Secure Remote Endpoints from Vulnerabilities in Video Conferencing & Productivity Applications like Zoom
With millions working, learning and collaborating remotely due to COVID-19 challenges, there’s an explosion of remote endpoints running Zoom and other collaboration and productivity applications such as Outlook, Teams, Webex, Slack, Office 365 and more. As remote endpoints are accessing organizations’ critical assets and data, more and more cyberattacks are targeting remote endpoints for exploiting weaknesses and vulnerabilities in collaboration tools like Zoom.
Details on Zoom Vulnerabilities
Recently published zero-day vulnerabilities on Zoom clients put all such remote endpoints at risk. Zoom has been very quick to respond to these security & privacy issues by providing the patches for Windows and Mac OS. Zoom is the most talked about tool and has gained a lot of attention due to this vulnerability; however, these vulnerabilities could be very well present in other collaboration and productivity applications as well, putting organizations’ critical assets at risk.
Several security vulnerabilities were reported on Zoom as below:
- Zoom leaking data to Facebook – Zoom confirmed that the Facebook SDK for iOS client feature has been removed and is reconfigured for users to log in with Facebook via their browser.
- Zoom meeting not end-to-end encrypted – As per this Zoom blog post, Zoom has implemented robust and validated internal controls to prevent unauthorized access to any content that users share during meetings, including – but not limited to – the video, audio, and chat content of those meetings.
Zoom responded quickly on security issues and provided remediation patches for multiple security vulnerabilities:
- A UNC Path Injection vulnerability: There is a UNC path injection vulnerability that exists in multiple softwares like Zoom, Outlook, and others. A remote attacker could exploit this vulnerability by transmitting malicious links, allowing attackers to steal the credentials of users who click on the link. When sending a chat message, any URLs that are sent are converted into hyperlinks so that other members can click on them to open a web page in their default browser. If a user clicks on a UNC path link, Windows will attempt to connect to the remote site using the SMB file-sharing protocol to open the remote file or whatever has been shared as links over chat in meetings. When doing this, by default Windows will send the user’s login name and their NTLM password hash, which can be cracked using free tools like Hashcat to de-hash or reveal the user’s password.
- A Privilege Escalation vulnerability: This vulnerability exists in pre-installation scripts bundled with the Zoom client that could make unauthorized use of the “AuthorizationExecuteWithPrivileges” API to perform various privileged installation tasks.
- A Code Injection vulnerability: This allows an attacker to record Zoom meetings or access the mic and camera at arbitrary times, bypassing the Hardened Runtime security feature.
Stay on top of security and vulnerability challenges posed by Zoom and other applications with Qualys Remote Endpoint Protection service
Qualys is offering its ‘remote endpoint protection’ service based on the multi-function Qualys Cloud Agent, which instantly provides visibility into remote endpoints with Zoom and other collaboration / productivity applications, detects vulnerabilities, manages their security hygiene proactively, and patches them quickly at no cost. This service is free for 60 days.
Qualys Remote Endpoint Protection offering enables:
#1 Automatic real-time inventory of all remote endpoints with Zoom and other collaboration applications installed on them
With a simple query shown below, you can easily discover and track hosts with the Zoom application installed on them, with meta-data such as users, processes, ports, and geographical locations. Further, you can automatically group existing hosts which have Zoom installed on them, as well as any new hosts that spin up in environment with zoom on them. Tagging makes these grouped remote hosts available for querying, reporting and management throughout the Qualys Cloud Platform.
