Part III: Implementing Effective Cyber Security Metrics that Reduce Risk Realistically

We outlined some critical cybersecurity metrics in Part I of this three-part blog series. In the final blog post, we will delve into three crucial aspects outlined in Josh’s article: tactical metrics for operational teams, strategic metrics for leadership, and the metrics addressing the organization’s technical debt related to end-of-life/end-of-support (EOL/EOS) hardware, software applications, and operating systems.
By leveraging the powerful capabilities of Qualys’ VMDR TruRisk and CyberSecurity Asset Management (CSAM) products, organizations can gain valuable insights, make risk-based decisions, and continue to reduce the organization’s risk.
Tactical Metrics for Operational Teams
In the ever-evolving landscape of cybersecurity, implementing effective metrics is crucial to assess an organization’s security posture. For operational teams, metrics provide valuable insights into the network environment and aid in making informed decisions to mitigate potential risks.
Here are some tactical metrics that operational teams should consider for effective risk reduction.
Introduction of Metrics for General Information Gathering
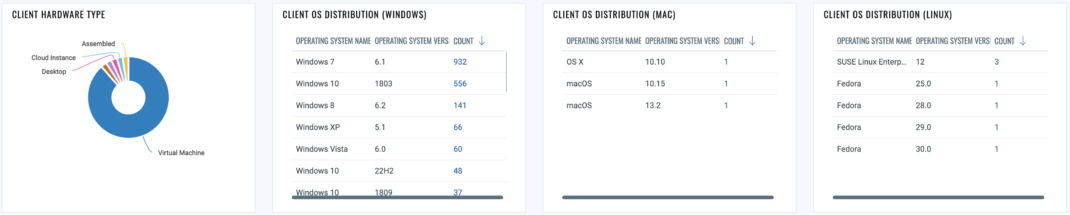
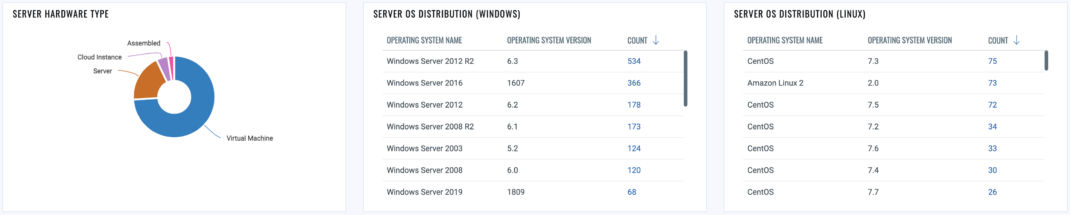
Before diving into the specific metrics, let’s first establish a baseline about the organization’s assets and software. This includes understanding the hardware distribution and associated risks. For instance, differentiating between mobile devices like laptops and tablets versus stationary devices like desktops helps identify unique vulnerabilities, plan targeted mitigations, and implement relevant controls.
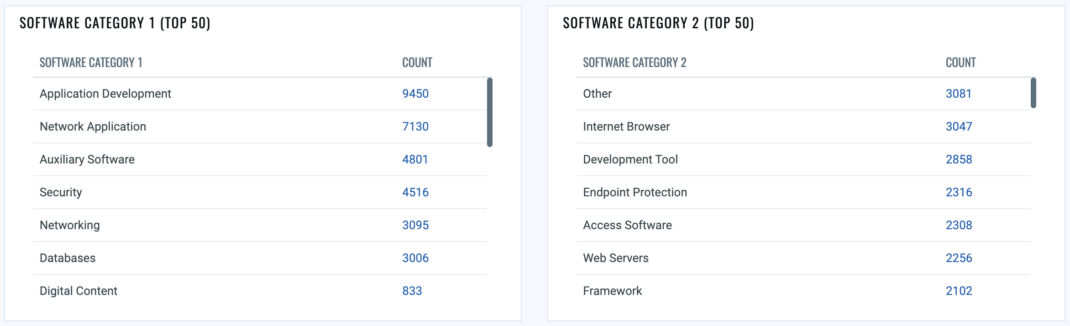
Another crucial aspect of general information gathering is reviewing the installed software in your organization. Although focusing on the top software installed on clients and servers is essential, paying more attention to the bottom ‘X’ software installed on your assets is equally vital. Often, suspicious software might lurk in lesser-known software categories. Therefore, uncovering such overlooked software is critical to reduce the risk and bolster the organization’s cybersecurity posture.
