Top MITRE ATT&CK Tactics and Techniques Leveraged in 2023

The Qualys Threat Research Unit has mapped vulnerabilities and misconfigurations to the MITRE ATT&CK framework tactics and techniques to help you get the attacker’s view. They have also analyzed vulnerabilities and misconfigurations across all our customers to find the top tactics and techniques leveraged by high-risk vulnerabilities.
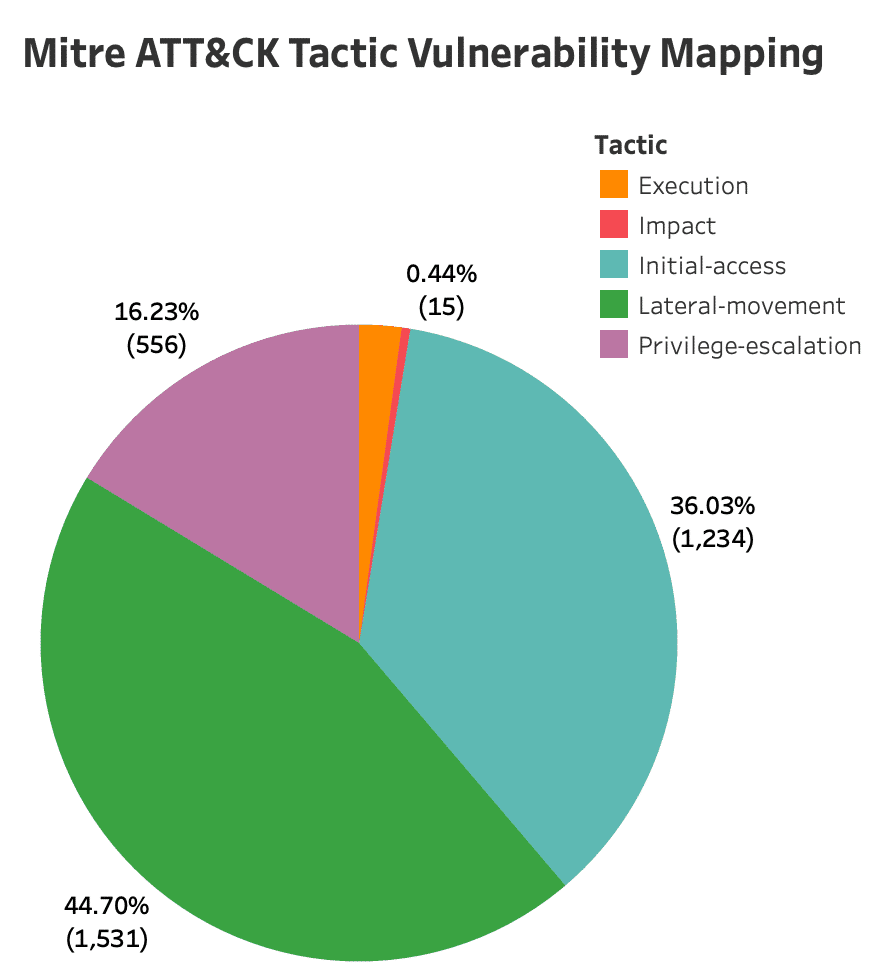
Top MITRE ATT&CK Tactics Leveraged By High-Risk Vulnerabilities
The top three tactics leveraged by high-risk vulnerabilities are Initial Access, Lateral Movement, and Privilege Escalation. Attackers first exploit vulnerabilities for initial access, then escalate privileges, and move laterally within systems.
