How to Prevent NPM Supply Chain Attacks in CI/CD Pipelines with Container Security

Introduction
Containerized applications power the backbone of modern software delivery. But with speed comes risk. Vulnerabilities and embedded secrets can slip through the cracks long before they hit production. The result? Alert fatigue, noisy false positives, and critical exposures that disrupt sprints and delay releases. That’s why Qualys is introducing a new Pipeline Integration capability for Qualys Container Security (KCS), also available with Qualys TotalCloud, giving teams the ability to identify and address issues in real time within their CI/CD workflows. For organizations already using Qualys VMDR, this is a game-changer: the same trusted vulnerability management capabilities you rely on for endpoints and servers are now seamlessly integrated into your container security pipeline.
Unlike other market solutions that only detect issues and may create noise, Qualys KCS with QScanner goes beyond detection to provide actionable vulnerability and secret scanning directly in your GitHub CI pipeline. Qualys prioritizes risks using an accurate lens based on 25+ threat feeds, including VMDR, and leveraging the Qualys Threat Research Unit (TRU). This ensures developers work in harmony with security teams to fix issues by focusing on higher-priority risks.
This means developers and security teams can stop chasing noisy alerts after deployment and start preventing risky code from ever leaving the build stage. With security embedded without slowing down builds, you reduce operational overhead, cut down on rework, and align security with your development velocity. All in a single, unified solution that integrates with your existing Qualys ecosystem.
The Case of NPM Supply Chain Attack
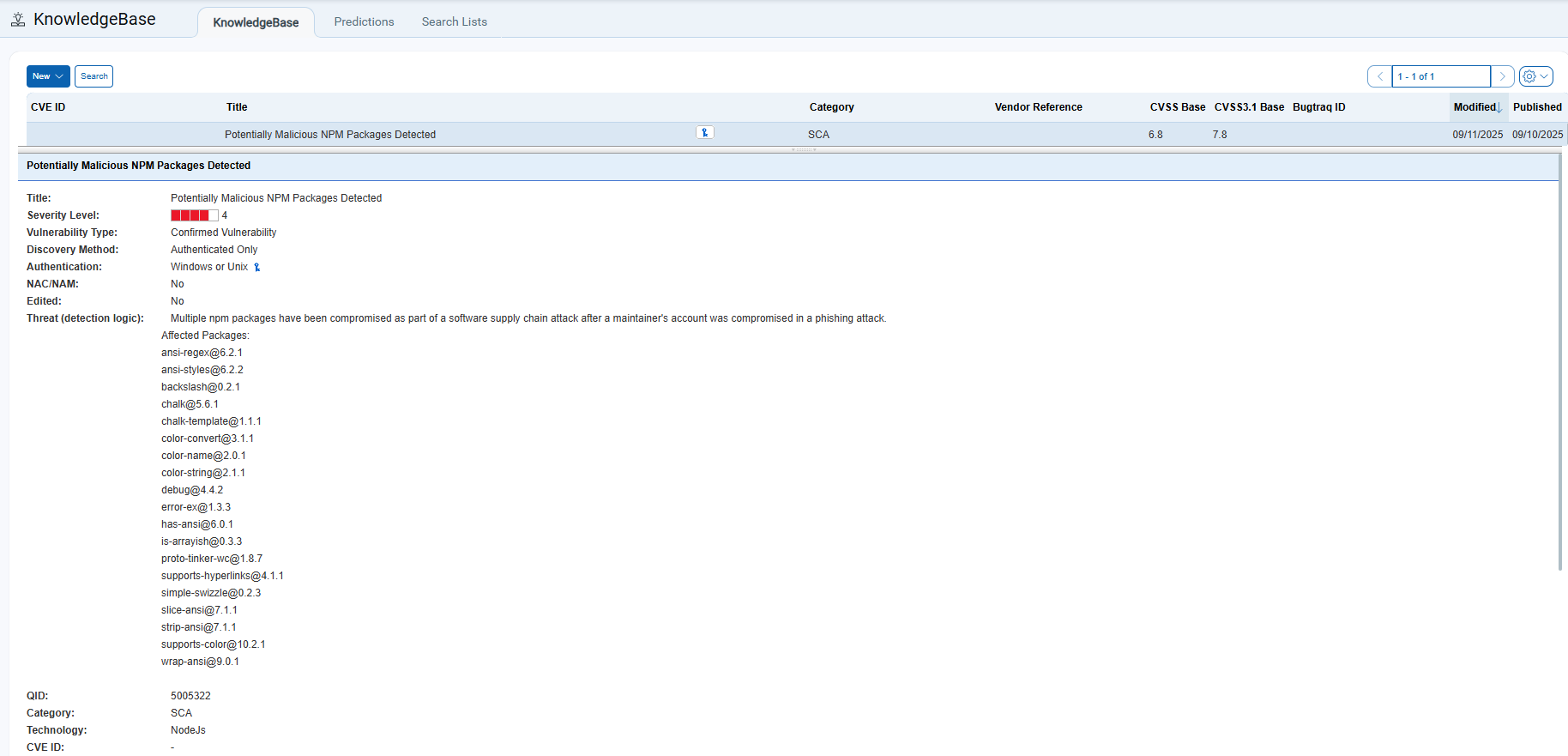
The Node Package Manager (NPM) is a default manager for the JavaScript runtime environment Node.js. It’s an important tool for JavaScript developers, enabling them to efficiently share and manage code packages. On September 8, 2025, attackers compromised 18 widely used NPM packages — including chalk, debug, ansi-styles, and strip-ansi — collectively downloaded 2.6 billion times per week. The malicious versions contained obfuscated JavaScript designed to intercept cryptocurrency transactions. The attack was stealthy, scalable, and devastating.