software: (publisher: ‘Zoom’)
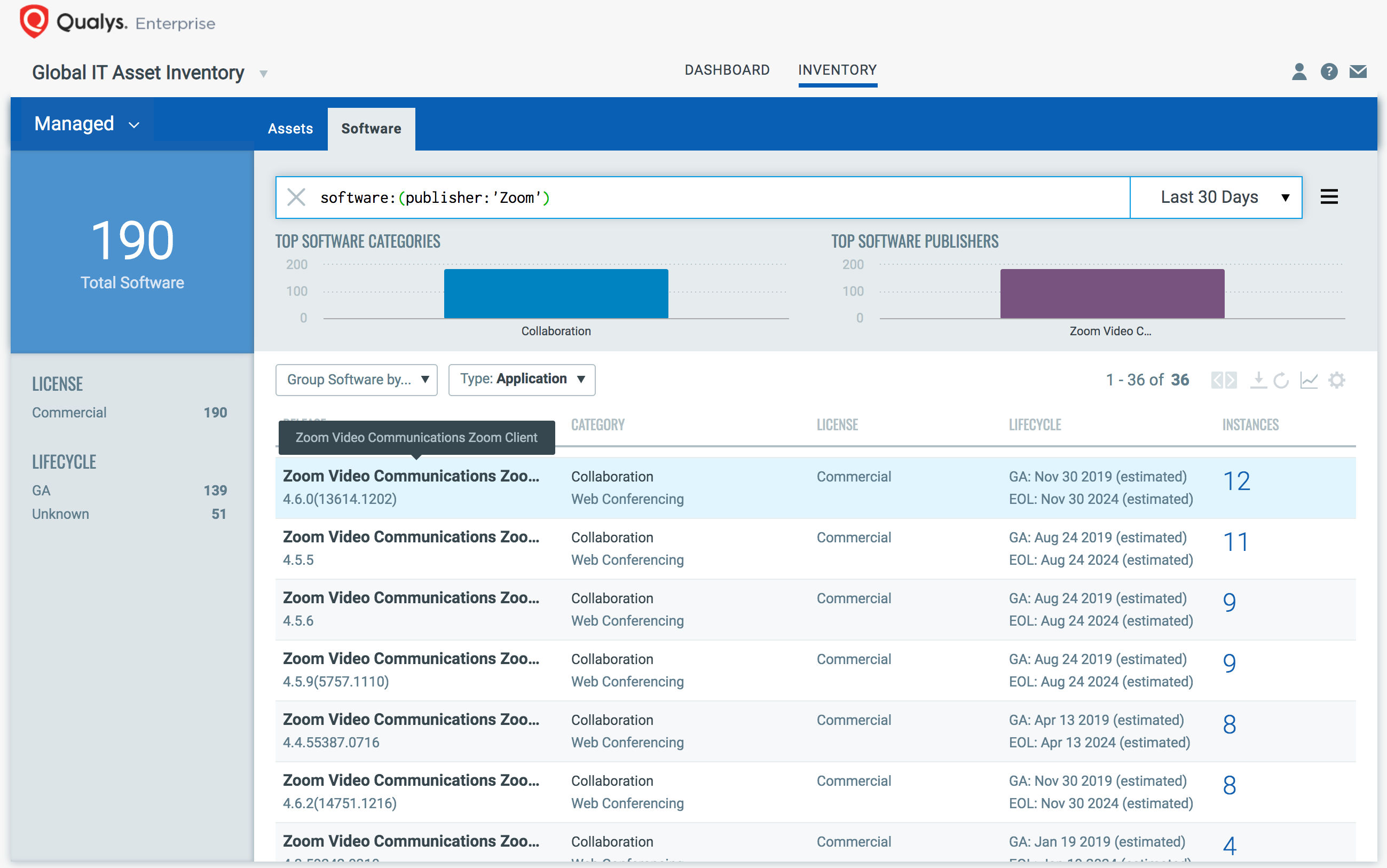
Additionally, you can also discover and track remote hosts with other collaboration and productivity tools installed on them, such as Outlook, Slack, Webex, Teams, Bluejeans and more.
software:(category1:`Collaboration`)
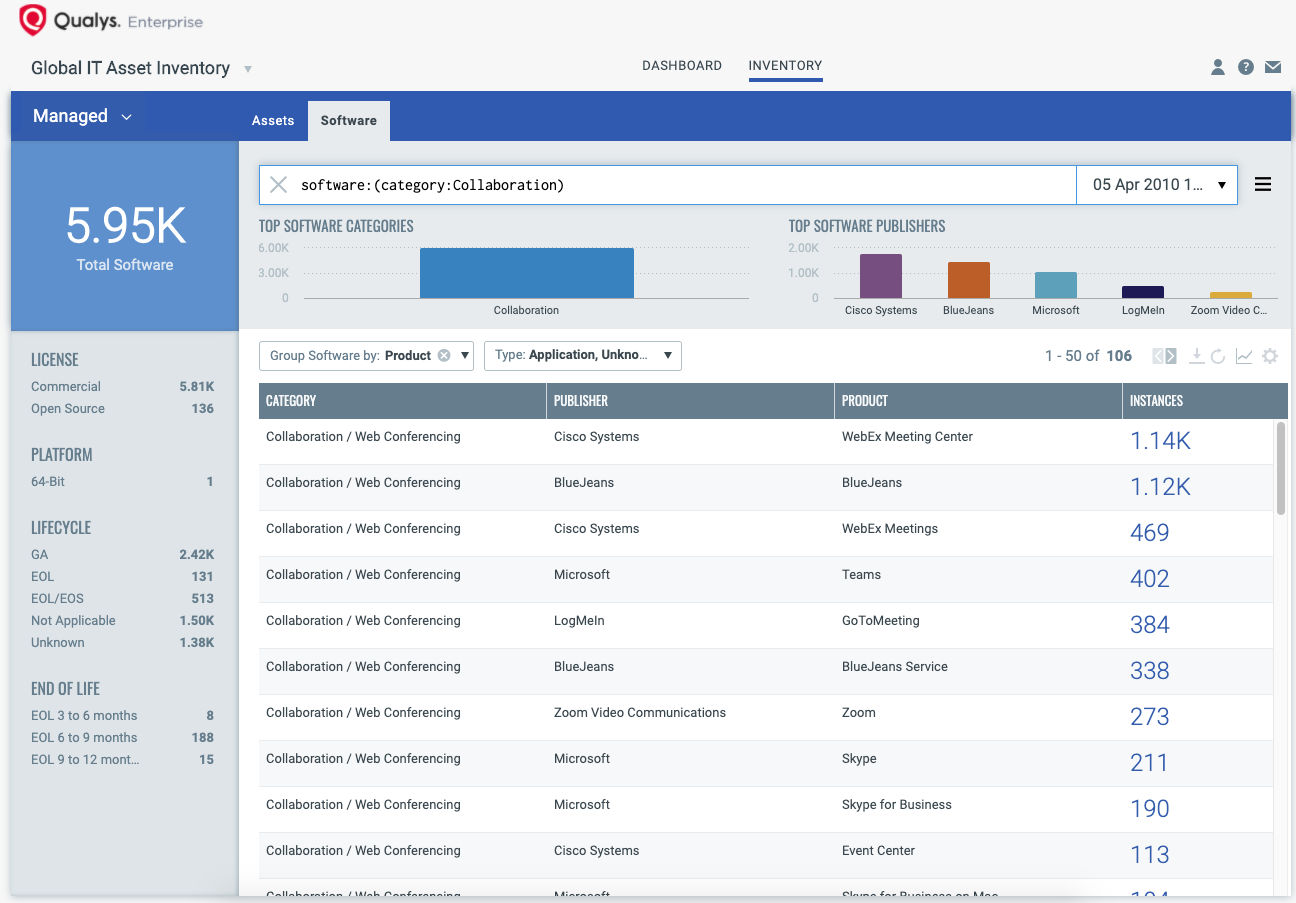
Once the hosts are identified, group them together with a ‘dynamic tag’, let’s say – “CollaborationTools”.
