Introducing Cyber Asset Management 3.0 With Enhanced Security Assessment

Qualys is re-defining attack surface management with CyberSecurity Asset Management (CSAM) 3.0, expanding the most comprehensive attack surface coverage on the market to include patent-pending EASM discovery and scan, passive sensing for unmanaged/untrusted devices built in to the Qualys agent, and new third-party API-based connectors to provide continuous visibility.
As the modern attack surface continues to evolve, cybersecurity teams must simplify and consolidate their approach to building a unified asset inventory. Too often, they rely on multiple siloed point solutions for narrow discovery use cases.
An external scanning tool that provides stale data from a snapshot. Another tool that pulls unstructured data from third-party sources. And a CMDB riddled with missing asset records. This approach results in visibility gaps, unstructured cyber risk data, and too much manual effort for security teams.
CSAM 3.0 consolidates the strategy for cybersecurity teams to eliminate the risk from unknown assets. The approach is twofold: First, it uses versatile and use-case-centric discovery methods to provide continuous visibility. Second, it allows teams to pinpoint the cyber risk from vulnerabilities and other cyber risk factors to drive TruRisk prioritization. This post will explore each approach in detail.

Asset Discovery and Eliminating Unknown Risks with CSAM 3.0
There are many places for assets to hide within the dynamic attack surface. Cybersecurity teams must account for multi-cloud, on-premises, IT/OT/IoT devices, and external assets from subsidiaries, mergers, and acquisitions. The diversity of cyber assets requires multiple methods of discovery:
- Scanners and sensors for internal assets such as IT devices and infrastructure
- External scanning for internet-facing assets, legacy systems, etc.
- Monitoring of multi-cloud environments
- 3rd-party connectors to pull asset records from external sources and siloed tools
- Passive sensing for IoT/OT devices for real-time visibility
No one solution can claim all these discovery methods except for CSAM 3.0.
CSAM expands its industry-leading suite of asset discovery methods with a pragmatic and use case-centric approach:
Patent pending EASM technology – Accurately discover and attribute internet-facing assets to the organization. CSAM 3.0 uses new attribution scoring and expands the use of open-source technology and a proprietary internet scanner to drive accurate discovery, attribution, and vulnerability assessment.

Cloud Agent Passive Sensing – Devices come and go from internal networks, and some may not support agents, which makes it difficult to track and manage associated cyber risks. CSAM 3.0 leverages the already-deployed Qualys agent to identify unmanaged/untrusted IT & IoT/OT devices to quickly perform vulnerability and compliance scans.

3rd-Party API-based Connectors – While API connectors alone are not sufficient for unified risk assessment, they can complement native discovery methods. Qualys recently announced connectors with Active Directory and BMC Helix, bolstering a growing list of external sources from which to sync and normalize asset records and business context. The result is a unified inventory that includes assets discovered natively along with those imported from external sources—all with complete cyber risk and business context.

CSAM 3.0 adds these methods to an already industry-leading native discovery suite, eliminating the term “unknown asset” from an organization’s vocabulary.
Assess Cybersecurity Risks to Your External Attack Surface Faster
By nature, the external attack surface for enterprise organizations is sprawling and dynamic. It might include dozens or hundreds of subsidiaries, mergers, and acquisitions, all with potentially unknown internet-facing assets and legacy systems. Even if security teams can discover all of it, they struggle to attribute assets to the organization and measure the immediate cyber risk.
Traditional external scanning tools rely on basic banner-grabbing and limited vulnerability signatures, leading to missed vulnerabilities, gaps in coverage, and a sprawl of irrelevant detections.
In addition to improved external asset discovery, CSAM 3.0 has added two ground-breaking capabilities to solve the risk assessment challenges for security teams.
- All external assets are now attributed to the organization with a confidence score, accounting for user-defined configurations, domain, subdomain, and related organizations, DNS lookup, SSL certificate data, open-source, and proprietary asset catalogs. Now, security teams can filter down to external assets that are properly attributed to the business.
- The latest EASM scanner in CSAM 3.0 includes lightweight vulnerability scanning upon discovery. What does this mean for risk assessment? Qualys Threat Research Unit (TRU) has already observed three times more critical vulnerabilities detected and a 60% reduction in irrelevant, unconfirmed vulnerabilities when compared with traditional external scanning methods, which rely on stale data snapshots.

Cyber Risk Assessment Vulnerabilities and Beyond
The goal of every CISO and cybersecurity team is to measure, communicate, and eliminate cyber risk. To do so efficiently, they need a foundation that not only includes every asset but provides cyber risk context. Yes, that means identifying and prioritizing the riskiest vulnerabilities as quickly as possible, but it also means accounting for misconfigurations and other risk factors associated with the asset, including:
- Upcoming end-of-life (EoL) and end-of-support (EoS) technology and associated vulnerability analysis
- Missing agents (such as EDR) and security controls
- Risky open ports exposed to the internet
- Misconfigured unauthorized software and services
All these factors are risk multipliers for an asset. For instance, if a business-critical asset has upcoming EoS software with high-risk vulnerabilities, those vulnerabilities are unpatchable, significantly elevating the risk. CSAM 3.0 not only provides this data on every asset to cybersecurity teams, but it automatically applies each risk factor to TruRisk Scoring and prioritization.

