TotalCloud Container Security Best Practices

Qualys Container Security (CS), an integral part of TotalCloud™ 2.0, provides a comprehensive view of the security posture of containerized applications.
Operationalizing a new technology tool in an enterprise often presents its own challenges. This blog seeks to help the operations team familiarize themselves with a few important processes and configure key parameters early in the rollout. Please note this is not a definitive guide; instead, it highlights a few points to consider. Here are some of the best practices to follow when using Qualys Container Security.
Maintaining Sensor Version
It’s always recommended that the Qualys CS sensor be updated to the newer version to take advantage of new features, bug fixes and to remediate sensor vulnerabilities. When a newer sensor version is available than the one deployed, you’ll see “Update Available” next to the sensor name.
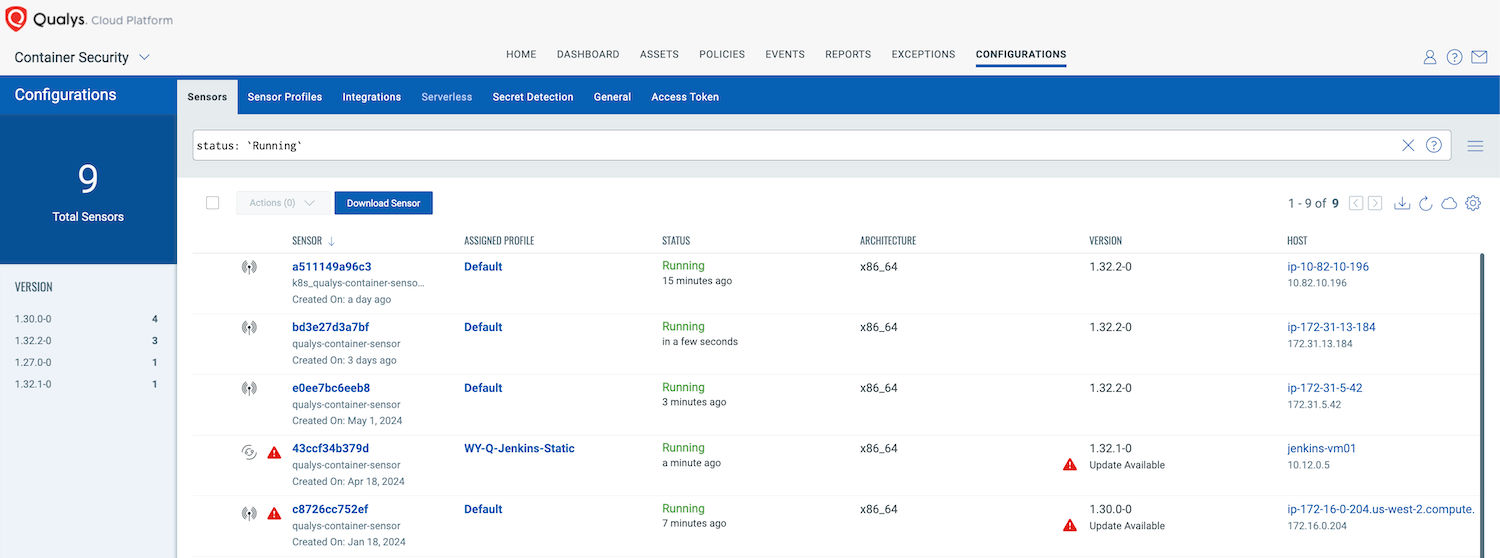
Update Strategy:
It’s always advised to use the latest Qualys CS sensor and review the release notes for every update.
- The status of the platform and scheduled maintenance windows are published at status.qualys.com. There is also an option to “Subscribe to Updates” for a specific platform and component. Example: US Platform 2, Container Security (CS).
- Review the release notes at www.qualys.com/documentation/release-notes with “Filters” as Container Security (CS).
- Container Security Sensor Image is available on dockerhub and is released regularly, almost every month. The sensor is also available as a Binary(tar.xz) for standalone host installation from the Qualys portal. Sensors deployed on a standalone container host with the installsensor.sh script or docker run command will be updated automatically.
For a medium to large size deployment, Qualys recommends using Qualys qcs-sensor Helm Chart for deployment. A few organizations even use Helm Charts and GitOps together for an efficient roll-out and upgrade process.
