Automatically Discover, Prioritize and Remediate Windows Adobe Type Manager Library Remote Code Execution Vulnerability (ADV200006) using Qualys VMDR®

On March 23, Microsoft released zero day advisory ADV200006 to address two critical remote code execution vulnerabilities in Adobe Type Manager Library that affects multiple versions of Windows and Windows Server.
The vulnerabilities exist within the way that Windows parses OpenType fonts. For example, an attacker could convince a user to open a specially crafted document or view it in the Windows Preview pane. Windows Preview pane is used by the Windows Explorer (which is called File Explorer in Windows 10) file manager application to preview pictures, video, and other content. Successful exploitation would require an attacker to convince a user to open a malicious document or visit a malicious page that exploits the WebClient service which is normally listening for WebDAV file shares.
Qualys released a blog post earlier on how to identify ADV200006 in your environment:
Microsoft Released Out-of-Band Advisory – Windows Adobe Type Manager Library Remote Code Execution Vulnerability (ADV200006)
Here we describe how to resolve it with Qualys VMDR®.
Identify Assets, Discover, Prioritize and Remediate using Qualys VMDR®
Qualys VMDR, all-in-one vulnerability management, detection and response enables:
- Identification of known and unknown hosts running vulnerable Windows systems with Adobe Type Manager Library
- Automatic detection of vulnerabilities and misconfigurations for Windows systems
- Prioritization of threats based on risk
- Integrated patch deployment
Identification of Windows Assets with Adobe Type Manager Library or WebClient service running
The first step in managing vulnerabilities and reducing risk is identification of assets. VMDR enables easy identification of windows hosts with Adobe Type Manager Library or WebClient service running –
operatingSystem.category1:`Windows`

You can further identify systems that are running “WebClient” service using a simple query:
operatingSystem.category1:`Windows` and services.name:`WebClient`

Once the hosts are identified, they can be grouped together with a ‘dynamic tag’, let’s say – ADV20006. This helps in automatically grouping existing Windows hosts ADV200006 as well as any new host spins up with this vulnerability. Tagging makes these grouped assets available for querying, reporting and management throughout the Qualys Cloud Platform.
Discover Adobe Type Manager Library RCE Vulnerabilities and Misconfigurations
Now that the windows hosts with ADV200006 are identified, you want to detect which of these assets have flagged this vulnerability. VMDR automatically detects new vulnerabilities like ADV200006 based on the always updated Knowledgebase.
You can see all your impacted hosts for this vulnerability tagged with ‘ADV200006’ asset tag in vulnerabilities view by using QQL query:
vulnerabilities.vulnerability.qid: 91617
This will return a list of all impacted hosts.

