Update5 – HackingTeam 0-day for Flash
Update5: Adobe has added a second vulnerability to APSA15-04, CVE-2015-5123, which TrendMicro has found. PoC code is available but not integrated into ExploitKits yet.
Update4: Adobe has acknowledged in APSA15-04 another 0-day for Flash originating in the data dump from HackingTeam. Security researcher Webdevil documents his finding in a tweet. Adobe credits Dhanesh Kizhakkian from FireEye who documented the PoC found in the datadump and notified Adobe (first?). Adobe expects to address the vulnerability next week (during normal Patch Tuesday maybe?). According to @Kafeine the vulnerability is already in use in the Angler Exploit Kit.
Update3: Adobe has released the patch for the HackingTeam 0-day, CVE-2015-5119. Beyond that vulnerability the update APSB15-16 also addresses 42 other vulnerabilities of which 27 can be used to reach remote code execution. Users of Google Chrome get their Flash update automatically, as are users of IE11 and IE11 from Microsoft. Users of other browsers needs to install patch manually, i.e. for Firefox, Opera and Safari. Install as quickly as possible to neutralize the exploits that are available in the major ExploitKits already.
In addition Adobe has pre-announced a new version of Adobe Reader (APSB15-15) for next Tuesday that will address critical vulnerabilities as well.
Update2: Adobe acknowledged the bug in APSA15-03 and will make an update available on Wednesday, July 8th. Excellent, quick reaction. Google is credited for reporting the bug now called CVE-2015-5119. Security researcher @kafeine reports that the Angler, Fiddler, Nuclear and Neutrino ExploitsKIts have added CVE-2015-5119 to their lineup. Patch as quickly as possible or think about adding EMET to your workstations.
Update: EMET 4.1 (last available version for XP) in its default configuration takes care of the attack on Windows XP. EMET is a good additional security tool to install once you are fully patched. It monitors for certain attack patterns and neutralizes them – if the exploit uses any of the common ways to execute shellcode EMET users have a good chance to get away unharmed.
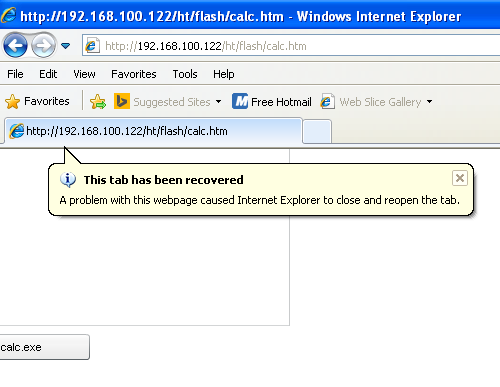
Original: On Sunday a databreach at the surveillance software company HackingTeam was made public. The attacker published a 400 GB dump of company data as a bittorrent file. Steve Ragan at CSO Online has researched and published an excellent time line on his Salted Hash blog.
In the data dump there are apparently exploits for both known and 0-day vulnerabilities. A 0-day for Adobe Flash has just been made public by security researcher Webdevil in a tweet. The exploit is from 2014 and quite simple to deploy. But at least in my limited testing setup works only partially – on Windows XP (latest Flash 18) fine, on Windows 7 with a crash and on 8.1 not at all. Nevertheless, I expect ExploitKit writers to integrate this exploit soon. Stay tuned for more information.