Organizations unknowingly pulled these poisoned packages into their builds, shipping tainted code into production environments.
This incident wasn’t just a wake-up call — it was a blueprint for how fragile modern software supply chains can be.
Enter QScanner: Your CI Pipeline’s First Line of Defense
For many modern teams, security often comes after the build is done — in post-deployment scans or manual reviews. But by then, it’s often too late or too expensive to fix. What you really need is a way to “shift left”. That’s where QScanner comes in. Let’s say you have a build process where:
- Source code is compiled via GitHub Actions.
- A container image is built as a pipeline artifact.
- This image is pushed to a registry (Docker Hub, ECR, GCR, etc.).
But before pushing, you want to ensure:
- There are no known vulnerabilities in the OS packages or application dependencies.
- The image doesn’t contain hardcoded secrets (e.g., API keys, passwords).
- The image meets your organization’s security policies.
This step is critical because fixing vulnerabilities or removing secrets after deployment, or missing several and resolving the wrong ones, is not only costlier but also increases your organization’s exposure window.
Integration with GitHub Actions
Scan the Image with QScanner in GitHub
Before you invoke QScanner to scan your container image, your GitHub Actions pipeline needs to perform some foundational steps. These steps ensure that a valid, scannable image is available — and that it’s built consistently in a way that QScanner can analyze effectively.
