Combine Qualys TruRisk™ and MITRE ATT&CK to Adopt Threat-Informed Defense to Reduce Risk
Table of Contents
There are so many vulnerabilities disclosed daily that no one can patch all of them. Unfortunately, attackers can exploit them while you are still in the process of reviewing, prioritizing, and patching. Effective risk-based prioritization focuses your limited resources and remediation efforts where you will have the greatest impact in reducing risk and safeguarding your assets.
While CVSS and EPSS are foundational metrics for risk severity, they can miss real threats and fail to filter out non-critical risks without the complete business context of the environment. To overcome this, Qualys TruRiskTM aggregates all the risk factors from over 73,000 vulnerability signatures with 25+ sources of threat intel and your business context to help you quantify your risk and prioritize up to 85% fewer vulnerabilities so that you can implement a focused remediation program.
In recent years, the MITRE ATT&CK framework has emerged as an essential instrument for contextualizing cyber risk from an attacker’s perspective. It provides a detailed matrix of tactics, techniques, and procedures (TTPs) employed by adversaries, empowering organizations to predict and recognize potential attack vectors. While the ATT&CK framework typically leans towards a reactive approach, commonly used in EDR, SIEM, and SOAR products, when coupled with the Threat-Informed Defense approach, it can be used to proactively prioritize risk and improve the effectiveness of remediation efforts.
Announcing MITRE ATT&CK Matrix Prioritization in Qualys VMDR
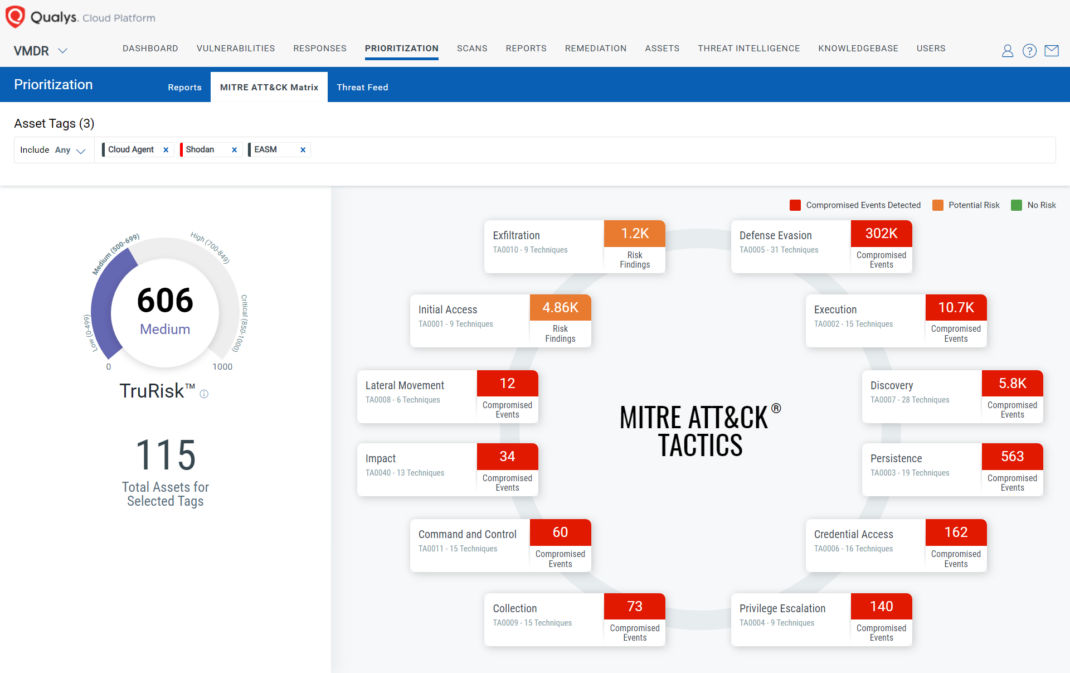
We’re incredibly excited to announce MITRE ATT&CK Matrix Prioritization in Qualys VMDR. This allows users to get a holistic attacker-centric view, visualize critical risk findings based on ATT&CK Tactics and Techniques, know their TruRisk, and prioritize remediation efforts effectively using the Threat-Informed Defense approach. The MITRE ATT&CK Matrix Prioritization is not only specific to vulnerabilities; it also includes misconfigurations and EDR incidents. This enables organizations to predict and identify potential threats in advance, make informed decisions to prioritize and address them promptly, and thus stay one step ahead of attackers.
Qualys now stands out as the only enterprise-scale solution to combine TruRisk and MITRE ATT&CK to manage cybersecurity risks proactively and enhance detection and response in a single platform.
