Achieving DORA Compliance with Qualys: A Comprehensive Approach
In the ever-changing landscape of finance and technology, it is crucial to have robust operational resilience and compliance frameworks. The Digital Operational Resilience Act (DORA) framework is a significant step in this direction, as it is intended to strengthen the resilience of financial institutions and their critical third-party technology service providers against Information Communication Technologies (ICT)-related incidents and disruptions. In this blog, we will discuss what the DORA framework entails, why it is essential, and how Qualys can help in achieving DORA requirements.
What Is the DORA Framework?
The DORA framework is a regulatory initiative introduced by the European Union (EU) to increase the financial sector’s resilience to ICT-related events. It covers banks, investment firms, insurance companies, and payment institutions, among others. In addition, DORA expands its coverage to include essential third-party technology service providers, such as cloud service providers, data analytics service providers, and software vendors.
The DORA Framework Comprises Five Key Pillars
- ICT Risk Management and Governance: Financial institutions must implement robust ICT risk management frameworks to effectively identify, assess, and mitigate ICT risks.
- ICT-Related Incident Reporting: All ICT-related incidents, no matter how big or small, must be reported to the right officials. This includes anything that had a small to major effect.
- Digital Operational Resilience Testing: This calls for testing ICT incident responses on a regular basis to mimic different situations, such as hacking, natural disasters, and human mistakes.
- ICT Third-Party Risk: This focuses on handling the risks that come with important third-party technology service providers. It requires due diligence, performance tracking, and planning for what to do if something goes wrong.
- Information Sharing: Encourages financial institutions and the right officials to share information about threats and incidents linked to ICT.
DORA is scheduled to take effect in 2025 and aims to harmonize and strengthen ICT risk management across the EU’s financial sector.
Why Is DORA Important?
The following factors highlight the significance of the DORA framework.
- Protection of Financial Consumers: The primary objective of DORA is to protect financial consumers from losses resulting from ICT-related incidents, thereby ensuring their financial security.
- Financial Stability: As ICT-related disruptions can have cascading effects, a resilient financial sector is necessary for economic stability. DORA mitigates this risk, reducing the potential for financial crises.
- Legal Compliance: DORA is legally binding for all EU financial institutions and critical third-party technology service providers. Violations may result in significant fines and penalties.
- Increased Customer Confidence: Organizations that adhere to DORA are viewed as more dependable by their customers, which increases confidence and loyalty.
- Cost Reduction: Investing in ICT risk management and resilience measures aids organizations in reducing the financial burdens associated with ICT-related incidents.
- Competitive Advantage: DORA-compliant organizations obtain a competitive advantage on the global market, thereby attracting customers who value resilience.
The DORA framework is a vital tool for organizations, especially those in the financial sector, seeking to fortify their ICT resilience and navigate the ever-evolving landscape of technology and finance. Compliance with DORA not only ensures legal adherence but also positions organizations for success by enhancing customer trust, reducing costs, and bolstering their competitive standing in an increasingly digital world.
DORA Compliance Implementation Challenges
While DORA aims to improve operational resilience, there are several challenges financial institutions may face while complying with DORA requirements.
Ever-evolving threat landscape: With the rapidly evolving threat landscape and risks, organizations need to stay ahead of these risks with continuous monitoring, updates, and mitigation strategies.
Complex Framework: Effectively comprehending and implementing complex requirements presents a challenging task.
Lack of Visibility: Having fine-grained visibility on information assets in the dynamic landscape is a persistent challenge.
Resource Constraints: Complying with DORA may require additional resources to map, and implement security controls, conduct regular risk assessments, and implement intricate requirements.
How Qualys Platform Capabilities Address DORA Requirements
The Qualys Cloud Platform is built with the world’s most comprehensive Vulnerability Management (VM) capabilities, including its own asset inventory, threat database, and attack surface management. The apps required for DORA compliance are delivered via one platform, managed with one dashboard, and deployed with a single agent.
The following table shows how Qualy’s capabilities can help your organization address all DORA requirements.
