Secure ElasticSearch, Kafka & Other Microservices with Qualys Cloud Platform
In this era of Digital Transformation, microservices are rapidly gaining popularity within continuously deployed systems. Organizations have moved away from the rigid monolithic architectures to more flexible ones that are based on microservices. Lots of organizations handling large amounts of real-time data use microservices such as Kafka and ElasticSearch, mainly due to the operational simplicity and speed of performance that they provide. However, this substantially increases the attack surface because of the exposed APIs and open ports.
In a recent security incident, more than 5 billion records were “inadvertently” left exposed over an unprotected ElasticSearch instance. Hackers used tools designed to detect vulnerable misconfigurations within IT assets like ElasticSearch to discover the instance, according to security researcher Bob Diachenko. The exposed data was well structured and included names, email addresses, phone numbers, LinkedIn, and Facebook profile information. This opened the individuals listed in the database to huge phishing attack risks. In early 2019, security researcher Justin Paine revealed that Honda Motor Company exposed an unsecured ElasticSearch database. It held more than 100 million documents that amounted to about 40GB of data. The information could have provided attackers with a map leading them to the company’s security “soft spots,” leaving it absolutely vulnerable.
Qualys Cloud Platform enables you to detect instances of ElasticSearch and Kafka in your asset inventory, giving you the ability to report on vulnerabilities. This capability reduces the risk of malicious intruders being able to gain access into your network through any underlying security loopholes in these microservices.
Qualys Platform Enables Auto-Discovery of Microservice Components
Organizations often have multiple small teams working within silos. Frequently, organizations and their security teams struggle to find out if microservices are being used by any of their engineering teams. When microservices are in use, it is challenging to identify where exactly they are.
Qualys Policy Compliance (PC) offers an auto-discovery mechanism based on the existing OS-based scans, giving you essential visibility so you can control and protect your applications and overall environment. You can run an authenticated scan and gain visibility into all the systems that are currently using ElasticSearch or Kafka, even if you do not specify an auth record for the host. The scan reports, complete with granular details such as the microservices’ version, file paths etc., ensure that you are aware of where and how microservices are being used in your environment.
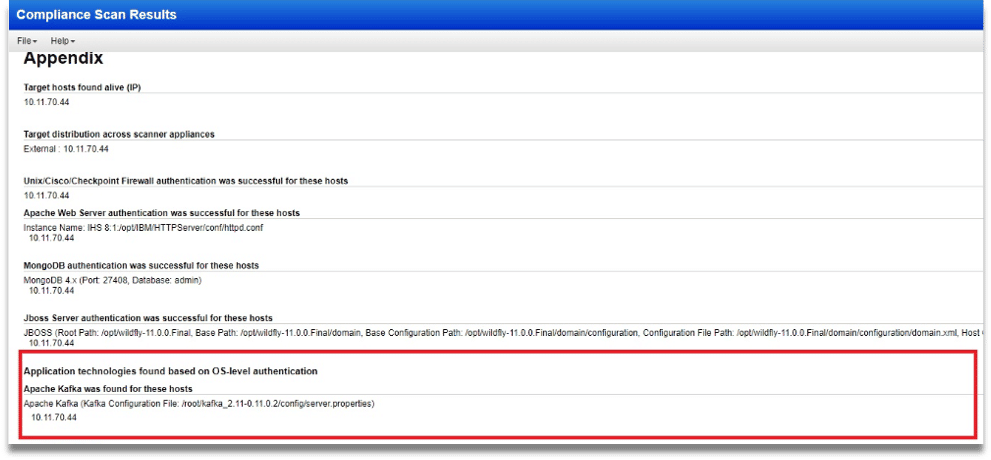
Figure 1: Apache Kafka instance discovery
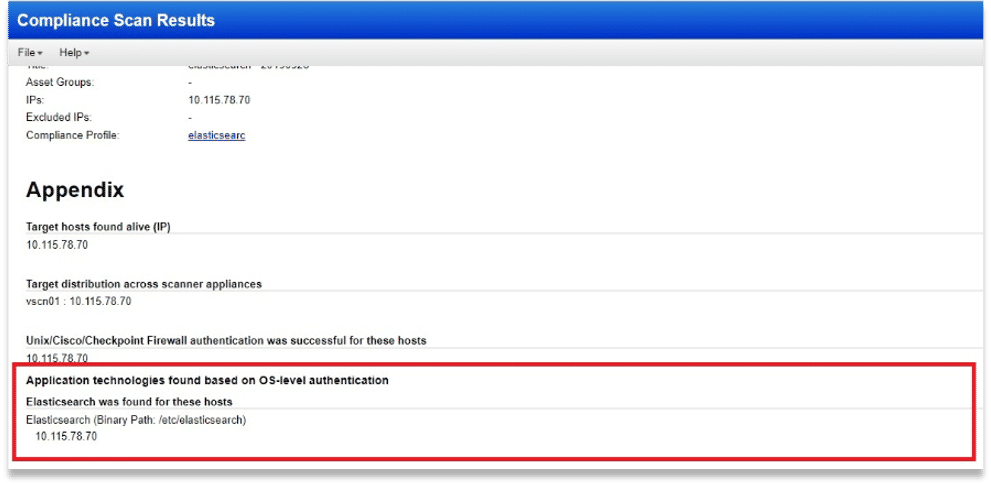
Figure 2: ElasticSearch instance discovery
Detect Misconfigurations Before It’s Too Late
It’s never an option for organizations to overlook the basic security recommendations and configurations. Vulnerabilities are mostly centered around a few configuration-based security problems. Due to the increased complexity of microservices architectures, it is critical that you perform in-depth health checks that include misconfiguration detection.
