Security, Uninterrupted: Inside Qualys’ Zero-Touch Security Vision with Qualys Cloud Agent
Table of Contents
- Zero-Touch Security: Autonomous Protection Across the Asset Lifecycle
- Discover and Secure Unknown Assets
- Effortless Agent Deployment Using Qualys Scanner
- Optimize Vulnerability Remediation with Zero-Touch Patch
- New Feature: Remote Log Collection for Seamless Troubleshooting and Analysis
- Efficient Cloud Agent Lifecycle Management
- Conclusion: Secure Your Assets With Zero-Touch Operations
- Get Started Today!
New Feature: Remote Log Collection for Seamless Troubleshooting and Analysis
In the modern enterprise, where resilience and scale are non-negotiable, the margin for error in cybersecurity has all but disappeared. Yet the tools available to security teams remain tethered to legacy workflows—dependent on IT tickets, cross-functional handoffs, and manual steps for even routine tasks like scanning for attack landscape, agent deployment, diagnostic log collection, manual scans, or vulnerability patching. This operational drag not only strains resources but introduces systemic risk: every delay introduces uncertainty, and every handoff becomes a potential vector for exposure.
At Qualys, we believe the path forward demands a re-architecture of operational security itself. Our answer is Zero-Touch Security—an initiative that eliminates the traditional friction points between intent and execution. Zero-touch does not mean absence of oversight; it means the removal of unnecessary intervention. It enables security teams to operate independently, precisely, and continuously across the asset lifecycle, from discovery and deployment to remediation and diagnostics, without requiring tickets, remote access, or IT intervention.
Let’s see what it means for Qualys to enable such a frictionless, autonomous security initiative.
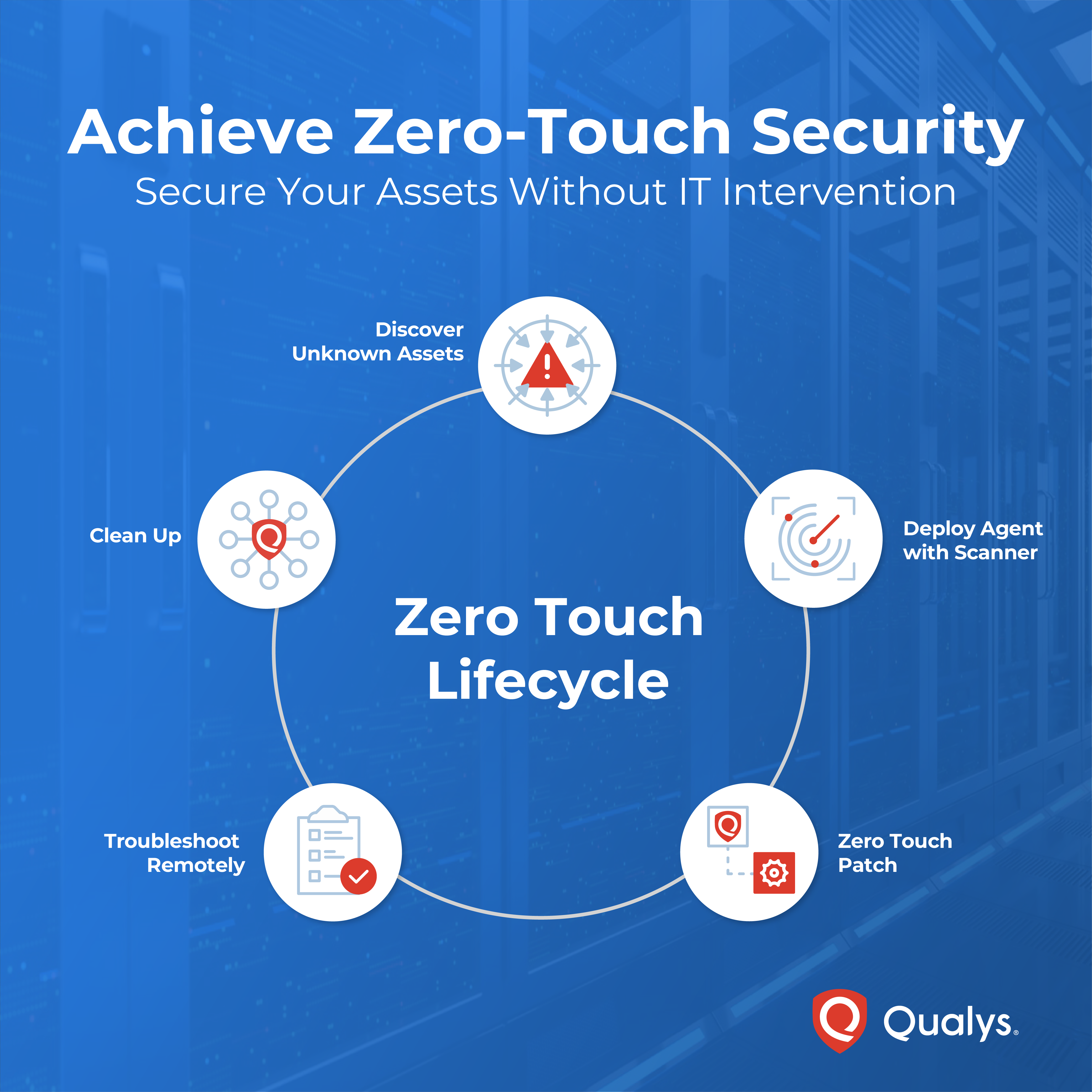
Zero-Touch Security: Autonomous Protection Across the Asset Lifecycle