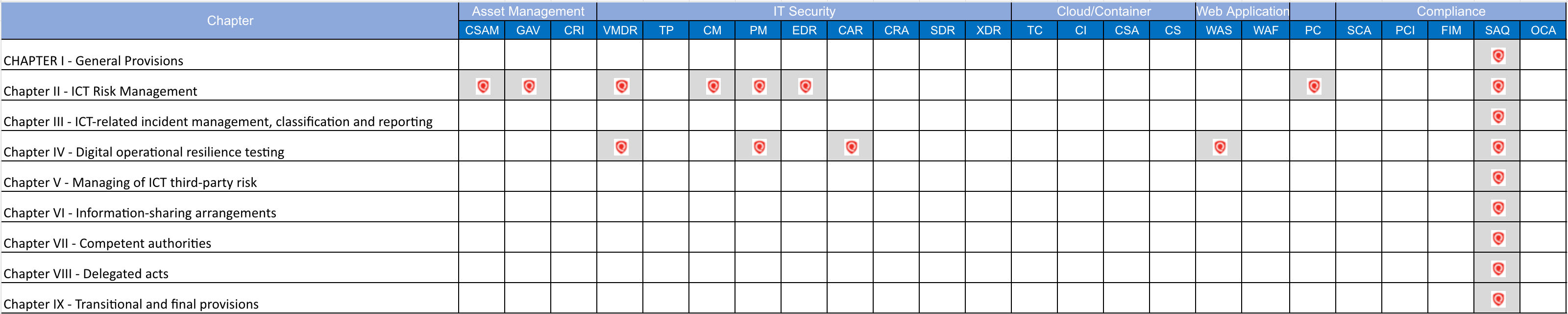
Unified view of Digital Operational Resilience Act (DORA) with Qualys Cloud Platform: Qualys Unified Dashboard unifies data from all Qualys capabilities into a single place for visualization and gives you single-pane-of-glass visibility in your organization.
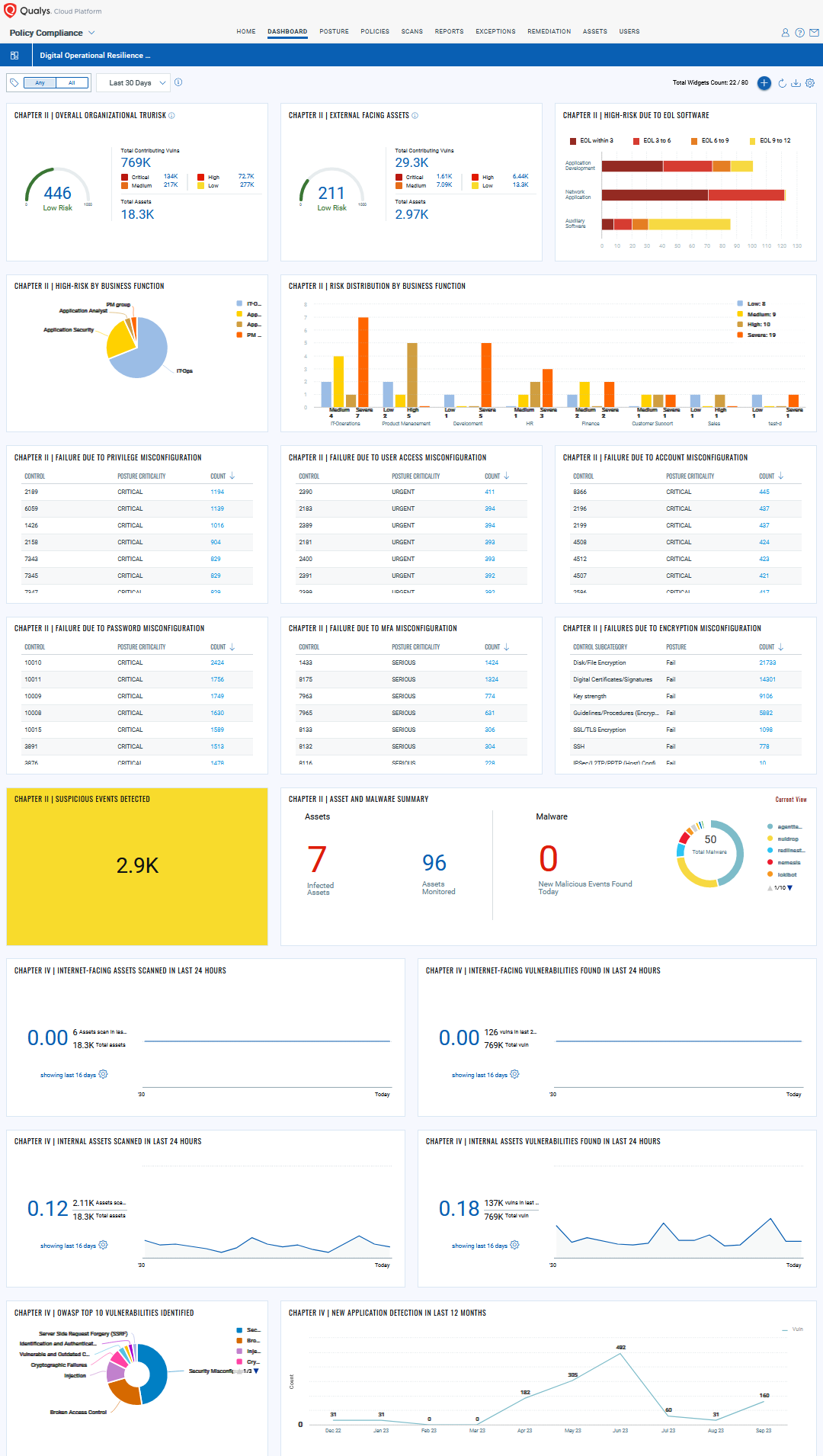
Let’s take a look at some of the key requirements and understand how Qualys helps you address them:
ICT risk management framework
The ICT Risk Management framework shall include at least strategies, policies, procedures, and tools that are necessary to duly and adequately protect all information assets and ICT assets, including computer software, hardware, and servers, as well as to protect all relevant physical components and infrastructures, such as premises, data centers and sensitive designated areas, to ensure that all information assets and ICT assets are adequately protected from risks including damage and unauthorized access or usage.
How Qualys helps: Qualys CyberSecurity Asset Management (CSAM) continuously discovers and monitors your entire attack surface, including internal known and previously unknown internet-facing assets, across your on-premises, cloud, and multi-cloud