#2 Gain a real-time view of all vulnerabilities in collaboration and productivity applications posing a risk to remote devices and your organization’s data
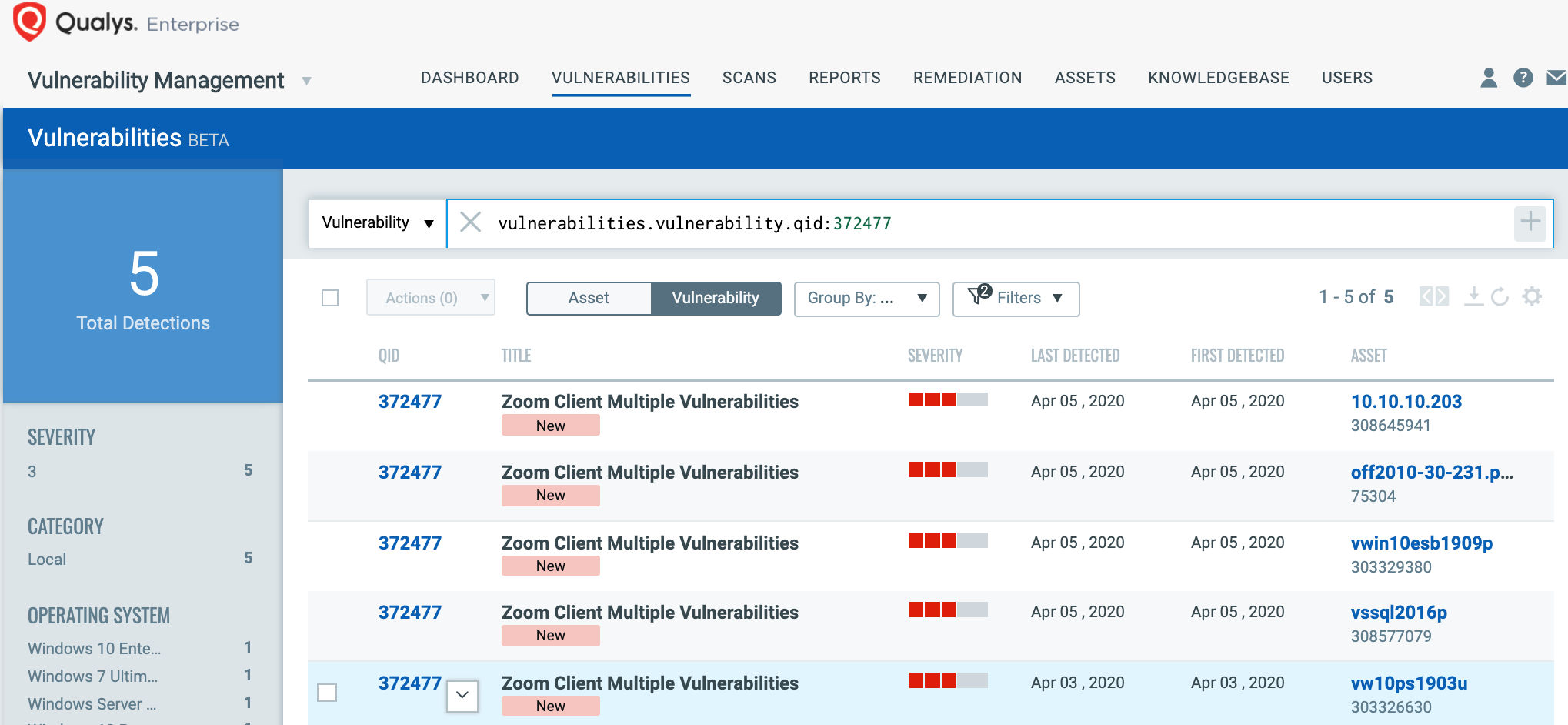
You can see all your impacted remote hosts tagged with the “CollaborationTools” asset tag for Zoom vulnerabilities with a simple query:
vulnerabilities.vulnerability.qid: 372477
