Container Security Becomes a Priority for Enterprises
Among the IT innovations that businesses are using to digitally transform operations, containers might be the most disruptive and revolutionary.
“They’re a real game changer,” Qualys Chief Product Officer Sumedh Thakar said at QSC 2018 in Las Vegas.
DevOps teams have embraced containers because they boost speed and flexibility in app development and delivery, and are ideal for microservices. In fact, by 2020 more than 50% of organizations will run containerized applications in production, up from under 20% in 2017, according to Gartner. Thus, security teams must prioritize protecting the applications that DevOps teams create with this OS virtualization method.
“We see container security as a significant new paradigm coming at us, which will bring a lot of change,” Qualys CEO Philippe Courtot said.

But to ensure the security and compliance of container-based code, organizations can’t rely on conventional application security products. “Your existing tools aren’t going to work,” said Asif Awan, Qualys’ Container Security CTO. Unsurprisingly, organizations cite security as the biggest challenge when deploying containers, according to Forrester.
“Security automation is a simple term but to get a handle over that entire automated and ever-accelerating CI/CD (continuous integration and delivery) pipeline is becoming more and more difficult,” Awan said.
Responding to this need, Qualys offers a comprehensive security solution that monitors and protects containerized applications from the inside. In order to do that, Qualys technology collects granular behavior data about the application, providing deep visibility and enforcing normal application behavior for runtime protection.
Read on to learn about Qualys’ container security approach.
The allure of containers
“Everybody loves containers,” Awan said.
Because they package an application and its dependencies without a guest OS, containers offer advantages over VMs. Applications can be developed more quickly, are more lightweight and portable, and can be spun up and down faster.
They also run consistently regardless of the underlying computing infrastructure, making them highly portable. In addition, because they’re much slimmer, many more containers than VMs can be packed into a host, saving computing resource costs.
Securing containers
Container security challenges are primarily related to a lack of visibility, monitoring capabilities and control over their deployments. For example, container developers often use un-validated, buggy software components from public repositories, and deploy containers with weak configurations, resulting in applications that are highly vulnerable to hacker exploits.
Containers also communicate with each other via exposed network ports, bypassing host controls, and they’re hard to track because they’re so ephemeral, making them difficult to monitor. Furthermore, organizations have delegated even more container tasks to providers of increasingly popular container-as-a-service (CaaS) and orchestration-as-a-service offerings.
The Qualys approach
“Qualys provides a comprehensive solution for visibility and control for the entire lifecycle of containerized apps,” Awan said.
The Qualys container security solution gives security teams continuous discovery, tracking, and protection of containers in DevOps pipelines and deployments at any scale.
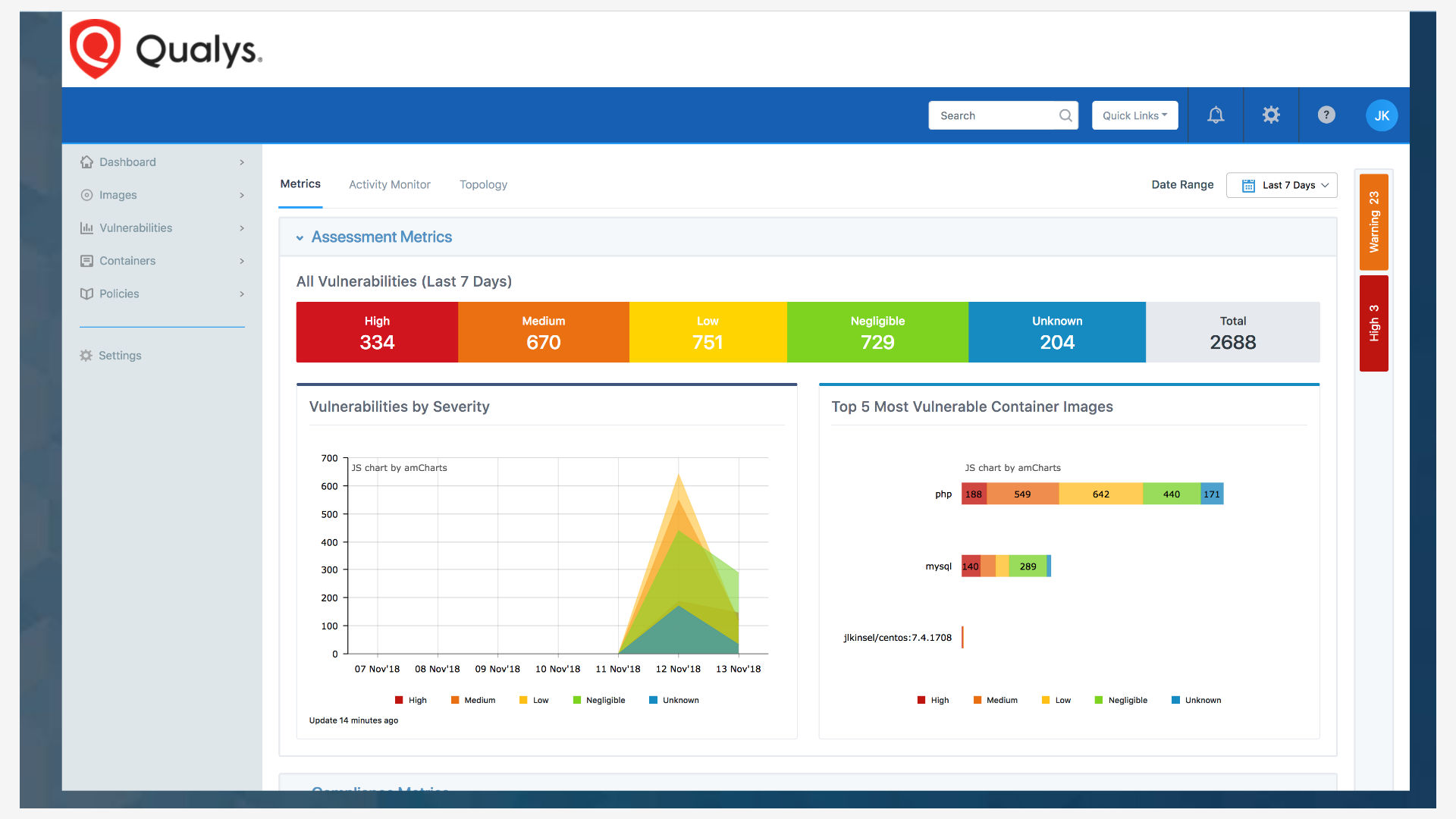
Awan explained that the traditional application security approach has been to either install an agent on the host, or monitor network traffic. Qualys believes the best way to protect a containerized application is from inside. “We layer in visibility and security in each application,” he said.
