Let Smart Automation Reduce the Risk of Zero-Day Attacks on Third-Party Applications
Last week, Google released yet another zero-day patch for its Chrome browser to fix a high-severity flaw that was already being exploited. That vulnerability (CVE-2022-3075) is the sixth actively exploited zero-day found in Chrome this year. While users are grateful for the urgent patch, it was released just before the Labor Day weekend when many IT and Cybersecurity staffers were on vacation and unable to respond to the vulnerability in a timely manner.
This event highlights the importance of responding quickly to the ever-growing volume of vulnerabilities introduced to your organization’s network as a result of third-party applications installed by either IT or end users. Browsers are the most common application by far, but many others such as iTunes, VLC Media Player, and other “user-oriented” applications are also frequently installed. When put into perspective, the total risk presented by third-party applications often exceeds the risk coming from native Windows operating systems.
Here’s the bottom line: Many organizations are severely challenged to respond quickly to these unexpected high-severity surprises. Why? They’re too busy simultaneously managing other mission-critical tasks and processes across their IT and Cybersecurity teams.
The solution for many organizations is the use of “Smart Automation.”
How Smart Automation Reduces Zero-Day Risks
Smart Automation entails a risk-focused approach to remediation; it is not patch focused. Using risk as a guide entails analyzing a customer’s environment for cybersecurity risk, and then recommending efficient automation jobs that will automatically remediate devices to address current and future risk. The use of a risk-based approach must include assessment of operational risks that could be affected by automated remediation. For example, automatically patching medical devices as soon as a new zero-day threat is disclosed may be great for cybersecurity; but could put patient health in danger if the patch breaks the device’s proper operation.
To help IT and Cybersecurity teams prepare for Smart Automation, we recommend starting with this four-point framework:
- Map your vulnerabilities. Map your environment for the different types of vulnerable assets you have and the teams that manage them. For example, most organizations will have a team that manages end user workstations, another team that manages servers, and multiple line-of-business owners that manage the different servers running production applications.
- Focus on risk. By definition, the more vulnerabilities you have, the greater risk your organization faces. Not to mention all the additional work for remediation. By leveraging automation and focusing on the products that are generating the largest number of vulnerabilities, you can get ahead of the problem and mitigate this increased risk.
- Understand operational risk. Work with the teams responsible for your various production environments to analyze any potential operational risks posed by deploying patches to those products.
- Adopt Smart Automation. Leverage automation with devices that introduce the most risk, and at the same time have minimal operational impact. The essence of Smart Automation is combining points #2 and #3.
Using Qualys and Zero-Touch Patching to Reduce Risk
As part of Qualys Patch Management (PM), Zero-Touch Patching intelligently identifies the riskiest products in your environment. It helps create automation jobs to automatically deploy the proper patches and configuration changes required for remediating vulnerabilities. It also leverages Qualys Vulnerability Management, Detection, and Response (VMDR) to prioritize work based on real-time threat indicators.
Google’s zero-day patch for the Chrome browser presents a good example of how Qualys helps address this four-point framework. Customers running Qualys PM tell us that Chrome is by far the riskiest application – even more than Windows OS. In consulting their IT/end user computing teams, many organizations have concluded that patching Chrome automatically on all workstations is low-hanging fruit, an easy win.
Using Zero-Touch Patching to ensure that Chrome is always up-to-date will minimize the top cybersecurity risk to workstations, while keeping operational risks extremely low. Many Qualys PM customers say workstation teams have never seen a Chrome patch break a business process. By leveraging Zero-Touch Patch jobs, new Chrome zero-day threats do not require any extra work from the IT team since automation will take care of it.
