QSC18 Virtual Edition: Securing Containers – From Build to Deployments

DevOps teams have embraced Docker container technology because it boosts speed, agility, and flexibility in app development and delivery. But it also creates security and compliance challenges.
“Containers are revolutionizing the IT landscape,” Hari Srinivasan, a Qualys Director of Product Management, said during QSC18 Virtual Edition. As the next big thing in IT, containers are seeing tremendous growth in adoption.
“Containers are lightweight, efficient, portable, and they boot faster, making it highly efficient and easy for developers to deploy their applications,” he said during his presentation “Securing Containers — From Build to Deployments.”
Containers are lighter than virtual machines because they can be spun up without provisioning a guest operating system for each one. For that reason, they also churn much more frequently.
With containers, applications can be smaller, focused on one or a few capabilities, and more portable, because they can be easily distributed across an IT environment, he said. That’s why containers have helped popularize microservices, a new architecture where applications are structured as independent, small, modular services.
Container security challenges
Container security challenges include the use of un-validated software pulled from public repositories, which often contains unpatched vulnerabilities, and the deployment of containers with weak configurations.
In addition, containers communicate directly with each other via exposed network ports in a way that bypasses host controls, and they’re hard to track because they’re so elastic and ephemeral.
This means that security teams must be able to discover and track containers at scale and across their IT environments, and integrate and automate security tools into DevOps pipelines. They must also implement effective vulnerability management, and build a container-native program for preventing, detecting and responding to intrusions, Srinivasan said
Qualys Container Security
Qualys’ new Container Security (CS) application gives organizations total visibility and continuous security for containers. With Qualys CS, InfoSec teams get continuous discovery, tracking and protection of containers in DevOps pipelines and deployments at any scale, he said.
Let’s look in detail at several key features.
Discovery & Inventory
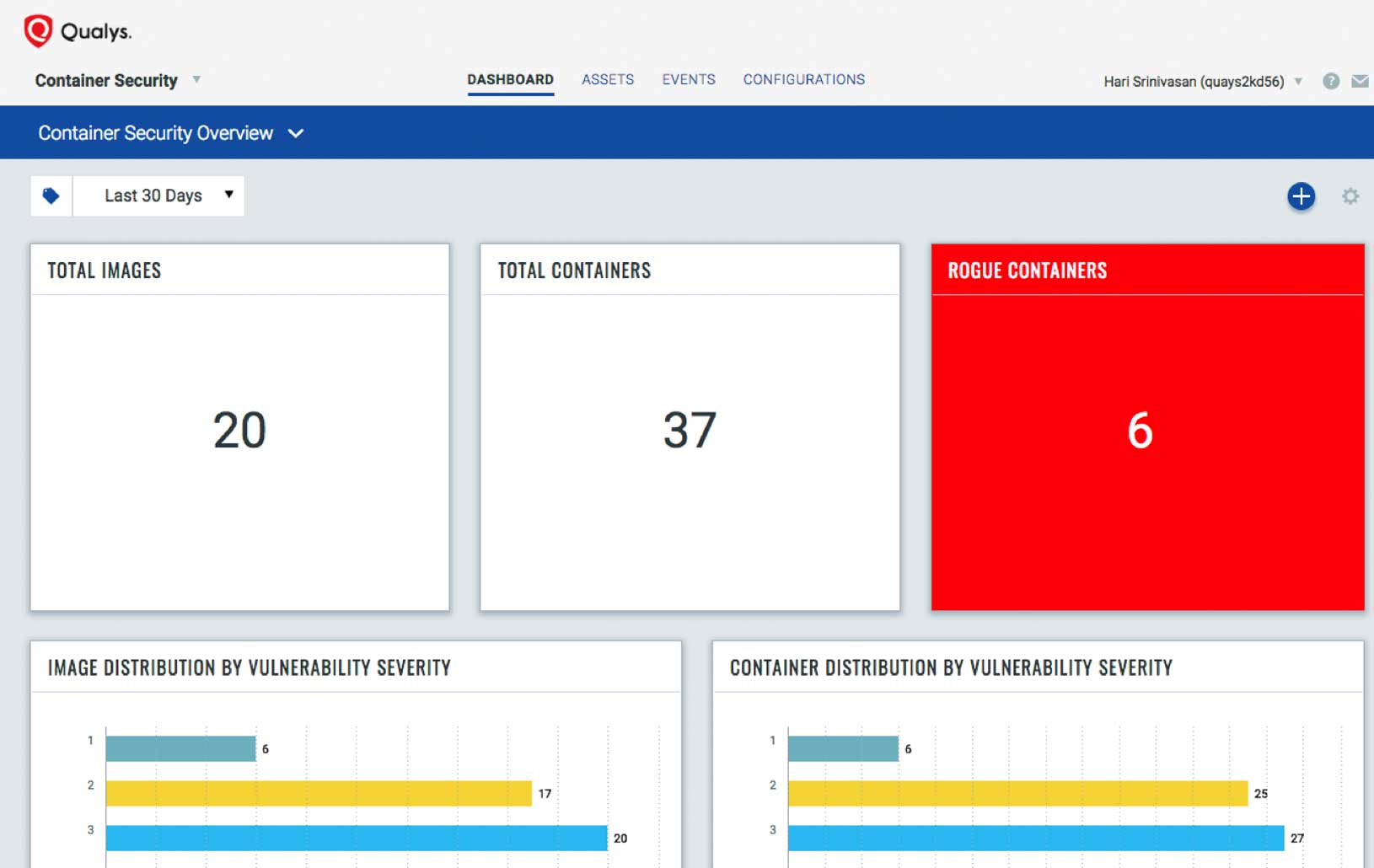
Qualys CS gives you visibility into your containers, so you can understand their deployment in your environment.
It provides complete topographic information on images, containers, and hosts, and detects where containers are hosted, and what’s their state, composition and behavior. In addition, Qualys CS helps you understand the associations across these environments to assess the impact of a threat.
This information is searchable, and can be visualized on Qualys CS’ dynamic and customizable dashboard.
Vulnerability Management
