Microsoft Exchange Server Zero-Days (ProxyLogon) – Automatically Discover, Prioritize and Remediate Using Qualys VMDR
Update March 10, 2021: A new section describes how to respond with mitigation controls if patches cannot be applied, as recommended by Microsoft. This section details the Qualys Policy Compliance control ids for each vulnerability.
Update March 8, 2021: Qualys has released an additional QID: 50108 which remotely detects instances of Exchange Server vulnerable to ProxyLogon vulnerability CVE-2021-26855 without authentication. QID 50108 is available in VULNSIGS-2.5.125-3 version and above, and is available across all platforms as of March 8th, 1:38 AM ET. This QID is not applicable to agents, so the signature version for the agent will not be updated. QID: 50107, released in VULNSIGS-2.5.121-4 and Windows Cloud Agent manifest 2.5.121.4-3 and above, will accurately detect this vulnerability via agents.
Original Post: On March 2nd, Microsoft released a set of out-of-band security updates to address critical remote code execution vulnerabilities in Microsoft Exchange Server. According to Microsoft these vulnerabilities are actively being exploited in the wild, and hence it is recommended to patch them immediately.
To detect vulnerable instances, Qualys released QID 50107 which detects all vulnerable instances of Exchange server. This QID is included in VULNSIGS-2.5.121-4 version and above.
CVEs addressed as part of this QID are: CVE-2021-26412, CVE-2021-26854, CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065, CVE-2021-27078.
Among the above CVEs, CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065 are being actively targeted in the wild using zero-day exploits. Microsoft attributes these attacks with high confidence to the HAFNIUM (Chinese cyber spy) threat actor group. These vulnerabilities are related to the following versions of Exchange Server:
- Exchange Server 2013
- Exchange Server 2016
- Exchange Server 2019
At the time of the security update release the vulnerabilities affect only on-premises Microsoft Exchange Server installations. Exchange online is not affected.
CVE Technical Details
CVE-2021-26855 is a Server-Side Request Forgery (SSRF) vulnerability that allows attackers to send arbitrary HTTP requests and authenticate to on-premises Exchange servers. Attackers can also trick the Exchange server to execute arbitrary commands by exploiting this vulnerability.
CVE-2021-26857 is an insecure deserialization vulnerability in the Unified Messaging service. Insecure deserialization is where untrusted user-controllable data is deserialized by a program. Attackers who successfully exploit this vulnerability can run their code as SYSTEM on the Exchange server.
CVE-2021-26858 is a post-authentication arbitrary file write vulnerability in Exchange. Exploiting this vulnerability could allow an attacker to write a file to any part of the target Exchange server. Attackers exploiting this vulnerability could write a file to any path on the target Exchange server.
CVE-2021-27065 is a post-authentication arbitrary file write vulnerability in Exchange. Similar to CVE-2021-26858, exploiting this vulnerability could allow an attacker to write a file to any path of the target Exchange server.
Attack Chain
Microsoft has provided details regarding how the HAFNIUM (threat actor) group is exploiting the above-mentioned critical CVEs. Following sequence of steps summarizes Microsoft’s findings.
- The initial step in the attack chain includes the threat actor group making an untrusted connection to the target Exchange server (on port 443) using CVE-2021-26855.
- After successfully establishing the connection, the threat actor group exploits CVE-2021-26857 that gives them ability to run code as SYSTEM on the target Exchange server. This requires administrator permission or another vulnerability to exploit.
- As part of their post-authentication actions, the threat actor group exploits CVE-2021-26858 and CVE-2021-27065 and proceeds to writing files to any path of the target server.
It has been observed that after gaining the initial access, the threat actor group deployed web shells on the target compromised server.
