The MGM Cybersecurity Breach: Learnings and Prevention Measures
As many are aware, the systems of the $14 billion dollar gaming and hospitality giant MGM have been brought to a halt for nearly 5 days due to a multi-vector attack that has come to affect Caesars Entertainment as well.
While the culprits of the attack are not confirmed, hacking group Scattered Spider, who is also associated with UNC3944-related groups Scatter Swine, Oktapus, and Muddled Libra, has been suspected to be the attacker.
This attack is notable not only because of its scope but also due to its use of ransomware made by ALPHV or BlackCat (Ransomware-as-a-Service), suggesting that the UNC3944 threat cluster is likely here to stay and expand.
Since 2022, the UNC3944 threat cluster has always deployed social engineering and SMS phishing campaigns (smishing) to obtain credentials to gain access and expand within a victim’s network. However, in 2023, UNC3944 began to evolve to muster advanced ransomware attacks targeting an array of private sector companies – MGM just being the most infamous of late.

What Does This Tell Us?
The message is clear with the evolution of the UNC3944 threat cluster and the use of ALPHV or BlackCat (Ransomware-as-a-Service). Ransomware attacks are growing more lucrative and, therefore, common. Attacker tactics, techniques, and procedures (TTPs) will continue to expand in their scope and complexity.
Even the most advanced and well-funded attack cluster, as in the case of UNC3944, still relies heavily on old-fashioned, persistent phone-based social engineering bto begin their attack, highlighting the importance of cybersecurity training and rigorous zero-trust networking access (ZTNA) policies to reduce lateral movement after attackers gain entry into a victim’s infrastructure.
Common Attack Tactics, Techniques, and Procedures (TTPs)
In the case of the recent MGM and Caesar Entertainments attack, UNC3944 TTPs suggest an evolution to the organization’s capabilities, building off of social engineering tactics and shifting into high tempo targeting using smishing of credentials, use of phishing kits, and publicly available credential theft.
While specific details of the attack may not be publicly disclosed due to ongoing investigations, it’s crucial to understand the broader security lessons drawn from such an incident. Here are a few logical attack methods deployed that may have affected MGM that every security stakeholder should be aware of and continuously test their security stack against.
- Phishing: APTs often begin with social engineering attacks, such as spear-phishing emails that trick employees into revealing login credentials or downloading malware
- Smishing: Sending SMS/text messages purporting to be from reputable companies to induce individuals to reveal personal information, such as passwords or credit card numbers.
- Zero-Day Exploits: The group may have exploited unknown vulnerabilities (zero-days) in MGM’s systems, making it difficult for the company to defend against the attack.
- Evasion Techniques: Scattered Spider employs evasion techniques to avoid detection by security tools and to maintain persistence within the compromised network.
- Supply Chain Attacks: The group may have targeted third-party vendors or suppliers connected to MGM, using them as a gateway to the main network.
Key Learnings and Preventative Measures
More importantly than pontificating ‘what happened’ to MGM, it’s important to discuss what we can learn from this incident. To avoid falling victim to similar vulnerabilities in the wake of more high-profile and expensive attacks, companies need to scale out their cybersecurity program and search for efficiency gains to outpace that of malicious actors like UNC3944 / Scattered Spider.
Security and IT organizations must work in unison to bolster their security posture with a scrutinous assessment in the following areas:
- Threat Intelligence: Stay informed about the latest threat actors and their tactics. Regularly update your threat intelligence to better measure and defend against known groups like Scattered Spider, with assurance that your current asset and VM management are deploying new CVEs and scripts with accurate vulnerability risk-based prioritization.
Check this guide to learn more about building a risk-based vulnerability management program.
- Detection and Remediation with Custom Logic: Invest in advanced threat detection and prevention systems that can identify and respond to APTs and zero-day exploits. If a CVE does not yet exist, test your ability to write your vulnerability detection and remediation script.
For more on the topic of vulnerability detection and remediation using custom logic, read our blog post on the release of first-party software risk management.
- Zero-Trust Architecture: Implement a zero-trust security model that assumes no one, even those within your network, can be trusted without verification for key areas of the network. In the modern era, where phishing and smishing campaigns grow more innovative, it is logical to assume that threat actors will be successful at initial entry. However, it is important to better contain lateral movement after initial entry. Leveraging a strict ZTNA strategy is key.
- Incident Response Plan: Review and update your incident response plan, ensuring it accounts for APTs and sophisticated attackers. Test it regularly to ensure its effectiveness across security and IT operations teams to work out friction and reduce MTTR.
- Employee Training: Continue to educate and train employees on cybersecurity best practices, specifically recognizing and reporting phishing attempts.
- Red Team Testing: Regularly engage in red teaming exercises to simulate real-world attacks and uncover vulnerabilities before malicious actors do.