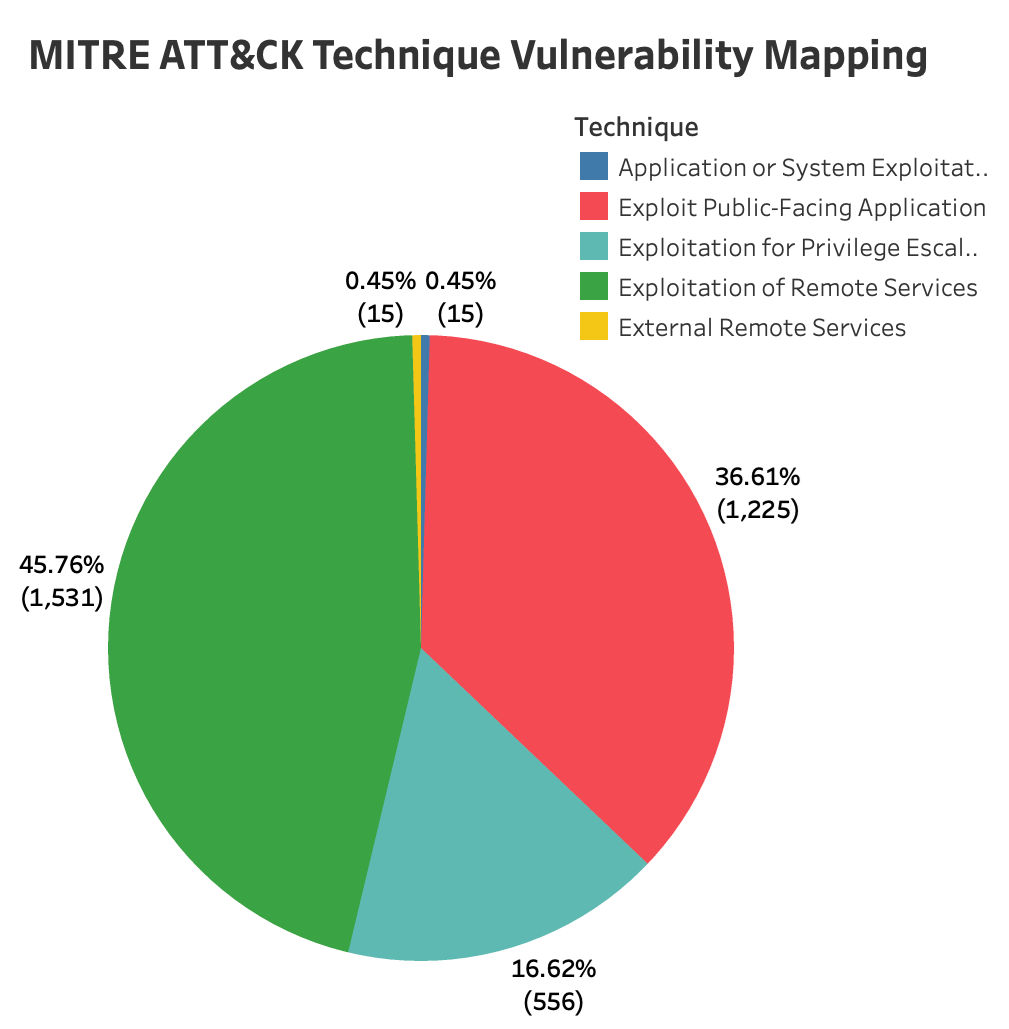
Top MITRE ATT&CK Techniques Based on High-Risk Vulnerabilities
A similar pattern emerges when we delve into the techniques associated with such vulnerabilities. The top techniques observed are the Exploitation of Remote Services, Exploitation of Public-Facing Applications, and Exploitation of Privilege Escalation. Attackers breach networks via public-facing apps and use remote service exploits for lateral movement.
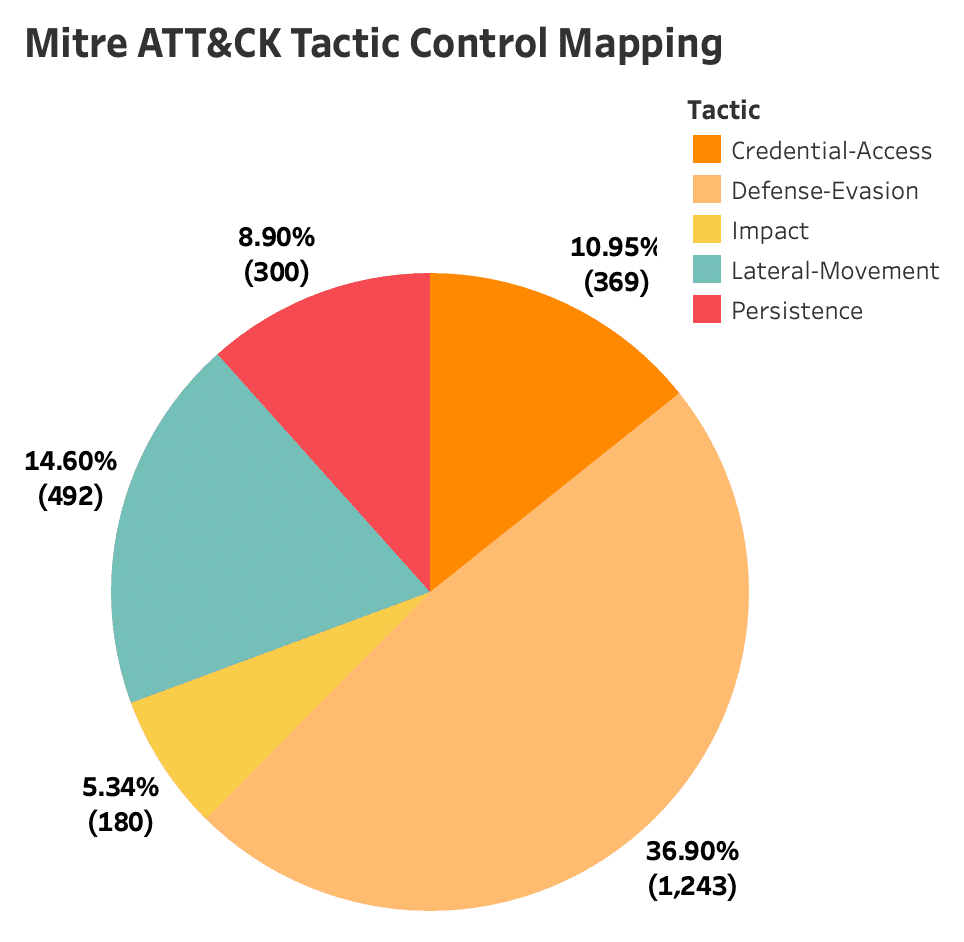
Top MITRE ATT&CK Tactics Based on Misconfigurations
The top three tactics leveraged by high-risk configurations are Defense-Evasion, Lateral Movement, and Credential Access. These are exploited by adversaries to gain unauthorized access, move laterally within the network, and obtain valuable credentials for further infiltration and data theft.
