Protect your Devices from Pegasus Spyware using VMDR for Mobile Devices’ Proactive Approach

Pegasus spyware is in the news, and it has been used to target devices of critical people from different sectors and countries including journalists, activists, politicians, and business executives. It has been said that a leaked list of 50,000 phone numbers of potential surveillance targets was obtained by Paris-based journalism nonprofit Forbidden Stories and Amnesty International.
Pegasus spyware is a surveillance software created by Israeli cyber intelligence firm NSO Group. Pegasus is one such software developed to gain access to your phone without consent and gather personal and sensitive information and deliver it to the user spying on you.
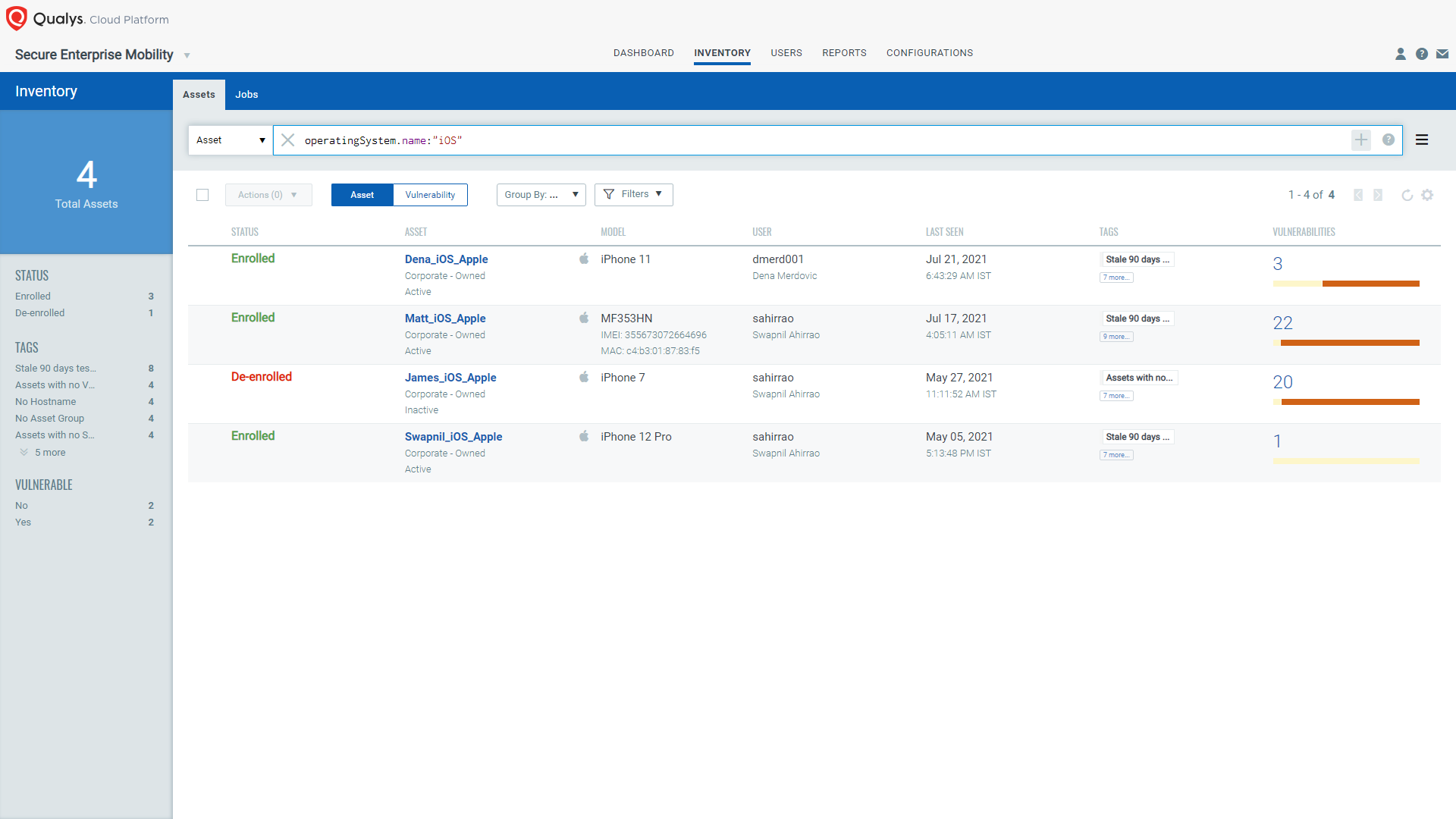
Attack Vectors and Impact of Pegasus Spyware
The first version of the spyware was detected in 2016 and used spear-phishing to infect a smartphone. It now adopts a different and more sophisticated approach for reaching new targets. It can infect a device using the “zero-click” attack done by exploiting the vulnerabilities present on the victim device. The “zero-click” attack happened earlier in December 2020 using iMessage vulnerabilities. Also, in 2019 using the WhatsApp vulnerabilities.