Customers with Qualys Threat Protection can stay on top of these threats proactively via the ‘live feed’ provided for threat prioritization. With ‘live feed’ updated for all emerging high and medium risks, you can clearly see the impacted hosts against threats.
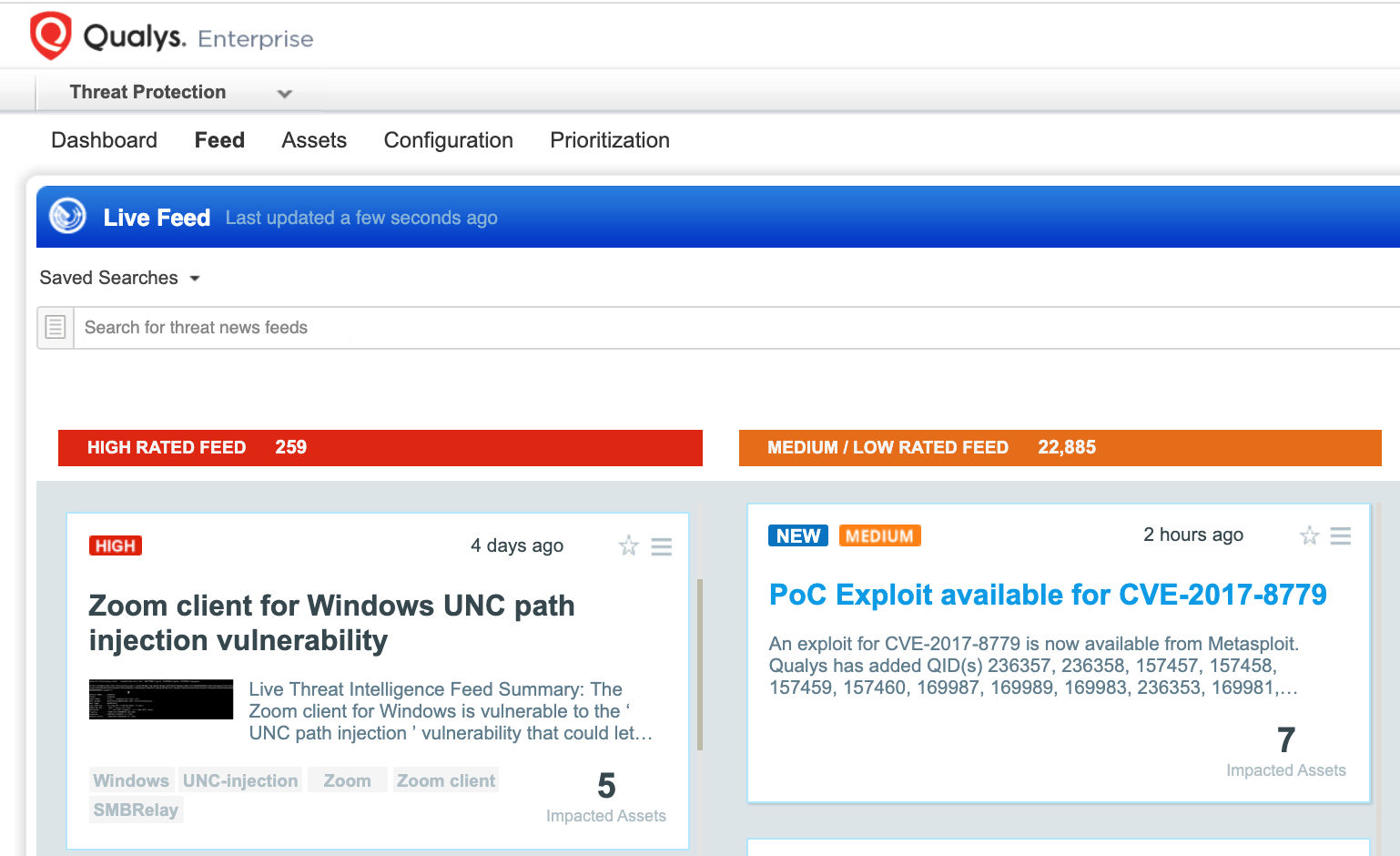
Simply click on the impacted assets for the zoom threat feed to see the vulnerability and impacted host details.