With the Zero-Touch Security Initiative with Qualys Cloud Agents, Qualys provides a streamlined approach to security that ensures continuous protection and operational efficiency. By rethinking how core security processes are orchestrated and automated, we are establishing a new standard—one where security posture is not constrained by organizational structure or continuous manual efforts or operational bandwidth but propelled by intelligent automation and platform-level integration. By enabling Zero-touch approach, we are aiming not to just deliver tools but rather redefine what it means to operate securely at enterprise scale. All you need to do is to deploy Qualys Cloud Agent once!
Below are the key features that make zero-touch security management possible:
- Discover and Secure Unknown Assets: Automatically detect and monitor all devices on your network, even those you didn’t know existed, with zero manual intervention.
- Effortless Agent Deployment Using Qualys Scanner: Deploy agents across your network without relying on IT teams or third-party tools, ensuring full coverage and consistency.
- Optimize Vulnerability Remediation with Zero-Touch Patch Automate the patching process to quickly address vulnerabilities without disruption or delays.
- Remote Troubleshooting Without IT Tickets: Troubleshoot agent issues remotely without needing IT involvement, speeding up resolution and minimizing downtime.
- Efficient Cloud Agent Lifecycle Management Automatically clean up and manage agent data, ensuring a streamlined and secure asset management process over time.
These features enable a fully automated, secure, and streamlined process that frees up IT resources while ensuring continuous, real-time protection.
Let’s dive into each piece of the zero-touch journey.
Discover and Secure Unknown Assets
The Challenge: Blind Spots in Asset Visibility
Many organizations struggle to maintain a complete and accurate inventory of all assets within their environment. Devices may join the network without proper tracking, unauthorized endpoints can go undetected, and assets in shadow IT environments may operate outside security policies. Traditional asset discovery methods, such as scheduled scans, often leave gaps due to network segmentation, firewall restrictions, and remote work environments.
These blind spots create security risks by allowing unmanaged or rogue devices to exist undetected. Attackers exploit these gaps, using unknown assets as entry points to infiltrate networks. Without continuous monitoring, organizations remain vulnerable to breaches stemming from devices they didn’t even know existed.