Additionally, employing advanced tools like Qualys (CSAM) can significantly aid operational teams in identifying critical software that may be missing on assets within the environment. The organization can reduce the attack surface and enhance its overall security or response capabilities by ensuring all essential software components are in place, running, and current.
Critical Operations Agent Coverage for Applicable/Compatible Assets
Agents (security, IT operations, etc.) play a decisive role in gathering real-time security data from devices across the organization. Assessing the coverage of these agents is a tactical metric that operational teams must focus on. It involves identifying the number of Qualys agents deployed in the organization compared to those missing on compatible devices, both clients and servers.
A comprehensive and up-to-date agent coverage ensures that security teams receive timely information, allowing them to respond promptly to potential threats and vulnerabilities. Moreover, it helps ensure that devices crucial for the organization have the necessary agents deployed to monitor their activity effectively and prevent risks to neighboring assets and networks related to compromised assets.
These tactical metrics empower operational teams to gain high visibility into their network environment, identify associated risks, and prioritize remediation efforts for risk reduction. By utilizing these metrics’ insights, organizations can reduce risk by enhancing their cybersecurity posture and thwart any accessible opportunities for an attacker to wreak havoc.
Strategic Metrics for Leadership
As cybersecurity continues to be a top concern for organizations, leadership teams play a significant role in shaping effective risk management strategies. Strategic metrics tailored for senior leadership are critical to making informed decisions and steering the organization toward a resilient security posture.
In the upcoming section, let’s take a look at the key strategic metrics offering valuable insights for leaders.
Qualys VMDR TruRisk Metrics
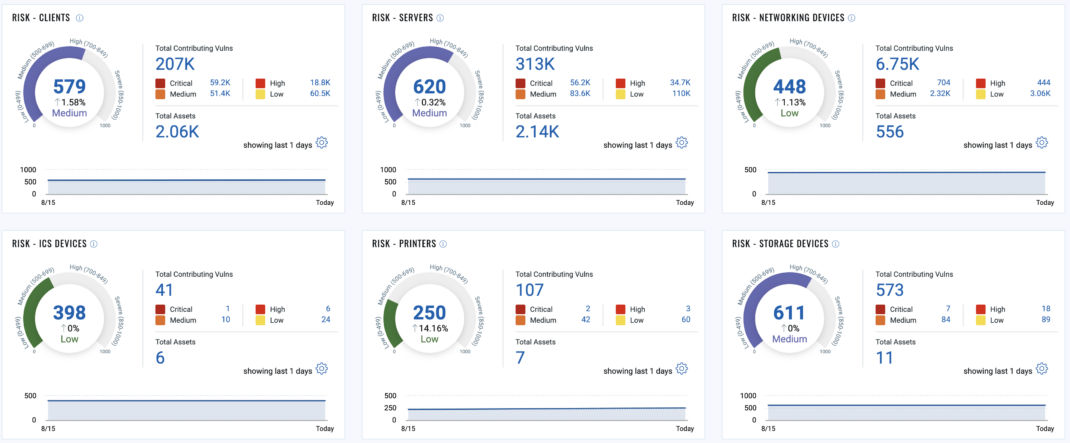
A. Organization-Wide Risk Scoring
Cumulative risk scoring aggregates vulnerabilities and their associated risks across the entire organization. An organization’s leaders gain essential insight into the overall security posture by assessing the cumulative risk. It is, therefore, essential to think through these metrics and the story you are trying to convey. For example, surveying an entire organization’s risk posture may downplay the actual risk because low criticality assets and detected vulnerabilities oversaturate the organization’s averages.
Consider using overall risk metrics for device types (clients, servers, network infrastructure, OT devices, printers, etc.) and device roles across the entire organization. These metrics help identify elevated risk areas, prioritize cybersecurity investments, and focus efforts on critical areas.
