Implement Risk-Based Vulnerability Management with Qualys TruRisk™ : Part 1

For today’s CISOs, managing cyber risk is Job #1 priority, and it’s a full-time concern. Security practitioners are spending a considerable amount of time responding to cybersecurity threats and finding ways to reduce risk from threats that are unknown.
Earlier this year Qualys introduced Qualys VMDR with Qualys TruRiskTM which helps organizations quantify cyber risk so that they can accurately measure it, take steps to reduce exposure, track risk reduction trends over time, and better measure the effectiveness of their cyber security program.
Qualys TruRisk™ is a new approach to prioritize vulnerabilities, assets, and groups of assets based on the actual risk, or the “true risk” (pun intended), they pose to the organization. This allows organizations to focus on up to 85% fewer critical vulnerabilities compared to CVSS based prioritization.
In a recent analysis, Aflac was able to reduce risk by 55% by leveraging Qualys TruRisk™ to focus on the highest risk first.
To help organizations realize similar benefits we are doing a three part series on how organizations can operationalize Qualys TruRisk™ in their respective environments to effectively manage and reduce cyber risk.
Identify Crown Jewels
Assign Asset Criticality
Qualys TruRisk™ is designed to quickly identify high-value assets with critical vulnerabilities. Asset criticality plays a key role in identifying high-value assets. When integrated with ServiceNow CMDB, Qualys VMDR automatically imports business criticality for assets.
But for organizations that don’t have an accurate CMDB, asset tagging is a key capability to operationalize Qualys TruRisk™. Asset tagging helps organizations organize assets within the organization. They can apply tags manually or configure rules for the automatic classification of your assets in logical, hierarchical, business-contextual groups. Assign Business Criticality through tags to establish priorities, and automatically calculate the asset criticality score of an asset based on the highest aggregated criticality. The most powerful use of tags is accomplished by creating a dynamic tag. Using a dynamic tag, the service automatically assigns tags to the assets based on search criteria in the dynamic tagging rule.
You can define asset criticality and risk in the following ways:
- Dynamically manage the risk across your assets in your organization.
The dynamic nature of the assets also makes the associated risk dynamic. E.g. Today the OS of the database is not EOL (End Of Life) or EOS (End of Service) then the risk associated with the database asset is less however when the same OS or any software is running on that asset is EOL or EOS then automatically the associated risk will go high. Another example is if an asset that was not exposed publicly and now is exposed publicly in that case the associated risk will automatically go high.
Using the Qualys dynamic tags you can achieve to track the dynamic risk associated with your assets. Assing the criticality score to the dynamic tags and define the rules accordingly to track the dynamic risk. Refer to the below section for more details. - Assign and manage the risk of assets considering the business aspect defined in CMDB.
If you have a CMDB and you are defining the asset criticality based on the business aspect then you can sync the defined criticality from the CMDB to Qualys to add more criticality context based on your organization consideration for that asset. Refer to the further section of the blog for more details on how to sync assets from CMDB to Qualys
Create tags (Static and Dynamic) and assign the asset criticality
You can configure the tags with asset criticality in the CSAM and Global AssetView apps. Navigate to CSAM > Tags
Click on the “Create Tag” button to add the basic details.

Enable the Asset Critically Score and assign the criticality from a 1-5 scale based on your business context
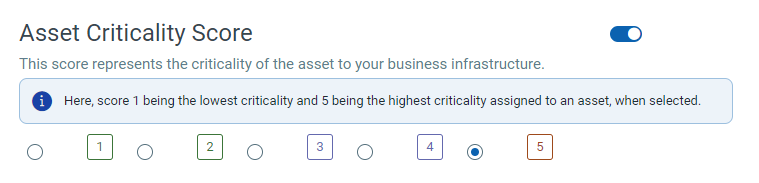
You can create static and dynamic tags based on your requirement. However, we recommend you use the dynamic tag to automate the association with assets based on search criteria in the dynamic tagging rule
Let’s go through a few dynamic tag examples that will help you to track the dynamic risk associated with the assets.