Having a complete view of all vulnerabilities in collaboration and productivity applications, across your remote endpoints is critical for prioritizing your patching efforts to ensure your users and IT environment are safe. With trending enabled for dashboard widgets, you can keep track of zoom vulnerability trends in your environment by importing pre-configured Zoom Vulnerabilities Dashboard :
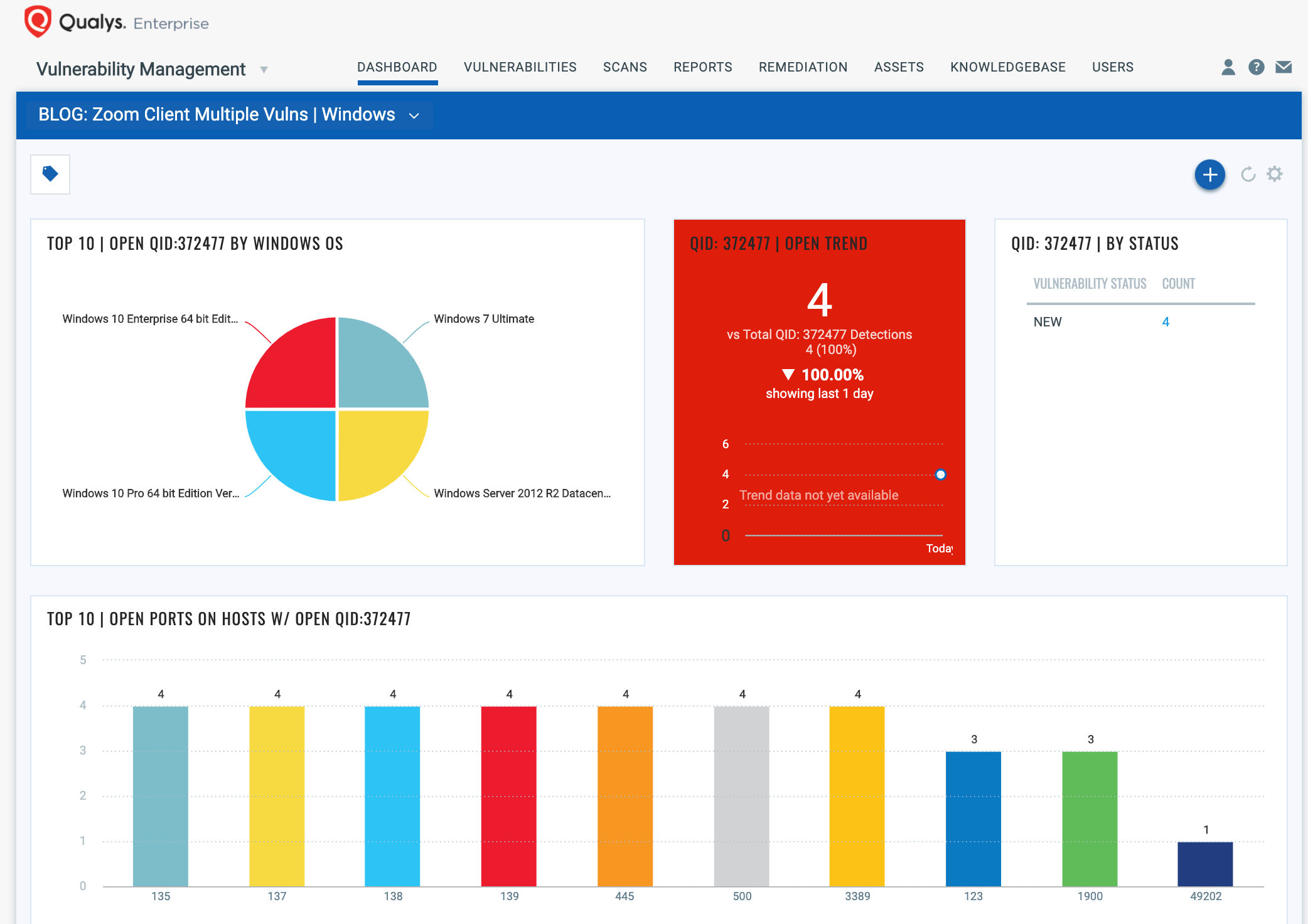
#3 Patch these remote endpoint systems with vulnerable Zoom applications within hours by deploying patches directly from the vendor’s website
Qualys Remote Endpoint Protection service through Qualys Patch Management lets you:
- Automatically correlate Windows hosts by simply selecting “Product: zoom” in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches, by directly downloading the patches from vendor’s website and CDNs, without overwhelming VPNs and limited bandwidth, unlike enterprise, on-premise solutions which would chock VPN and bandwidth by pushing patches through them.