MITRE ATT&CK Framework
The MITRE ATT&CK framework is organized into two core elements: Tactics and Techniques. Tactics refer to broad categories that characterize the objectives behind cyber-attacks, serving as a guide to the ‘why’ behind an adversary’s actions. Techniques, by contrast, provide a detailed ‘how,’ specifying the exact methods attackers employ to accomplish their tactical aims. When necessary, techniques are broken down into sub-techniques, offering an even more refined view of the attacker’s arsenal.

Traditionally, the MITRE ATT&CK framework has been used by security teams for better detection, investigation, and response in EDR, SIEM, and SOAR product lines. Increasingly, they are looking to use this knowledge of adversaries’ intentions and tactics more broadly to evaluate their cybersecurity defense and prioritize risk, making better investment decisions to prevent attacks. The biggest hurdle they have is the lack of necessary insights because legacy (or traditional) vulnerability, configuration, or attack surface management tools do not help visualize these risks in terms of the MITRE tactics and techniques, or they need to use multiple siloed tools and stitch together the risk context of these attacks to understand the overall efficacy of their risk management program.
Organizations need the Threat-Informed Defense approach, which, in addition to ATT&CK, includes other threat information, such as vulnerabilities, misconfigurations, software EOS/EOL, etc., to help them stay one step ahead of attackers. Proactively monitoring attackers’ behavior is crucial for defenders to safeguard key assets.
Top MITRE ATT&CK Tactics and Techniques Leveraged
Qualys Threat Research Unit (TRU) has mapped vulnerabilities and misconfigurations to the MITRE ATT&CK framework tactics and techniques to help you get the attacker’s view. They have also analyzed vulnerabilities and misconfigurations across all our customers to find the top tactics and techniques leveraged by high-risk vulnerabilities. Below you will find the the highlights of their findings; you can find further details in our earlier blog post.
| Top MITRE ATT&CK Tactics Leveraged By High-Risk Vulnerabilities | Initial Access, Lateral Movement, and Privilege Escalation |
| Top MITRE ATT&CK Techniques Based on High-Risk Vulnerabilities | Exploitation of Remote Services, Exploitation of Public-Facing Applications, and Exploitation of Privilege Escalation |
| Top MITRE ATT&CK Tactics Based on Misconfigurations | Defense-Evasion, Lateral Movement, and Credential Access |
| Top MITRE ATT&CK Techniques Based on Misconfigurations | File and Directory Permissions Modification, Exploitation of Remote Services, and Indicator Removal |
How to Combine Qualys TruRisk™ and MITRE ATT&CK to Reduce Your Cyber Risk
The MITRE ATT&CK Framework serves as a common language to showcase the threat landscape and helps organizations to effectively explain the threat at all levels of their cybersecurity program.
Qualys EPP, EDR, and FIM already enable security teams to detect and investigate incidents for better analysis and response using the MITRE ATT&CK framework. We are now extending the power of the MITRE ATT&CK framework to VMDR and Policy Compliance to enable security teams to continuously visualize the efficacy and TruRisk of their cyber defense against the attack tactics and techniques in real time. We also provide a consolidated view of associated vulnerabilities, misconfigurations from CIS/DISA, and external asset surface exposures impacting business-critical assets to assist security teams in prioritizing security risks, detecting missing patches, and facilitating remediation efforts. Mapping vulnerabilities and misconfigurations with MITRE ATT&CK Tactics and Techniques and using Qualys TruRisk help security teams measure and prioritize risk effectively and adopt the Threat-Informed Defense approach.