- Servers are a critical component of the asset inventory. You can create a dynamic tag “Server Criticality 3” using the QQL –
and assign the criticality as 3. Now, on the evaluation of the dynamic tag, it will assign this tag and criticality to all existing server assets detected in your eco-system automatically. It will also get assigned to the newly added server if you add any in the future automatically.operatingSystem.category:Server and hardware.category2:`Server`
- Now if the OS of the server becomes EOL/EOS then the criticality of that server assets would be higher as compared to the server without an EOL/EOS operating system. You can create a dynamic tag “Server Criticality 5” for EOL/EOS OS using QQL –
The dynamic tags on evaluation check if any EOL/EOS OS is running on any of the servers. If found then automatically assign the tag and increase the criticality to 5 which helps to bring these assets into your radar to take remediation action.operatingSystem.category:Server and operatingSystem.lifecycle.stage:EOL/EOS and hardware.category2:`Server`
- Tracking public-facing assets are very important as they are more risky assets than that internal-facing assets. Cloud itself is dynamic and the same is inherent in the cloud instances. You can create dynamic tags “AWS Public Instances” for public-facing AWS Assets using QQL –
and assign criticality as 4. On evaluation, it will assign the tag and criticality to all public-facing AWS EC2 instances for better tracking.aws.ec2.publicIpAddress:*
- Track assets with specific software installed then you can create dynamic tags using QQL software –
and assign the criticality based on your requirement. Here you can replace ‘OpenSSL’ with the software name for which you want to track and assign the criticality.name:openssl
- You can also create dynamic tags based on the asset name using QQL-
and assign the criticality based on your requirement.asset.name:pci
Update existing tags to assign the asset criticality
If tags are already created, then you can easily assign the asset criticality by editing the tag. Enable the Asset Criticality Score and set the score.
If the asset has multiple tags associated with different asset criticality scores, then the maximum asset criticality score among the tags will be considered. As per the below screenshot, the maximum asset criticality score among the associated tags is ‘4’, and ‘4’ is set as the criticality score.
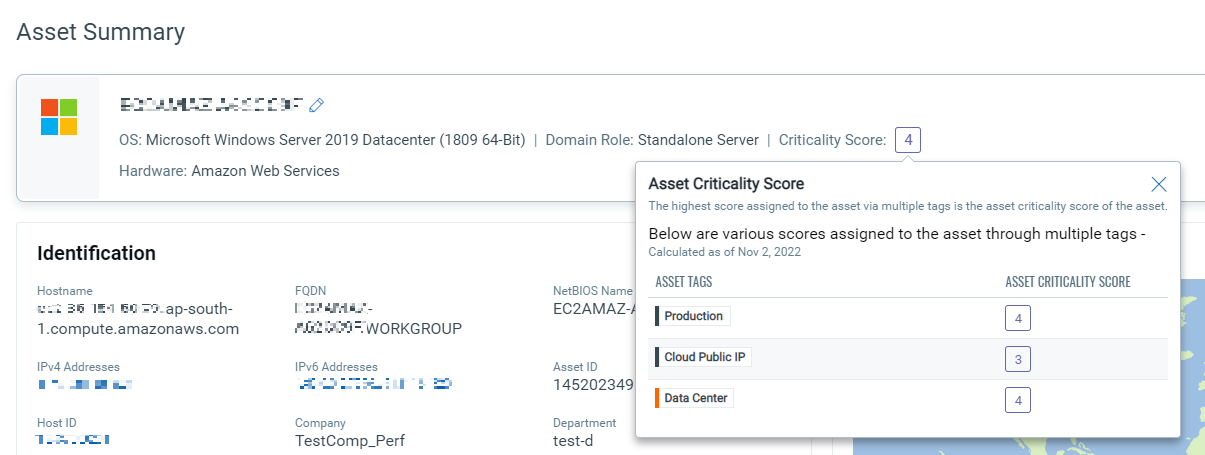
If the tags associated with your assets do not have a criticality score set, by default the asset criticality score ‘2’ will be applied to that asset. We recommend you set an asset criticality score for correct risk score evaluation. For more information on configuring Asset Criticality refer to the step-by-step guide.
Leverage APIs to set asset criticality
You can also leverage the APIs to set the asset criticality.
Create Tag API – /qps/rest/2.0/create/am/tag.