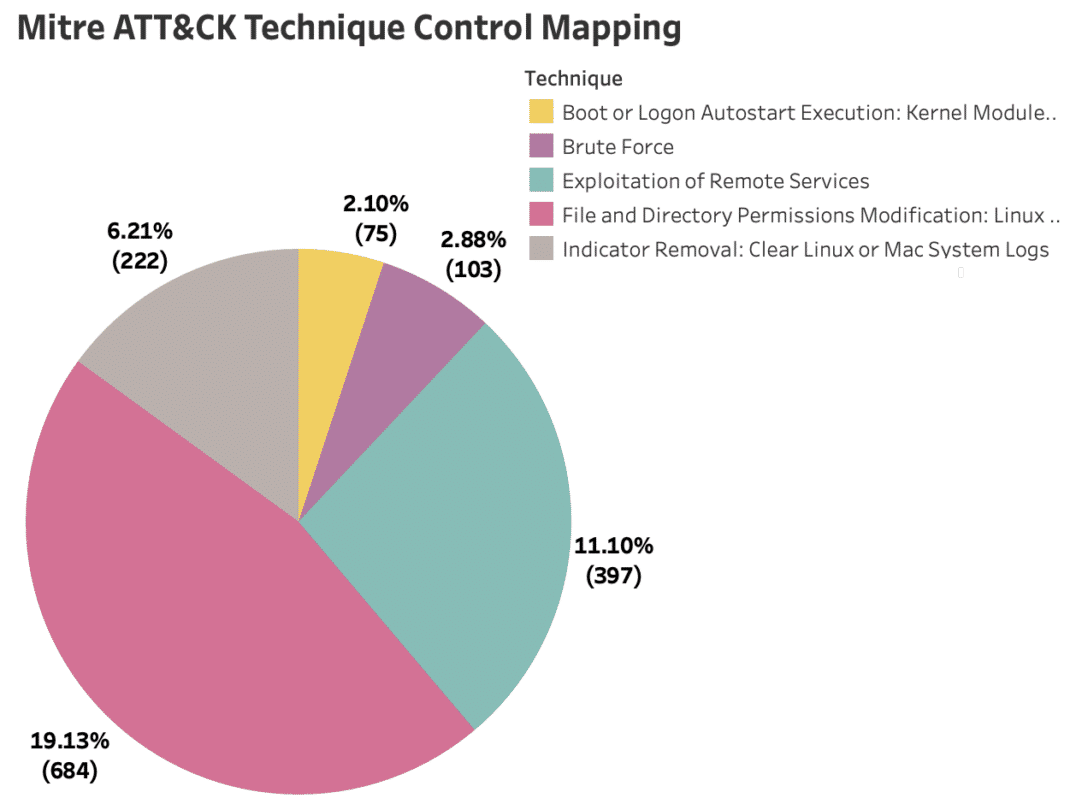
Top MITRE ATT&CK Techniques Based on Misconfigurations
The top three techniques leveraged by high-risk configurations are File and Directory Permissions Modification, Exploitation of Remote Services, and Indicator Removal. These are interconnected and exploited by adversaries to manipulate file permissions, exploit vulnerabilities in remote services, and conceal their activities to avoid detection and attribution.
To combat risk and get the attacker’s view, Qualys VMDR now features MITRE ATT&CK Matrix Prioritization. This allows users to get a holistic attacker-centric view, visualize critical risk findings based on ATT&CK Tactics and Techniques, know their TruRisk, and prioritize remediation efforts effectively using the Threat-Informed Defense approach. Qualys’ MITRE ATT&CK Matrix prioritization, along with TruRisk, empowers organizations to identify critical risks and remediate them effectively.
Try Qualys VMDR to know the TruRisk of MITRE ATT&CK Tactics and Techniques in your organization.