Active Exploitation of 7-Zip RCE Vulnerability Shows Why Manual Patching is No Longer an Option
A critical remote code execution (RCE) vulnerability in 7-Zip (CVE-2025-11001) is now being actively exploited. The issue stems from improper handling of symbolic links within crafted ZIP files. When a malicious archive is extracted, 7-Zip may write files outside the intended directory, allowing an attacker to overwrite system files or execute arbitrary code with the permissions of a service account.
Originally disclosed in October 2025, the vulnerability carries a CVSS v3 score of 7.0 and affects all versions prior to 25.0.0. Exploitation has been observed across multiple sectors, including healthcare and finance. A related issue, CVE-2025-11002, shares the same underlying cause and is addressed in the same update.
On November 18, 2025, NHS England Digital issued an advisory confirming active exploitation and urging organizations to update 7-Zip without delay. Unpatched systems remain susceptible to a range of impacts, including ransomware deployment, data theft, or persistent access through malicious ZIP files that may be triggered by simply opening or extracting an archive.
How Qualys Patch Management Helps Proactively respond to such Vulnerabilities
Manual patching for utility applications, such as 7-Zip, is often delayed, even when the security risk is high. Qualys Patch Management addresses this by enabling automated, prioritized, zero-touch patching, ensuring vulnerable systems are updated well before attackers can exploit them.
Automatic Patching of Applications Like 7-Zip
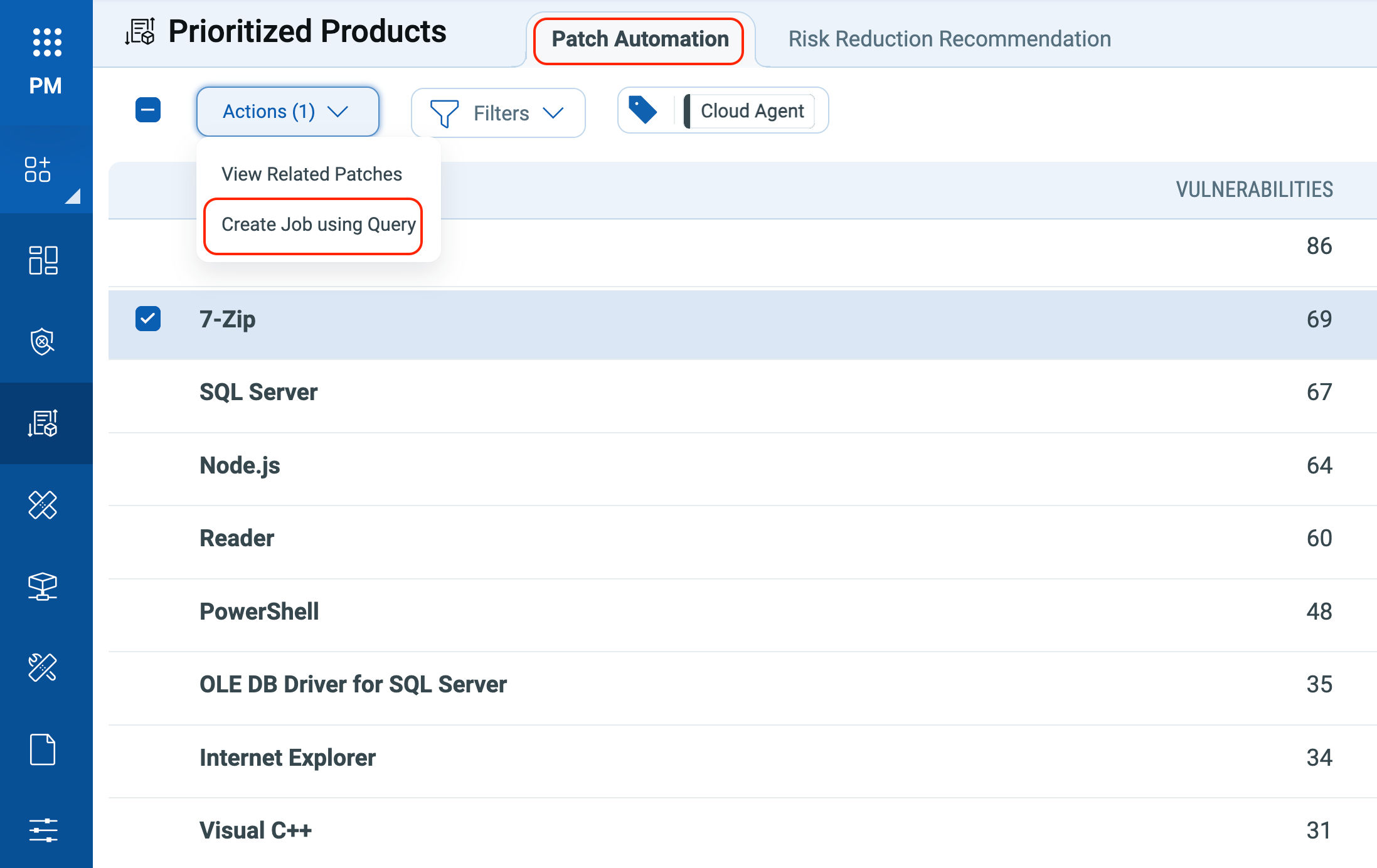
Qualys Patch Automation enables Security and IT teams to automatically deploy updates for commonly used products. Because 7-Zip is lightweight and its updates rarely affect workflows, it is well-suited for automated patching with minimal operational risk. In simple terms, it delivers low risk and high impact.
Prioritized Remediation Based on Real-Time Risk
Qualys identifies which systems are running vulnerable 7-Zip versions and applies the patch for CVE-2025-11001 and CVE-2025-11002, delivering an immediate, high-impact reduction in risk.
Conclusion
With active exploitation of CVE-2025-11001 underway, it is important to update 7-Zip to version 25.00 or later, which includes fixes for both symbolic-link vulnerabilities.
Integrating Qualys Patch Management ensures updates are applied automatically and consistently, reducing your attack surface while keeping daily operations uninterrupted.
Discover a smarter, automated approach to securing everyday software with Qualys Patch Automation.