Qualys PC helps you negate such loopholes and obtain a clearer picture, which is supported by robust data. Qualys PC’s control library contains policies and controls that are specifically created for ElasticSearch and Kafka. You can import these policies and scan your hosts for misconfigurations and take necessary action to mitigate risks.
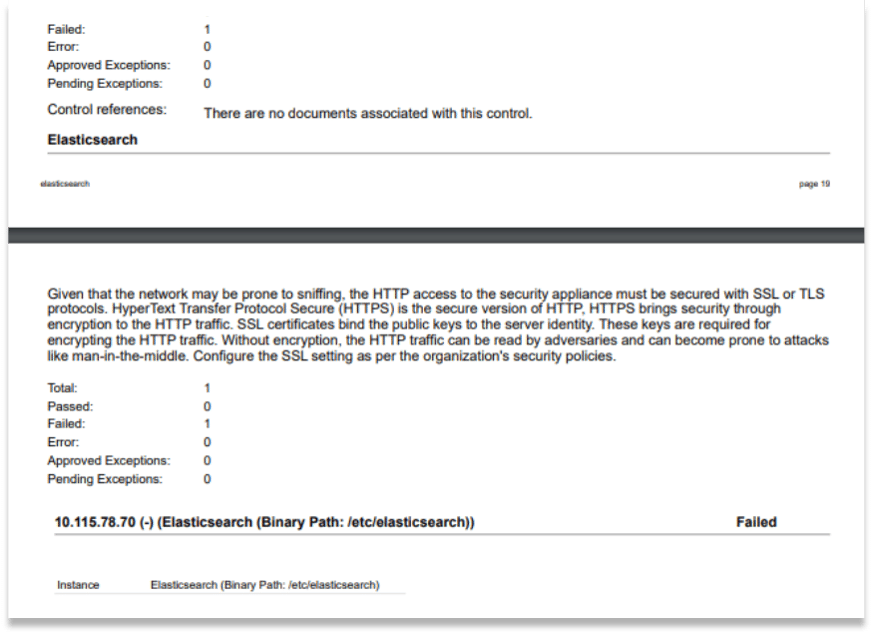
Figure 3 Detection of misconfigurations
Ensure Accurate and Precise Detection
Passive forms of monitoring such as CVE-based vulnerability scanning and gathering data are not sufficient for an environment that uses microservices. More often than not, CVE-based vulnerability assessments provide false assurance that everything is secure with the microservices in use.
Qualys Vulnerability Management (VM) includes QIDs specifically created to detect vulnerabilities in ElasticSearch and Kafka; Qualys PC contains policies with more than 40 controls for Kafka and ElasticSearch. The Qualys controls and compliance checks are capable of pointing vulnerabilities as well as potential weaknesses in the microservices with absolute precision.
