Evaluate Your Windows Endpoints for Storm-0978 Activity With Qualys Endpoint Security
Summary:
On July 11, Microsoft released security bulletins to fix 132 vulnerabilities. With the July Patch Tuesday, Microsoft also remediated six zero-day vulnerabilities. For your quick reference, the following are the zero-day vulnerabilities:
- CVE-2023-32046 – Windows MSHTML Platform Elevation of Privilege Vulnerability
- CVE-2023-32049 – Windows SmartScreen Security Feature Bypass Vulnerability
- CVE-2023-36874 – Windows Error Reporting Service Elevation of Privilege Vulnerability
- CVE-2023-36884 – Office and Windows HTML Remote Code Execution Vulnerability
- CVE-2023-35311 – Microsoft Outlook Security Feature Bypass Vulnerability
- ADV230001 – Guidance on Microsoft Signed Drivers Being Used Maliciously
Of these, the Qualys Threat Research Unit (TRU) finds CVE-2023-36884 particularly interesting. Microsoft attributes this vulnerability to a threat actor named Storm-0978/RomCom. Additionally, due to the nature of these vulnerabilities, the chances that a threat actor will combine CVE-2023-32049, and CVE-2023-35311 with CVE-2023-36884 are high.
What is interesting about this threat actor, which can be — attributed to the Russian region — is that this group employs clever tactics to stay under the radar. It also uses ransomware-laced activities, which might help its real espionage goals remain undetected. More surprising is that no patches have been released for this vulnerability. Microsoft mentions that Microsoft Defender for Office 365 already protects systems by enabling the “Block all Office applications” as per the attack surface reduction rules on creating child processes.
Another interesting tidbit, which you will find in the vulnerability analysis section, is the close resemblance to an earlier released Follina vulnerability that affected the Microsoft Office suite of products.
Since there are no patches, let’s first see how to remediate this vulnerability.
Remediation:
It is recommended by Microsoft that the HKLM\SOFTWARE\Policies\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION registry key be set with Microsoft Office binaries such as Excel, and Winword. Based on documentation that dates to Internet Explorer 7, this is a security measure designed to prevent malicious sites from accessing system file objects.
This PowerShell script can help you make the required registry changes:
$registryPath = "HKLM:\SOFTWARE\Policies\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION" $applications = "Excel.exe", "Graph.exe", "MSAccess.exe", "MSPub.exe", "PowerPnt.exe", "Visio.exe","WinProj.exe", "WinWord.exe", "Wordpad.exe" if (Test-Path -Path $registryPath) { $existingKeys = Get-ItemProperty -Path $registryPath -Name $applications -ErrorAction SilentlyContinue | Where-Object { $_.PSObject.Properties.Value -eq 1 } foreach ($app in $applications) { if ($existingKeys -notcontains $app) { Set-ItemProperty -Path $registryPath -Name $app -Value 1 -Type DWord } } } else { New-Item -Path $registryPath -Force | Out-Null foreach ($app in $applications) { Set-ItemProperty -Path $registryPath -Name $app -Value 1 -Type dword } }
As a result, this means that the vulnerability exists in the Internet Explorer component that is used to render the web component. This opens a huge attack surface vulnerability in a subdued component currently being phased off. Based on preliminary TRU analysis, customers should also look at the following features:
- FEATURE_BLOCK_INPUT_PROMPTS
- FEATURE_BLOCK_LMZ_IMG
- FEATURE_BLOCK_LMZ_OBJECT
- FEATURE_BLOCK_LMZ_SCRIPT
- FEATURE_BLOCK_SETCAPTURE_XDOMAIN
- FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION
- FEATURE_HTTP_DISABLE_NTLM_PREAUTH_IF_ABORTED_KB902409
- FEATURE_CREATE_URL_MONIKER_DISABLE_LEGACY_COMPAT
- FEATURE_DISABLE_LEGACY_COMPRESSION
- FEATURE_DISABLE_MK_PROTOCOL
- FEATURE_DISABLE_NAVIGATION_SOUNDS
- FEATURE_DISABLE_TELNET_PROTOCOL
- FEATURE_DISABLE_UNICODE_HANDLE_CLOSING_CALLBACK
Qualys customers can use Qualys Custom Assessment and Remediation (CAR) to implement this fix at scale across all their endpoints.