The attack vectors for the Pegasus spyware are the vulnerabilities present on the devices: OS-level message (SMS) or iMessage app, WhatsApp, or other vulnerabilities that can be exploited.
Once Pegasus spyware is installed on the device, it can effectively monitor any activity you perform on it. This includes reading or copying your messages, extracting your media files, accessing your browser history, recording your calls, and much more.
VMDR for Mobile Devices Helps Protect from Pegasus Spyware
Qualys VMDR for Mobile Devices detects devices that are potentially prone to Pegasus spyware based on the vulnerabilities mentioned below, which is a proactive approach. Pegasus is sophisticated spyware with anti-forensic and self-destruct features that make it difficult to detect. If it is uninstalled later, it does not leave any trace. VMDR for Mobile Devices must therefore detect if the device is vulnerable to Pegasus rather than detecting the presence of Pegasus spyware itself.
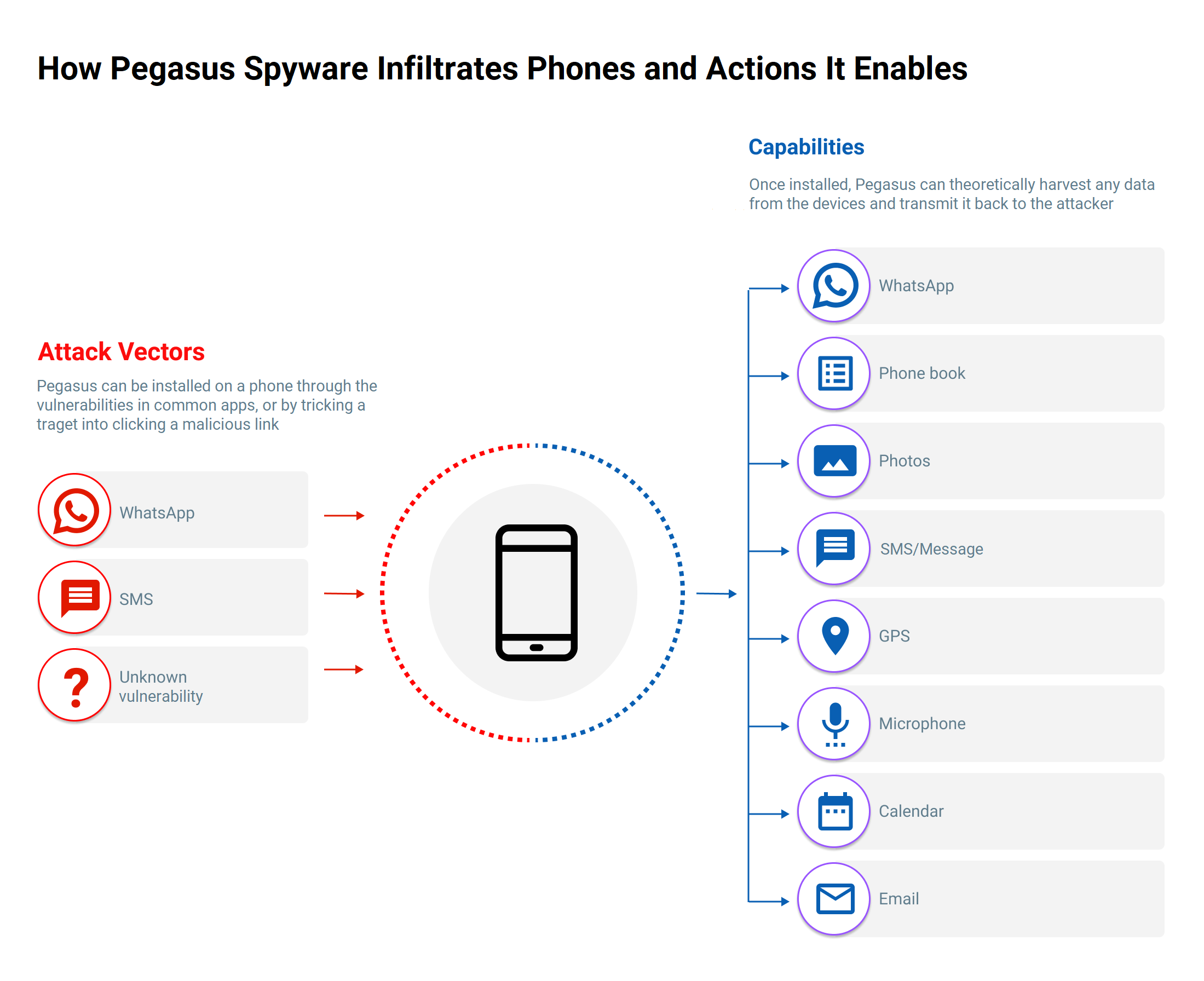
iOS Pegasus:
All iOS devices are vulnerable to the following CVEs that are fixed in the latest iOS versions that might be used to install Pegasus spyware and to get the details from the devices
- CVE-2020-9954, CVE-2020-9956, CVE-2020-9947, CVE-2020-9950, CVE-2020-9988, CVE-2020-9989, CVE-2020-9941 – Fixed in iOS and iPadOS 14
- CVE-2020-10017, CVE-2020-27908, CVE-2020-27909 – Fixed in iOS and iPadOS 14.2
- CVE-2020-29610 – Fixed in iOS and iPadOS 14.3
- CVE-2021-1838, CVE-2021-1746, CVE-2021-1743, CVE-2021-1763, CVE-2021-1768, CVE-2021-1745, CVE-2021-1762, CVE-2021-1767, CVE-2021-1753, CVE-2021-1781 – Fixed in iOS 14.4
- CVE-2021-1879 – Fixed in iOS and iPadOS 14.4.2
- CVE-2021-30743, CVE-2021-1883 – Fixed in iOS 14.5
