Augment Security Asset Tagging with Custom Assessment and Remediation (CAR)
Table of Contents
Security asset tagging provides a flexible and scalable way to organize the assets in your environment based on specific requirements. It enables you to create tags and assign them to your assets, which can improve your cybersecurity maturity and reduce risks for breaches and audit failures. Qualys Cybersecurity Asset Management (CSAM) provides an excellent way to create standard tags, and Qualys Custom Assessment and Remediation (CAR) allows you to extend this capability when more advanced and customized tagging is needed.
For example, Qualys CAR can be leveraged to assign asset tags based on specific conditions, such as tagging Linux hosts where the audit system is in an immutable mode, or tagging Windows hosts where Windows Subsystems for Linux (WSL) has been enabled. Also, tagging hosts where password policies are misconfigured, or hosts where unsigned binaries are found, etc.
In this blog, we’ll provide an example of how to use CAR for sensitive data tagging.
Sensitive data often includes confidential information that must be protected from unauthorized access. As noted in the Protecting Personal Information Guide by the Federal Trade Commission, the first key principle that describes a sound data security plan advises organizations to TAKE STOCK and determine what personal information resides in files and on computers.
Let’s dive into this use case, where assets with sensitive information need to be tagged as ‘Sensitive Assets’.
Step 1 – Create a static asset tag named ‘Sensitive Asset’ in Qualys CSAM
Step 2 – Go to Qualys CAR and import the ‘Sensitive data discovery’ script from the Qualys Script Library. This script scans the entire file system for sensitive information and leverages CSAM APIs to assign the tag to the host.
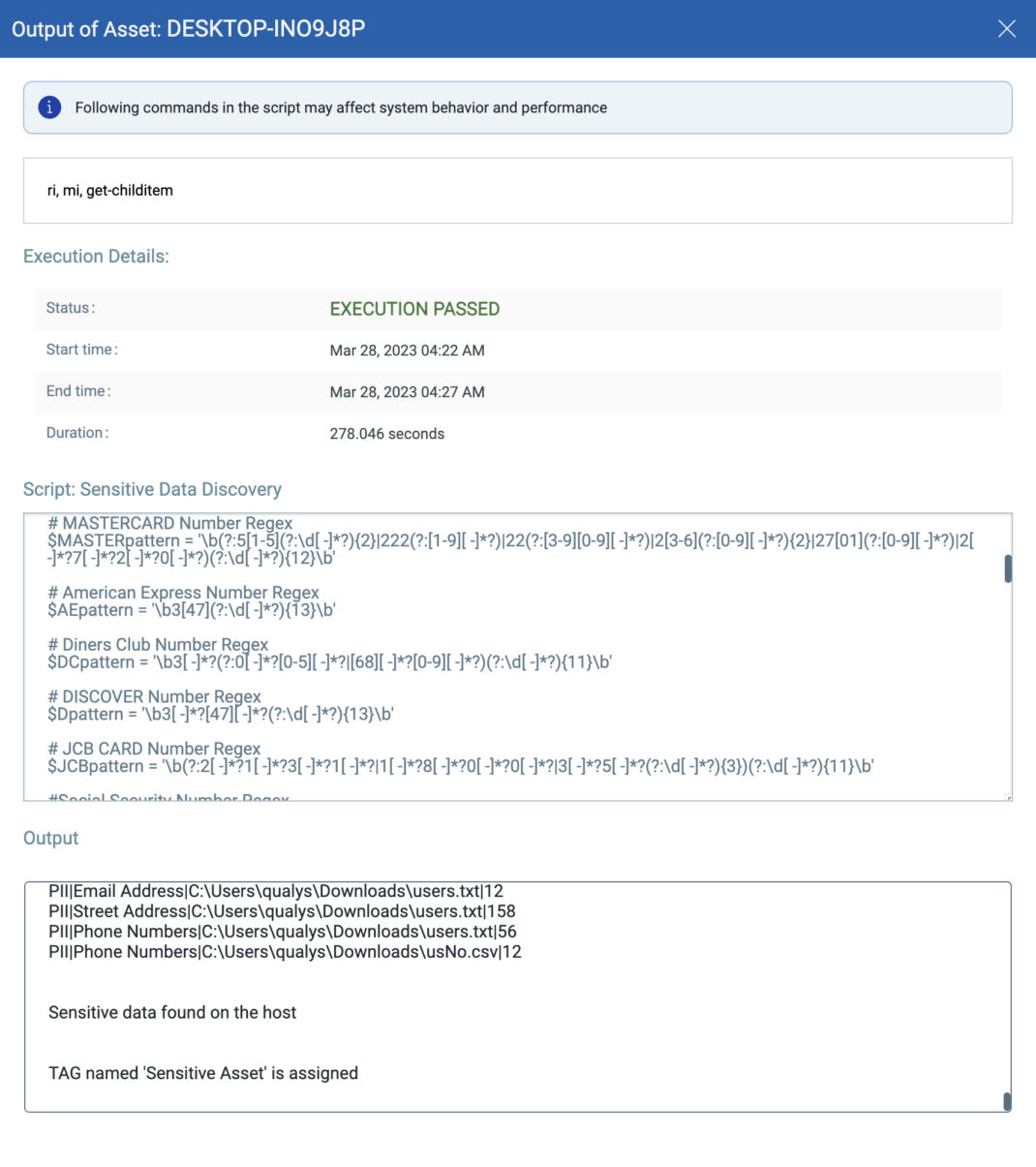
Check the script output under the asset job. The output lists sensitive data such as:
- Electronic Protected Health Information (ePHI)
- Payment Card Information (PCI)
- Personally Identifiable Information (PII) such as Social Security Numbers (SSN) or other identifying numbers or codes, telephone numbers, email addresses, etc.