Vulnerability Analysis:
Starting with a similar approach to the one that Qualys TRU followed while analyzing the Follina vulnerability, let’s look to statically analyzing the document type:
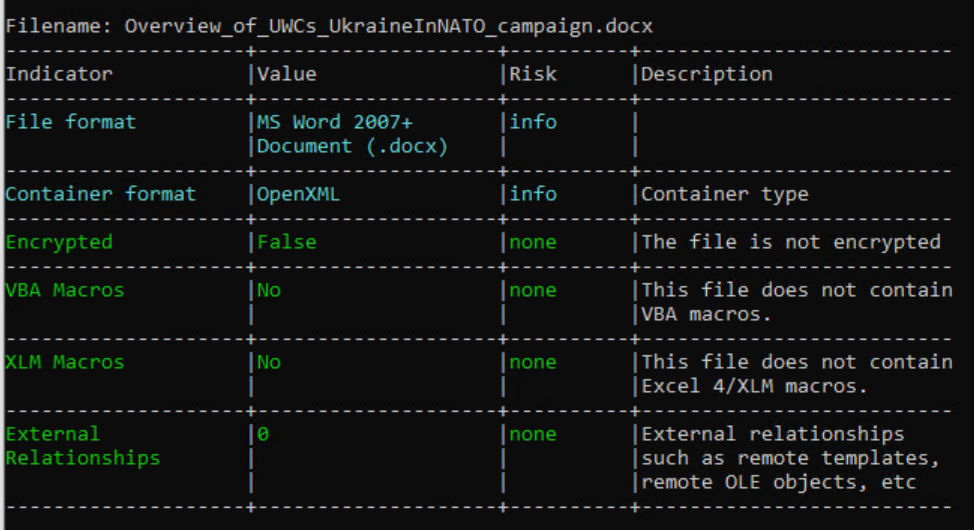
This is a .docx with OOXML, which contains no VBA or XLM macros. Now let’s move to understanding the relationships in the file:
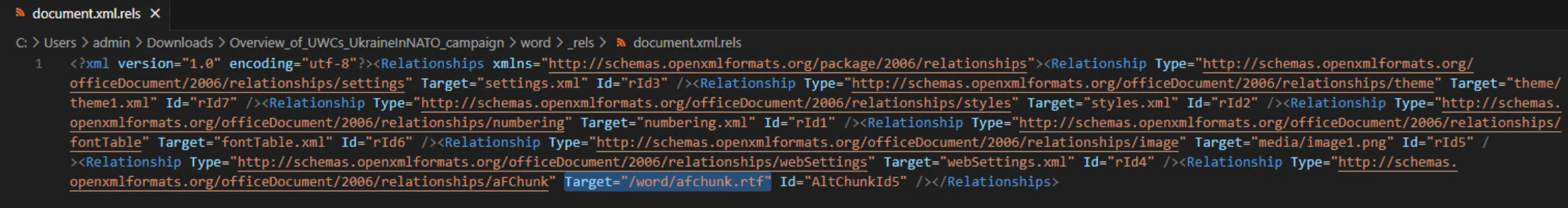
We see that an “afchunk.rtf” Rich Text Format (RTF) document is referenced as an AltChunk, which stands for Anchor for Imported External Content and has been created with OLE2LINK. By analyzing the RTF file with a tool such as rtfdump.py (thank you, @didierstevens!), we will get to see the following:
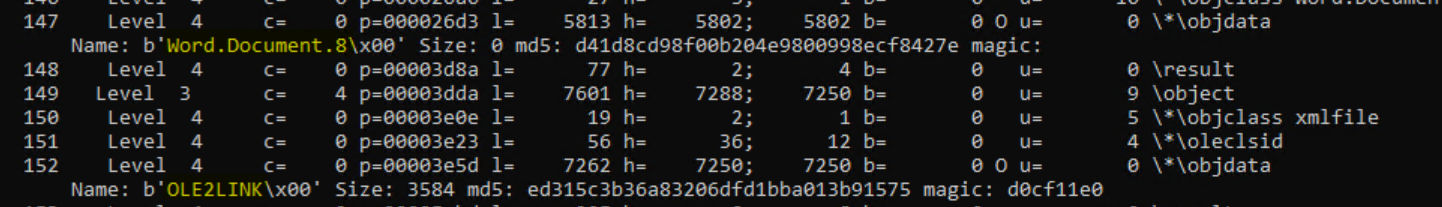
We also know that this RTF file is not well-formed:

This file further extracts an embedded .url file that downloads the malicious payload from the following location:
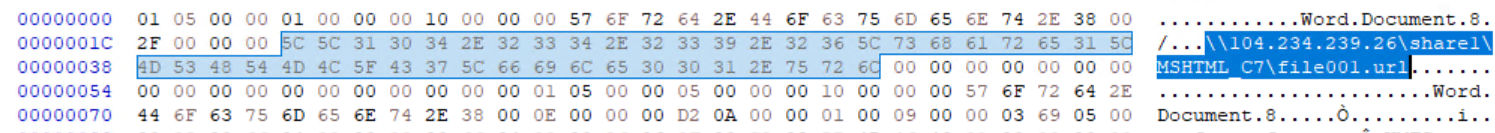
The host is down, but the IP/ASN is known to host TOR/VPN infrastructure. This ~24kb file size leads to another filetype analysis illustrating that this is, in fact, another Microsoft Word file:
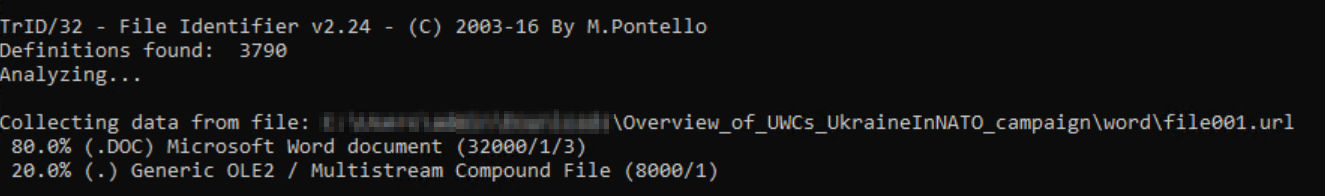
It also contains another file – start.xml.
