Patch Tuesday September 2015
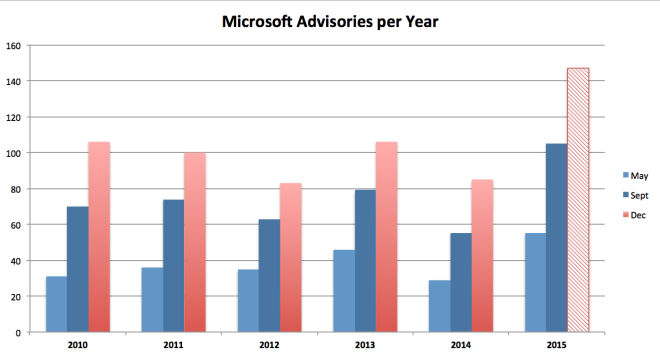
Hello to Patch Tuesday September 2015: We are ¾ through the year and have broken the 100 bulletin mark with this months 12 additions. We are now projecting over a 145 bulletins until the end of the year, a bit higher than our initial projection from May when said we would be seeing just over 140 bulletins this year.
Some of the growth can be attributed to new products, for example this month’s MS15-095 is for Microsoft’s Edge browser (four critical vulnerabilities) that did not exist before the introduction of Windows 10. But the real reason for the rise in bulletins is probably the rising attention that computer security is getting which makes looking at computer security issues a valid career choice for more and more professionals. Recent data breaches at OPM, Target and Ashley Madison have shown that the vulnerabilities and the relative slowness in addressing them can have impacts beyond the financial realm.
This month’s top spot is for the Windows GDI+ bulletin MS15-097. The bulletin is rated critical on Windows Vista and Server 2008, plus Microsoft Office 2007 and 2010, plus Lync 2007, 2010, 2013. In addition one of the vulnerabilities, rated as only as important in the bulletin is under attack in the wild: CVE-2015-2546 allows for an escalation of privilege once on the machines, allowing the attacker to become administrator of the targeted machine. CVE-2015-2546 affects all versions of Windows including Windows 10.
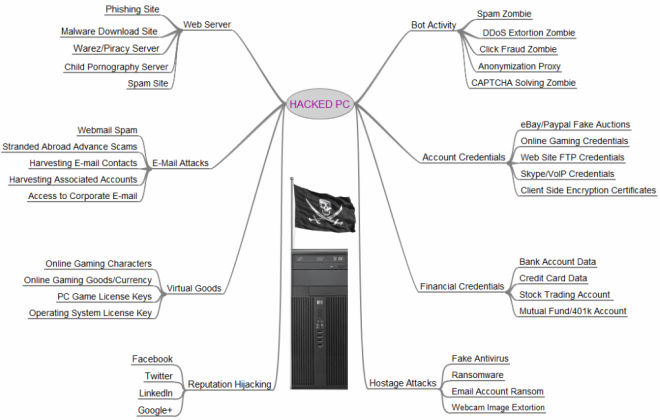
Our second priority lies with MS15-094, the update for Internet Explorer. It addresses 17 flaws, 14 considered critical, i.e. allowing the attacker to take over your browser and execute code on your machine, simply have gone to a webpage. These Remote Code Execution (RCE) vulnerabilities are a mainstay for mass infections that many attack groups look for. We label them “opportunistic” because they do not choose their targets specifically, but rather make their money by infecting as many machines as possible. Take a look at Brian Krebs’ graphic on how to monetize a machine to get an idea why this is useful:
Specifically Hostage Attacks (lower right) have been increasing in the last couple of months, with new variants appearing periodically.
Microsoft’s Edge browser is fixed in bulletin MS15-095, so if you run Windows 10 already that is an important patch to apply. It addresses four critical vulnerabilities, all of them also present in the “old” Internet Explorer.
Also four vulnerabilities are addressed in the critical bulletin MS15-099 for Microsoft Office and Excel. All of them allow for Remote Code Execution when a malicious file is opened. One of the vulnerabilities is currently under limited and targeted attack. Attackers would typically trick users into opening the file by disguising it as something harmless and interesting, say a resume for an open position listed on your site, an article about a subject that is interesting to you or an offer for a free membership or other benefits to some of your users. A recent Incident Report by Bitstamp had some interesting detail on how customized and detail-oriented these attacks can be.
On the server side MS15-103 addresses three vulnerabilities in Exchange server (all in Outlook Web Access) and MS15-096 a DoS condition in Active Directory. These vulnerabilities should be addressed on your normal patch schedule if you run these services.
MS15-100, MS15-101, MS15-102 address vulnerabilities in Windows Media Center, .NET and Windows Task Manager and are all rated important, meaning they can only be abused if the attacker is already on the machine. You should address them on your normal Patch schedule as well.
Adobe: There is no Flash update (just Shockwave APSB15-22). That is the first time since October 2013. Maybe an effect of the modification to Flash that makes exploitation harder – buffer heap partitioning?
That’s it for this Patch Tuesday. Let me know if the increasing number of bulletins represents a challenge to you or whether your processes are scaling as is. Thanks for your attention and see you soon.