CVSSv4 Public Preview Announcement
On June 8, 2023, at the 35th Annual FIRST Conference in Montreal, the public preview of CVSSv4 was announced. The Common Vulnerability Scoring System (CVSS) is an open framework for communicating the characteristics and severity of software vulnerabilities. Since its initial release in 2004, CVSS has enjoyed widespread adoption. It is used by the industry and government agencies for accessing the severity of the vulnerability and helping consumers prioritize and drive remediation for vulnerabilities.
In this blog post, we will review some of the most notable changes between CVSSv3.1 and CVSSv4.
About CVSS
The Common Vulnerability Scoring System (CVSS) is an open framework for communicating the characteristics and severity of software vulnerabilities. CVSS is owned and managed by FIRST.Org, Inc. (FIRST), a US-based non-profit organization, whose mission is to help computer security incident response teams across the world. Since its initial release in 2004, CVSS has enjoyed widespread adoption. In September 2007, CVSS v2.0 was adopted as part of the Payment Card Industry Data Security Standard (PCI DSS). In March 2016, CVSS v3.0 was formally adopted as an international standard for scoring vulnerabilities.
CVSSv3.1 Vs CVSSv4.0
The figure below provides an overview of the changes between CVSSv3.1 vs CVSSv4.0.
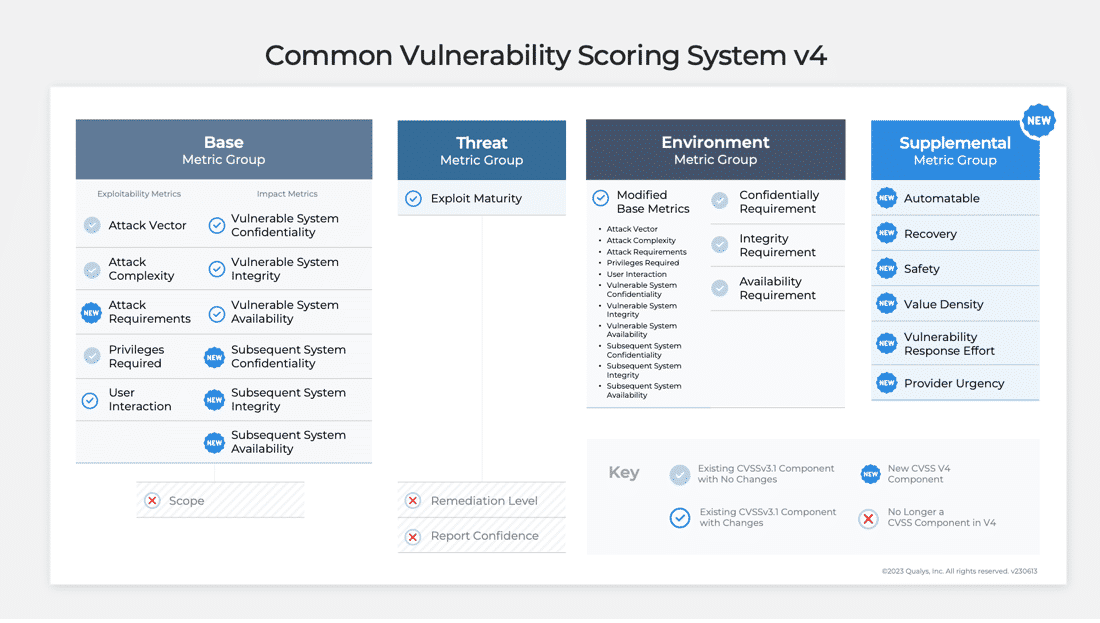
What Is New In CVSSv4.0?
Nomenclature
The CVSS framework always consisted of three metric groups, i.e. Base, Temporal, and Environment. However, due to the popularity of the CVSS Base Score, it became synonymous with the overall CVSS score. CVSS score is not just a base case. To stress the importance of this, the following new nomenclature was adopted by CVSSv4:
| CVSS Nomenclature | CVSS Metrics Used |
|---|---|
| CVSS-B | Base metrics |
| CVSS-BE | Base and Environmental metrics |
| CVSS-BT | Base and Threat metrics |
| CVSS-BTE | Base, Threat, Environmental metrics |
Supplemental Metric Group
CVSSv4.0 introduces a new optional metric group called the “Supplemental Metric Group.” It provides metrics that describe and measure additional extrinsic attributes of a vulnerability. The Supplemental Metric Group aims to provide contextual information that consumers can use to take additional actions that help them in further risk analysis. It is important to note that Supplemental metrics are optional, and they do not have any impact on the calculated CVSS scores. Supplemental metrics to help you better understand extrinsic questions about vulnerabilities include:
| Safety | Does exploiting this vulnerability have a safety impact on an organization? |
| Automatable | Are attackers able to automate exploitation of this vulnerability? |
| Recovery | After an attack are the systems/component able to self-recover? |
| Provide Urgency | What is the rating provided by the vendor for this vulnerability? |
| Value Density | What resources will the attacker gain control over with a single exploitation event? |
New Base Metric: Attack Requirement (AT):
The new Attack Requirement (AT) metric aims to provide more granularity than provided by the “Attack Complexity (AC)” metric. This new metric captures the prerequisite deployment and execution conditions or variables of the vulnerable system that enable the attack.