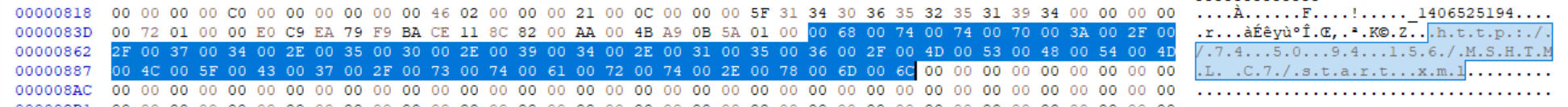
Based on reporting from other vendors, we have also observed additional IP addresses. You can find these IOCs at the end of this blog post. This document file is extracted and loaded after the original .docx file. Rest assured that as more information becomes available, we will update this blog.
Exploit Detection using Qualys EDR:
By leveraging the EPP solution bundled with Qualys EDR, customers will be presented with the following severity nine events.

Customers can also use the following QQL query to determine if there are any infections within their ecosystem:
file.hash.sha256:["07377209fe68a98e9bca310d9749daa4eb79558e9fc419cf0b02a9e37679038d", "1a7bb878c826fe0ca9a0677ed072ee9a57a228a09ee02b3c5bd00f54f354930f", "3a3138c5add59d2172ad33bc6761f2f82ba344f3d03a2269c623f22c1a35df97", "a61b2eafcf39715031357df6b01e85e0d1ea2e8ee1dfec241b114e18f7a1163f", "e7cfeb023c3160a7366f209a16a6f6ea5a0bc9a3ddc16c6cba758114dfe6b539"]

Based on network-related IOCs, customers can search using the following QQL query:
network.remote.address.ip:["74.50.94.156", "104.234.239.26", "94.232.40.34", "66.23.226.102"]
To detect child processes of Microsoft Office applications, customers can search using the following QQL query:
operatingsystem.fullname:"Windows" and type: PROCESS and action:`running` and process.parentname:["excel.exe", "msaccess.exe", "mspub.exe", "powerpnt.exe", "winword.exe"]
VMDR:
The Qualys Research Team has also released the following QID to help customers identify assets exposed to this vulnerability in their environment:
| QID | Title | VulnSigs Version |
|---|---|---|
| 92038 | Microsoft Office and Windows HTML Remote Code Execution Vulnerability (Zero Day) for July 2023 | VULNSIGS-2.5.811-3 |
Related IOCs:
| Artifact | SHA256 |
|---|---|
| File001.url | 07377209fe68a98e9bca310d9749daa4eb79558e9fc419cf0b02a9e37679038d |
| calc.exe | 1a7bb878c826fe0ca9a0677ed072ee9a57a228a09ee02b3c5bd00f54f354930f |
| Letter_NATO_Summit_Vilnius_2023_ENG.docx | 3a3138c5add59d2172ad33bc6761f2f82ba344f3d03a2269c623f22c1a35df97 |
| Overview_of_UWCs_UkraineInNATO_campaign.docx | a61b2eafcf39715031357df6b01e85e0d1ea2e8ee1dfec241b114e18f7a1163f |
| afchunk.rtf | e7cfeb023c3160a7366f209a16a6f6ea5a0bc9a3ddc16c6cba758114dfe6b539 |
| 104[.]234[.]239[.]26 | |
| 74[.]50[.]94[.]156 | |
| 94[.]232[.]40[.]34 | |
| 66[.]23[.]226[.]102 |
The file name is “Powerpnt.exe” not “PowerPoint.exe”
Thank you for pointing this out. The post has been updated with the correct spelling.