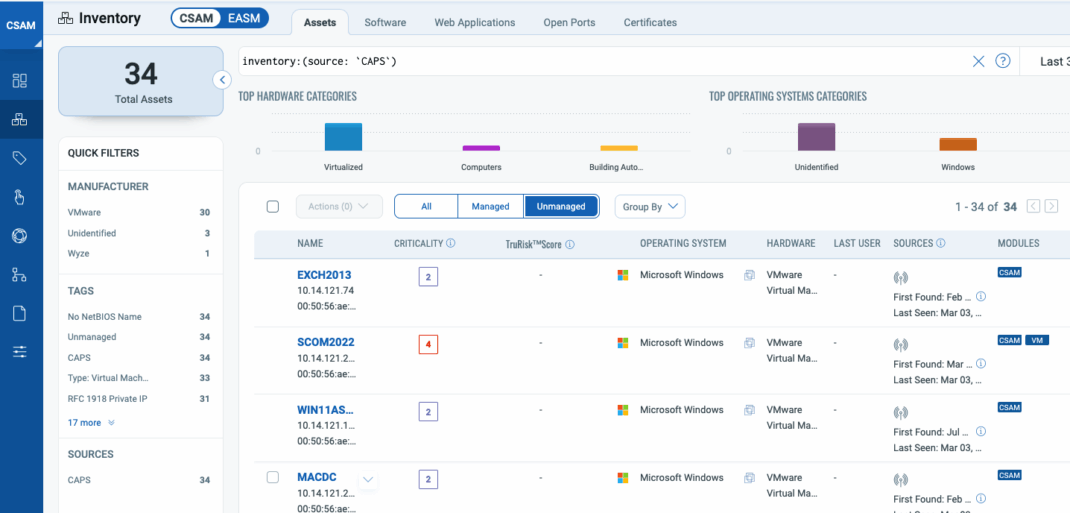
The Solution: Continuous, Unobtrusive Asset Discovery
Qualys Cloud Agent Passive Sensor (CAPS) continuously monitors network traffic to identify all devices communicating within an environment. Unlike traditional scanning methods, CAPS operates passively, meaning it detects assets without requiring credentials, firewall exceptions, or intrusive scans that could disrupt operations.
Key Benefits:
- Real-time asset discovery – Detects new devices as soon as they appear on the network.
- Zero disruption – No impact on network performance or business operations.
- Extended visibility – Covers both IT and OT environments, including unmanaged and IoT devices.
From Discovery to Protection: Streamlined Asset Activation at Scale
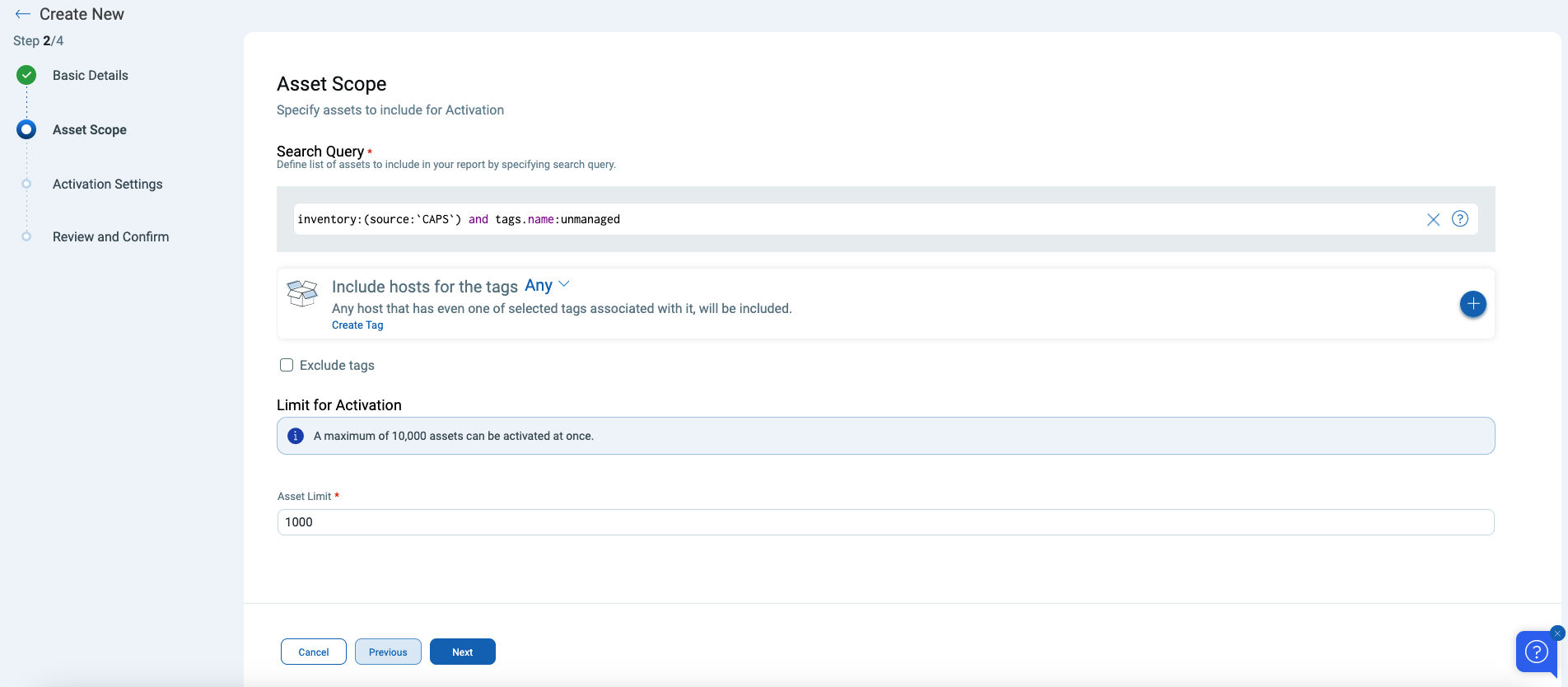
Once unknown assets are detected, Qualys makes it easy to bring them under security management through an automated Asset Activation Workflow. With rule-based activation, organizations can instantly operationalize discovered assets using flexible criteria—such as QQL queries or dynamic tags. The platform supports automatic activation across key modules, including Vulnerability Management, Certificate View, and Policy Audit.