Qualys does this by replicating container images and embedding its security logic in them. That way, customers get very specific data about the application. “Anything that an app does, all of those activities, are captured and we automatically create a behavior profile,” he said.
That profile gets converted into detailed security policies which are enforced at the individual container level. That way, security teams can detect containers that drift from their normal behavior.
Qualys’ policy-based orchestration also stops vulnerable container images from being spun-up in Kubernetes clusters. In this way, Qualys’ solution enables teams to zero-in on host-level or container-level vulnerability and patch compliance.
The result: Deep visibility and runtime application protection for containerized and serverless “container as a service” workloads like AWS Fargate and Azure Container Instances. This is the right way to monitor and secure applications because the infrastructure stack changes constantly and is managed through offerings like AWS Fargate/Lambda and Azure Container Instances/Cloud Functions.
This approach is also inherently more secure than those based on privileged and elevated system capabilities, which give the privileged security containers access and control over all other containers, according to Awan. As was seen with the recently patched Kubernetes flaw (CVE-2018-1002105), it’s likely that similar vulnerabilities and threats will emerge, because adding root privileges to the layer that’s exposed to the external, hostile environment makes that layer a target for malicious activity.
By embedding visibility and security within the container itself, Qualys can monitor and control all container network, storage, and application calls from within each container. It also retains the portability and agility of containers by automatically moving and scaling with them.
In short, with Qualys’ solution, organizations can protect all phases of container deployment — the build, ship, and runtime stages, he said.
Build
In this phase, the main goal is keeping unsafe, vulnerable images out of your container repository. DevSecOps teams can perform vulnerability analysis right from their CI/CD tools after they’ve been integrated via REST APIs or via custom plug-ins with Qualys. Developers get automatically notified if the image fails, and can access detailed, actionable vulnerability information for fixing the issue.
Qualys also provides visibility into container images’ software composition, to know, for example, if open source packages are used, and how these packages licensed, Awan said.
Ship
In this phase, organizations should monitor for vulnerabilities and misconfigurations of the images already in their registries. Qualys inventories and scans images in on-premises registries and cloud-based registries.
Organizations can also schedule automated daily scans to detect newly-disclosed vulnerabilities and to check the new images being added to the repositories. That way, organizations can make sure they are enforcing compliance with internal and external standards and policies.
Runtime
When containers are deployed in production, it’s critical to have visibility and continuous monitoring of runtime environments, and to respond to breaches. With Qualys, organizations can detect vulnerable containers, identify where they are, and assess their potential impact based on how widespread they are in the environment.
Qualys also lets security teams validate images against security policies, and block unapproved images from being spun up as containers through integration with orchestrators to enforce compliance.
And finally, Qualys provides deep application-level visibility into all the container activites and enforces the normal behavior at an individual container level for application protection.
For more information about Qualys’ container security solution, please watch the video of Awan’s QSC talk, which includes more details, and a live demo.