), organizations can leverage out-of-the-box library content to fast-track compliance assessments on IBM zSystems servers using industry-recommended best practices such as Center for Internet Security (CIS) Benchmarks and DISA STIG policies, which you can fully customize to meet your organization’s unique needs. Qualys’ comprehensive policy compliance reports provide the details you need to make informed compliance and risk decisions to prevent security audits and risks.
Qualys Policy Compliance also provides intuitive and accessible workflows for assessing, monitoring, reporting, and remediating security-related configuration issues.
Qualys PC’s content-rich policy libraries for IBM zSystems and LinuxONE provide ready-to-use security policies that are highly scalable and easy to deploy. Qualys’ controls and compliance checks can point to vulnerabilities and potential weaknesses in microservices with absolute precision.
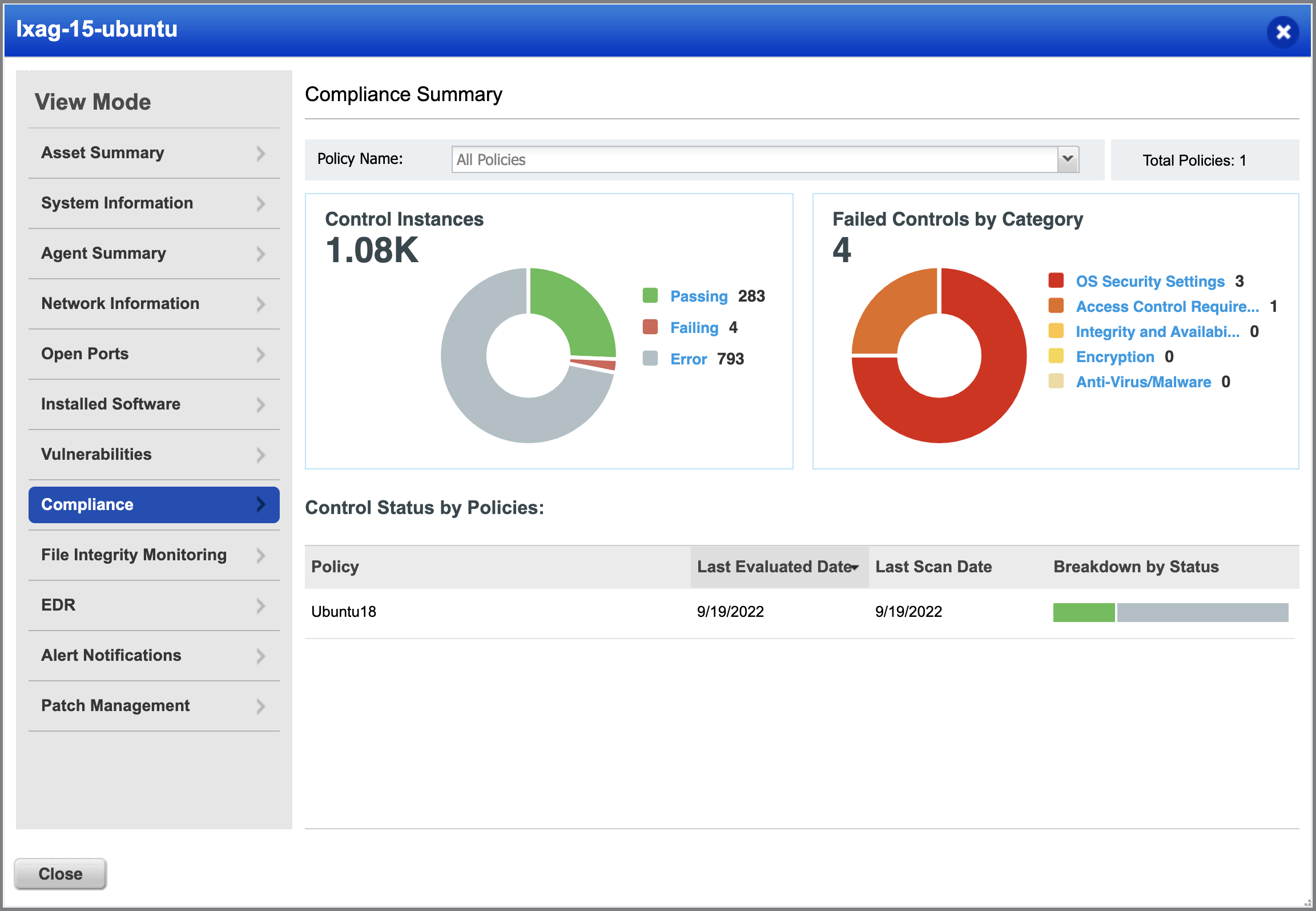
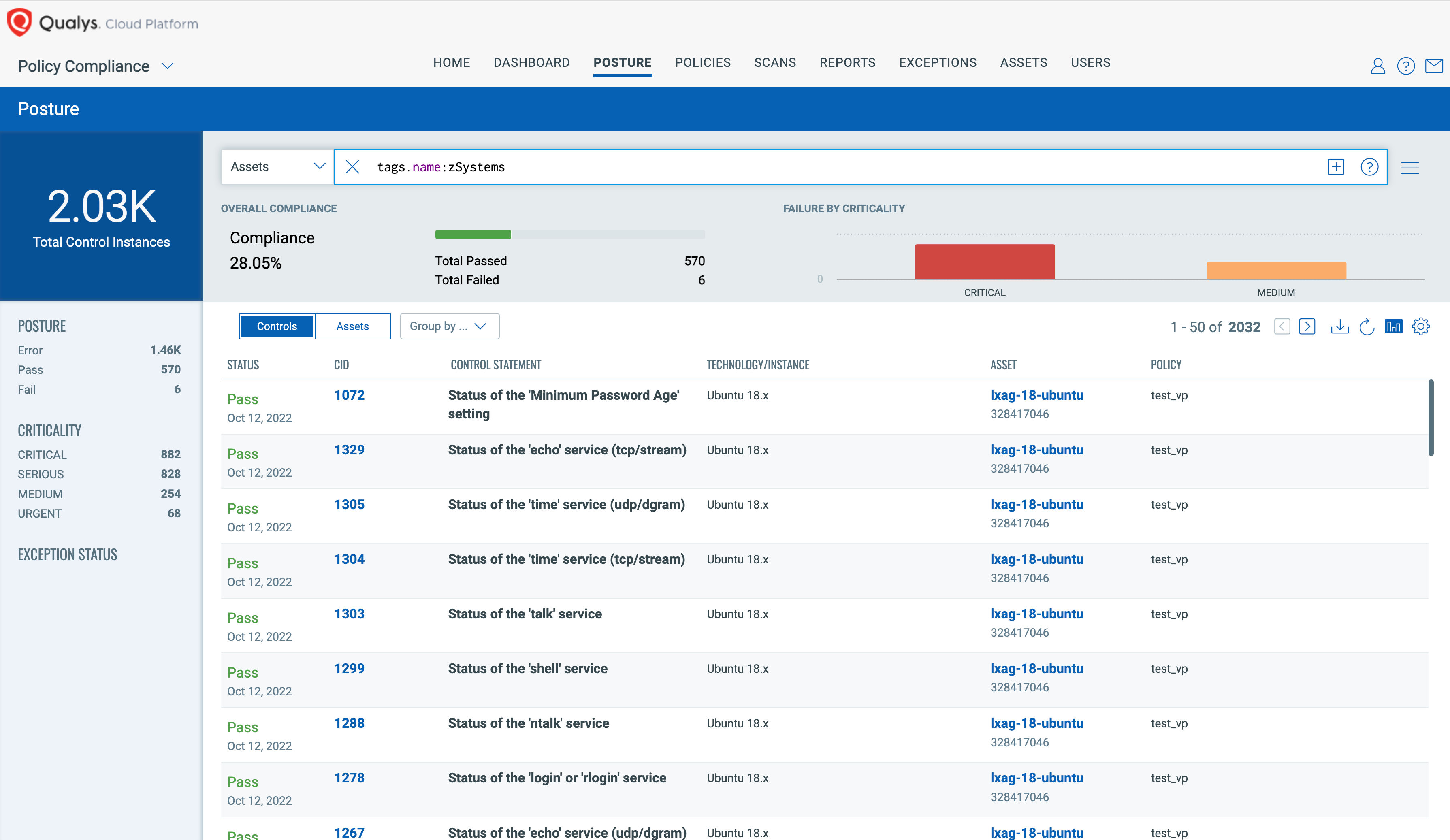
The compliance posture of Controls and Assets with zSystems and databases running on zSystems can be viewed under the Posture tab, as shown below. The posture tab enables you to track compliance posture based on assets, criticality, technologies, and other factors to prioritize and remediate high-risk assets.
We have included a short tutorial video to complement this blog. View the video to learn how to use Qualys Cloud Agent for zSystems and LinuxONE.
Hybrid Coverage now includes Robust IBM Mainframe Systems
In summary, to reduce an organization’s attack surface, strengthen its security posture, and meet compliance mandates, all systems and running applications must be continuously assessed for vulnerabilities and misconfigurations. Qualys is now available on IBM zSystems, which means mainframes, distributed systems, cloud assets, and more are all protected by a single, comprehensive, integrated solution, and organizations can get a unified and comprehensive security risk posture.
With the Qualys platform, you can rest assured that all your assets on global hybrid zSystems environments are covered with six sigma accurate vulnerability detection, risk prioritization, integrated remediation options and configuration compliance for multiple technologies.
Get Started
To learn more on how Qualys for IBM zSystems and LinuxONE can help with security and compliance in your organization:
- Contact your Qualys Technical Account Manager
- Start a Qualys Trial at no extra cost.