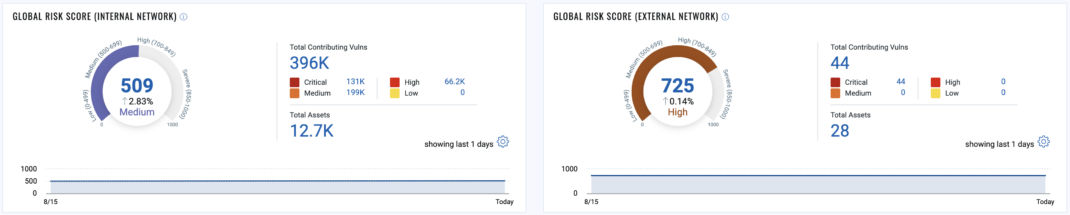
B. Internal Network Vs. External/Internet-Facing Networks
Segmenting risk metrics between internal and external networks provides essential insights into the organization’s threat exposure. Understanding the risk variations helps leaders make targeted decisions to fortify external-facing systems and safeguard sensitive internal assets.
C. Granular Risk Scoring
In contrast, to organization-wide risk scoring, granular risk scoring focuses on more specific areas of the organization. Considering the geographical distribution of an organization’s operations, evaluate risk posture metrics by geographic regions, subsidiaries, or business units. From these more specific areas of your environment, create more specific risk scoring for assets by device type, teams, business impact, etc. This approach allows leaders to allocate resources efficiently and tailor security measures to their own specific unique challenges.
D. Risk Metrics for On-Premise Data Centers versus Cloud Platforms
It is important to compare risk metrics between on-premise data centers and cloud platforms. On-premise data centers typically offer a secured physical environment but may face scaling, resource provisioning, and hardware maintenance challenges. On the other hand, cloud platforms provide impressive scalability, almost limitless flexibility, and managed services. Still, they also introduce new security considerations related to shared responsibility models (distribution of responsibilities related to security between the cloud service provider and customer) and potential misconfigurations.
By evaluating risk metrics for on-premise data centers and cloud platforms, leaders can identify areas that require additional measures to mitigate risk, allocate resources strategically, and balance on-premise and cloud investments based on the organization’s risk appetite and overall business objectives.
Understanding Current Technical Debt
Technical debt refers to the backlog of overdue maintenance and updates to software and hardware in an organization. Identifying technical debt is essential to measuring risk related to outdated devices and software as it directly impacts the organization’s security and operational efficiency. Here are the key metrics related to technical debt that senior leadership should be aware of:
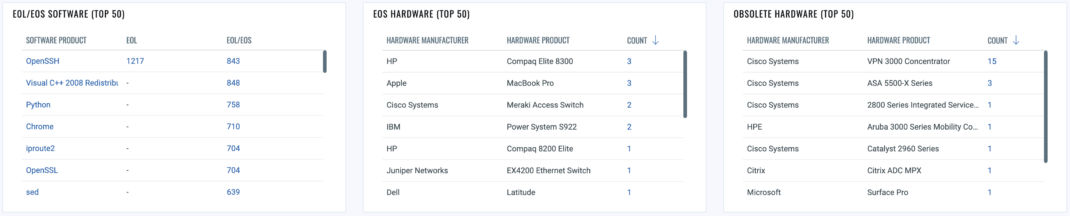
1. Identifying End-of-Life (EOL)/End-of-Support (EOS) Software and Hardware
Obsolete software and hardware present significant risks to an organization. Unsupported systems no longer receive updates and security patches, increasing their vulnerability to exploitation. Highlighting EOL/EOS assets gives leadership an urgent call to action to promptly replace or upgrade these components.
2. Conveying Vulnerabilities and Risks Associated with EOL/EOS Components
Outdated software, hardware, and operating systems lacking security updates and patches become perfect targets for cyber attackers, leading to data breaches and tarnishing the organization’s reputation. In industrial environments, successful exploits can compromise systems and disrupt production processes, resulting in financial losses and contractual issues. Theft of intellectual property, compliance violations, and network breaches further underscores the urgency of addressing your organization’s EOL/EOS assets and other components. By presenting the vulnerabilities and their impacts on the organization’s overall risk, leaders can make informed decisions to invest in upgrades and enhance cybersecurity, safeguarding the organization from potentially devastating attacks.
3. Granular View of Technical Debt Metrics
As mentioned previously, breaking down technical debt metrics further by region, business unit, network zone, or team provides a more granular view of specific areas requiring immediate attention. This level of detail enables leadership to allocate resources strategically and address critical vulnerabilities promptly by being able to pinpoint specific components in their environment and engage appropriate device owners and other key stakeholders.
