March 2022 Patch Tuesday: Microsoft Releases 92 Vulnerabilities With 3 Critical; Adobe Releases 3 Advisories, 6 Vulnerabilities With 5 Critical.
Table of Contents
- Microsoft Patch Tuesday Summary
- Notable Microsoft Vulnerabilities Patched
- Notable Adobe Vulnerabilities Patched
- Discover and Prioritize Patch Tuesday Vulnerabilities in VMDR
- Respond by Patching
- Monthly Webinar Series: This Month in Vulnerabilities & Patches
- Join the webinar: This Month in Vulnerabilities & Patches
- About Patch Tuesday
- Contributor
Microsoft Patch Tuesday Summary
Microsoft has fixed 92 vulnerabilities, including 21 Microsoft Edge vulnerabilities, in the March 2022 update, with three classified as critical as they allow Remote Code Execution (RCE). This month’s Patch Tuesday release includes fixes for three publicly disclosed zero-day vulnerabilities as well. As of this writing, none of this month’s list of vulnerabilities is known to be actively exploited in the wild.
Microsoft has fixed several problems in their software including Denial of Service, Edge – Chromium, Elevation of Privilege, Information Disclosure, Remote Code Execution, Security Feature Bypass, and Spoofing vulnerabilities.
Notable Microsoft Vulnerabilities Patched
This month’s advisory covers multiple Microsoft products, including, but not limited to, .NET and Visual Studio, Azure Site Recovery, Defender, Edge (Chromium-based), Exchange Server, HEIF Image Extension, HEVC Video Extension, Intune, Microsoft 365 Apps, Office, Paint 3D, Remote Desktop, SMB Server and Windows OS.
CVE-2022-21990 and CVE-2022-23285 – Remote Desktop Client Remote Code Execution (RCE) Vulnerability
This vulnerability has a CVSSv3.1 score of 8.8/10. In the case of a Remote Desktop connection, an attacker with control of a Remote Desktop Server could trigger a remote code execution (RCE) on the RDP client machine when a victim connects to the attacking server with the vulnerable Remote Desktop Client.
Exploitability Assessment: Exploitation More Likely.
CVE-2022-23277 – Microsoft Exchange Server Remote Code Execution (RCE) Vulnerability
This vulnerability has a CVSSv3.1 score of 8.8/10. The attacker for this vulnerability could target the server accounts in an arbitrary or remote code execution (RCE). As an authenticated user, the attacker could attempt to trigger malicious code in the context of the server’s account through a network call.
Exploitability Assessment: Exploitation More Likely.
CVE-2022-24469 – Azure Site Recovery Elevation of Privilege Vulnerability
This vulnerability has a CVSSv3.1 score of 8.1/10. An attacker can call Azure Site Recovery APIs provided by the Configuration Server and in turn, get access to configuration data including credentials for the protected systems. Using the APIs, the attacker can also modify/delete configuration data which in turn will impact Site Recovery operation.
Exploitability Assessment: Exploitation Less Likely.
CVE-2022-24508 – Windows SMBv3 Client/Server Remote Code Execution (RCE) Vulnerability
This vulnerability has a CVSSv3.1 score of 8.8/10. In addition to releasing an update for this vulnerability, Microsoft has also provided a workaround that may be helpful in your situation. In all cases, Microsoft strongly recommends that you install the updates for this vulnerability as soon as they become available even if you plan to leave this workaround in place: This vulnerability exists in a new feature that was added to Windows 10 version 2004 and exists in newer supported versions of Windows. Older versions of Windows are not affected.
Exploitability Assessment: Exploitation More Likely.
Notable Adobe Vulnerabilities Patched
Adobe released updates to fix six CVEs affecting AfterEffects, Illustrator, and Photoshop. Of these six vulnerabilities, five are treated as critical.
APSB22-14 : Security Update Available for Adobe Photoshop
This update resolves an important vulnerability. Successful exploitation could lead to memory leak in the context of the current user.
APSB22-15 : Security Update Available for Adobe Illustrator
This update resolves a critical vulnerability that could lead to arbitrary code execution.
APSB22-17 : Security Update Available for Adobe After Effects
This update addresses critical security vulnerabilities. Successful exploitation could lead to arbitrary code execution in the context of the current user.