Following table shows the MITRE ATT&CK Technique and Tactic details.
| Tactic | Technique | Sub-Technique | TID |
|---|---|---|---|
| Reconnaissance | Gather Victim Identity Information | Email Addresses | T1589.002 |
| Reconnaissance | Gather Victim Identity Information | IP Addresses | T1589.005 |
| Resource Development | Develop Capabilities | Exploits | T1587.004 |
| Initial Access | Exploit Public-Facing Application | – | T1190 |
| Execution | Command and scripting interpreter | PowerShell | T1059.001 |
| Persistence | Create Account | Domain Account | T1136.002 |
| Persistence | Server Software Component | Web Shell | T1505.003 |
| Credential Access | OS Credential Dumping | LSASS Memory | T1003.001 |
| Credential Access | OS Credential Dumping | NTDS | T1003.003 |
| Lateral Movement | Remote Services | SMB/Windows Admin Shares | T1201.002 |
| Collection | Archive Collected Data | Archive via Utility | T1560.001 |
| Collection | Email Collection | Remote Email Collection | T1114.002 |
| Collection | Email Collection | Local Email Collection | T114.001 |
| Command and Control | Remote Access Software | – | T1219 |
| Exfiltration | Exfiltration over Web Service | Exfiltration to Cloud Storage | T1567.002 |
Discover and Remediate the Zero-Day Vulnerabilities Using Qualys VMDR
Identify Microsoft Exchange Server Assets
The first step in managing these critical vulnerabilities and reducing risk is identification of assets. Qualys VMDR makes it easy to identify Windows Exchange server systems.
Query: operatingSystem.category:Server and operatingSystem.category1:`Windows` and software:(name:Microsoft Exchange Server)
Once the hosts are identified, they can be grouped together with a ‘dynamic tag’, let’s say – “Exchange Server 0-day”. This helps in automatically grouping existing hosts with the 0-days as well as any new Windows Exchange server that spins up in your environment. Tagging makes these grouped assets available for querying, reporting and management throughout the Qualys Cloud Platform.
Discover Exchange Server Zero-Day Vulnerabilities
Now that hosts running Microsoft Exchange Server are identified, you want to detect which of these assets have flagged this vulnerability. VMDR automatically detects new vulnerabilities like these based on the always updated KnowledgeBase (KB).
You can see all your impacted hosts for this vulnerability tagged with the ‘Exchange Server 0-day’ asset tag in the vulnerabilities view by using this QQL query:
VMDR query: vulnerabilities.vulnerability.qid:50107
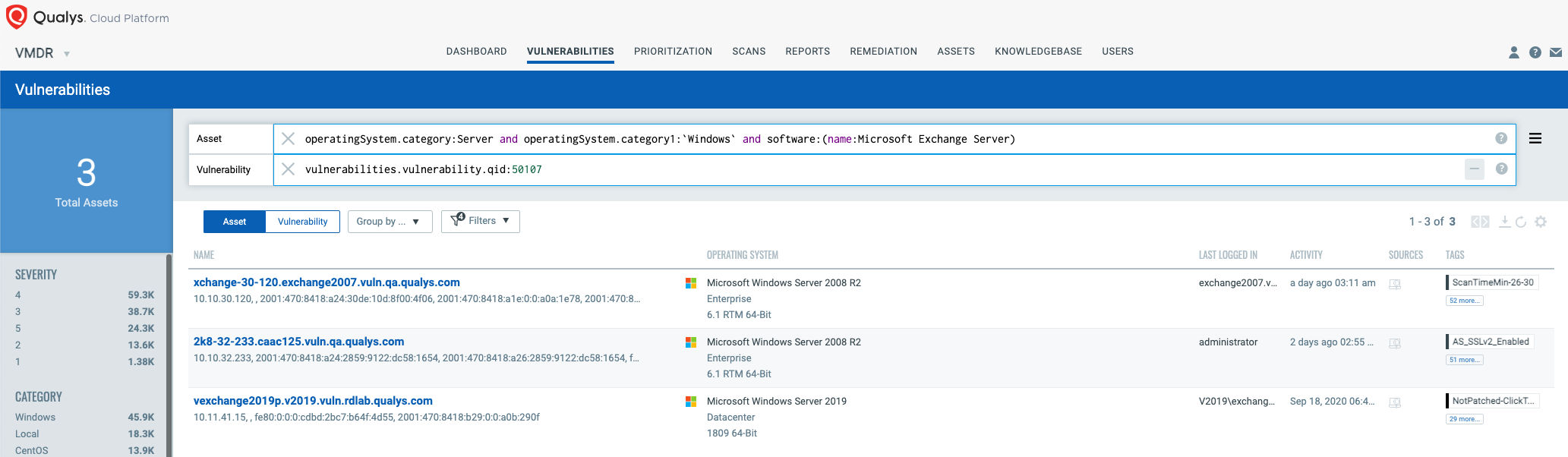
QID 50107 is available in signature version VULNSIGS-2.5.121-4 and above and can be detected using authenticated scanning or the Qualys Cloud Agent manifest version 2.5.121.4-3 and above.