Sample of creating an asset tag and assigning a criticality score
API request
curl -n -u "USERNAME:PASSWORD" -H "content-type: text/xml"-X "POST" -- "https://qualysapi.qualys.com/rest/2.0/create/am/tag" < file.xml Note: “file.xml” contains the request POST data.
Request POST data
<?xml version="1.0" encoding="UTF-8" ?> <ServiceRequest> <data> <Tag> <name>External_Facing</name> <criticalityScore>4</criticalityScore> <color>#FFFFFF</color> </Tag> </data> </ServiceRequest>
Response
<?xml version="1.0" encoding="UTF-8"?> <ServiceResponse xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:noNamespaceSchemaLocation="https://qualysapi.qualys.com/qps/rest/2.0/create/am/tag"> <responseCode>SUCCESS</responseCode> <count>1</count> <data> <Tag> <id>7824612</id> <name> External_Facing </name> <created>2021-06-08T13:09:00Z</created> <modified>2021-06-08T13:09:00Z</modified> <color>#FFFFFF</color> <criticalityScore>4</criticalityScore> </Tag> </data> </ServiceResponse>
Update Tag API
- /qps/rest/2.0/update/am/tag/
- /qps/rest/2.0/update/am/tag
Sample of Updating an asset tag with criticality score and tag ID in URL
API request
curl -n -u "USERNAME:PASSWORD" -H "content-type: text/xml"-X " "POST" -- "https://qualysapi.qualys.com/rest/2.0/update/am/tag/11175413" < file.xml Note: “file.xml” contains the request POST data.
Request POST data
<?xml version="1.0" encoding="UTF-8" ?> <ServiceRequest> <data> <Tag> <name>name change3</name> <criticalityScore>5</criticalityScore> <children> <remove> <TagSimple> <id>123</id> </TagSimple> <TagSimple> <id>456</id> </TagSimple> </remove> </children> </Tag> </data> </ServiceRequest>
Response
<?xml version="1.0" encoding="UTF-8"?> <ServiceResponse xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:noNamespaceSchemaLocation="https://qualysapi.qualys.com/qps/rest/2.0/update/am/tag"> <responseCode>SUCCESS</responseCode> <count>1</count> <hasMoreRecords>false</hasMoreRecords> <data> <Tag> <id>11175413</id> </Tag> </data> </ServiceResponse>
You can refer to Asset Management and Tagging API v2 user guide for more information.
Leverage CMDB Sync to automatically set criticality
If you are using CMDB then you can leverage the Qualys CMDB Sync Service Graph Connector App for Configuration Management Database (CMDB) automatically synchronizes comprehensive information about your global IT resources that are continuously monitored by Qualys Asset Inventory. CMDB sync to sync assets from CMDB to Qualys
The mapping of business capabilities is an important step in calculating the Qualys Asset Criticality Score from App/Services Business Criticality. The business criticality mappings provide a connection between the Business Applications Criticality and the Qualys Criticality.
