Understanding the Hidden Cyber Risk from Tech Debt and EoL/EoS Security Gaps

Table of Contents
End-of-life (EoL) and end-of-support (EoS) hardware, software, and operating systems exist in every single technology environment, and they are an exponential multiplier of cyber risk. By definition, vulnerabilities with EoL/EoS technology are unpatchable. In some cases, IT teams can pay for extended support. But in other cases (such as unsupported OSS components), outdated technology is a ticking time bomb of cyber risk. Attackers have exploited vulnerabilities in EoL/EoS technology in many prominent events, causing global business disruption and exposure. Such examples include:
- 2023 U.S. Federal Agency attack resulting from unsupported versions of Adobe ColdFusion
- More than 50% of application installations with Log4j were “end-of-support” on Day Zero of the Log4Shell vulnerability
- 98% of computers affected by the 2017 WannaCry attack were running an EoL version of Windows 7
Regulations concerning EoL/EoS are increasing. PCI, SOX, HIPPA, and FedRAMP have issued compliance standards and penalties for failing to replace known malicious software. NIST and NCSC have also provided guidelines and compliance frameworks. In addition, the OASIS Open Group has launched the Open EoX initiative to standardize best practices for communicating EoL/EoS across vendors and manufacturers. These are positive steps, but they don’t resolve the immediate need for organizations to track, prioritize, and eliminate the risk from EoL/EoS proactively.
This blog post will quantify the cyber risk associated with EoL/EoS for the average organization, explore a proactive solution for mitigating that risk, and provide a way for CISOs to lead or influence the organization’s approach.
How Risky Is EoL/EoS Technology and Its End-of-Life Vulnerabilities?
While we know EoL/EoS technology exists in the environment, every CISO wants to understand the risk to their most critical assets.
According to Qualys Threat Research Unit, 20% of critical assets have confirmed high-risk EoS software.

It’s true—one in five critical assets has unpatchable, EoS software with vulnerabilities scored “high” or “critical”. These assets can include PII or customer data, production databases, customer-facing services, or other crown jewels of the business.
The more critical the asset, the more critical the cyber risk.
But what about attackers? How often are they targeting EoL/EoS technology?
Nearly one-half (48%) of CISA Known Exploitable Vulns are found on EoS software, so attackers are targeting out-of-date technology often. In fact, vulnerabilities associated with EoS software are 4x more likely to be weaponized.
With that in mind, it should come as no surprise that EoL/EoS technology is often associated with high-profile attacks.
Why Do Organizations Struggle to Manage Cyber Risks from Tech Debt and EoL/EoS Challenges?
Simply put, many organizations often do not consider cyber risk when prioritizing upgrades to technology—unless it is responsive.
Most organizations (larger ones in particular) have tasked IT teams with complete control of managing the budget and resources required to upgrade technology. On the surface, the primary risk of tech debt is business disruption. Outdated software, systems, and technology can fail at the worst times, costing teams productivity and revenue. As a result, CIOs and IT leaders focus on preventing business disruption.
In the event of a Log4Shell-type outbreak, the organization scrambles to respond to the cyber risk associated with end-of-support software. These upgrades became an urgent priority only after the disclosure of Log4Shell, as evidenced by the fact that over 50% of vulnerable installations were end-of-support on Day 0. While these assets may not have been candidates for upgrades due to business disruption, they certainly became business-critical in the face of critical security risk.
IT and Security teams need to prioritize according to cyber risk proactively, and it must be collaborative.
Cybersecurity teams hold the keys to cyber risk data that can drive better tech debt management. If CISOs and SecOps leads are not tracking the cyber risk associated with EoL/EoS and sharing that data with IT, it’s time to start.
But how?
Solution to Proactively Manage Tech Debt and EoL/EoS Risks.
The infrastructure is likely already in place for cybersecurity teams to track and mitigate risk from EoL/EoS proactively. They already account for asset criticality, vulnerabilities (and likelihood of exploitation), and other multiplying risk factors. They simply need to add cyber risk from EoL/EoS to their formula and, most importantly, communicate this data with IT to prioritize upgrades.
That means projecting upgrades for software, hardware, and operating systems 6 to12 months ahead of the EoL/EoS date, identifying critical assets and high-risk vulnerabilities associated with tech debt, and providing clear prioritization of cyber risk to IT. Ideally, this data should sync with the CMDB (IT’s source of truth for business operations) so that each team maintains a proactive view. This way, IT leadership can budget for upgrades proactively, minimizing the risk of unpatchable, obsolete technology prior to the next zero-day outbreak.