The Importance of a Risk-Based Vulnerability Management (RBVM) Program
The recent Scattered Spider attack on MGM reinforces the ongoing and evolving nature of cyber threats in the digital age. Cybersecurity remains a top priority for organizations across all sectors, and lessons from incidents like these underscore the need for continuous improvement in vulnerability management. And threat mitigation is a matter of business risk – just not cyber risk.
By taking proactive measures, staying informed about emerging threats, threat actor TTPs, and investing in advanced security solutions, businesses can better protect their sensitive data and the trust of their customers in an era where cybersecurity threats continue to grow in complexity and sophistication.
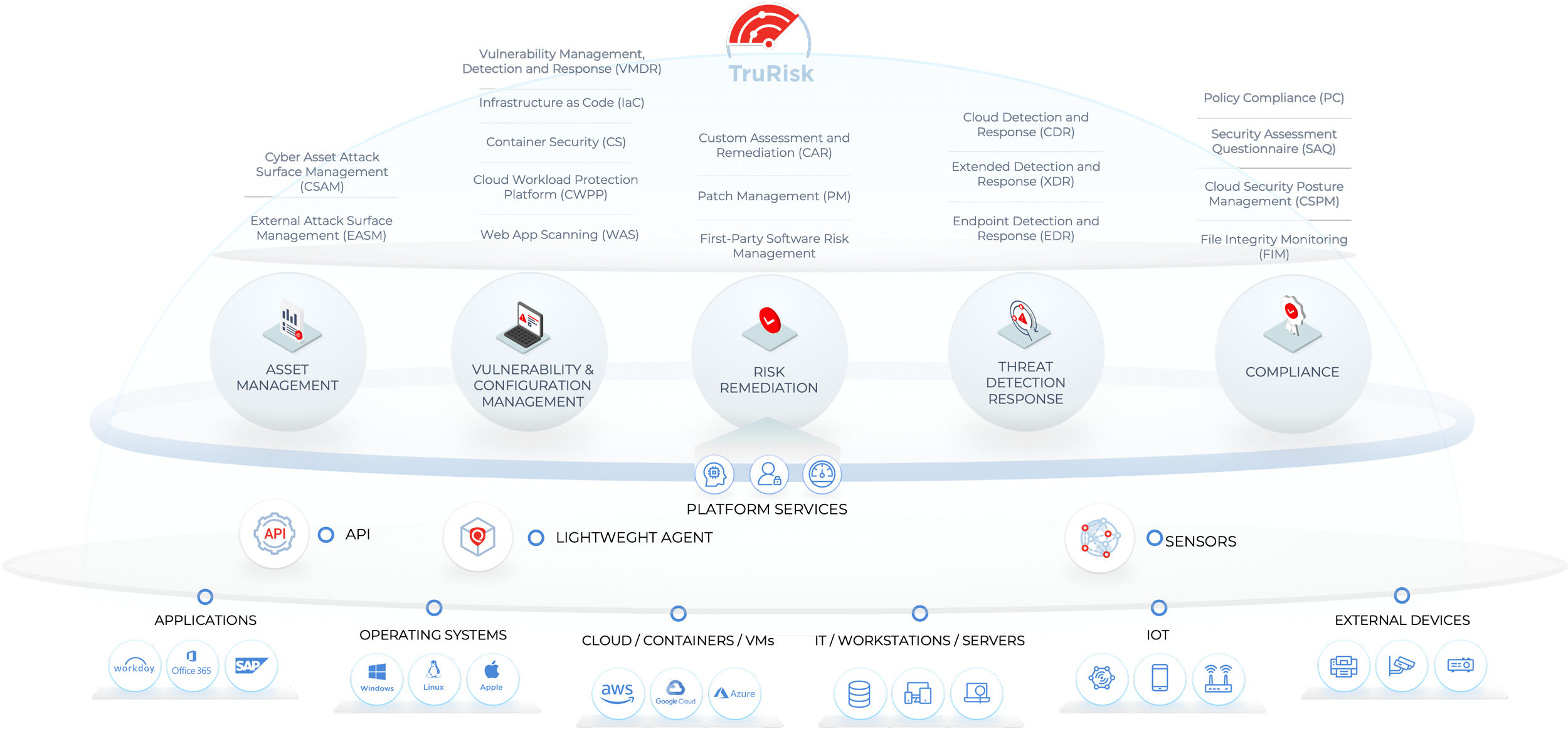
Risk-Based VM strategy (RBVM) is more than just applying risk scores to vulnerability management. It’s about applying risk-based threat prioritization to response and remediation paths across the entire organization.
However, it must be seamless and holistic to amicably respond to threats across an organization. By unifying patching, anti-ransomware, and endpoint security, organizations can better identify but also remediate threats wherever they may be.
To learn more about how to build an effective RBVM that stands up to emerging threats and innovative threat actors, don’t miss our webinar on September 28th, 7 Signs Your Vulnerability Management Is Failing.