Here’s what needs to happen before QScanner comes into play:
- Build your code.
- Generate build artifact – container image.
- Download QScanner binary.
- Scan the generated image using qscanner. QScanner can scan both the image that is available locally in runtime (e.g. docker) or the image tar.
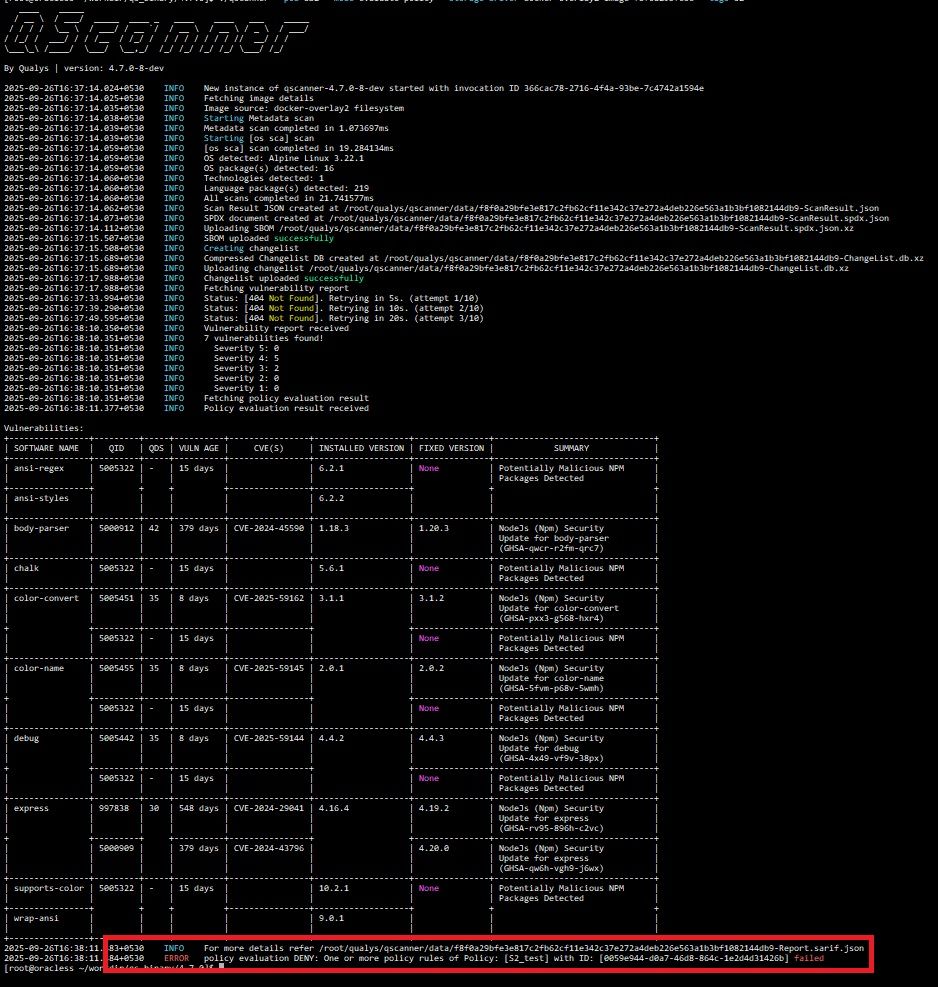
- Get vulnerabilities.
- Generate GitHub Actions Compliant SARIF report. This report gets generated by QScanner by default along with a summarized tabular report.
- Upload the SARIF report via codeql-action.

Detect vulnerabilities
When you integrate QScanner with GitHub Actions and output results in SARIF format, your findings don’t just stay in logs — they’re surfaced directly in GitHub’s Security tab under Code scanning alerts.
This is where security meets developer workflow. Instead of forcing developers to learn new tools or switch contexts, QScanner brings the insights directly into the GitHub environment they already use every day.
Where to find it?
In your GitHub repository:
- Go to the Security tab
- Click on Code scanning alerts
Here, GitHub displays a centralized list of issues detected during your builds — including:
- CVEs (vulnerabilities in packages/libraries)
- Secrets (tokens, credentials, keys)
- File locations and line-level context
- Severity and actionable remediation guidance

Scan for Embedded Secrets