Attack Complexity – Reflect the exploit engineering complexity required to evade or circumvent defensive or security-enhancing technologies. (Defensive measures)
Attack Requirements – Reflect the prerequisite conditions of the vulnerable component that make the attack possible.
What was updated/removed in CVSSv4.0?
Rename and Simplified Threat Metrics:
CVSSv4.0 renamed the “Temporal” Metric from CVSSv3.1 to “Threat Metrics.” CVSSv4.0 also retired the “Remediation Level (RL)” and “Report Confidence (RC)” metrics. In addition, the “Exploit Code Maturity (E)” was renamed to “Exploit Maturity (E).” The “High (H)” and “Functional (F)” values for this metric in CVSSv3.1 were also merged into one value of “Attacked (A)” in CVSSv4.0.
Update Base Metric: User Interaction (UI):
This metric captures the requirement for a user, other than the attacker, to participate in the successful compromise of the vulnerable component. CVSSv4.0 proposes the User Interaction (UI) metric to be more granular. CVSSv3.1 the User Interaction (UI) metric had values None(N) or Required(R). With CVSSv4.0 this metric now provides more granularity to the amount of interaction required as Passive (P) or Active (A). See more details at: https://www.first.org/cvss/v4.0/specification-document
Retired Base Metric: Scope (S):
One of the CVSSv3.1 Base Metric of Scope(S) was retired in CVSSv4.0 due to the lack of clarity on the usage of this metric. This led to inconsistent scoring among vulnerabilities by different product providers. Due to this reason, the Scope Metric was retired in favor of two sets of impact metrics:
- Vulnerable System Impact – Confidentiality (VC), Integrity (VI), Availability (VA)
- Subsequent System(s) Impact – Confidentiality (SC), Integrity (SI), Availability (SA)
MISC:
Apart from these changes, CVSSv4.0 provides improved guidance to CVSS analysts to produce consistent scores, guidance on scoring vulnerabilities in software libraries etc. CVSSv4.0 is designed to support multiple CVSS scores for the same vulnerability that affects multiple products, platforms, operating systems, etc. It also provides guidance to extend the CVSS framework for other industry sectors such as privacy, automotive, etc.
How does CVSS 4.0 compare to TruRisk?
CVSS 4.0 represents a decent upgrade compared to CVSS 3.1, primarily due to the renaming of key metrics such as Temporal to Threat Metrics. This change makes it much easier for end users to evaluate the severity of a vulnerability. The inclusion of fine-grained details regarding user interaction required for vulnerability exploitation is also a welcome addition.
However, alongside the beneficial changes in version 4.0, there is also an increase in complexity. One longstanding issue with CVSS ratings has been the potential for inconsistencies in how individuals/vendors rate vulnerabilities. Moreover, with the introduction of more variables, the resulting scores can vary.
Ultimately, when assessing the risk of a vulnerability, the key metric that truly matters is the exploitability (which CVSS 4.0 addresses), evidence of exploitation (which it does not), and the likelihood of exploitation (as referenced by EPSS).
An ideal score is one that takes into account the CVSS rating to evaluate the technical severity and combines it with the exploitability factors referenced above. This is where TruRisk scores come into play, as it assists organizations in assessing the true risk of a vulnerability by considering multiple factors. These scores are designed to be easily understandable, even for non-technical teams, and greatly simplify the implementation of risk-based vulnerability management. See what goes into Qualys TruRisk scores here.
Conclusion:
CVSSv4.0 provides consumers with fine, granular metrics to better understand the technical characteristics of vulnerabilities. With the simplification of Temporal Metrics along with the addition of granular Base and Environmental Metrics, it aims to help consumers better understand the risk of vulnerabilities. With the addition of Supplemental Metrics, CVSSv4.0 consumers will be able to better communicate extrinsic characteristics of vulnerabilities, which will help customers better assess their risk and drive effective remediation.
CVSSv4.0 is still in public preview and open for comments. While there are several new and updated metrics that provide more detailed information, it’s additional work for analysts, and its success will depend greatly on how quickly consumers will adopt it.