This intelligent workflow accelerates time-to-value by eliminating manual processes and enabling dynamic, policy-driven asset onboarding. By automating activation based on real-time discovery, organizations can ensure that every asset—regardless of how or where it appears—is promptly brought under protection. With integrated reporting, fine-grained control, and support for key security modules, teams gain the visibility, agility, and scale needed to reduce risk and enforce consistent security coverage across the entire environment.
Effortless Agent Deployment Using Qualys Scanner
The Challenge: Complex and Inconsistent Agent Deployment
Rolling out security agents across a large, distributed environment can be a logistical nightmare. Many organizations rely on endpoint management tools or manual installations, which introduce inconsistencies and delays.
- Scalability Issues: Deploying agents across thousands of systems requires coordination between security and IT teams, often leading to delays and incomplete coverage.
- Configuration Complexity: Ensuring agents are properly installed and configured on every device requires significant effort, especially across diverse OS environments.
- Network and Access Limitations: Remote or isolated devices may not be reachable via traditional deployment methods, creating security gaps.
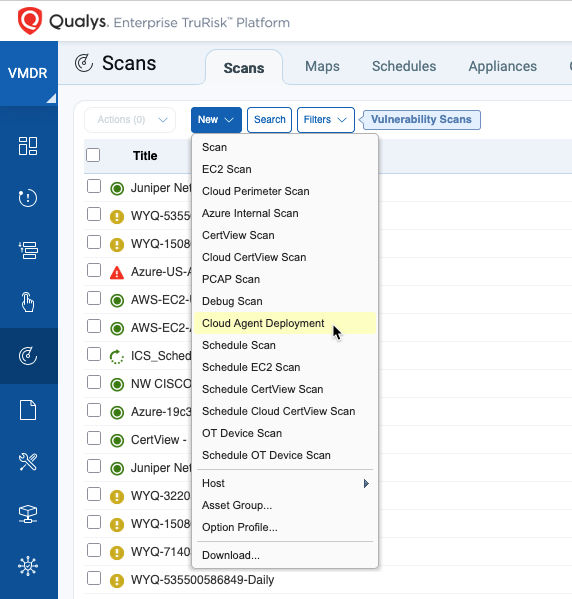
The Solution: Automated Deployment Using Qualys Scanner
Qualys streamlines deployment with Cloud Agent Deployment using Qualys Scanner, enabling organizations to install Cloud Agents directly through an existing Qualys Scanner Appliance.