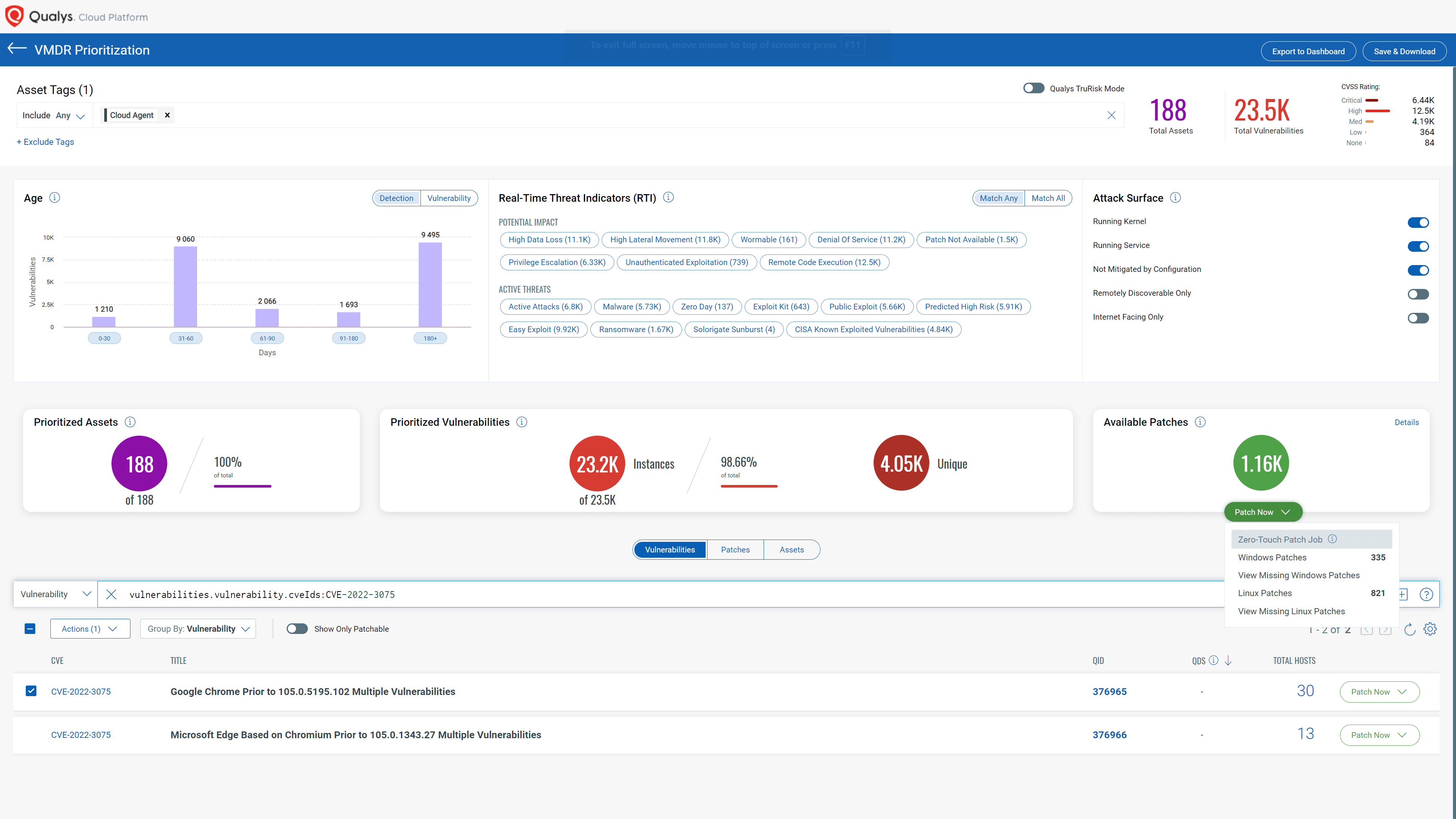
Leveraging the “Auto Update” Feature for Chrome and Other Third-Party Applications
Some third-party applications including Chrome provide the ability to self-update automatically. This is a welcome feature, so Qualys encourages IT and Cybersecurity teams to have this enabled throughout the enterprise. However, enabling auto-update alone does not ensure that any given software update was successful while tracking the result status is often difficult.
Qualys recommends that organizations use Zero-Touch Patching side-by-side with the auto-update feature to ensure that patches are always deployed. Our solution also allows teams to monitor successful completion of their recently executed jobs.
If you haven’t had a chance to try Qualys Patch Management, we encourage you to see for yourself how easy it is to get the benefits of Zero-Touch Patching. Sign up for a free trial. Qualys Patch Management automatically integrates with all other Qualys cloud services you may already be using.