EoS software contributing to the TruRisk of an asset.
Keep Your CMDB Up to Date With Cyber Asset Management
According to Gartner, 99% of organizations with inaccurate CMDBs experience business disruption. Even worse, IT and Security teams are unable to respond efficiently to critical cyber risk.
The primary reason for inaccurate or incomplete CMDBs is that their inventory is updated infrequently (and often manually). For many organizations, blind spots on the external attack surface or to IoT/OT devices on the network lead to broken CMDBs.
With these enhancements to CSAM 3.0, customers can leverage a more powerful CMDB sync (bi-directional/unidirectional supported) to ensure all internal AND external asset records are up-to-date in IT’s source of truth, including the cyber risk context above. For instance, IT teams will have proactive visibility into upcoming EoL/EoS to budget and execute technology upgrades. This way, organizations can map and assign vulnerability remediation tickets with 96% accuracy and reduce MTTR by half.
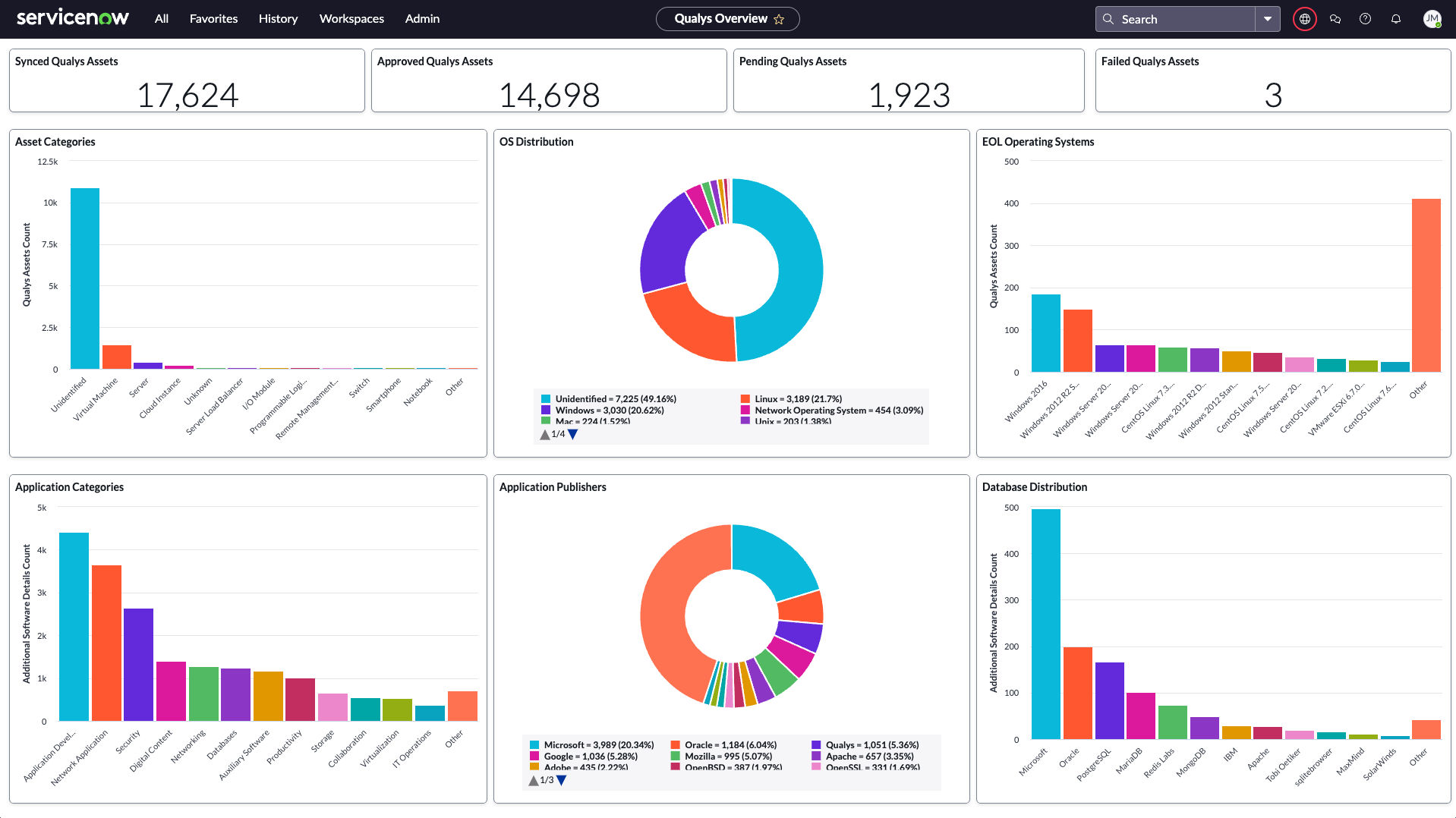
It’s a win-win for both departments. CISOs reduce cyber risk in half the time, and CIOs prevent business disruptions stemming from inaccurate CMDBs.
Eliminate Unknown Assets, Reduce Cybersecurity Risk
With the release of CSAM 3.0, Qualys is providing customers with an arsenal of discovery methods to eliminate cyber risk from unknown assets. It is the foundation for risk-based vulnerability management and step zero for customers to maximize the Enterprise TruRisk Platform.
Try CSAM 3.0 at no cost for 30 days