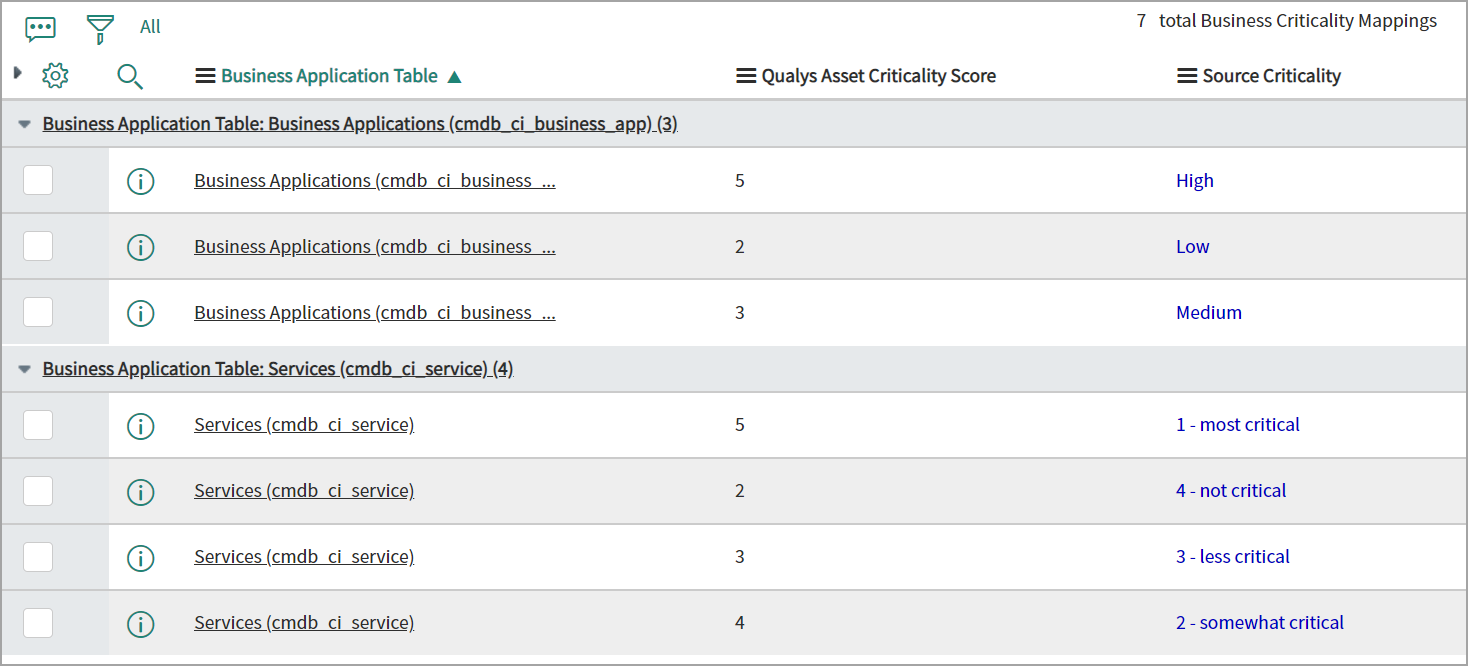
The business criticality mapping will be used while creating the tags for the asset criticality score. Asset criticality will be mapped to Business Name tags only.
The Qualys TruRisk™ score is evaluated during the asset scan. On each scan, the score is updated. Once you create proper tags with asset criticality as per your organization’s requirement you don’t need to do any additional configurations for the Qualys TruRisk score evaluation.
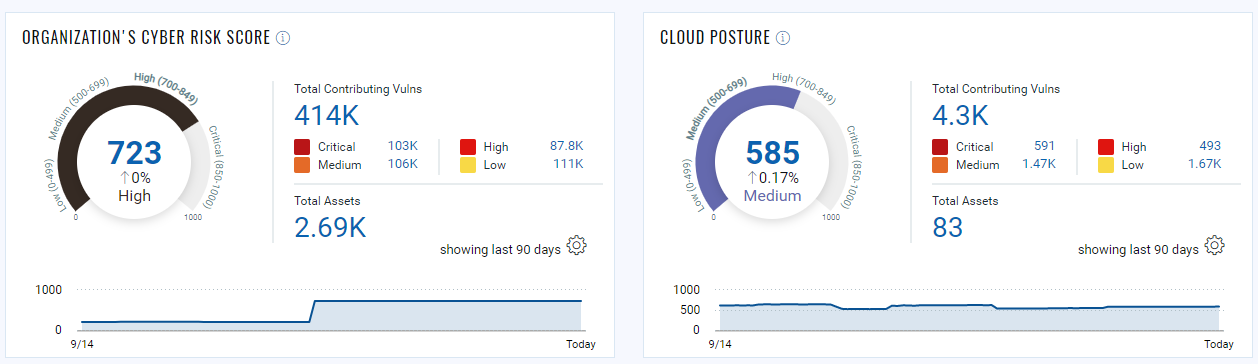
Hope you enjoyed reading this blog and learned a few tips and tricks to operationalize Qualys TruRisk™ in your environment. In the next part, we will discuss how these steps can help you visualize and measure risk in your environment. Stay tuned.
Start your free trial of Qualys VMDR with Qualys TruRiskTM
Read the following blogs for more information on VMDR integration with CMBD and ITSM