VMDR also enables you to stay on top of these threats proactively via the ‘live feed’ provided for threat prioritization. With ‘live feed’ updated for all emerging high and medium risks, you can clearly see the impacted hosts against threats.
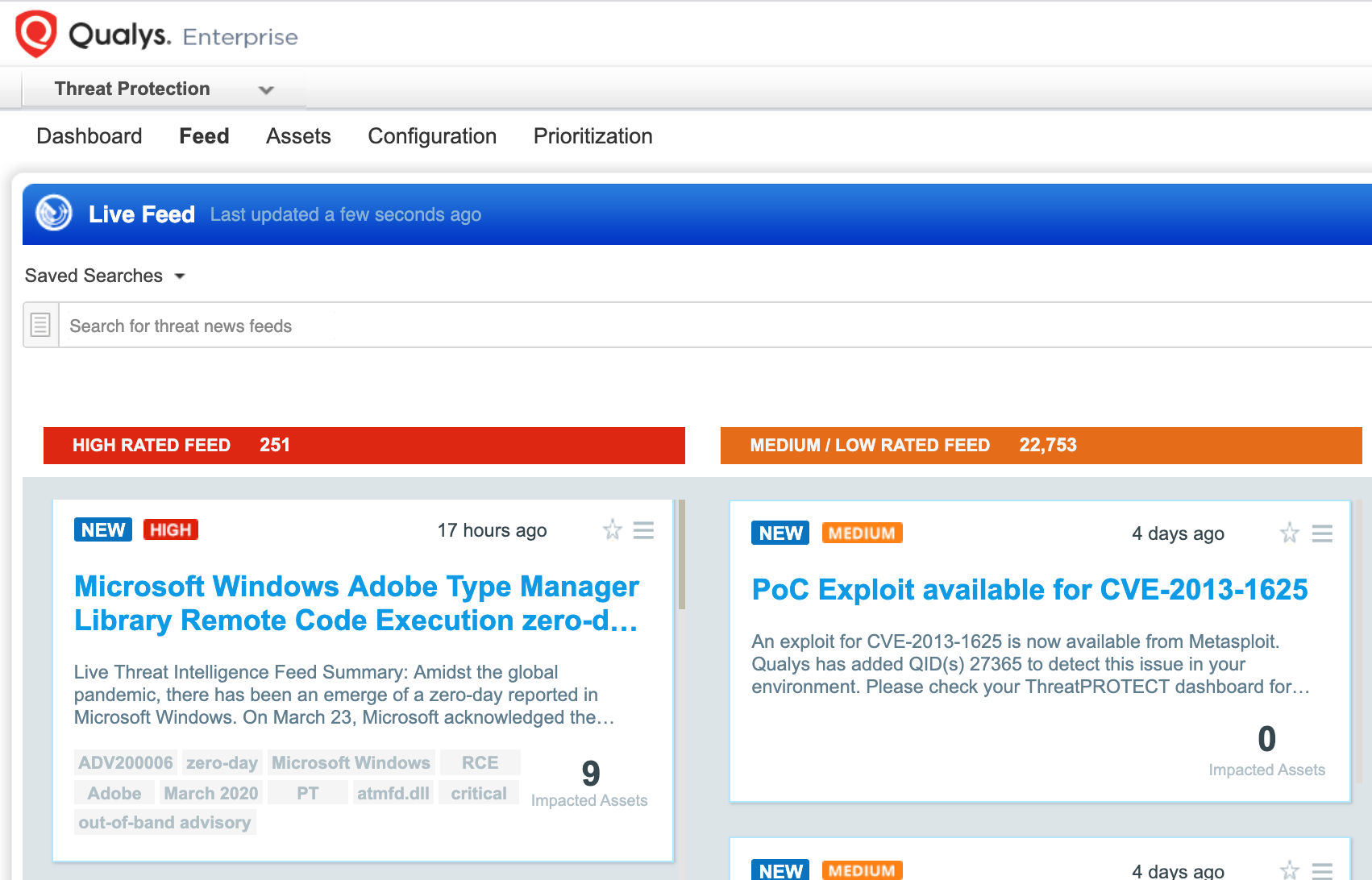
Simply click on the impacted assets for the ADV20006 threat feed to see the vulnerability and impacted host details.
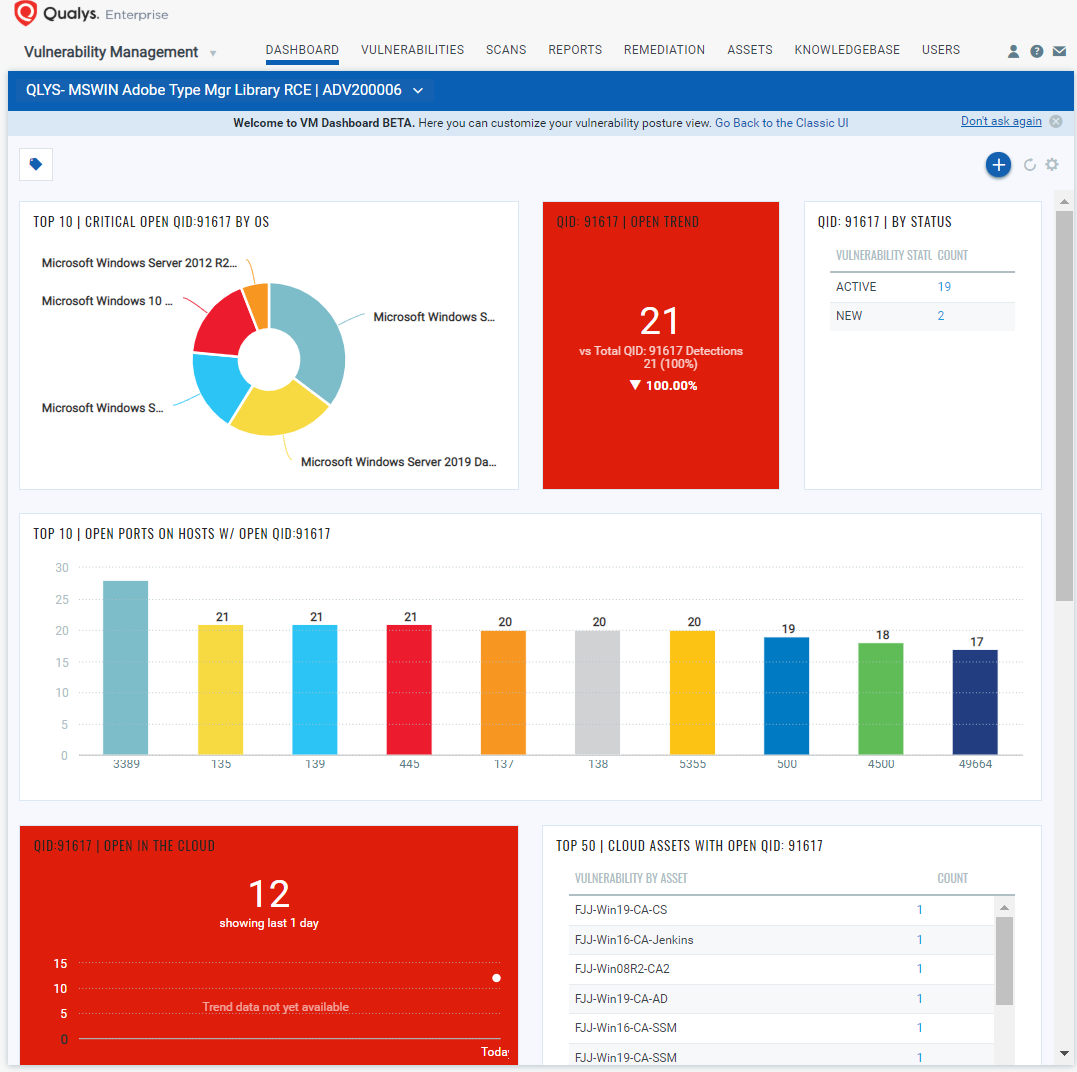
With VM Dashboard, you can track ADV200006, impacted hosts, their status and overall management in real time. With trending enabled for dashboard widgets, you can keep track of ADV200006 vulnerability trends in your environment using Microsoft Adobe Type Manager Library RCE Vulnerability Dashboard –
Configuration management adds context to overall vulnerability management
To overall reduce the security risk, it is important to take care of Windows systems misconfigurations as well. Qualys VMDR shows your windows systems misconfiguration posture in context with your vulnerability posture, allowing you to see which hosts have Adobe Type Manager Library RCE vulnerability.
With Qualys Policy Compliance module of VMDR, you can automatically discover the status of the ‘WebClient’ service and if they have misconfigurations in context to ADV200006 vulnerability.
- Qualys configuration ID – 14916 “Status of Windows Services” would be evaluated against all windows systems for which WebClient service is running on the host as shown below –