- Create a proactive, daily job with a 24-hour “Patch Window” to ensure all remote hosts will continue to receive the required patches as new patches become available for the emerging vulnerabilities.
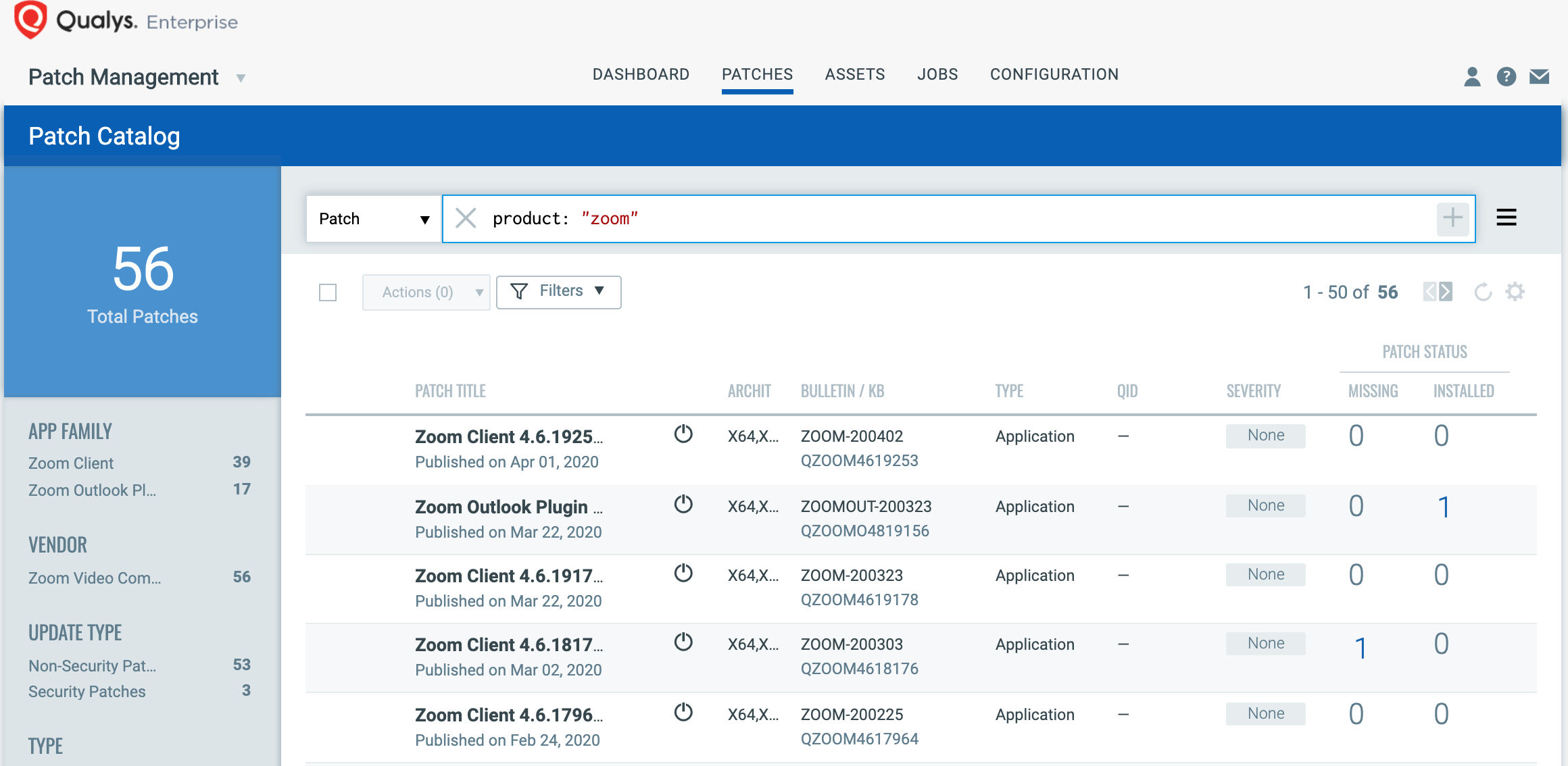
Users are encouraged to apply patches as soon as possible.