Discover and Prioritize Patch Tuesday Vulnerabilities in VMDR
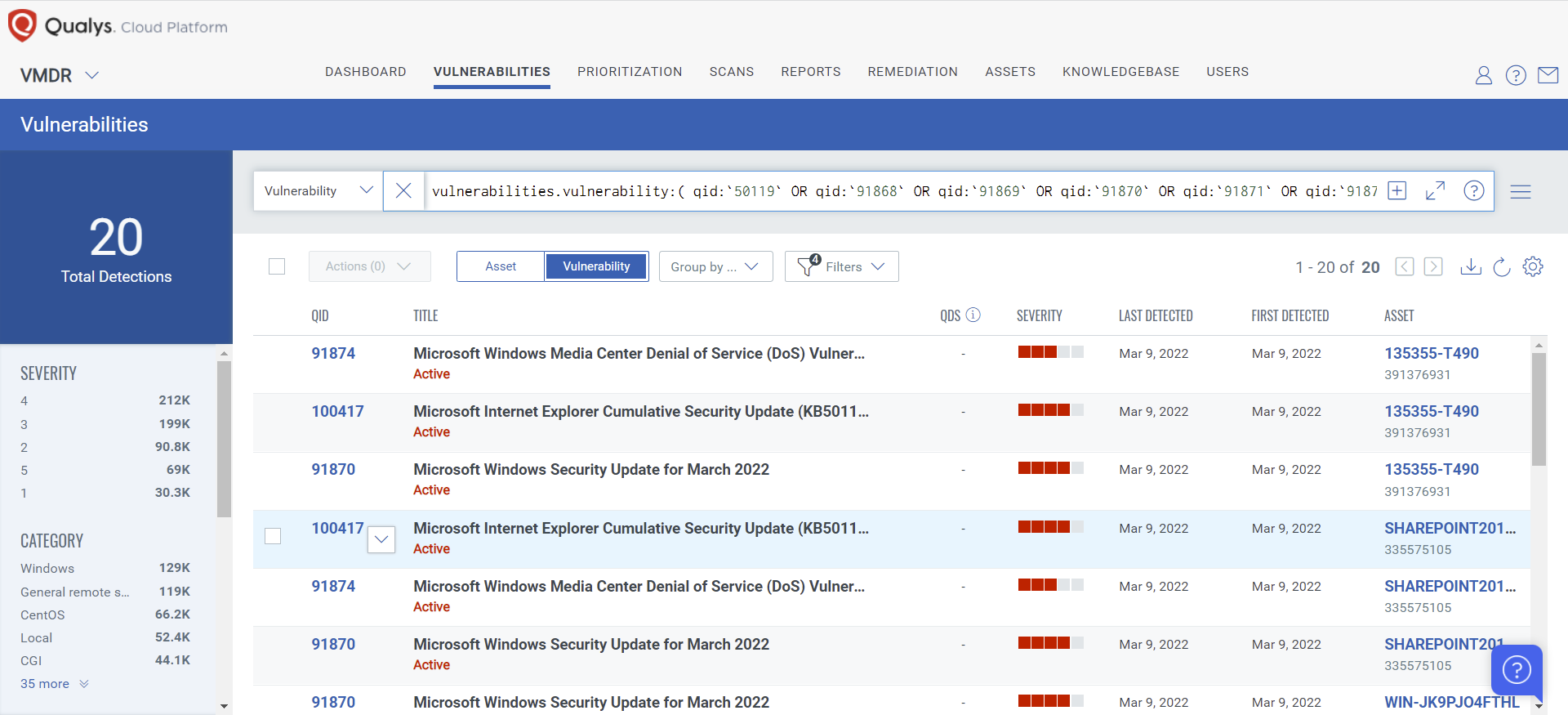
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledge Base (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability:( qid:`50119` OR qid:`91868` OR qid:`91869` OR qid:`91870` OR qid:`91871` OR qid:`91872` OR qid:`91873` OR qid:`91874` OR qid:`91875` OR qid:`100417` OR qid:`110403` OR qid:`376453` OR qid:`376454` )
Respond by Patching
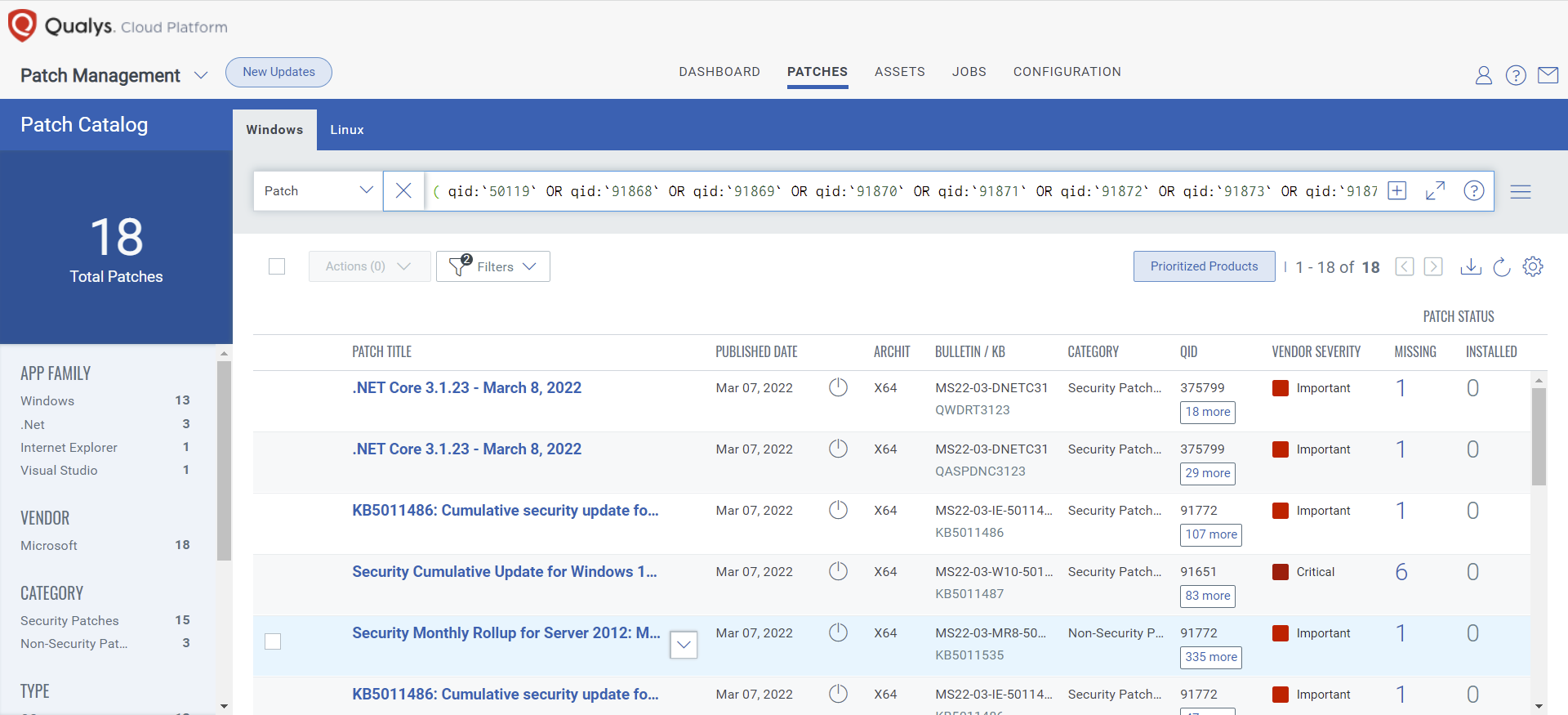
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches in one go.
The following QQL will return the missing patches pertaining to this Patch Tuesday:
( qid:`50119` OR qid:`91868` OR qid:`91869` OR qid:`91870` OR qid:`91871` OR qid:`91872` OR qid:`91873` OR qid:`91874` OR qid:`91875` OR qid:`100417` OR qid:`110403` OR qid:`376453` OR qid:`376454` )
Monthly Webinar Series: This Month in Vulnerabilities & Patches

The Qualys Research team hosts a monthly webinar series to help our existing customers leverage the seamless integration between Qualys Vulnerability Management Detection Response (VMDR) and Patch Management (PM). Combining these two solutions can reduce the median time to remediate critical vulnerabilities.
During the webcast, we will discuss this month’s high-impact vulnerabilities, including those that are part of this month’s Patch Tuesday alert. We will walk you through the necessary steps to address the key vulnerabilities using Qualys VMDR and Patch Management.
Join the webinar: This Month in Vulnerabilities & Patches
About Patch Tuesday
Qualys Patch Tuesday QIDs are published as Security Alerts, typically, late in the evening on the day of Patch Tuesday, followed later by the publication of the monthly queries for the Unified Dashboard: 2022 Patch Tuesday (QID Based) Dashboard.
Contributor
Bharat Jogi, Director, Vulnerability and Threat Research, Qualys
Thank you for sharing.