- Helm Charts can be used to update the CS Sensor. Upgrading to the latest release could be as simple as executing a command “helm upgrade” with relevant flags.
- GitOps gives you tools and a framework to take DevOps practices, like collaboration, CI/CD, and version control, and apply them to infrastructure automation and application deployment. There are CNCF-graduated projects like argo and Flux (https://www.cncf.io/projects/) that can be used to declaratively manage the state of deployment.
- K8s DaemonSet: There is a Container Security Sensor daemonset.yaml file which can be downloaded from the Qualys portal.
- To perform the update, modify the daemonset yaml file to change
imagePullPolicy: IfNotPresent to Always
This declares Kubernetes to always download the sensor image from the dockerhub. If the latest tag has changed this will pull the new version of the sensor. - To update the sensor regularly, schedule the below command on a regular basis:
kubectl -n qualys rollout restart daemonset/qualys-container-sensor
This command performs a rolling restart of the sensors.
- To perform the update, modify the daemonset yaml file to change
- For other upgrade methods for Standalone, AWS ECS Cluster, Docker Swarm, etc. please follow the steps from the Container Security Sensor Deployment Guide.
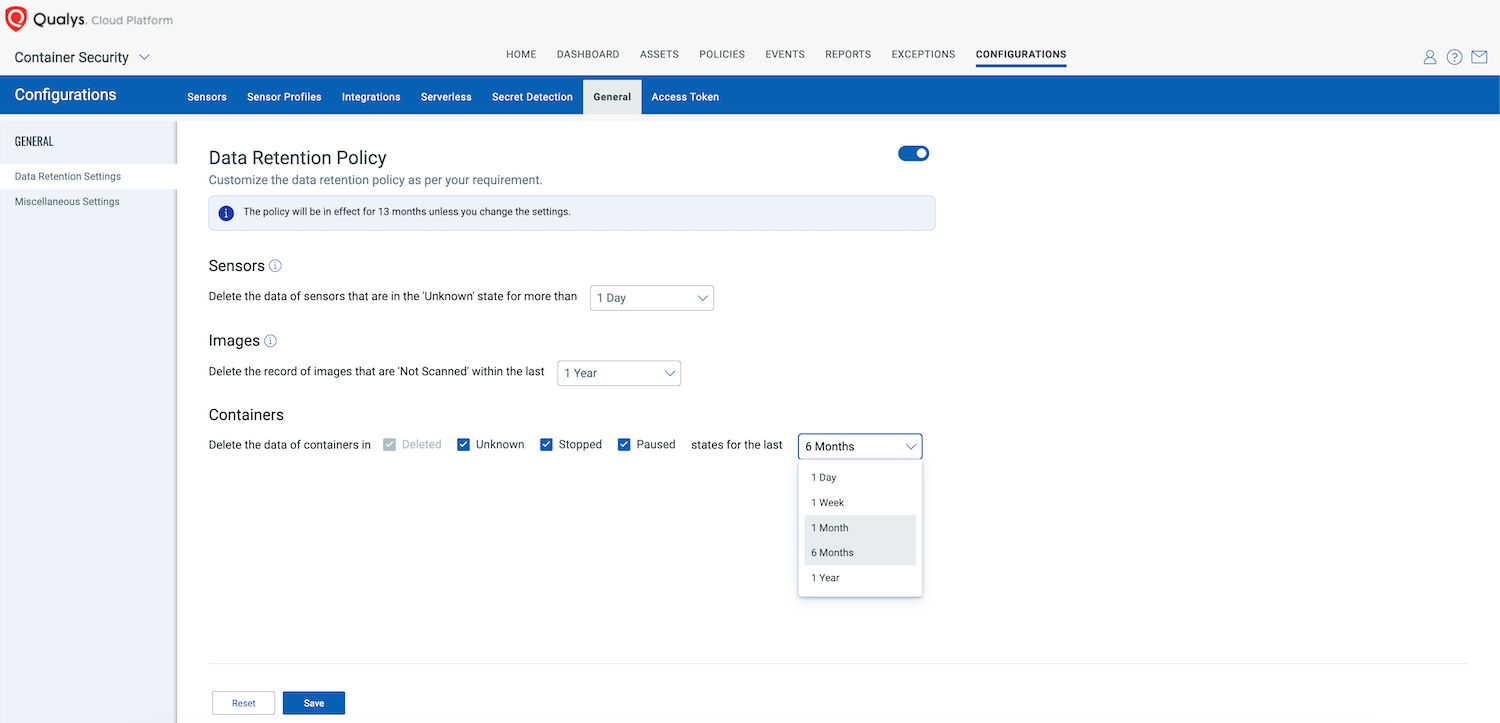
Data Retention Policy
Qualys will retain the Qualys CS data for months by default, which can be useful for Container Security Forensics. Sometimes, this can cause information overload or infobesity for the operations team. There are data retention settings that can be enforced based on requirements. This feature can be used to delete the data and records of Sensors, Images, and running containers based on state.