Using the MITRE ATT&CK Matrix for Prioritization
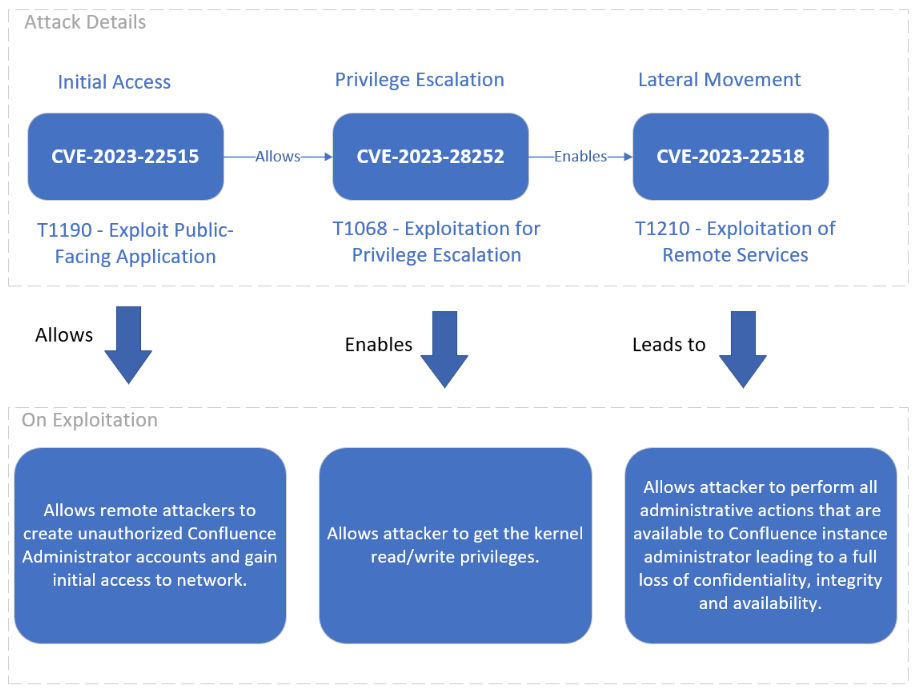
Let us review an example of a ransomware attack to understand how the mapping of vulnerabilities would help you to adopt the Threat-Informed Defense approach. Here, we are talking about the attack through the exploitation of critical vulnerabilities in a widely used application – Atlassian Confluence. Atlassian Confluence is a collaboration and documentation tool used by several organizations and often contains confidential data such as financial data, customer information, employee data, project plans, product roadmaps, and other intellectual property. A successful exploit of Atlassian Confluence vulnerability CVE-2023-22515 allows an attacker to get initial access to the network of the public-facing Confluence app. This allows the attacker to exploit Microsoft vulnerability CVE-2023-28252 to gain the privilege escalation of the kernel. That, in turn, enables the attacker to exploit CVE-2023-22518 to gain full administrator access and perform all administrative actions, leading to loss of confidentiality, integrity, and availability.
To use the MITRE ATT&CK Matrix Prioritization in Qualys VMDR, select the asset tags for the assets you want to get the MITRE ATT&CK view. Once you select the asset tags, you will see the TruRisk score of the selected asset tags along with the MITRE tactics of the risk findings detected on the selected assets. This shows you the prioritized ATT&CK Tactics based on compromised EDR events and risk findings that include vulnerabilities and misconfigurations for the selected assets.
Now that you have identified the top tactics you need to focus on, click on one of them to get the prioritized ATT&CK Techniques of that Tactic. Here also you can view the associated assets and their risk findings, alongside the compromised EDR events. Click on the technique to identify the critical assets, internet-facing assets, critical vulnerabilities, misconfiguration, and compromised EDR events that may lead to the attack.
At the Technique level, the TruRisk Score for the asset helps you identify the critical assets and vulnerabilities based on the QDS score. Considering the above example using MITRE ATT&CK Matrix Prioritization, you can see the above CVEs’ QIDs as part of the “Vulnerability Findings” widget in the respective Tactics and Techniques view. The QDS score is 95 for the QID associated with CVE-2023-22515, CVE-2023-28252, and CVE-2023-22518, which will be shown at the top for prioritization.
Remediation Strategies
Qualys goes beyond the identification and prioritization of risk and aids in risk reduction by remediating vulnerabilities and misconfigurations. The MITRE ATT&CK Matrix Prioritization helps you identify the highly impacted tactics and, based on that, identify the techniques. Then, you can identify the vulnerabilities and misconfigurations.
Using Qualys Patch Management with a zero-touch approach automates the patch management process, significantly reducing the MTTR. Additionally, Qualys Policy Management offers provisions to remediate misconfigurations through remediation scripts, mitigating critical risk exposure for assets.
Qualys Policy Management provides provisions to remediate the misconfigurations through remediation scripts. Fixing misconfigurations plays a role in the mitigation of the critical risk exposure for an asset. The remediation of control is supported only on Agent assets. To identify the agent asset, use QQL – asset.trackingMethod:Agent in the Assets dropdown. Along with that, in the Controls dropdown, you can add QQL – posture.status:Fail or can add the specific control IDs.
Qualys EDR provides a provision to quarantine assets in case of any malicious event. The Quarantine Asset feature restricts the infected host machine from performing any network communication. You can Quarantine an Asset from the Incidents or Asset tab. Through the Incidents tab, you can quarantine the assets on which critical/malicious incidents are detected.
Conclusion
In conclusion, the MITRE ATT&CK Framework is a pivotal tool in cybersecurity, offering a comprehensive understanding of adversary tactics and techniques. By leveraging the TruRisk and MITRE ATT&CK context, organizations can proactively monitor and prioritize risks that matter. Qualys’ MITRE ATT&CK Matrix prioritization, along with TruRisk, empowers organizations to identify critical risks and remediate them effectively. This holistic approach, involving patch management automation and misconfiguration remediation, is instrumental in reducing the attack surface and enhancing overall cybersecurity resilience.
Try Qualys VMDR to know the TruRisk of MITRE ATT&CK Tactics & Techniques in your organization.
Contributors
- Swapnil Ahirrao, Principal Product Manager, VMDR, Qualys