Qualys Enterprise TruRisk™ Platform Extends FIM with Real-Time Monitoring of Unauthorized Access to Sensitive Data and Configuration Change Detection on Network Devices
Table of Contents
- Introducing FIM 4.0 with File Access Monitoring (FAM) and Agentless FIM to ensure compliance with the new PCI 4.0
- PCI DSS 4.0 mandates FAM and FIM on network devices
- Why is FAM key for your compliance and security?
- How is FAM different from FIM?
- Your network devices must be protected
- Qualys FIM for Network Devices
- Key differentiators of Qualys FIM
- Summary
- Learn more
Introducing FIM 4.0 with File Access Monitoring (FAM) and Agentless FIM to ensure compliance with the new PCI 4.0
File Integrity Monitoring (FIM) solutions are essential for virtually any organization to help identify suspicious activities across critical system files and registries, diagnose changes, and send alerts. However, not all FIM solutions are created equal. To ensure adequate compliance and cybersecurity resilience, any FIM solution should include File Access Monitoring (FAM) and support for agentless devices.
With File Integrity Monitoring 4.0, Qualys has introduced the most comprehensive FIM solution, which includes real-time File Access Monitoring (FAM) and Agentless FIM, starting with FIM on network devices.
PCI DSS 4.0 mandates FAM and FIM on network devices
According to PCI DSS 4.0, “The cardholder data environment (CDE) is an example of a more sensitive
area within an entity’s network” and requirement 10.2.1.1 states that “Audit logs capture all individual user access to cardholder data.” This means that any access to sensitive data, such as cardholder data, must be detected and alerted in real time, which is precisely what Qualys FAM provides.
Additionally, PCI DSS 4.0 Requirement 1.2.2.c requires entities to “examine network configuration settings to identify changes made to configurations of Network Security Controls (NSCs).” This use case can be achieved by FIM on network devices, another groundbreaking feature released by Qualys FIM.
Why is FAM key for your compliance and security?
Unauthorized access to sensitive data can lead to data breaches, which makes it critical to identify high-frequency and high-risk file accesses in real time. While it won’t stop unauthorized access, it can put your team into action more quickly and mitigate the damage.
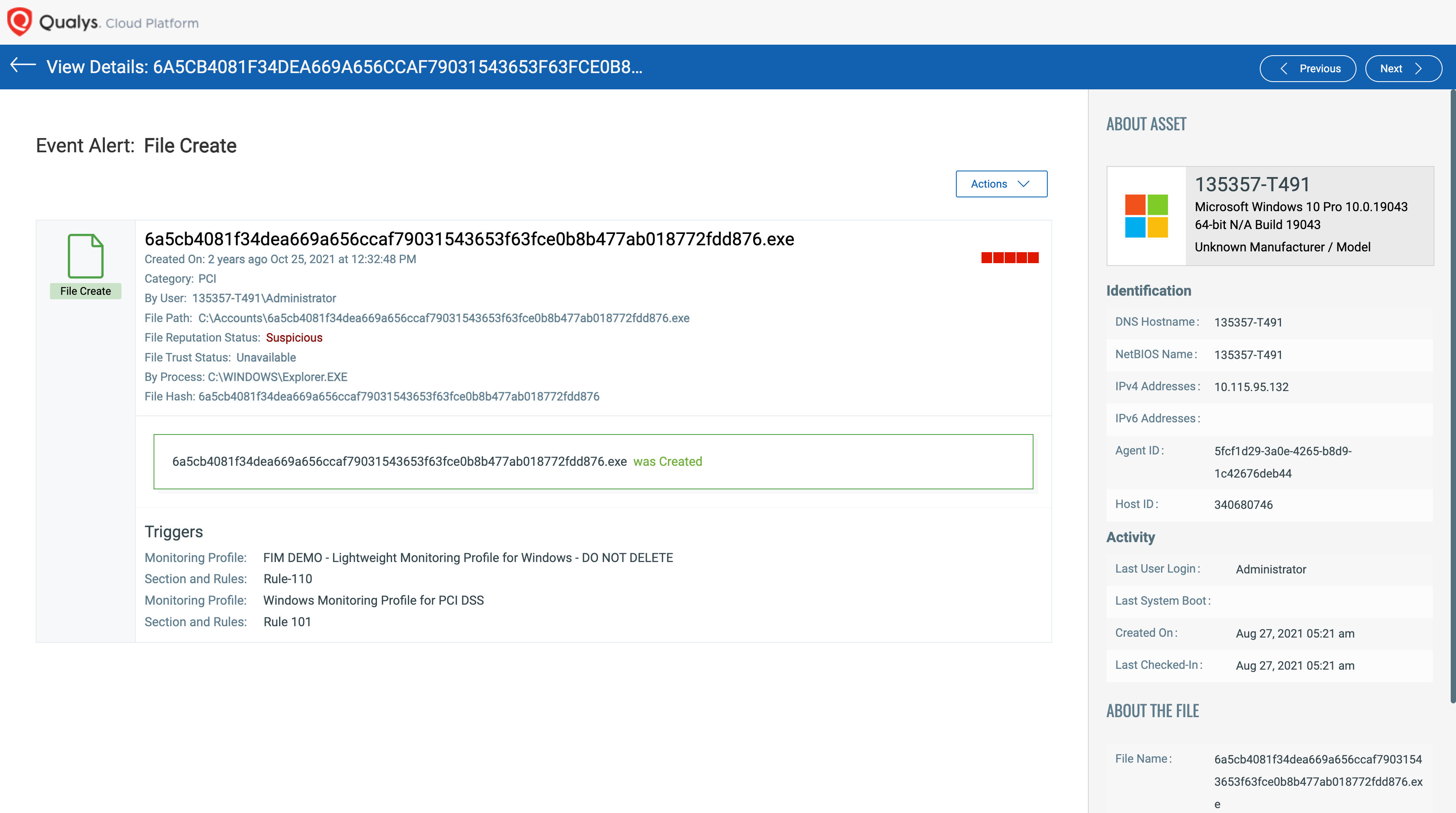
FAM allows you to generate real-time alerts when critical files with sensitive data are accessed by unauthorized users. The figure below shows the staggering number of unauthorized access attempts made during a 6-month timeframe.