Key Benefits:
- Automated installation – Deploy agents without manual intervention.
- Centralized control – Manage deployments across Windows and Linux systems from a single platform.
- No third-party dependencies – Eliminates reliance on additional deployment tools or IT support.
Read more about Qualys Scanner Deployment
Optimize Vulnerability Remediation with Zero-Touch Patch
The Challenge: Inconsistent and Delayed Patch Deployment
Vulnerability remediation is a critical component of any organization’s security posture. However, patching systems can be a slow and error-prone process, requiring manual intervention, coordination between teams, and often, disruption to business operations.
- Patch deployment delays – Waiting for scheduled maintenance windows or coordination with IT teams can lead to significant delays in applying critical patches.
- Risk of human error – Manual patch management processes are vulnerable to mistakes that may leave systems unprotected.
- Disruptions to productivity – Reboots and system downtime during patching can impact business operations, leading to decreased productivity and user frustration.
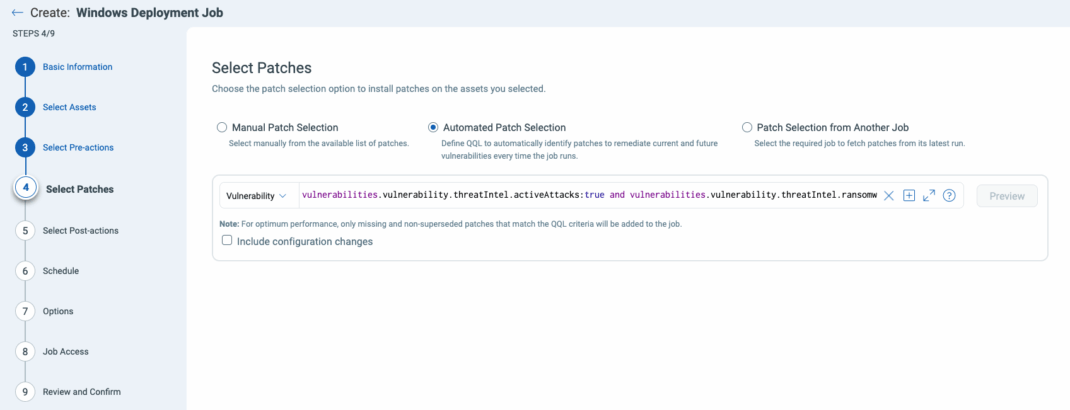
The Solution: Qualys Zero-Touch Patch Management
With Qualys Zero-Touch Patch, you can streamline vulnerability remediation by automating the patching process across your environment. This solution enables:
- Automated patch deployment – Once vulnerabilities are detected, patches are automatically deployed to affected systems without any manual intervention.
- Non-intrusive updates – Patches are applied with minimal disruption to business operations, reducing downtime and user impact.
- Comprehensive coverage – Zero-Touch Patch works across both on-premises and cloud environments, ensuring all systems are patched in real-time.
Key Benefits:
- Faster remediation – Reduce the time between vulnerability detection and patch deployment.
- Reduced risk – Apply critical patches automatically to protect against the latest threats.
- Minimal disruption – Keep systems secure without interrupting business continuity.
Learn more about Zero-Touch Patch
New Feature: Remote Log Collection for Seamless Troubleshooting and Analysis
The Challenge: Log Collection and Troubleshooting Complexity
Collecting and analyzing logs from security agents across large environments can be cumbersome. Traditional methods often require manual access to each device, leading to delays, incomplete data collection, and an inefficient troubleshooting process. This challenge is compounded by the need to open IT tickets, schedule remote sessions, and manually diagnose problems, which can introduce delays and end-user disruptions.