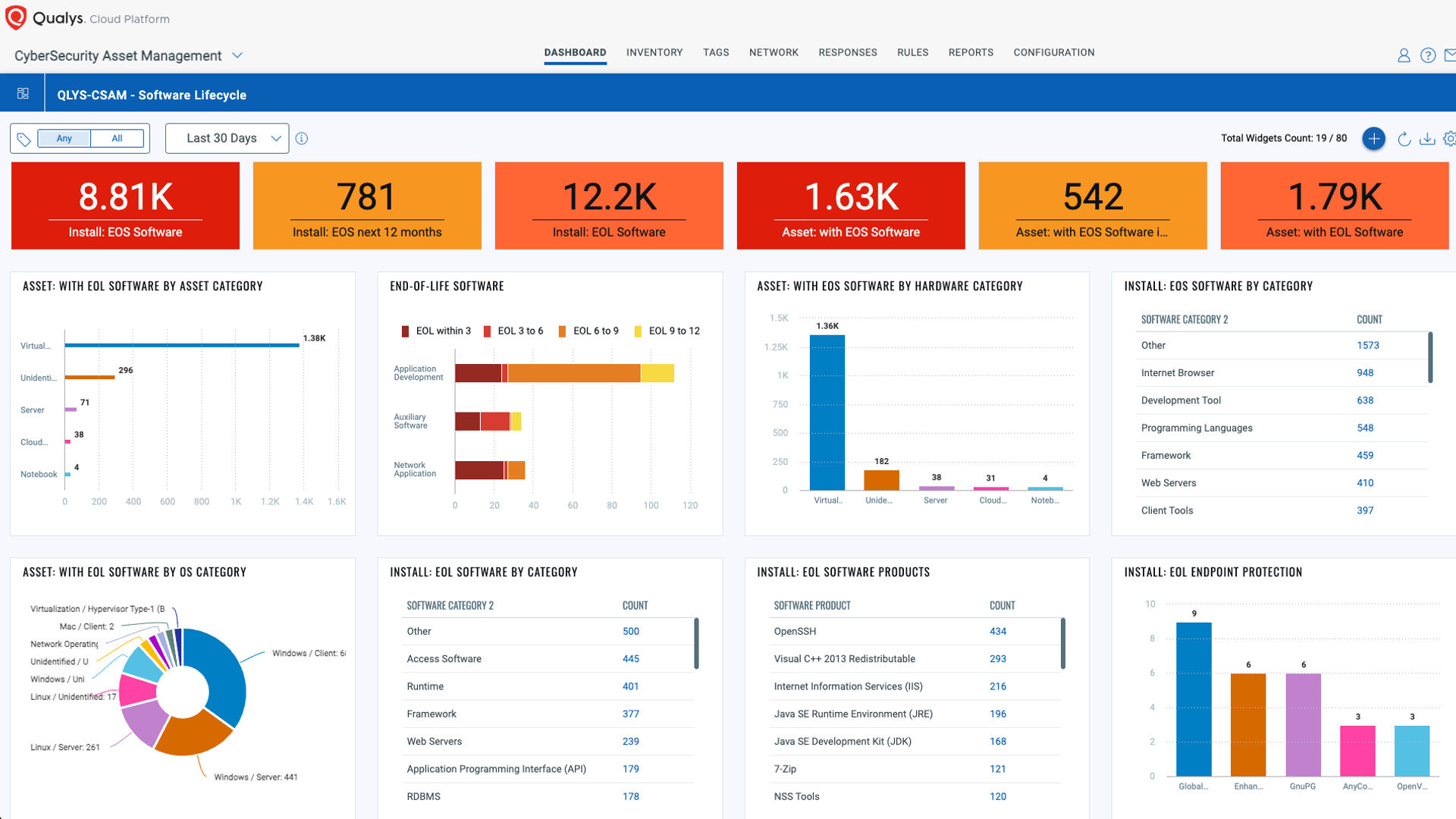
Get the Access to the Qualys Tech Debt Report at No Cost
Qualys CyberSecurity Asset Management has long provided proactive tech debt management for customers. Now, we’re introducing a cost-free, frictionless snapshot view for all Qualys customers to take inventory of current and future EoL/EoS technology.
Request your tailored Tech Debt Report
With a single click, VMDR customers can download a snapshot view of upcoming EoL/EoS technology, the associated cyber risk, and tailored recommendations for priority upgrades.
The Tech Debt Report comes with a 30-day CSAM trial to start proactively managing risk from tech debt.
The data is powered by the Qualys Threat Research Unit, including a continuously updated catalog with over 5,000 software publishers and over 1,400 hardware manufacturers. It maps upcoming tech debt to CVEs and Threat Intel and accounts for asset criticality when pinpointing the most critical cyber risks.
Download your Tech Debt Report today for a snapshot view of all current and upcoming EoL/EoS, share with IT leadership, and start building a proactive Tech Debt Program that always accounts for cyber risk.
Contributors
- Pablo Quiroga, Director of Product Management, Qualys