The purge rule of these records can be from 1 Day to 1 Year. The advice is to gradually reduce retention to avoid infobesity and be comfortable with the approach. Example: Start with 6 months and gradually change it to 1 Month, 1 Week, or even 1 Day.
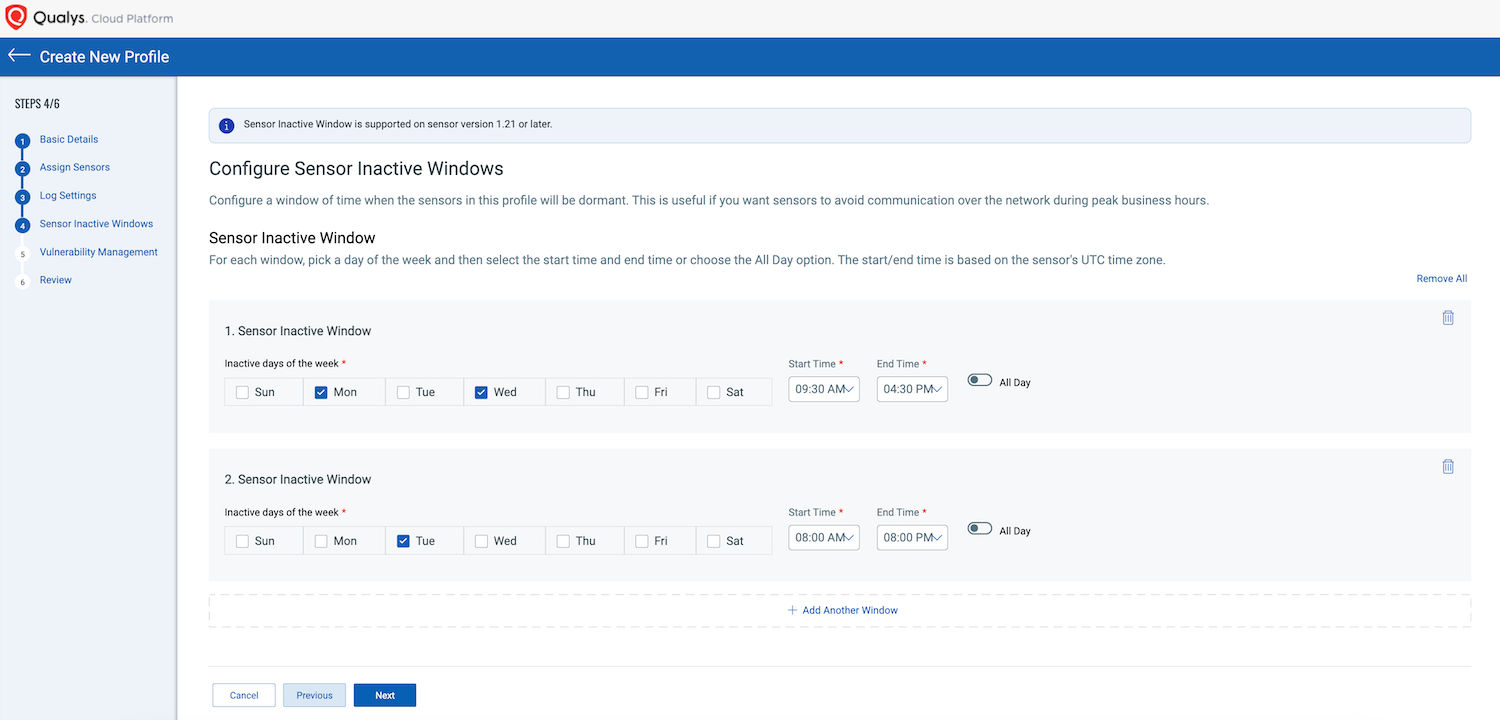
Sensor Inactive Windows: Option to Control the Scan
Qualys CS Sensor runs in an always ON mode to help continuous risk mitigations. There is no option to manually trigger any scan job. A new asset scan is launched when any of the following events occur:
- Events on images: load, pull, import, tag
- Events on containers: start, create, unpause
- The scan is launched when there’s a new manifest.