The Solution: Streamlined Remote Log Collection and Troubleshooting
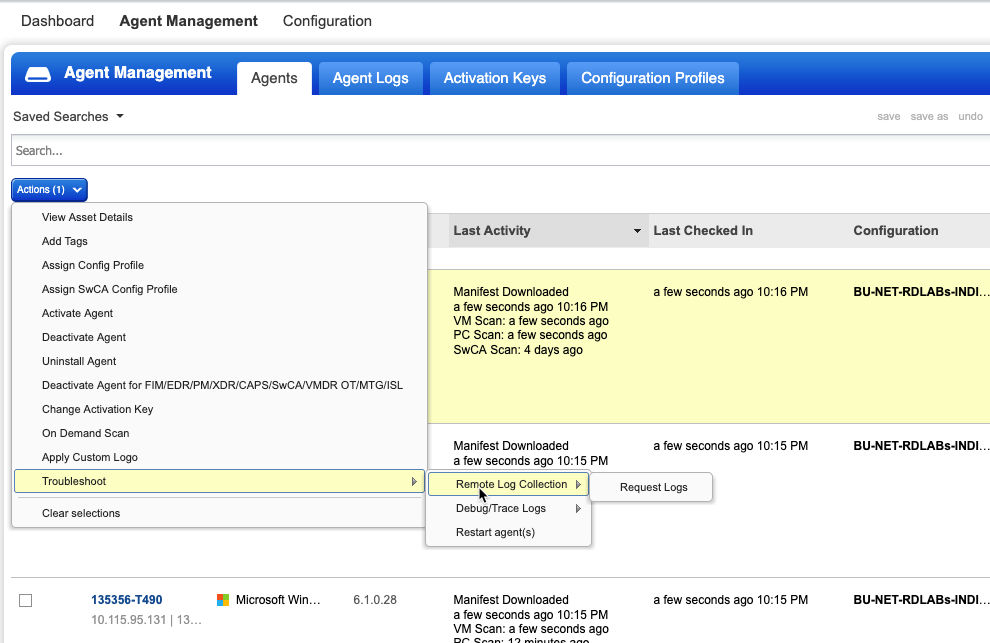
Qualys introduces the Remote Log Collection feature, which enhances troubleshooting and log analysis by eliminating the need for manual intervention or local access. This feature enables seamless remote log collection and a fully remote troubleshooting process, streamlining diagnostics and resolution while reducing IT workload.
Key Features and Benefits:
- Customizable Log Collection: Choose to capture all logs or focus on specific capabilities, such as Vulnerability Management, Patch Management, FIM (File Integrity Monitoring), and more. This customization ensures you collect only the relevant data for analysis.
- Agent Logs or Agent Logs Plus Directory Files: Select between receiving agent logs alone or a more detailed collection that includes agent logs and associated directory files for deeper analysis.
- Track Log Collection Status: Once log collection is requested, a new interface allows you to track the status in real-time. You can monitor whether logs are still processing or ready for download, ensuring transparency throughout the process.
- Download Logs for Seven Days: Logs are available for download within a seven-day window, providing ample time for analysis and troubleshooting.
- Remote Troubleshooting Without IT Tickets:
The Remote Log Collection feature works in tandem with remote troubleshooting capabilities, reducing the need for IT tickets, remote sessions, or user intervention. Key remote actions include:- Enable debug logging remotely for in-depth diagnostics.
- Restart agents without requiring local access.
- Disable self-protection for advanced troubleshooting when necessary.
- Capture agent logs remotely for faster issue resolution.
- To enable the new Remote Log Collection feature, please open a support ticket or contact your Qualys Technical Account Manager.
Pro Tip: To further enhance your troubleshooting experience, log into the support portal and use the Agent Log Analyzer Tool, which offers a graphical interface to interact with logs, allowing quicker identification and resolution of issues.
By centralizing these capabilities, organizations can quickly identify and resolve security agent issues, reduce exposure to security risks, and maintain continuous security operations, all without interrupting workflows or requiring IT support.
View full remote troubleshooting options
To enable the new Remote Log Collection feature, please open a support ticket or contact your Qualys Technical Account Manager.