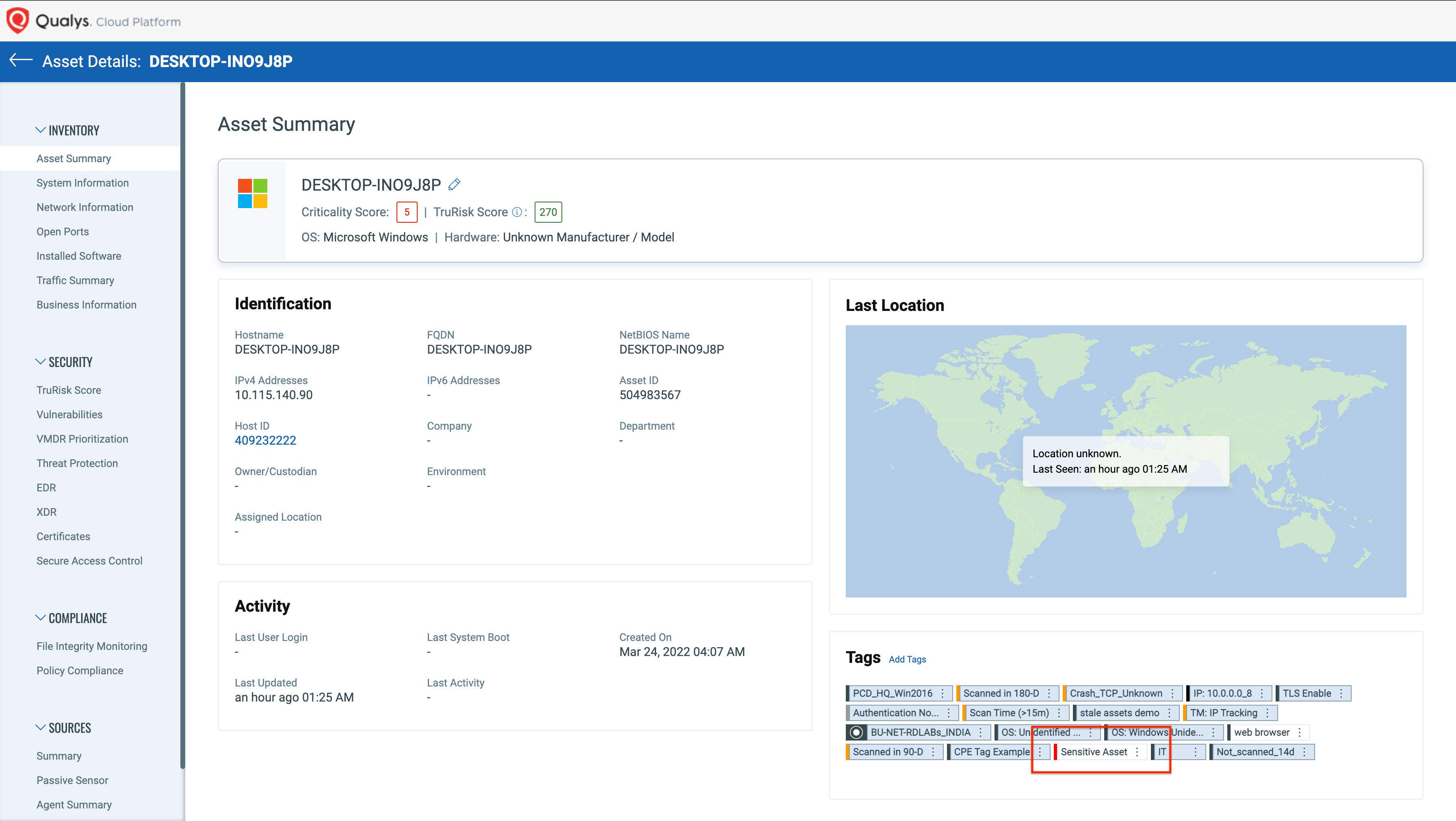
Script execution can be scheduled for the auto assignment of tags. To verify the tag association, check for the asset details and assigned tag.