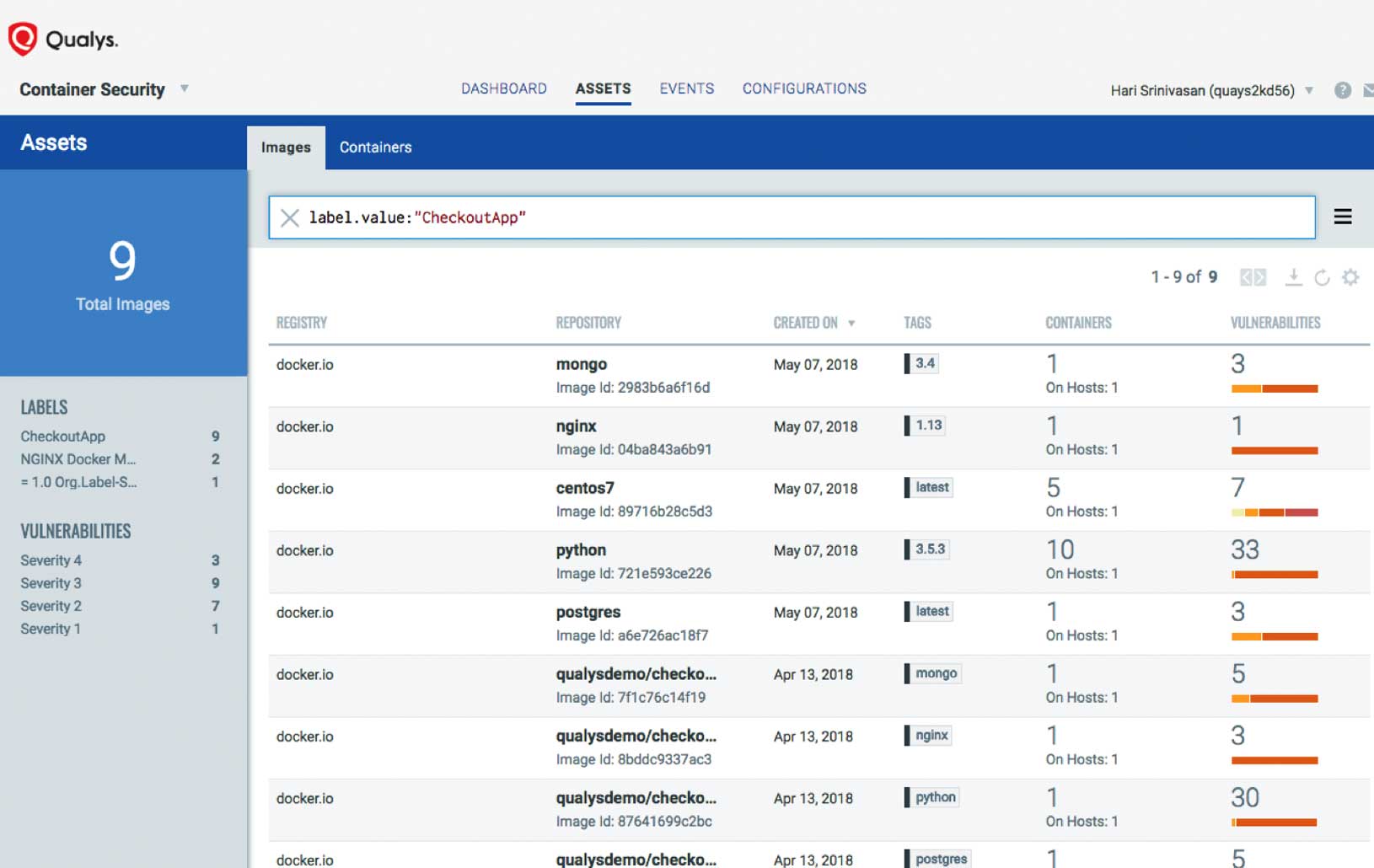
Qualys CS secures your entire container pipeline by performing vulnerability management from the ‘build’ to the ‘deployment’ stages.
- BUILD: At the ‘build’ stage, you can find and fix container vulnerabilities using Qualys CS’ Jenkins plug-in or REST APIs. Plug-ins for other CI/CD (continuous integration / continuous delivery) tools are in the works.
- REGISTRY: As secure images are pushed to public or private registries, Qualys CS scans and analyzes them either on demand or on a pre-set schedule.
- RUNTIME: At the ‘runtime’ stage, Qualys CS scans running containers for vulnerabilities and anomalous behaviors.
- HOST: Using Qualys virtual scanners or agents, Qualys CS identifies vulnerabilities and compliance issues of Docker hosts.
Runtime Tracking
With Qualys CS, you can identify rogue runtimes, thanks to its ability to track and log events as they happen in the system. “Since containers are highly ephemeral in nature, you need a constant watch on what’s going on in your environment,” Srinivasan said.
It’s key to detect if there are any changes happening in the containers, and what caused those variations. “Containers are supposed to be immutable. They are supposed to mimic the parent image,” Srinivasan said.
REST API Support
Qualys CS lets you automate security into DevOps processes and the CI/CD pipeline. “Well adapted into the modern practices of DevOps, all of the functionality set is available via REST APIs,” he said.