Efficient Cloud Agent Lifecycle Management
The Challenge: Managing Agents Over Time Without Creating Gaps
Security agents must be properly maintained throughout their lifecycle—from deployment to retirement—to ensure an effective security posture. However, improper agent decommissioning can lead to:
- Lingering data clutter: Old, unused agent records accumulate, making it harder to manage active devices.
- Reinstallation confusion: If an agent is mistakenly removed, reinstalling and reconfiguring it can be cumbersome.
- Security risks: Unmonitored, outdated agents may continue running with old policies, creating potential vulnerabilities.
The Solution: Automated Agent Lifecycle Management
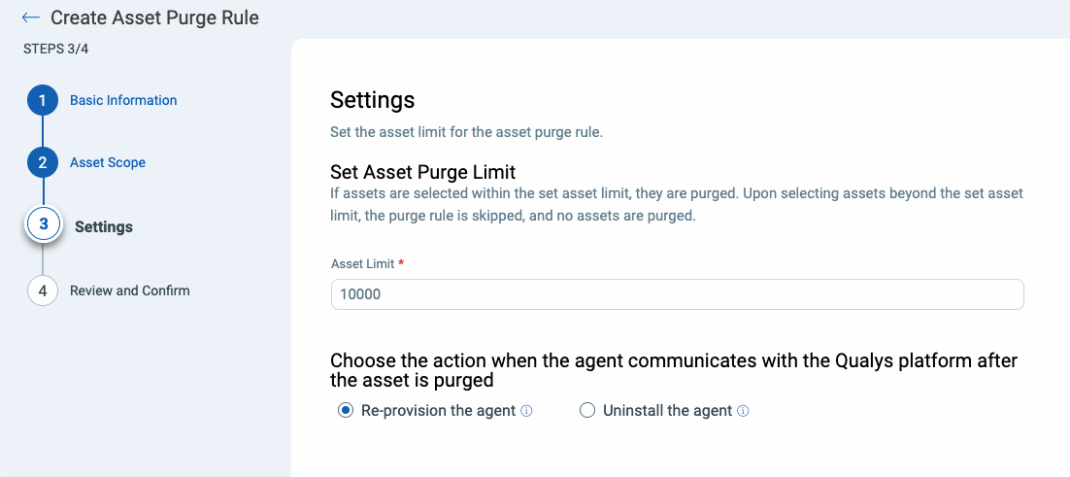
Qualys’ enhanced Cloud Agent purge rules provide a structured way to clean up agent data while maintaining control over asset visibility.
Key Benefits:
- Automated purging – Removes outdated agent data while retaining necessary historical records.
- Self-reinstatement – If a removed agent checks in again, it will re-provision itself without requiring a full reinstall.
- Optimized security – Ensures only active, managed agents are maintained, reducing clutter and potential risks.
Discover how to enhance agent lifecycle management
Conclusion: Secure Your Assets With Zero-Touch Operations
By leveraging these modern security features, organizations can:
- Eliminate the need for IT tickets and remote sessions – Free up IT resources and reduce response times.
- Ensure complete visibility and security of all assets – Detect and monitor every device in real-time.
- Streamline agent deployment and management – Automate processes without requiring manual installations.
- Troubleshoot and manage security issues remotely – Reduce disruptions while maintaining compliance.
A zero-touch security lifecycle reduces operational overhead and strengthens your overall security posture—without requiring constant team coordination. Secure your assets effortlessly and focus on what truly matters: growing your business.
Get Started Today!
Threat actors move fast, and your defenses must move faster. Instead of the traditional, reactive options, Zero-touch automation offers a smarter way forward: eliminating blind spots, streamlining response, and freeing your teams to focus on strategic priorities. With continuous protection and remote remediation baked into your operations, security becomes proactive by design, not reactive by necessity.
Now is the time to simplify, scale, and strengthen your security with Qualys’ zero-touch automation. Experience seamless vulnerability management without the need for IT intervention and empower your security teams to stay ahead of threats—before the next breach demands it.
Start your free trial of Qualys TruRisk™ Platform and transform your cybersecurity strategy!