environments. It delivers natively integrated External Attack Surface Management (EASM) to enable Cybersecurity teams to identify all assets visible on the internet, including previously unknown assets and any potential security issues—before attackers find them.
Qualys CSAM automatically detects all your assets and classifies all elements including hardware, and software identifying key aspects such as end-of-life/support dates.
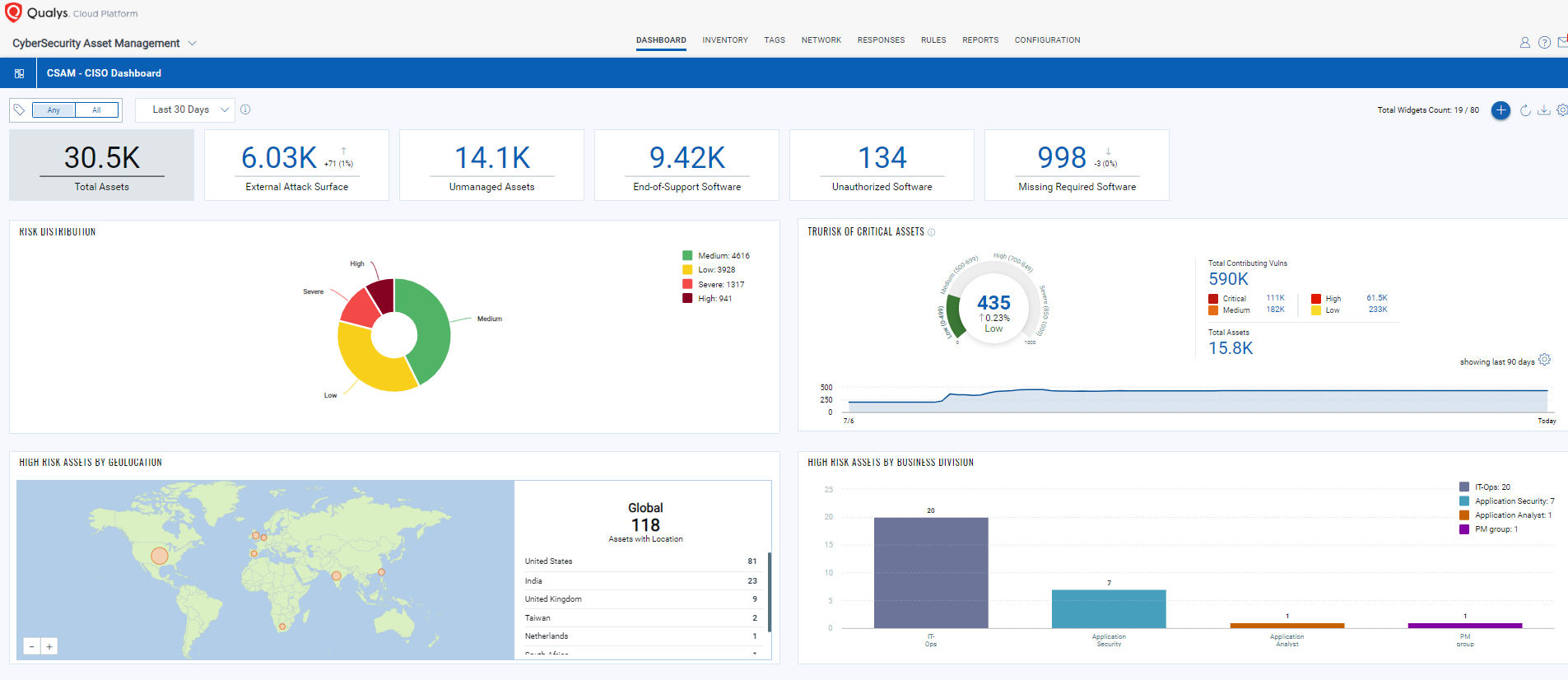
Identification
Financial entities shall, on a continuous basis, identify all sources of ICT risk, in particular the risk exposure to and from other financial entities, and assess cyber threats and ICT vulnerabilities relevant to their ICT-supported business functions, information assets, and ICT assets.
How Qualys helps: This requirement addresses the need for continuous vulnerability management and risk prioritization.
Qualys Vulnerability Management, Detection and Response (VMDR) offers an all-inclusive risk-based vulnerability management solution to prioritize vulnerabilities and assets based on risk and business criticality. VMDR continuously assesses assets for the latest vulnerabilities and applies the latest threat intel analysis to prioritize actively exploitable vulnerabilities. VMDR with TruRisk offers organizations visibility and insights into cyber risk exposure, making prioritizing vulnerabilities and assets based on business risk easy.
VMDR seamlessly integrates with configuration management databases (CMDB) and patch management solutions to quickly discover, prioritize, and automatically remediate vulnerabilities at scale to reduce risk.
Qualys Patch Management lets you automatically correlate vulnerabilities with patches and required configuration changes, decreasing your remediation response time. Qualys Patch Management efficiently maps vulnerabilities to patches and required configuration changes and automatically creates ready-to-deploy “patch jobs” that can be scheduled and deployed automatically.
Backup policies and procedures, further harmonization of ICT risk management tools, methods, processes and policies:
Financial entities shall minimize the impact of ICT risk by deploying appropriate strategies, policies, procedures, ICT protocols and tools.
How Qualys helps: This requirement emphasizes ensuring that proper policies are in place and implemented across the environment to prevent any loss of data and exposure due to misconfiguration.