Qualys has released an additional QID: 50108 which remotely detects instances of Exchange Server vulnerable to ProxyLogon vulnerability CVE-2021-26855 without authentication. This QID is not applicable to agents. QID 50108 is available in VULNSIGS-2.5.125-3 version and above.
Organizations that use on-premises Exchange installations typically also enable Outlook Web Access (OWA), which is exposed to the internet to allow users to connect into their e-mail systems. It is therefore recommended organizations employ both remote and authenticated scanning methods to get the most accurate view of vulnerable assets, as using only the agent-based approach would not provide a comprehensive picture of the vulnerability exposure.
With VMDR Dashboard, you can track ‘Exchange 0-day’, impacted hosts, their status and overall management in real time. With trending enabled for dashboard widgets, you can keep track of the vulnerability trends in your environment using the Exchange Server 0-Day Dashboard.
Dashboard: Exchange Server 0-Day Dashboard | Critical Global View
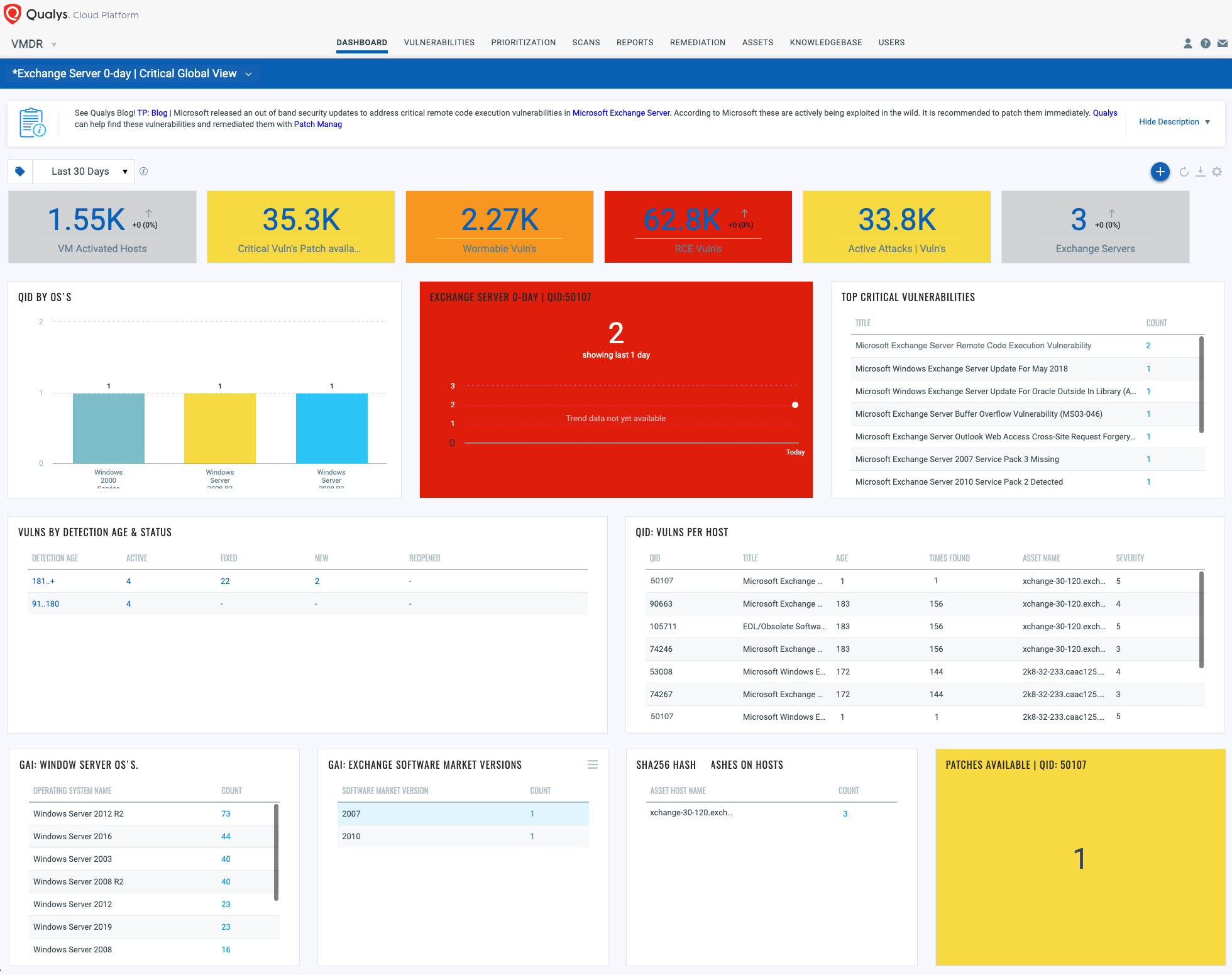
Respond by Patching
VMDR rapidly remediates the Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select “qid: 50107” in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches in one go for hosts grouped together by a tag – Exchange Server 0-day.
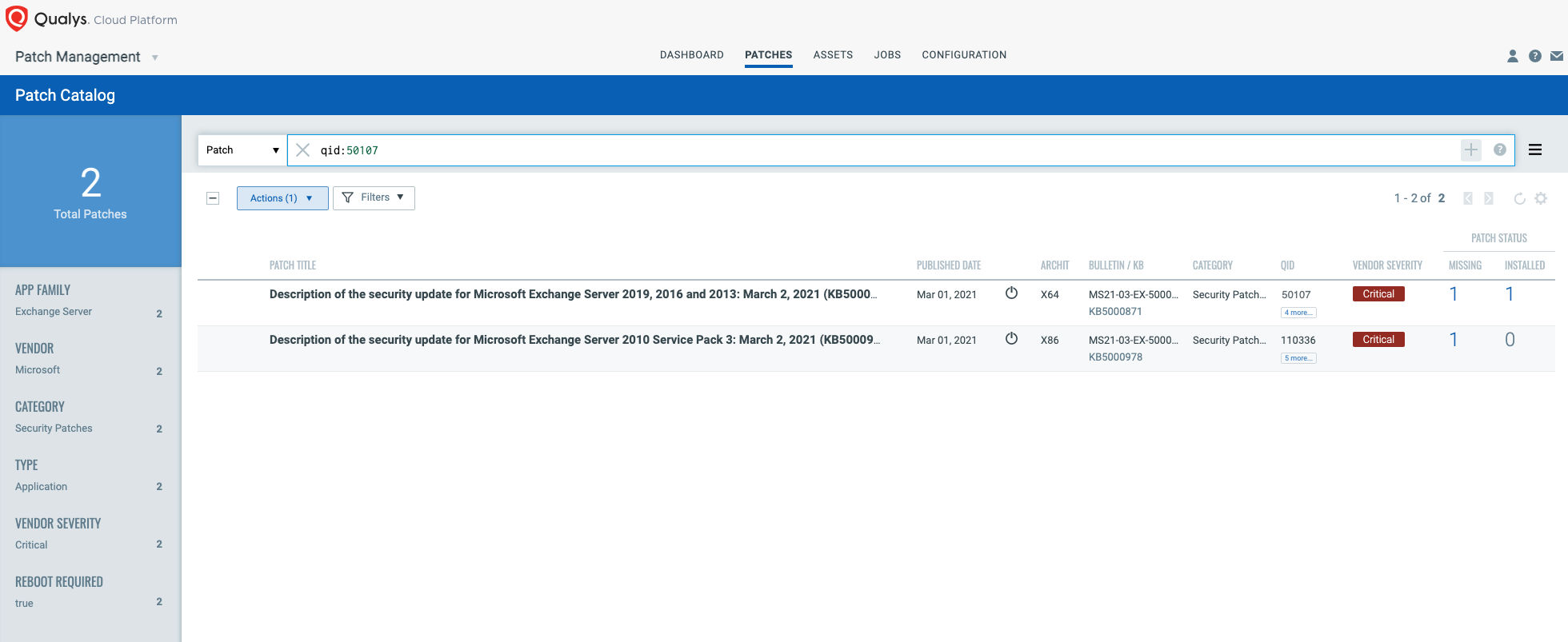
Security updates are available for the following specific versions of Exchange:
- Update for Exchange Server 2019: Requires Cumulative Update (CU) 8 or CU 7
- Update for Exchange Server 2016: Requires CU 19 or CU 18
- Update for Exchange Server 2013: Requires CU 23
- Update for Exchange Server 2010: Requires SP 3 or any SP 3 RU
- This is a defense-in-depth update.