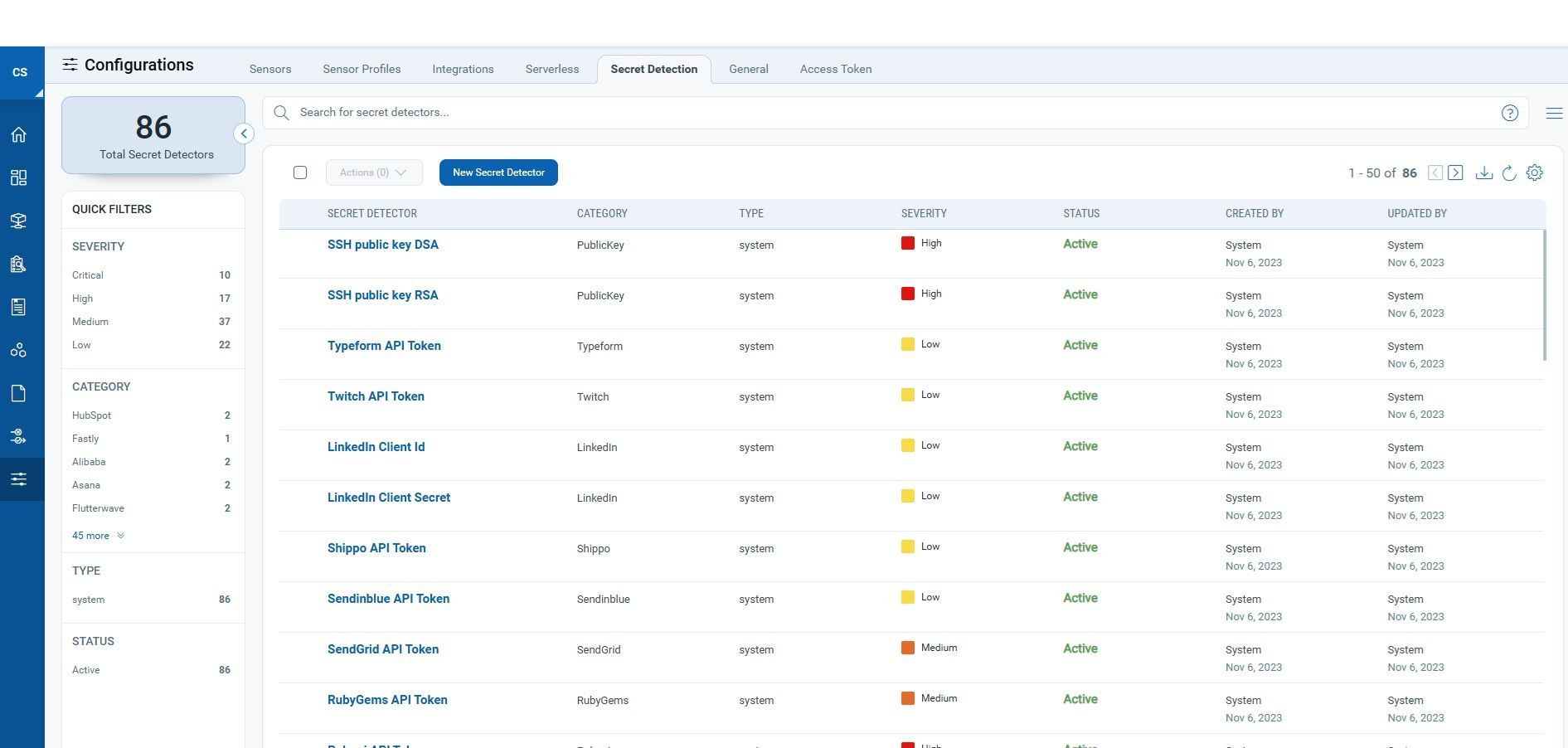
When you run qscanner with –scan-types pkg,secret, it will also scan your container image’s filesystem for exposed credentials. It uses 85+ system detectors and supports custom rules to flag secrets like:
- AWS keys
- Database credentials
- API tokens
- SSH keys, and more
Found something sensitive? The report shows exact file paths and line context so you can fix it before it leaves your CI/CD environment. Catching these issues early not only prevents security incidents but also helps maintain compliance with internal policies and industry regulations.
Enforce Policies with Centralized Evaluation
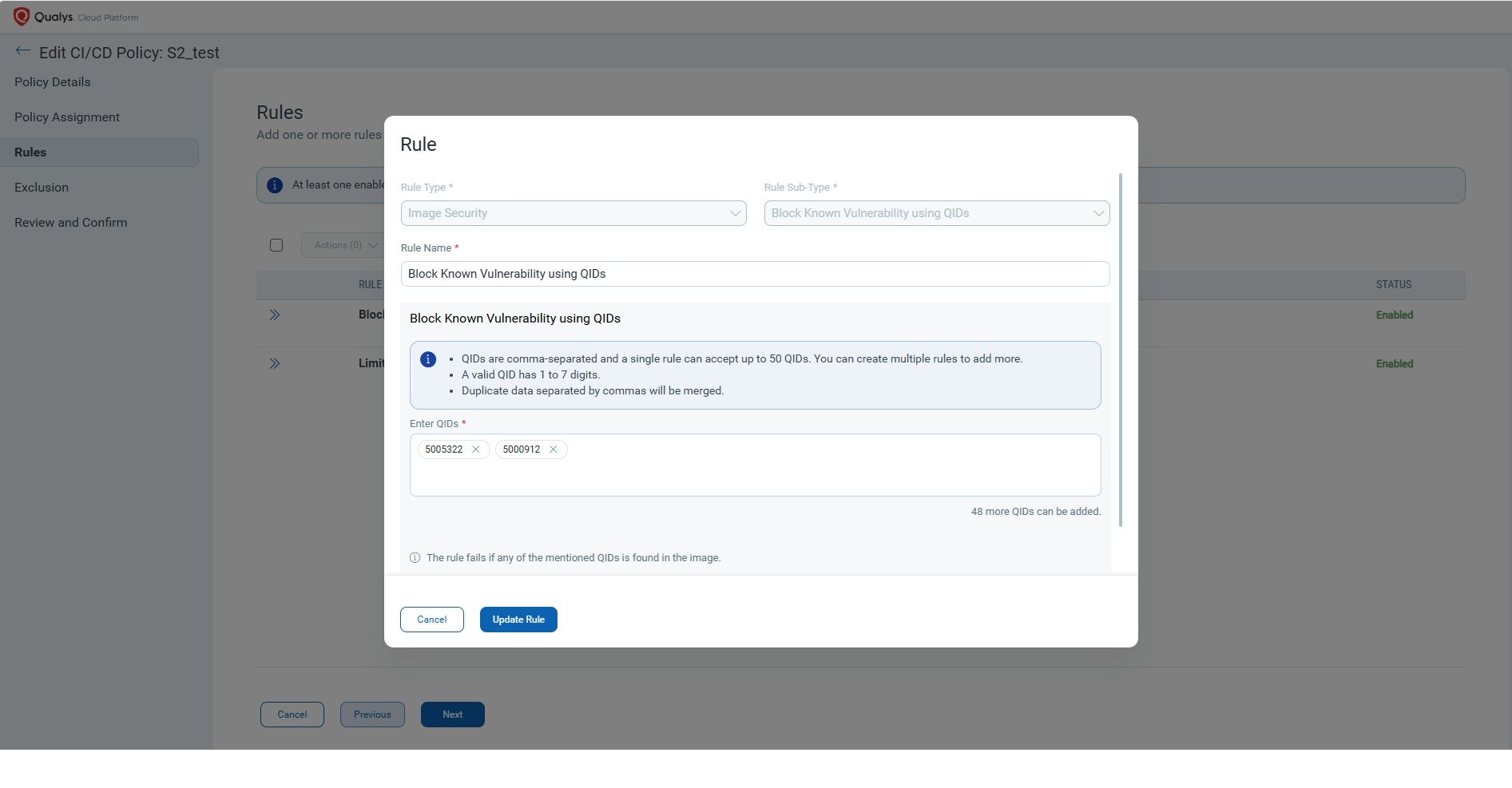
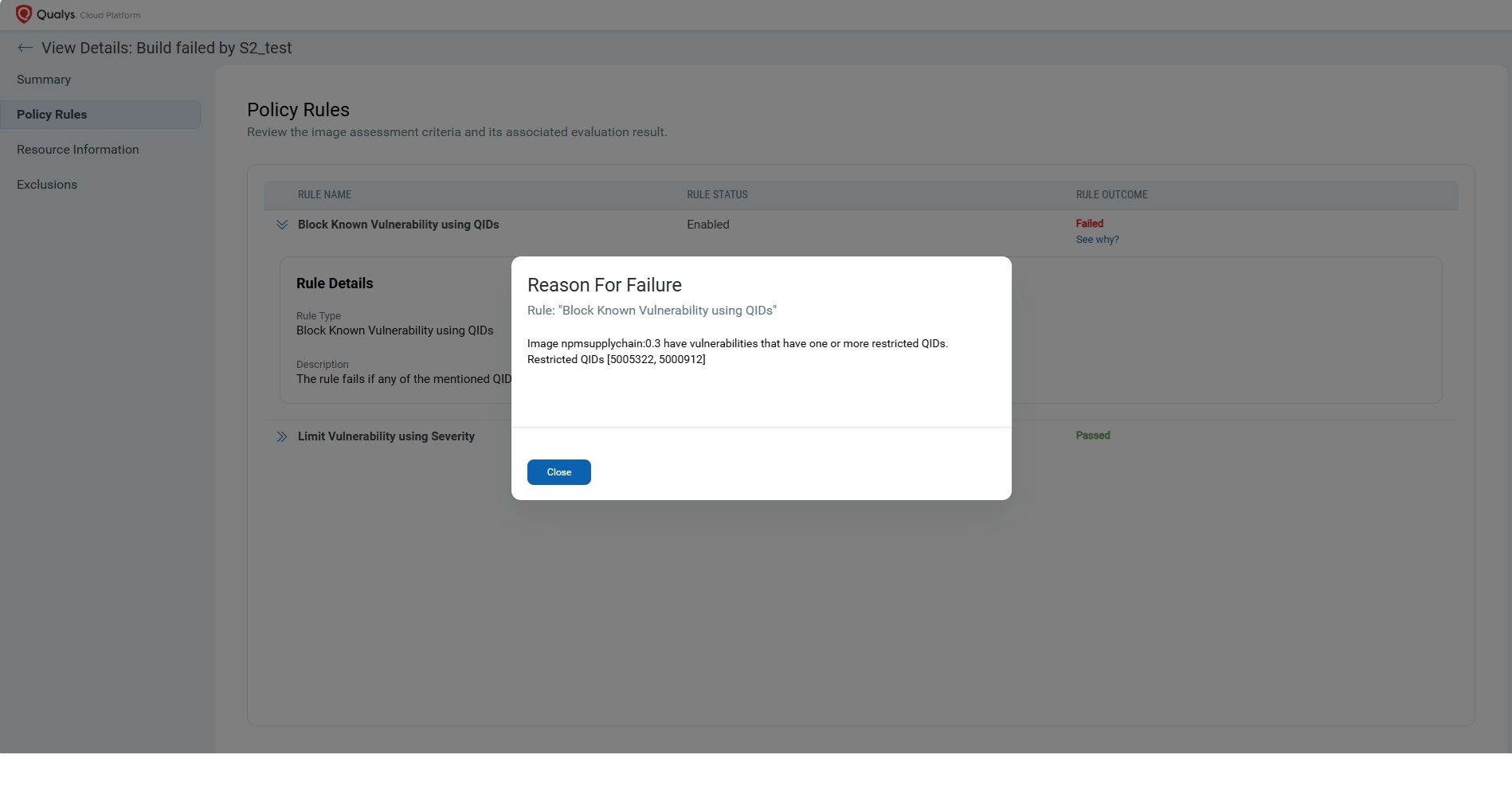
Want to automate enforcement across teams or builds? You can run qscanner with –mode evaluate-policy. You can define custom policy rules in the Qualys platform — for example:
- Block any image with Critical or High vulnerabilities
- Flag images containing secrets
- Enforce Qualys Detection Score (QDS) threshold.
These rules are evaluated automatically using the Qualys Centralized Policy Engine, and the results are available in the QScanner console. Depending on the results of the policy evaluation, you can pass or fail the build. This kind of automated governance ensures consistent enforcement of your organization’s security standards across every repository and every team, without manual intervention.
Why QScanner belongs in your CI/CD