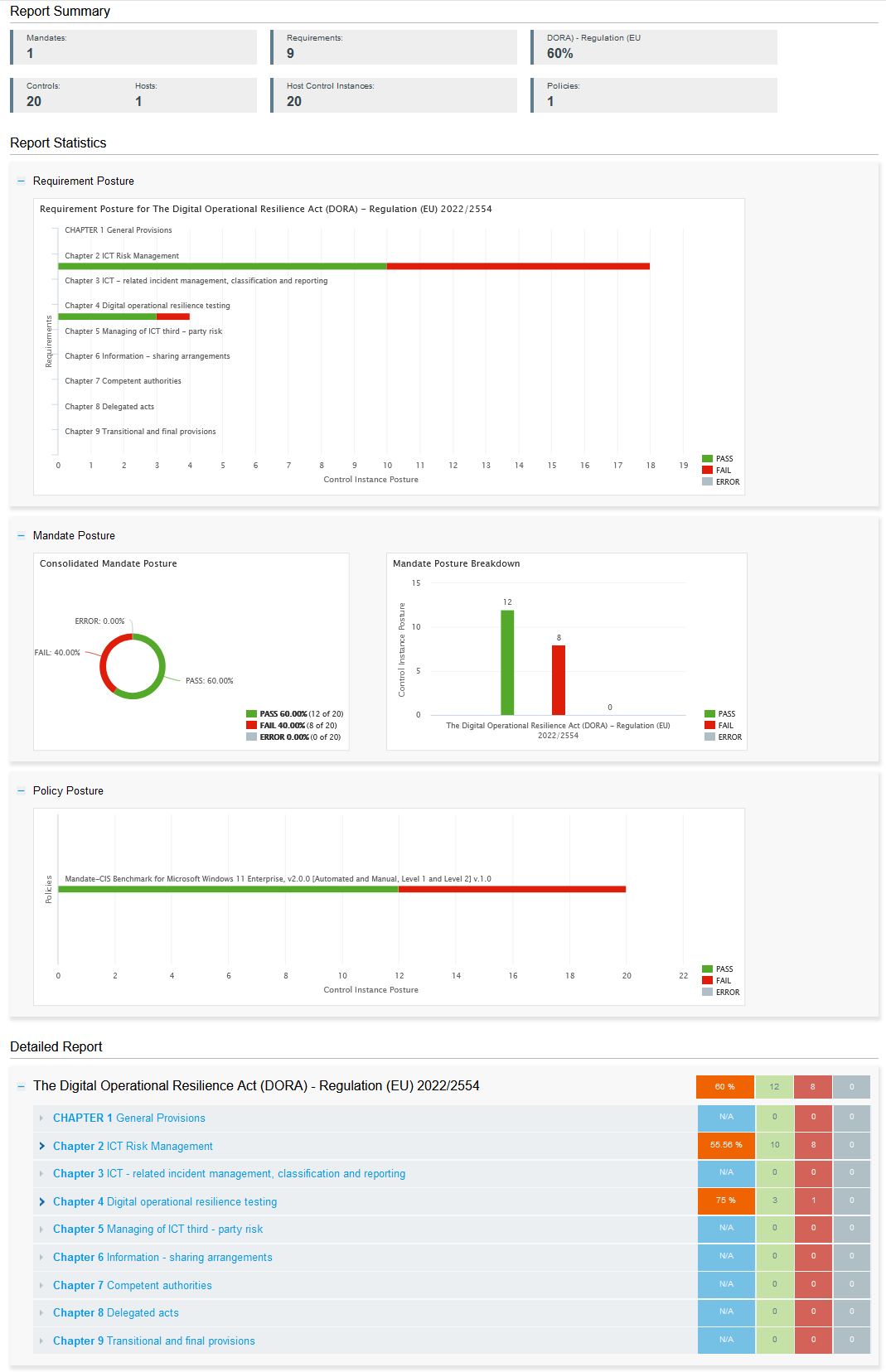
Qualys Policy Compliance (PC) has an integrated compliance-driven approach and risk management solution that lets you prevent configuration drifts, comply with external regulations and internal policies, prioritize and track remediations, and centrally manage exceptions. Qualys PC enables you to meet regulatory requirements and detect, prioritize, and remediate misconfigurations to mitigate risks and enhance overall security.