Users are encouraged to apply patches as soon as possible.
Respond with Mitigation Controls if Patches Cannot Be Applied
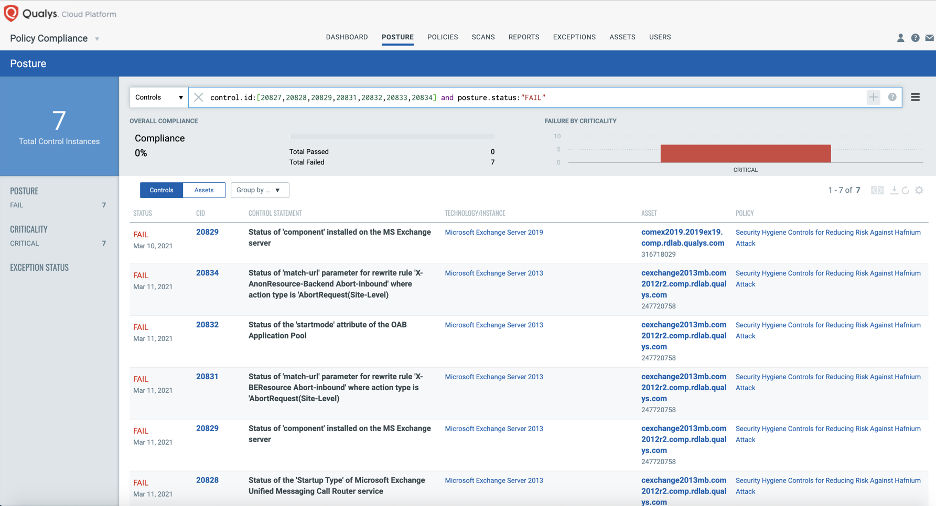
We recognize not all organizations may be able patch their systems right away. In such scenarios Microsoft has recommended a few interim mitigation controls to limit the exploitation of these vulnerabilities. Qualys Policy Compliance has added controls based on these recommendations for impacted Exchange Servers 2013, 2016, and 2019. The vulnerability details and corresponding Control IDs (CIDs) are provided below.
CVE-2021-26855: This mitigation will filter https requests that contain malicious X-AnonResource-Backend and malformed X-BEResource cookies which were found to be used in the SSRF attacks in the wild. This will help with defense against the known patterns observed but not the SSRF as a whole.
- CID 20831 – Status of match URL of rewrite rule ‘X-BEResource Abort – inbound’ for which action is ‘AbortRequest at site level
- CID 20834 – Status of match URL of rewrite rule ‘X-AnonResource-Backend Abort – inbound’ for which action is ‘AbortRequest at site level
CVE-2021-26857: Disabling the UM Service will mitigate this vulnerability.
- CID 20829 – Status of ‘component’ installed on the MS Exchange server
- CID 20828 – Status of Microsoft Exchange Unified Messaging Call Router service
- CID 20827 – Status of Microsoft Exchange Unified Messaging service
CVE-2021-27065: Disabling OAB Application Pool will prevent this CVE from executing successfully as the API will no longer respond and return a 503 when calling OAB, which will mitigate the Arbitrary Write exploit that occurs with OAB. After stopping the WebApp Pool you will also need to set the OabProxy Server Component state to Inactive.