Metrics for Identifying and Reducing Technical Debt
As organizations continue to navigate the complexities of cybersecurity, addressing technical debt is crucial to maintaining a robust security posture. In the following section, let’s now explore metrics that aid in identifying and reducing End-of-Support (EOS) and End-of-Life (EOL) components, empowering organizations to mitigate risks effectively.
Identifying EOS/EOL Hardware, Applications, and Operating Systems using Qualys CSAM
Querying and Determining Prevalent EOS/EOL Categories
Leveraging Qualys CSAM, organizations can easily query and identify all EOS/EOL categories, such as hardware, applications, and operating systems. Monitoring these metrics provides valuable insights into the extent of technical debt in the environment. By tracking the presence of outdated components, security teams can prioritize remediation efforts, ensure that vulnerable assets are promptly upgraded or replaced, and monitor remediation efforts using trend data.
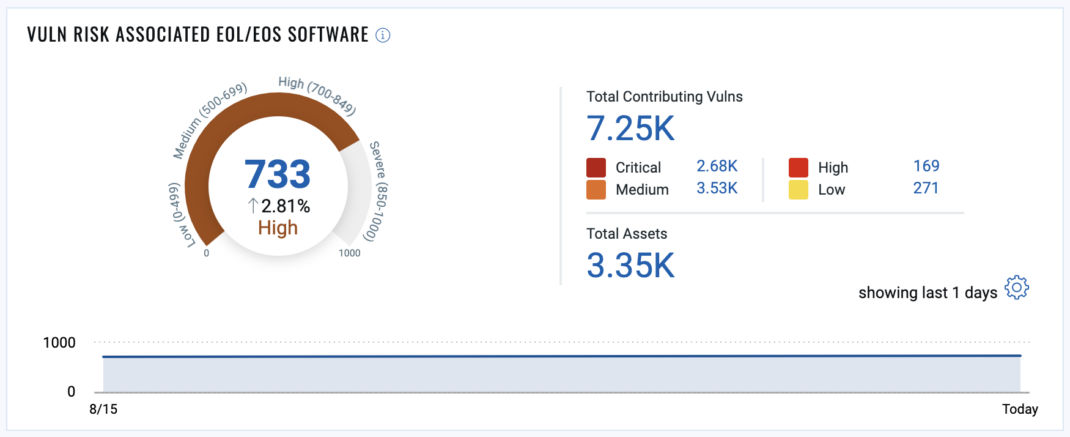
Measuring Risks Associated with Vulnerabilities in EOS/EOL Components
Once EOS/EOL components are identified, risk can be measured using vulnerability data associated with the obsolete components. Utilizing Qualys VMDR TruRisk, organizations can gauge the severity of vulnerabilities on outdated components across their entire organization. Metrics such as the number of critical vulnerabilities on EOS/EOL hardware or applications can highlight areas of immediate concern, prompting swift action to remediate these risks.
For example, consider a scenario where an organization’s web servers run EOS web applications, exposing them to known vulnerabilities. A metric showing the number of critical vulnerabilities on these servers and the potential impact of a successful attack can draw attention to the urgent need for an operating system upgrade or migration to a supported platform. Addressing these vulnerabilities proactively drives the organization’s risk exposure and strengthens its overall security posture.
Thus, harnessing metrics to identify EOS/EOL components and assess vulnerabilities in these assets empowers organizations to tackle technical debt effectively. By proactively addressing outdated hardware, applications, and operating systems, security teams can reduce the attack surface and fortify defenses against potential cyber threats. These metrics are vital in achieving a resilient and secure environment as part of a comprehensive cybersecurity strategy.
Conclusion
In conclusion, implementing adequate security metrics is paramount for organizations seeking to reduce risk realistically. Combining tactical metrics, such as hardware and software assessments, with tools like Qualys VMDR and CSAM provides valuable insights into vulnerabilities and suspicious software.
On the other hand, strategic metrics, utilizing Qualys TruRisk metrics, empower leadership to make informed, risk-based decisions, allocate resources efficiently, and align security strategies with business goals. Addressing technical debt, EOS/EOL hardware, applications, and operating systems through the suite of Qualys products allow organizations to prioritize remediation efforts, minimize attack surfaces, and fortify their defense against evolving threats.
Embracing these proactive cybersecurity measures safeguards an organization’s reputation, sensitive data, and uninterrupted operations and ensures long-term growth and trust among stakeholders in today’s dynamic digital landscape.
Additional Contributor
Josh Hankins, Chief Technical Security Officer, Qualys