With out-of-the-box rich library content based on industry- and vendor-recommended best practices, such as the CIS Benchmarks and the Defense Information Systems Agency’s (DISA) Security Technical Implementation Guides (STIGs), you can fast-track your compliance assessments, or you can customize your control requirements to suit your unique needs.
Policy Compliance provides a holistic view of the DORA compliance posture using mandate-based reporting against the DORA Framework. The comprehensive reporting makes it easier to view the compliance posture of organization against in terms of underlying security baseline against mandate and also helps you better understand your organization’s compliance against DORA framework.
Qualys Security Assessment Questionnaire (SAQ ) helps create campaign questionnaires with due dates, notifications, assigned reviewers, various answer formats, question criticality, answer scores, evidence requirements and varying workflows.
Qualys SAQ streamlines your third-party and internal risk assessment processes right from the questionnaire creation phase. With Qualys SAQ, you easily design in-depth surveys to make business-process control assessments of security policies and practices of third parties and internal staff, and their compliance with industry standards, regulations, and internal requirements. Qualys SAQ also provides out-of-the box templates that can be used directly for these internal assessments.
Protection and prevention
For the purpose of adequately protecting ICT systems and with a view to organizing response measures, financial entities shall continuously monitor and control the security and functioning of ICT systems and tools and shall minimize the impact of ICT risk on ICT systems through the deployment of appropriate ICT security tools, policies and procedures.
How Qualys helps: Qualys agents run in real-time, providing detailed data on your risk posture. Key elements such as Endpoints with EDR tooling and misconfigurations are reported. Qualys Endpoint Detection and Response (EDR) prevents future attacks by eliminating vulnerabilities exploited by malware and preventing all other assets from the same attack. Unpatched vulnerabilities leave an open door for malware to successfully infect an endpoint and carry out its objectives. Multi-Vector EDR is natively integrated with Qualys VMDR, allowing you to take a single malware incident, immediately pivot to identify all assets susceptible to the same exploit, and patch them all using Qualys Patch Management.
Conclusion
Complying with the Digital Operational Resilience Act (DORA) requires financial institutions to enhance their cybersecurity and operational resilience measures. Organizations can simplify and streamline the path to compliance by leveraging Qualys’ suite of integrated apps – including Qualys Policy Compliance (PC), Vulnerability Management, Detection and Response (VMDR), and CyberSecurity Asset Management (CSAM).
These apps help organizations identify vulnerabilities, enforce security policies, maintain accurate asset inventories, and demonstrate compliance to regulators and auditors. By employing these tools, organizations can strengthen their cybersecurity posture, meet DORA’s requirements, and safeguard the financial sector from potential risks and threats.
More About the Qualys Cloud Platform
The Qualys Cloud Platform is one of the only security and compliance platforms that is FedRAMP Authorized to Operate (ATO) at the Medium Impact level. Qualys was selected by the Department of Homeland Security (DHS) to support 70 U.S. federal agencies for its Continuous Diagnostics and Mitigation (CDM) program. The CDM program provides strong support to ensure risk-based, consistent, and cost-efficient cybersecurity solutions to protect all organizational tiers by:
- Reducing attack surfaces
- Increasing cybersecurity posture visibility
- Improving cybersecurity response capabilities
- Streamlining DORA compliance
The Qualys Cloud Platform is one of the most advanced security platforms for EU financial firms and provides an entity-wide view of risk-based cybersecurity posture, with more than two dozen security and compliance applications fully integrated by a single, centralized interface and agent.
The platform simultaneously conforms with most Zero Trust Security Models and many of the broader guidelines documented in NIST Special Publication 800-53 v5.
To learn how your organization can easily and quickly comply with DORA, please visit Qualys today to start your free trial.
Contributors
- Jayesh Rajan – Manager, Compliance Analysis
- Bill Reed – PMM
- Shekhar Rana – Solutions Architect