- CID 20832 – Check the ‘startMode’ of the OAB Application Pool (MSExchangeOABAppPool)
CVE-2021-26858: Disabling ECP Virtual Directory will prevent CVE-2021-27065 from executing successfully as the API will no longer respond and return a 503 when calling the Exchange Control Panel (ECP).
- CID 20833 – Check the ‘startMode’ of the ECP Application Pool (MSExchangeECPAppPool)
Qualys Policy Compliance can be used to easily monitor these mitigating controls for impacted Exchange assets.
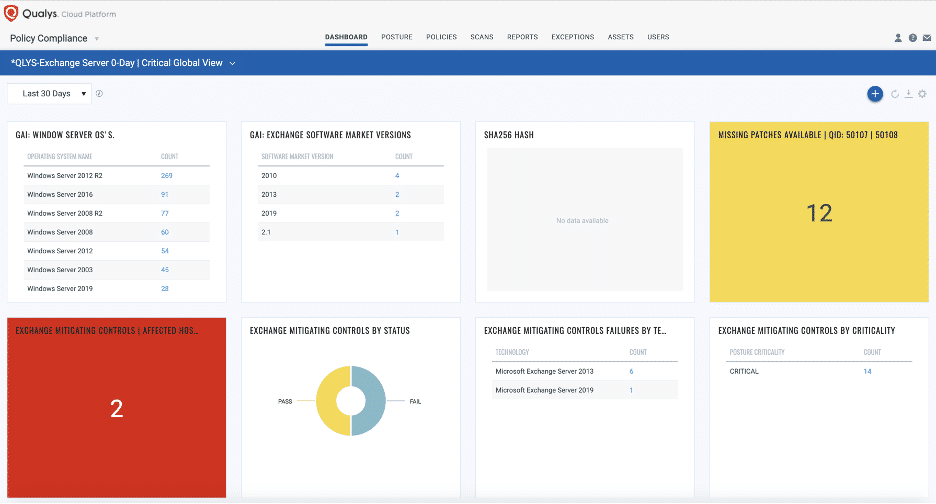
Drill down into failing controls to view details and identify issues.
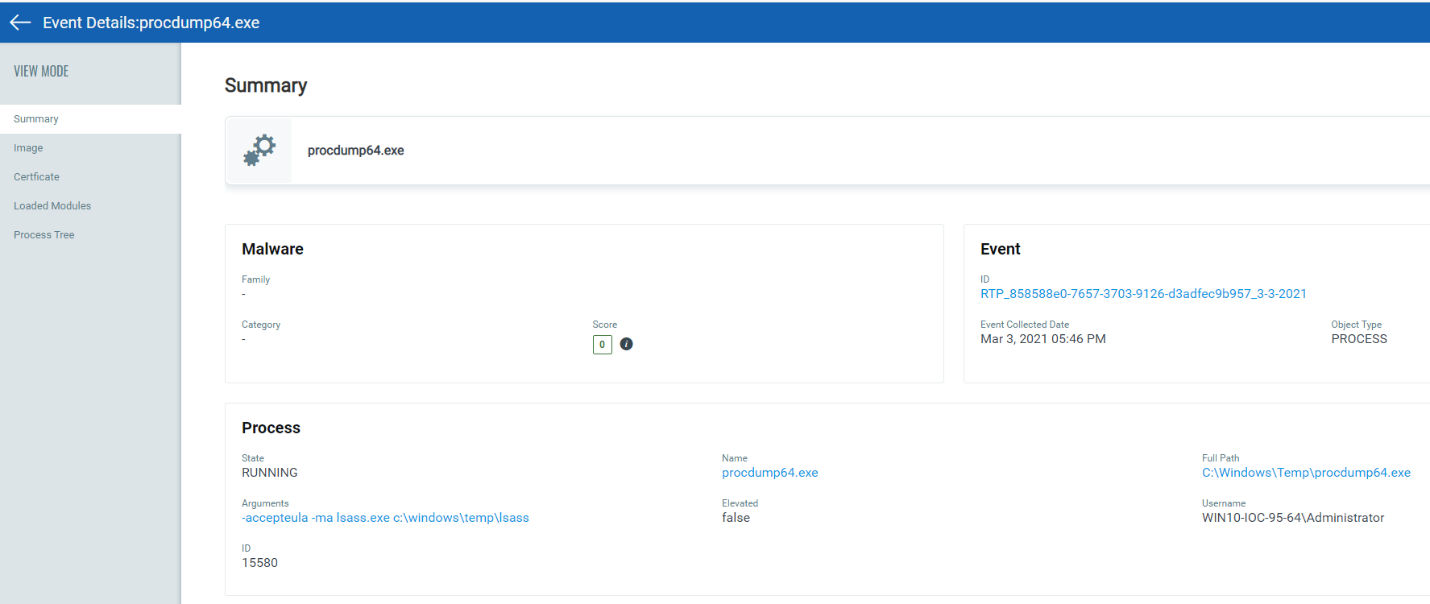
Post-Compromise Detection Details
After compromising a system, an adversary can perform the following activity:
Use legitimate utilities such as procdump or the rundll32 comsvcs.dll method to dump the LSASS process memory. Presumably, this follows exploitation via CVE-2021-26857 as these methods do need administrative privileges.