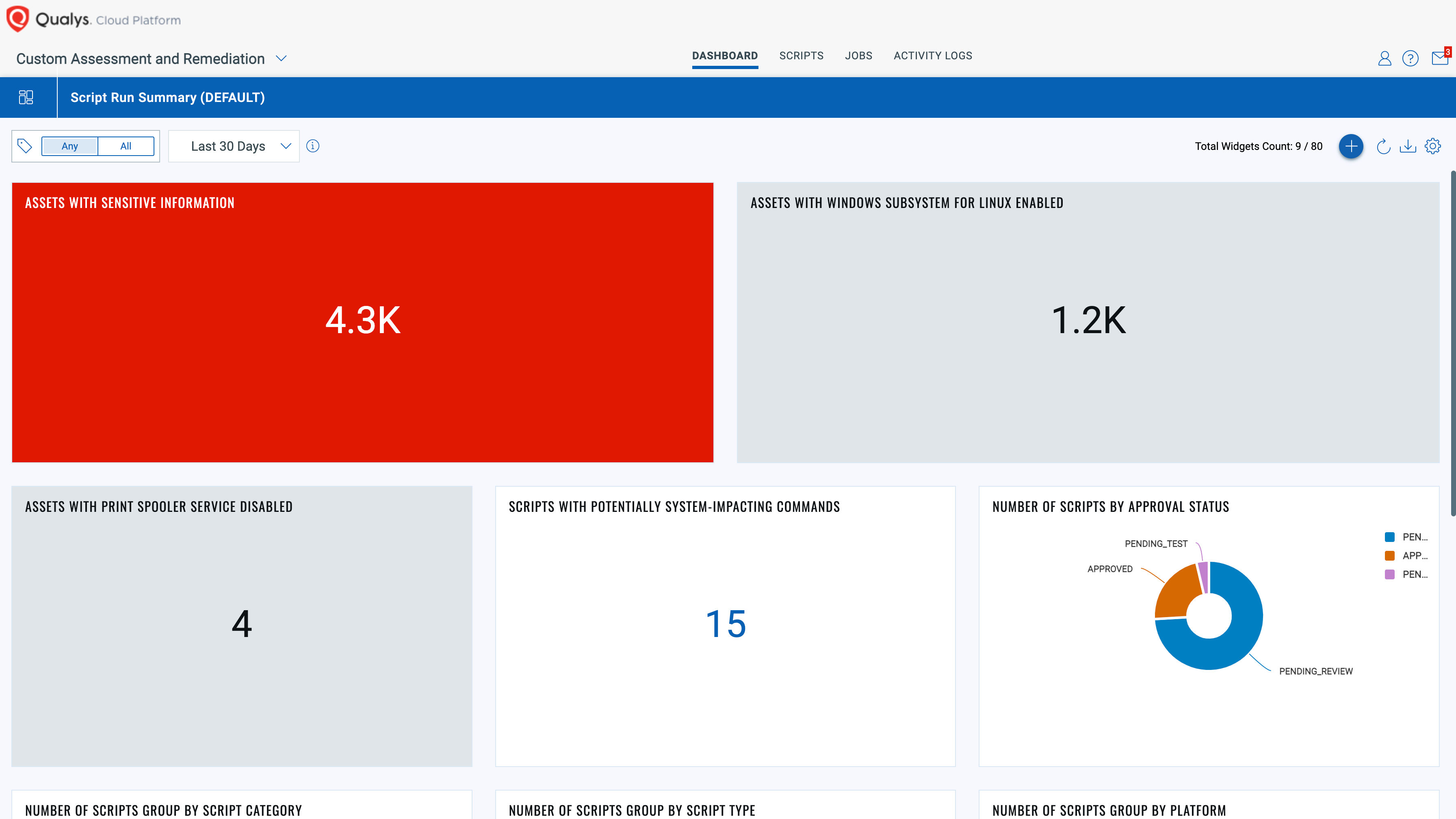
Create dashboards for better visualization
Once this is done, another script, such as ‘sensitive data protection’ from the Qualys Library, can be run on the newly tagged host to encrypt the sensitive data.
Asset tagging can be a vital requirement to ensure flexibility and scalability when organizing assets based on specific requirements. It enables you to create tags and assign them to your assets, which can improve your cybersecurity maturity and reduce risks for breaches and audit failures. As part of the Qualys Cloud Platform, Qualys Cybersecurity Asset Management (CSAM) and Custom Assessment and Remediation (CAR) help you to simplify, streamline, and improve your asset tagging capabilities to reduce cybersecurity and compliance risks.
Free Trial
Start a no-cost trial to explore how Qualys CSAM and CAR can help your organization.
Learn More
- CAR API User Guide
- Blog – https://blog.qualys.com/vulnerabilities-threat-research/2022/09/28/remediate-your-vulnerable-lenovo-systems-with-qualys-custom-assessment-and-remediation
- Blog – https://blog.qualys.com/product-tech/2022/05/20/put-secops-in-the-drivers-seat-with-custom-assessment-and-remediation
- CAR Datasheet