- The scan is launched every 48 hours on containers (i.e., 48 hours after the last successful scan)
The Container Scanning Interval can be selected for how often sensors should re-scan containers. 48 hours is recommended for optimum performance. The General Sensor Profile can be configured to re-scan containers as frequently as 12 hours for critical workloads. These settings can change over time since Qualys keeps adding granular scan settings and enhancing the functionalities based on fast-paced technology innovations.
However, there are use cases where the Ops team (Cloud/Dev/Sec) would like to pause sensors during the maintenance window or business hours. And the other use case might be to run sensors during a specific window. Such scenarios can be covered by using sensor inactive windows.
The purpose of an inactive window is to prevent the sensor from generating data during specific times, such as when routine maintenance is being performed on the system.
Dashboard and Reports
Qualys Unified Dashboard (UD) provides an extensive and ever-expanding library of dashboards related to all teams in an IT and security organization. Unified Dashboard brings information from all Qualys applications into a single place for visualization. The dashboard library helps create custom dashboards using existing widget templates, customize existing widgets, or create your own widgets. Qualys Query Language (QQL) is used to build search queries to fetch information from Qualys databases.
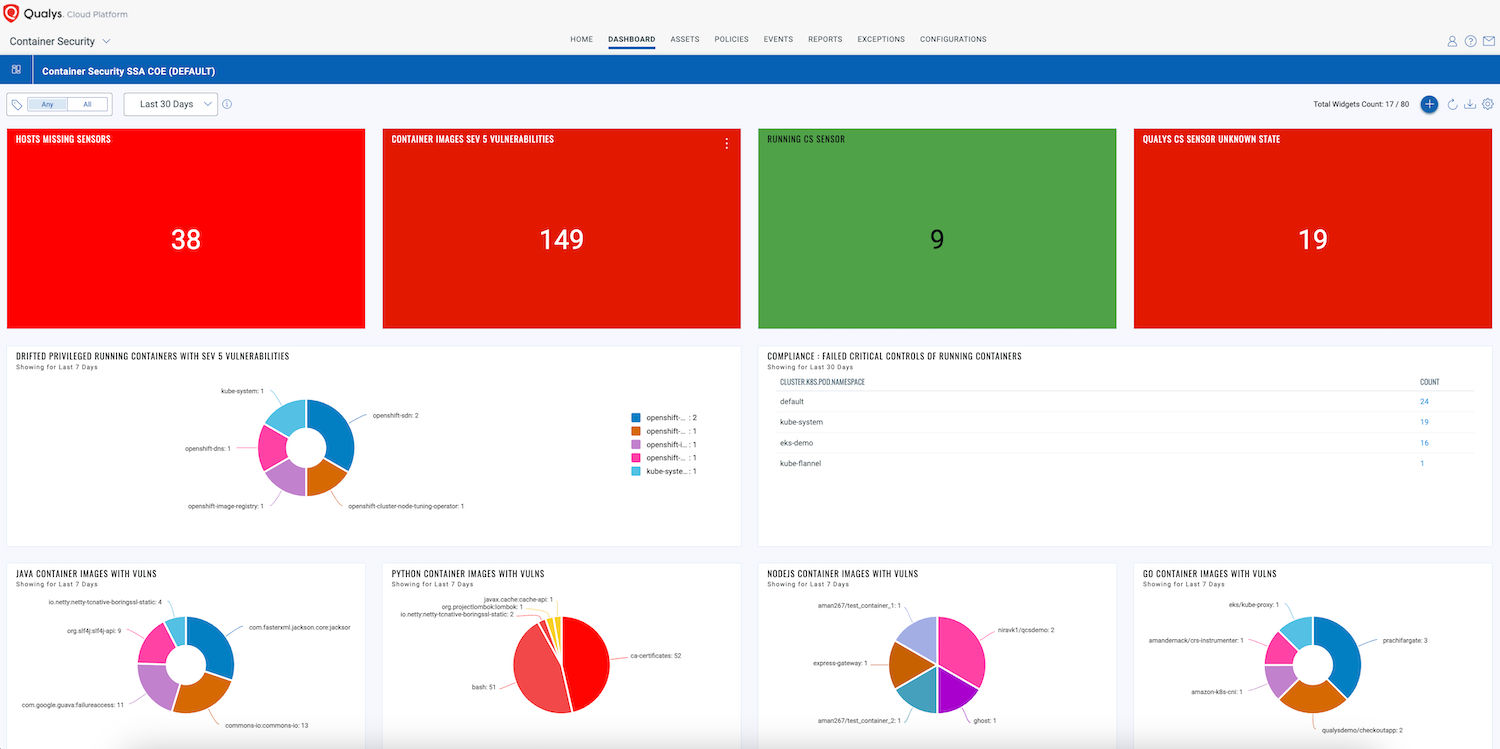
Scheduled reports for container vulnerabilities, image vulnerabilities, secrets, and malware could be very useful.
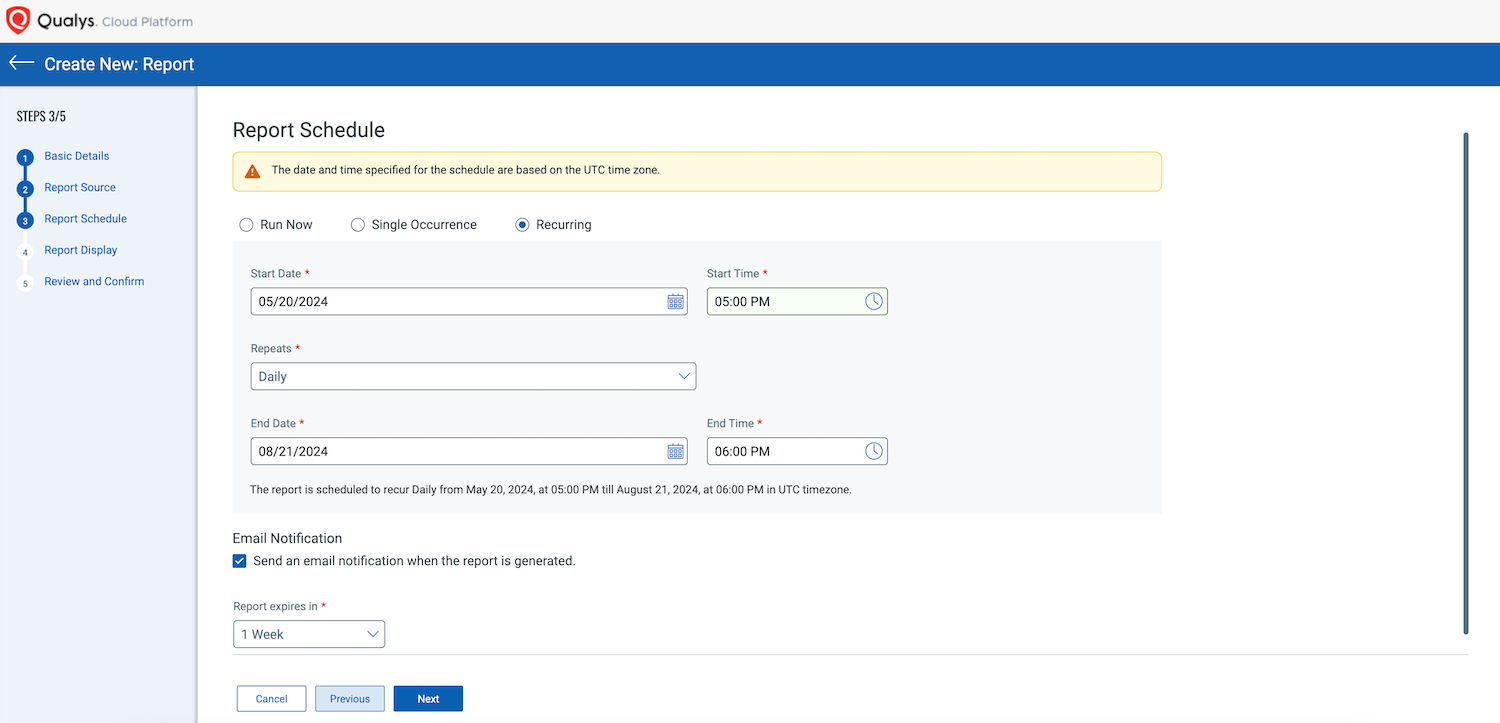
Using APIs
For Day 2 operations, it’s a good idea to invest some time and effort in creating custom integrations or scheduled tasks. Qualys’ Container Security API guide can help you develop the scripts and workflows.