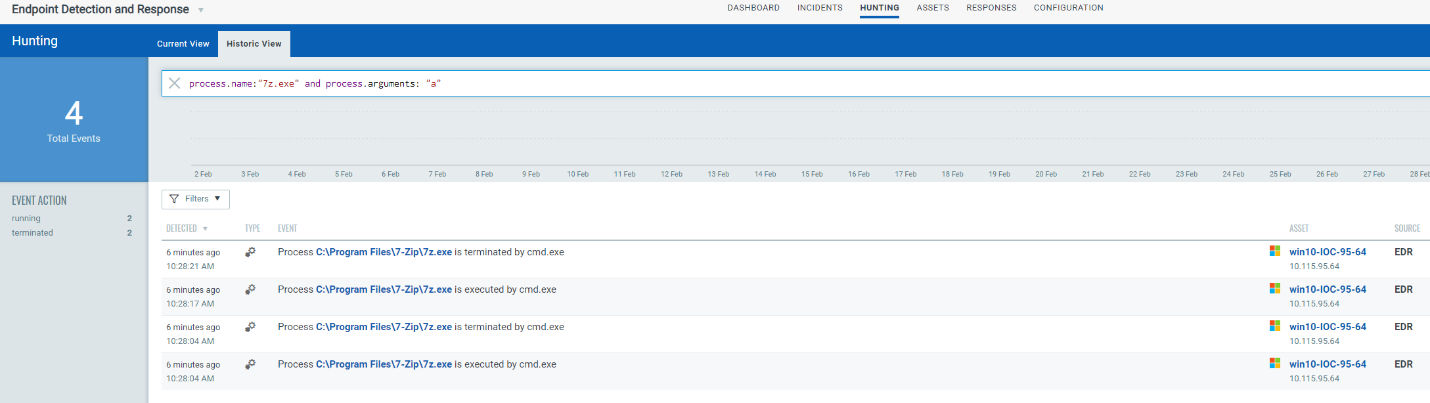
Use 7-Zip or WinRar to compress files for exfiltration.
Use PowerShell based remote administration tools such as Nishang & PowerCat to exfiltrate this data.