Native container sensor
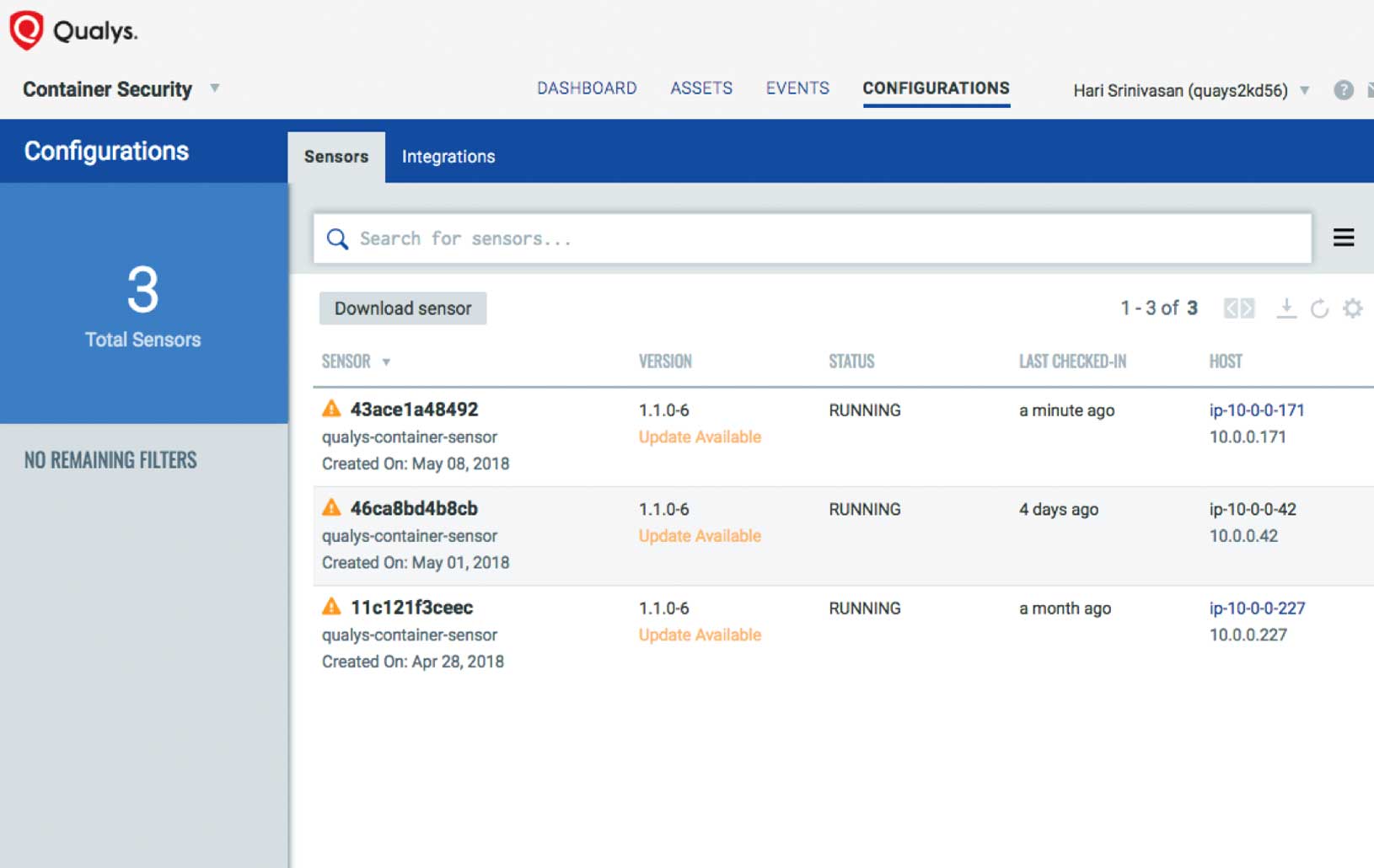
Qualys CS also features a native container sensor, which is distributed as a Docker image. Users can download and deploy it as a “sidecar” unprivileged container directly on hosts.
The sensor supports Docker containers running on Linux, and is deployable across Kubernetes, Docker Swarm and other orchestration environments. It’s self-updating and can be configured to communicate over proxies.
Powered by the Qualys Cloud Platform
Qualys CS is generally available today, along with almost 20 other security and compliance Qualys apps, all natively integrated and self-updating. The Qualys Cloud Apps are powered by the Qualys Cloud Platform, which provides end-to-end discovery, prevention, detection and response.
The platform gives organizations a continuous, always-on assessment of their global security and compliance posture, with instant, “single pane of glass” visibility across all IT assets, wherever they reside.
Qualys CS extends organizations’ security and compliance capabilities into new cloud workloads through the use of DevOps and containers.
“Qualys Container Security provides you with total visibility and continuous security for your containers,” Srinivasan said. “This is applicable to your ‘build’ environments and to your live, active runtime deployments.”
Watch the on-demand version of Srinivasan’s presentation, which goes into detail on these and other topics, features a demo of Qualys CS, and includes a Q&A with the audience.