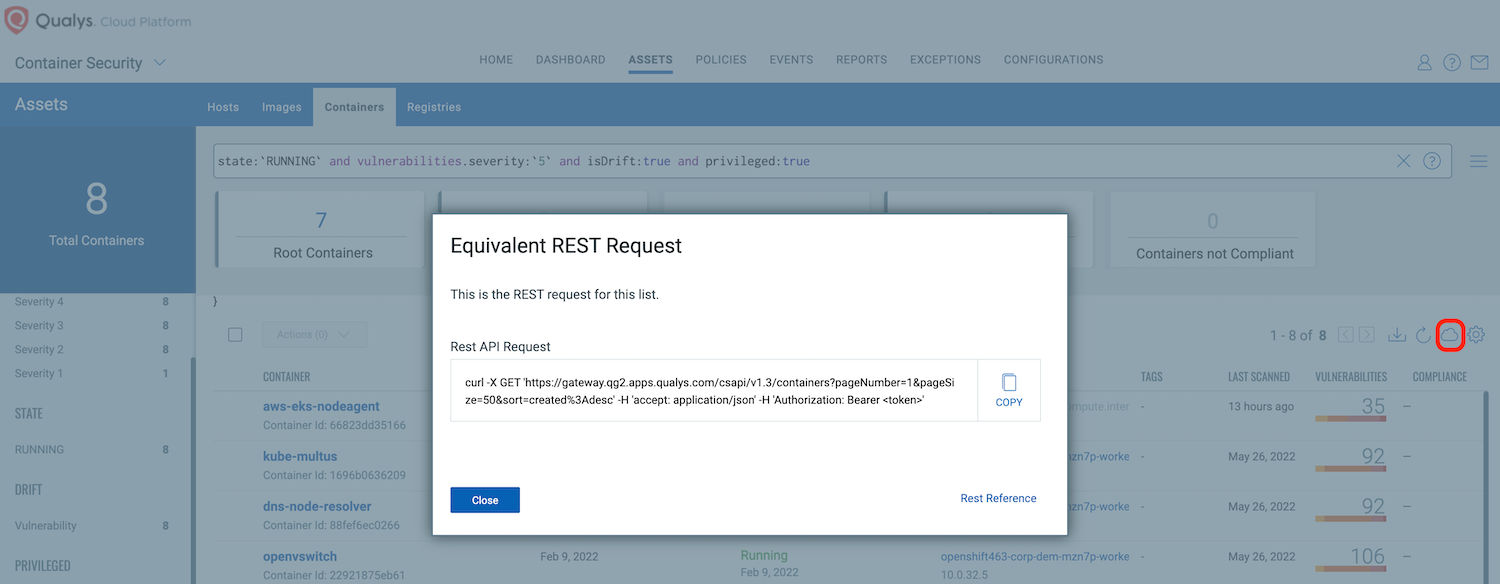
All features of Container Security are available through REST APIs. An equivalent Rest API request for each tab is provided in the user interface. (Marked with a circle on the figure below).
Documentation
Troubleshooting and Help
Container Security Troubleshooting | How to collaborate with Qualys Support
This is wonderful Blog Nirav – appreciate you taking the time to write this.