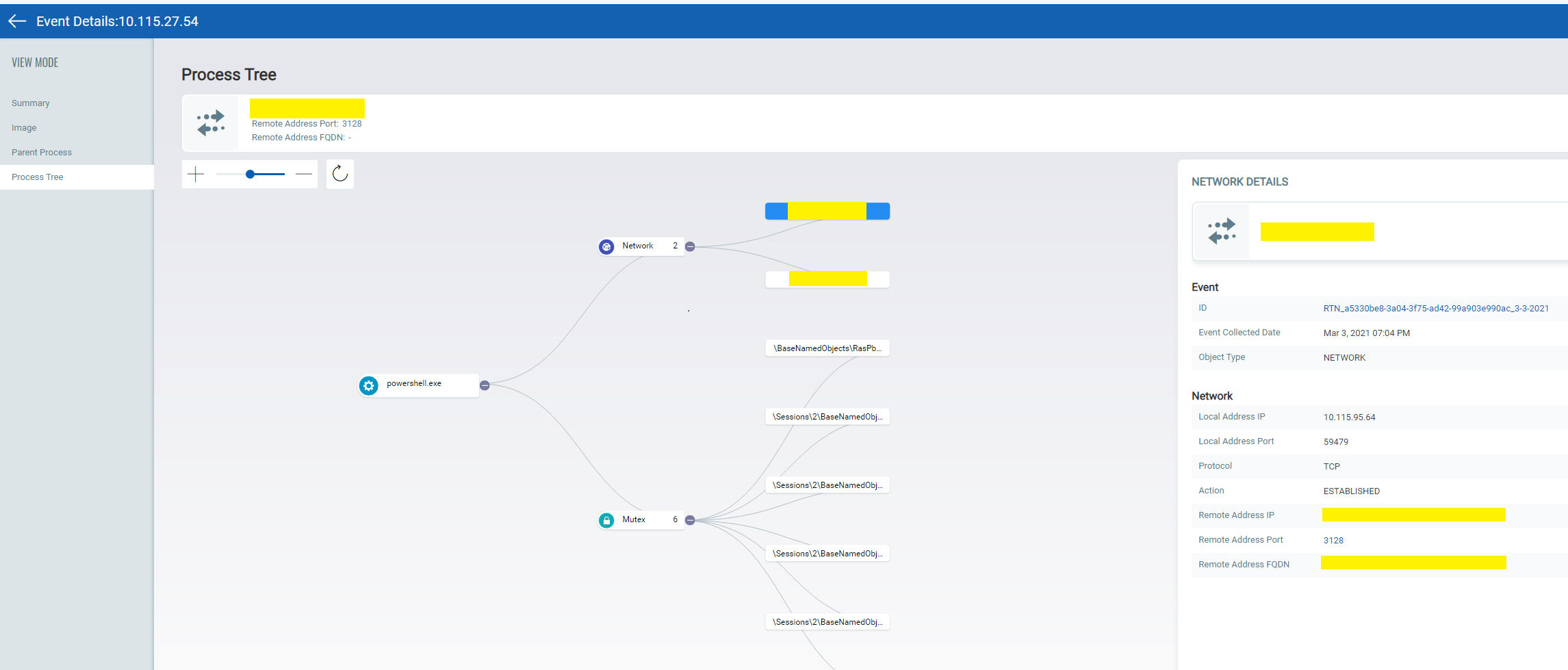
To maintain persistent access on compromised systems, adversaries may also create a domain user account and install ASPX- and PHP-based web shells for command and control. Information about their probable location and their related hashes are mentioned below.
Web shell hashes:
b75f163ca9b9240bf4b37ad92bc7556b40a17e27c2b8ed5c8991385fe07d17d0 097549cf7d0f76f0d99edf8b2d91c60977fd6a96e4b8c3c94b0b1733dc026d3e 2b6f1ebb2208e93ade4a6424555d6a8341fd6d9f60c25e44afe11008f5c1aad1 65149e036fff06026d80ac9ad4d156332822dc93142cf1a122b1841ec8de34b5 511df0e2df9bfa5521b588cc4bb5f8c5a321801b803394ebc493db1ef3c78fa1 4edc7770464a14f54d17f36dc9d0fe854f68b346b27b35a6f5839adf1f13f8ea 811157f9c7003ba8d17b45eb3cf09bef2cecd2701cedb675274949296a6a183d 1631a90eb5395c4e19c7dbcbf611bbe6444ff312eb7937e286e4637cb9e72944
Web shell paths:
C:\inetpub\wwwroot\aspnet_client\ C:\inetpub\wwwroot\aspnet_client\system_web\ %PROGRAMFILES%\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\ %PROGRAMFILES%\Microsoft\Exchange Server\V14\FrontEnd\HttpProxy\owa\auth\ C:\Exchange\FrontEnd\HttpProxy\owa\auth\
References
- https://techcommunity.microsoft.com/t5/exchange-team-blog/released-march-2021-exchange-server-security-updates/ba-p/2175901
- https://www.microsoft.com/security/blog/2021/03/02/hafnium-targeting-exchange-servers/