- Qualys configuration ID – 17616 “Status of ‘atmfd.dll’ file existence or ‘DisableATMFD’ registry key in the Microsoft Windows System” would be evaluated against all affected windows systems.
- Window 7/8/8.1, Windows 2008 Server, Windows 2012 Server, Windows Server 2012 R2 – Control checks whether atmfd.dll exist or “DisableATMFD” is set to 1 under the key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows
- For Windows 10, Windows 2016 Server version <= 1607 – Control check whether atmfd.dll exists as shown below –

Risk-Based Prioritization of ADV200006 Vulnerability
Now that you have identified the hosts with context of detected vulnerabilities and misconfigurations, you may want to prioritize your remediation based on the risk, as each vulnerable asset might not pose the same risk.
High Risk:
- Hosts with WebClient service running should be prioritized. After applying this workaround it is still possible for remote attackers who successfully exploit this vulnerability to cause the system to run programs located on the targeted users computer or the Local Area Network (LAN), but users will be prompted for confirmation before opening arbitrary programs from the Internet.
- Hosts that have “atmfd.dll” file should be prioritized and can be identified via QID 91617 or misconfigurations (CID 17616 control is failing) are detected as shown below-

Medium Risk:
- Hosts with “atmfd.dll” present, however, the CID 17616 control – “Status of ‘atmfd.dll’ file existence or ‘DisableATMFD’ registry key in the Microsoft Windows System” is detected as hardened as shown below –

Workaround:
While patches are not available yet, Microsoft provided workarounds to secure vulnerable systems:
- Disable the Preview Pane and Details Pane in Windows Explorer (WE)
- Disable the WebClient service
- Rename ATMFD.DLL or disable the registry key for Windows 8.1 and below
The first two workarounds provide less security against the vulnerability, as the attack could still be conducted with permissible conditions. In the first case, a local, authenticated user can still exploit this vulnerability from running a specially crafted program. In the second case also, it is still possible for remote attackers to run programs located on the targeted user’s computer or the LAN. However, users will be prompted for confirmation before opening arbitrary programs from the Internet.
When applying the third workaround, Microsoft says Disabling registry key may cause certain applications to stop working properly as OpenType fonts is not Windows native application and is installed via third-party applications. This mitigation appears to be to the most effective workaround for this vulnerability, as it blocks the vulnerable code from being used by Windows. Because supported Windows 10 versions do not use ATMFD.DLL, this mitigation is not applicable.
Get Started Now
Start your Qualys VMDR trial for automatically identifying, detecting and patching critical Windows Adobe Type Manager Library Remote Code Execution Vulnerability (ADV200006).