Integrating QScanner into your CI/CD pipelines offers more than just scanning- it delivers intelligent, real-time security feedback that keeps your container images safe from the start. With this integration, you gain:
- Shift-left security: Detect vulnerabilities and secrets before they reach production
- Policy enforcement: Block non-compliant images automatically with QDS thresholds and central policy rules
- Native developer experience: QScanner’s SARIF output integrates directly into GitHub’s UI — no extra tools, log parsing or dashboards.
- Inline PR visibility: Developers see vulnerabilities and secrets right in pull requests, with file paths and context
- Security and development alignment: Security gates become part of the dev workflow, not an afterthought
- Automation made simple: Use GitHub’s built-in actions to upload reports and enforce quality gates in just a few lines of YAML
- DevSecOps alignment without slowing down builds
- Risk-based prioritization using QDS
- Faster remediation: Clear, prioritized findings help developers fix issues quickly and confidently
- Cleaner, safer container images in every release
With QScanner and GitHub Actions, you turn your CI pipeline into a first line of defense — ensuring every image your team builds is secure, compliant, and production-ready.
Ready to embed security directly into your workflows? Learn more about QScanner at https://docs.qualys.com/en/qscanner/release-notes/qscanner/qscanner_introduction.htm
Final Takeaway
The new QScanner integration with GitHub Actions is more than just another scan step in your CI/CD pipeline; it’s a critical shift-left capability that lets you catch vulnerabilities, embedded secrets, and policy violations before they ever become production issues. By leveraging Qualys’ deep vulnerability intelligence and centralized policy enforcement, DevSecOps teams can create harmony with security teams to optimize efforts and outcomes. They can move fast without sacrificing security, all while reducing noise and focusing on truly actionable findings.
Whether you’re already a Qualys VMDR customer looking to extend trusted protection into your container workflows or you’re evaluating solutions that truly align security with developer velocity, QScanner with GitHub CI integration delivers a clear advantage over point tools. Start building cleaner, safer container images today, and see how easy it can be to secure your software supply chain from the inside out.
Supply chain attacks are no longer rare — they’re inevitable. The question isn’t if your pipeline will be targeted, but when. With QScanner embedded in your CI/CD workflows, you gain the visibility, intelligence, and automation needed to catch threats before they ship. Don’t wait for the next NPM-style compromise. Shift left with QScanner — and secure your software supply chain from the inside out.
Schedule a call with a Qualys Cloud Security technical expert to learn more.