Year closing – December 2013 Patch Tuesday
Today Microsoft released 11 security bulletins that address 24 vulnerabilities in the last Patch Tuesday of 2013. This month’s patches takes the total number of bulletins to 106 and the distinct vulnerability count to just over 330 for the year.
Our top priority today is MS13-096, which addresses the 0-day vulnerability in the TIFF parser in Microsoft GDI+ library. This vulnerability is currently under targeted attacks in the Middle East and Asia, and the exploits typically arrive in an Office document. If your machines run on later versions of Microsoft software, you are not affected. However, if you are behind, you should install this patch as soon as possible as you are most likely on a vulnerable configuration, such as Windows XP or an older version of Office (2003 or 2007).
The second currently open 0-day vulnerability does not get addressed in this patch cycle, as it was discovered too late to make it into this release. It is also less severe as it depends on a second vulnerability for delivery on the targeted machine. In the wild, exploits have been delivered through a PDF document abusing an older vulnerability in Adobe Reader. Fortunately, the vulnerability only affects the older Windows, versions XP and 2003, and allows an attacker to become administrator and then install malware to take control of the machine. If you have a vulnerable configuration, we recommend you implement the work-around specified in security advisory KB2914486 and turn off the NDPROXY component. Side-effects should be minimal and limited to the telephony and modem interfaces which should not be in use in most environments.
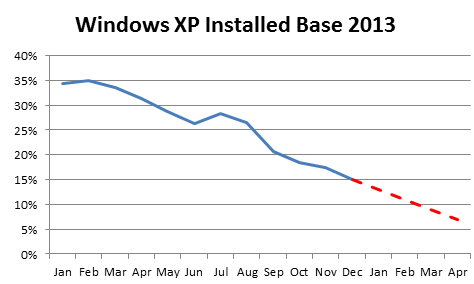
If you are impacted by these two 0-days, you are running older versions of Microsoft software and should evaluate whether it is worth maintaining that strategy. In particular, Windows XP and Office 2003 are on their way out and will be discontinued in April 2014. Their security situation will then become very quickly unmaintainable as Microsoft will cease to publish updates. However, you are not alone – there are almost 15% of enterprise users who still have Windows XP in their networks. We have seen some substantial drop-offs in recent months, but it is doubtful that they will be able to eliminate all XP machines from their networks by April 2014.
But back to the December bulletins. After the TIFF 0-day bulletin we believe that MS13-097, which addresses 7 vulnerabilities in Internet Explorer (IE) should be next on your priority list. All versions of IE are affected and the bulletin comes with a low Exploitability rating of 1, indicating that an exploit for the vulnerabilities would not be hard to craft. The exploit would be delivered through a malicious webpage. Also browser-related but in a separately installed ActiveX component, MS13-099 addresses a critical flaw in VBScript, which could be used to take control of the targeted machine.
MS13-105 is a bulletin related to Microsoft Exchange and addresses a number of flaws related to Outlook Web Access (OWA). After Oracle’s release of a new version of their Outside-In in the Critical Patch Update of October 2013, we already knew that Microsoft would have to incorporate the patch into a future release. The attack vector here is a malicious document sent via e-mail and if visualized by a user, could be used to take control of the mail server. It is not the only the vulnerability in OWA that was addressed, there is also a Viewstate serialization issue and XSS scripting problem. If you use OWA in your setup, MS13-105 is an important patch for your organization.
The remaining critical vulnerability addresses a flaw in the Authenticode signing algorithm that is currently being exploited in the wild. Attackers have been abusing installers from legitimate software makers to install malware. These installers are configured in a way to dynamically download code extensions that are not checked for correct signatures, and attackers have found a way to piggyback on that mechanism. MS13-098 addresses the concrete issue that was found in the wild and prepares the system for a more stringent integrity check that will prevent such abuse in the future. Because of the presence of legacy code, this more stringent system will be activated only six months from now. If you are interested in the underlying technical issues, Microsoft has a detailed post on the issue on the the SRD blog.
One more vulnerability is being abused in the wild. MS13-104 updates Microsoft Office and addresses a flaw in a new SAML-based authentication protocol in Office 365. The vulnerability can be used to steal the authentication token and impersonate a user on the online version of Microsoft Office suite – Office 365.
The remaining vulnerabilities are less critical – rated “important.” They should be addressed in your normal patch schedule and fix local Windows issues in MS13-101 and MS13-102, Office in MS13-106, Sharepoint in MS13-100 and Microsoft Visual Studio in MS13-103.
Adobe Update
Adobe published two updates today: both Shockwave and Flash are getting new versions. Adobe is aware of attacks in the wild against the Flash player, which come embedded in a Word document. Our recommendation is to include the Flash release in your "patch urgently" category. Users of Google Chrome and Internet Explorer 10 get the new Flash player automatically.
In other security news we had another example of the fragility of the SSL certificate ecosystem. Last weekend Google detected a rogue certificate; a French government agency had emitted a certificate for Google websites enabling them to decrypt all traffic by that flowed through their network, a classic MITM setup. The certificate has been revoked, and Google and Microsoft have blacklisted the certificate in question in their browsers directly. Today Mozilla is releasing a new version of Firefox (v26) that excludes that certificate from their certificate store. In addition to fixing five critical vulnerabilities the version also introduces a security feature: click-to-play for plug-ins (for example Java which has been much under attack this past year), which requires a user to approve the execution of a plug-in.
Overall, while this is normal sized Patch Tuesday, it is closing a year with over 100 software updates. 100+ updates continues a trend that we already saw in the last couple of years. While we are getting better in writing software and are committing fewer errors, attackers are stepping up their game as well, constantly looking for new loopholes in our infrastructure. One thing is clear to me though – the 0-days show that being on the latest version of operating systems and application software is a clear advantage in terms of resilience, and it helps IT to run a safer infrastructure. I hope you are already in the category of organizations that have migrated away from XP, Server 2003 and Office 2003, or are at least in the group that is quickly moving towards 0% by April 2014.