#4 Manage your security hygiene and configurations proactively so that new vulnerabilities don’t leave endpoints exposed to exploits
It is important to harden and manage these remote hosts for security hygiene so that you reduce the risk of new vulnerabilities coming up in these collaboration applications like Zoom and the endpoints are not left exposed to exploits.
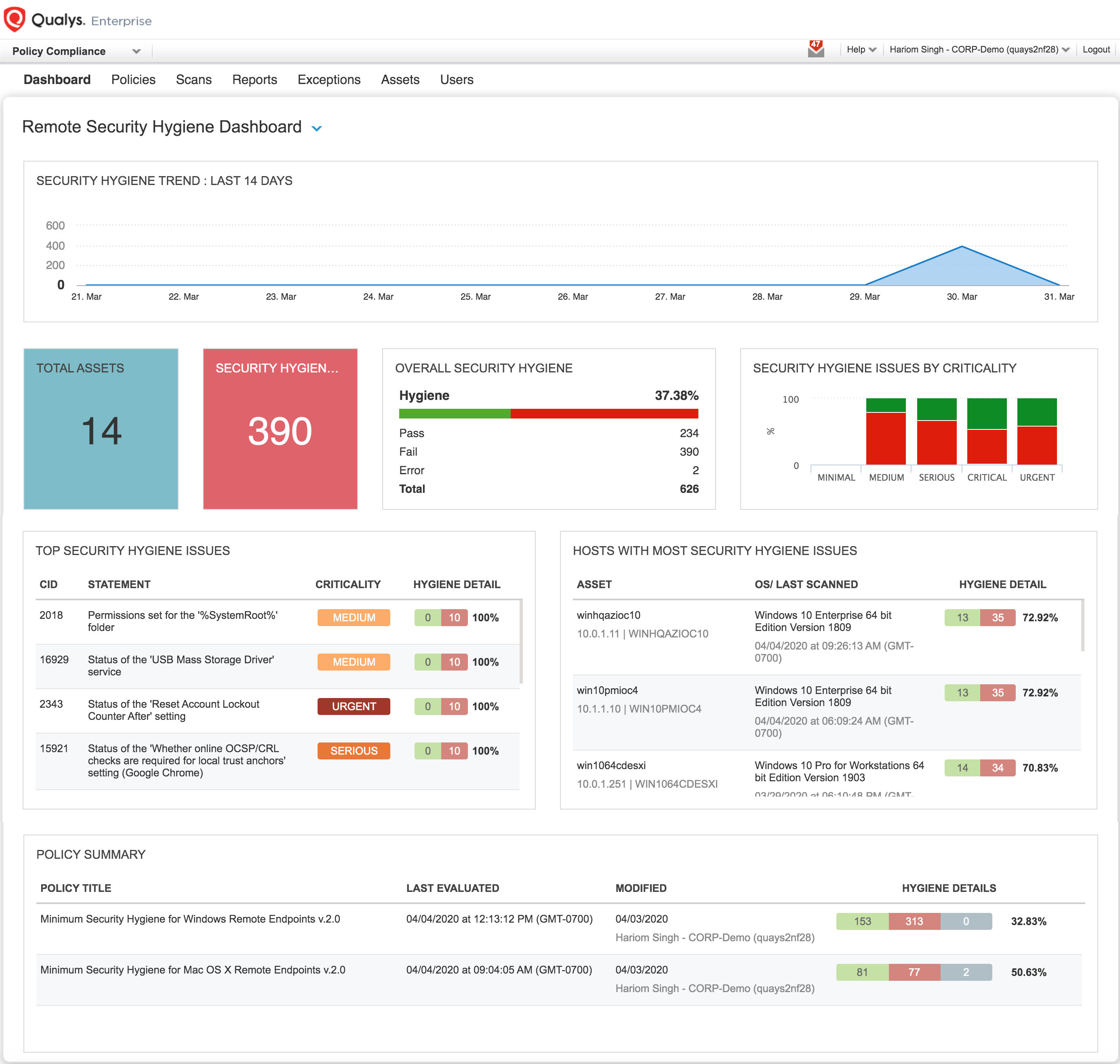
The security configuration assessment integrated in Remote Endpoint Protection service (also available if you are an existing Qualys Policy Compliance customer) enables monitoring for the below ‘compensating and risk mitigating controls’ for Windows and Mac OS to reduce the risk due to these vulnerabilities in the Zoom application and safeguard you better for future such vulnerabilities.