These access operations would likely go unnoticed if there’s no FAM solution in place to create alerts, and this could potentially lead to a breach if it is not taken care of in time. Furthermore, without the power of noise canceling, reviewing two million highly sensitive events is unreasonable. The combination of Qualys noise canceling technology with the power of FAM allows customers to filter efficiently through the vast number of unauthorized access events.
How is FAM different from FIM?
- FIM generates alerts when the integrity of a file is modified. If sensitive data is accessed but not modified, FIM doesn’t generate any alerts and data theft goes unnoticed as no hash changed on access operation.
- FAM augments FIM by generating alerts for these unauthorized access operations and provides comprehensive “who-what-when and where” details.

For more details, refer to this blog post: Real-time File Access Monitoring (FAM) with Qualys FIM.
Your network devices must be protected
According to Gartner research, 95% of all firewall breaches are caused by misconfiguration, not flaws, which makes it imperative to monitor for any changes to configuration from a hardened baseline.
Expanding FIM usage to network devices ensures you gain complete visibility over your networking infrastructure changes. This is critical in detecting any accidental or intentional modifications that may lead to unauthorized network access or other related security breaches. This is also a core compliance requirement your auditors may look for.
FIM on network devices allows you to generate alerts when a network configuration is modified. This alert includes the side-by-side comparison of a baseline versus a modified configuration.

Qualys FIM for Network Devices
Qualys FIM allows our customers to enable FIM capabilities without the need to install a new FIM agent, as it utilizes the same Qualys agent to provide an industry-leading FIM solution. Now, with the introduction of FIM on network devices, Qualys customers who use Qualys scanners can leverage the same scanners without needing to change configurations or provide new credentials to enable FIM functionalities on their network devices. By utilizing the same scanner, Qualys FIM customers can start seeing results quickly while significantly reducing the maintenance and security costs involved in configuring and managing the different scanners required to store critical credentials.
For more details, refer to this blog post: Agentless FIM for Detecting Network Configuration Changes.
Key differentiators of Qualys FIM
- The most comprehensive FIM solution: Agent-based and agentless deployment options. Coverage for servers, endpoints, network devices, and more.
- File Access Monitoring (FAM): Empowers SOC teams with real-time alerts for access to sensitive data, ensuring proactive threat response.
- Ready-to-use, fine-tuned profiles for compliance frameworks: Reduces analyst time by 50% with streamlined setup and analysis.

- Reduced compliance risks: Comply with regulatory compliance mandates and frameworks such as PCI DSS 4.0, HIPAA 2023, NERC CIP, GDPR, CCPA and NIST CSF 2.0, NIS2, and many others.
- Always remain audit-ready: Built-in automated incident management and compliance reporting with dynamic dashboards, designed especially for PCI DSS 4.0 and other regulations.


- Minimized alert fatigue with noise-canceling FIM: Eliminate 90%+ of the noise for trusted users and processes. Built-in threat intelligence enriches file reputation status for binaries and portable executable files, enabling you to easily detect malicious or suspicious hashes.
- Extended data retention: Qualys stores FIM events on our platform for 13 months with all the data immediately accessible for analysis, saving you operational costs and ensuring full compliance.
- Ready for PCI DSS 4.0: Helps meet all PCI DSS 4.0 FIM requirements: Qualys FIM Has You Covered.
Summary
FIM 4.0 takes Qualys FIM to the next level, allowing you, our customers, to track not only file and folder changes but also critical file access. Furthermore, as many critical devices in every infrastructure are network devices, expanding Qualys FIM to support network devices ensures full protection and ensures audit results are successful. The new FAM and FIM on network devices are available now and are part of the FIM license; if you own Qualys FIM, you can start using those capabilities today.
To experience Qualys File Integrity Monitoring 4.0 for yourself, start a trial today.