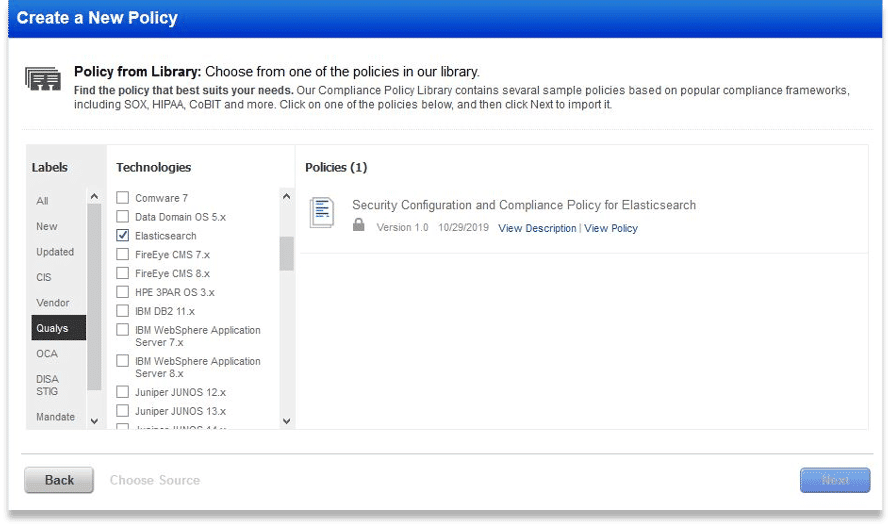
Figure 4 ElasticSearch Policy
Single-Pane-of-Glass View
It’s just as important to collect relevant data as it is to analyze the data that’s collected, which is how you gain a precise understanding of your organization’s security posture. You can leverage the power of the Qualys Dashboard to have a single-pane-of-glass view of your organization’s security posture with regards to ElasticSearch and Kafka.
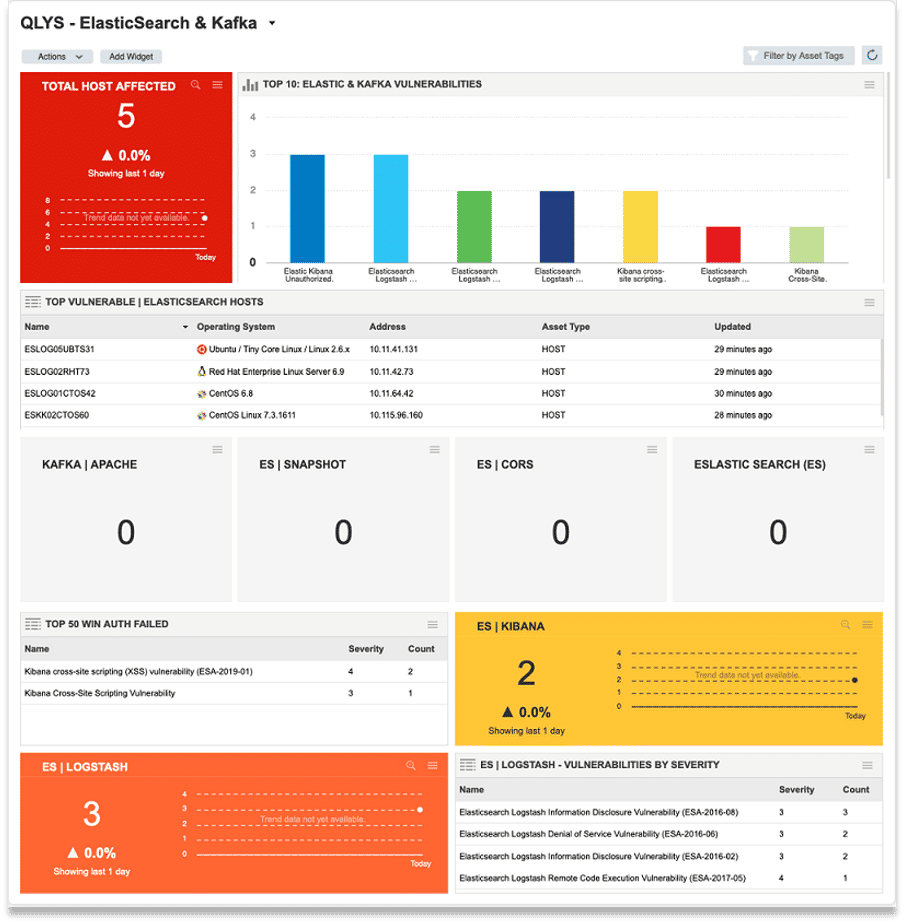
Figure 5 Dashboard for ElasticSearch and Kafka vulnerabilities
The dashboard includes graphical details for the top 10 ElasticSearch and Kafka vulnerabilities, and the 10 vulnerable assets that use ElasticSearch and Kafka microservices etc. The details included in the dashboard give you a single-glance perspective of your organization’s security, configuration and compliance status vis-à-vis emerging technologies and microservices such as ElasticSearch and Kafka. With the detailed, actionable information presented through the dashboards, business decisions can be quick, accurate, and effective.
Conclusion
Qualys Cloud Platform has efficiently helped customers strengthen their environments against vulnerabilities that are induced through microservices, and enabled them to take proactive measures to strengthen security. Built with the combination of a robust platform, intelligent architecture, and support of the extensive policies and controls, Qualys ensures that your network is fortified to be able to detect vulnerabilities and to fix them without delay.
To get started with Qualys, sign up for a free trial.