Qualys configuration ID – 8243 “Configure ‘Network Security:Restrict NTLM: Outgoing NTLM traffic to remote servers'” would be evaluated against all hosts on which Zoom application is installed as shown below –
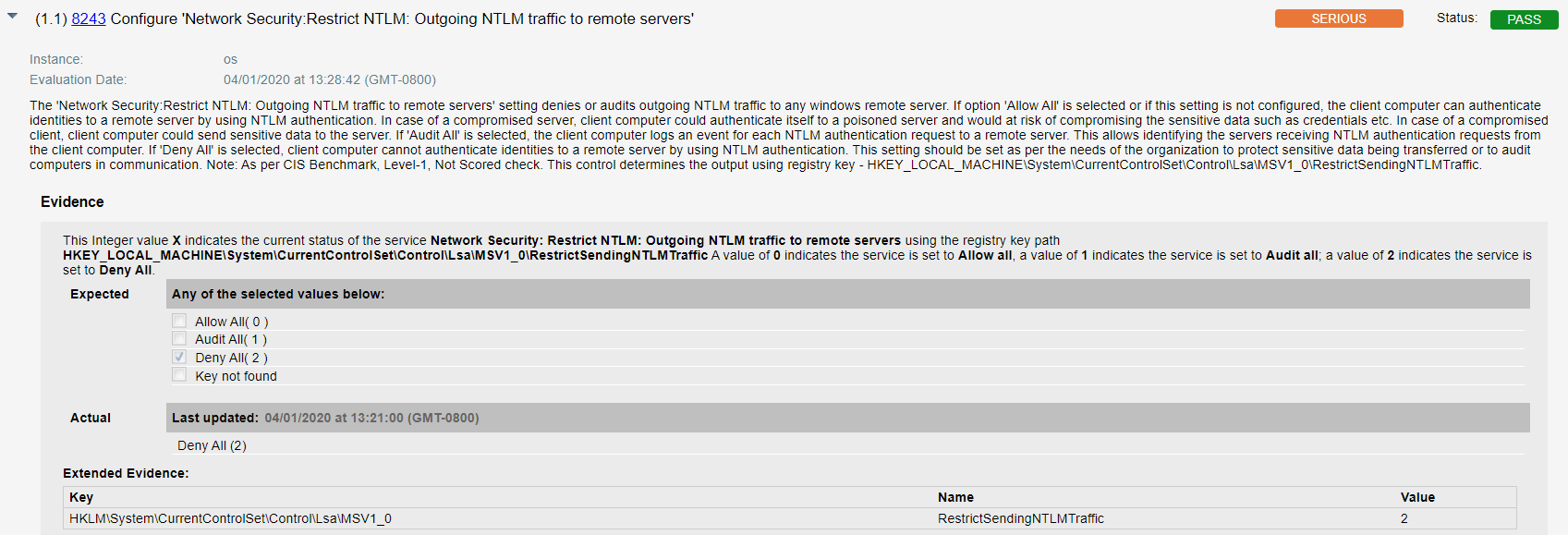
Having a complete view of all configuration in collaboration and productivity applications across your remote endpoints allows you to prioritize your patching efforts to ensure your users and IT environment are safe.
Summary
Securing your remote endpoints for security hygiene and vulnerabilities due to video conferencing and productivity tools will help you minimize business disruption and productivity downtime as well as reduce cyber exposure to data breaches and exploits, ensuring you get the maximum out of these collaboration applications during this remote work journey.
Get Started Now
Start your free 60-day trial of Qualys Remote Endpoint Protection for automatically identifying, detecting and patching critical remote endpoint misconfigurations and vulnerabilities. We hope this service helps you quickly get control over your remote endpoints.
Please reach out to your technical account manager (TAM) for any questions, comments or feedback or simply mail us at sales@qualys.com.
Additional Resources:
Video: How to enable and use Qualys Patch Management
Training: Patch Management video library
How Qualys Patch Management lets you automatically correlate vulnerabilities and patches, decreasing your remediation response time
Training: Cloud Agent video library
How you can leverage your existing vulnerability Qualys Cloud Agent for configuration management and remote patching
Learn how you can manage inventory of remote endpoints, vulnerabilities and security hygiene issues and patch them through –https://blog.qualys.com/technology/2020/03/24/secure-your-global-remote-workforce
About the Authors:
Shailesh Athalye, VP of Compliance Solutions, Qualys
Contributors:
Hariom Singh, Director of Product Management, Compliance Solutions, Qualys
Animesh Jain, Product Manager, Vulnerability Signatures, Qualys