- CVE-2021-30665, CVE-2021-30663, CVE-2021-30666(iOS 12.5.3), CVE-2021-30661(iOS 12.5.3) – Fixed in iOS and iPadOS 14.5.1 & iOS 12.5.3
- CVE-2021-30707, CVE-2021-30749, CVE-2021-30734 – Fixed in iOS and iPadOS 14.6
- CVE-2021-30788, CVE-2021-30759, CVE-2021-30792, CVE-2021-30791 – Fixed in iOS and iPadOS 14.7
Note that more CVEs might be exploited by Pegasus of the old iOS versions, i.e., below 14.0. If you are using old iOS versions, then your device might be more vulnerable to Pegasus spyware.
With VMDR for Mobile Devices, quickly check the security posture of all your mobile devices across your enterprise to remove blind spots, continuously detect these vulnerabilities and prioritize them. This helps you to take appropriate actions on the impacted devices.
Android Pegasus:
VMDR for Mobile Devices quickly detects and prioritizes all the WhatsApp vulnerabilities, other messaging app vulnerabilities, and OS vulnerabilities. Earlier, the attack of Pegasus was made through WhatsApp app vulnerabilities, i.e., the Pegasus spyware can be installed on the phone using these vulnerabilities.
Respond by Patching and Remediation
VMDR for Mobile Devices helps you to get a view of all vulnerabilities along with their priorities. Prioritizing the vulnerabilities based on the severity helps you take corrective and preventive actions on the impacted devices.
VMDR for Mobile Devices provides you the patch orchestration for Android devices that helps you rapidly remediate your Android assets. Patch orchestration helps you initiate the most relevant per-application version patches on the affected assets.
You do not have to create multiple jobs; one job will take care of all vulnerabilities of that application.
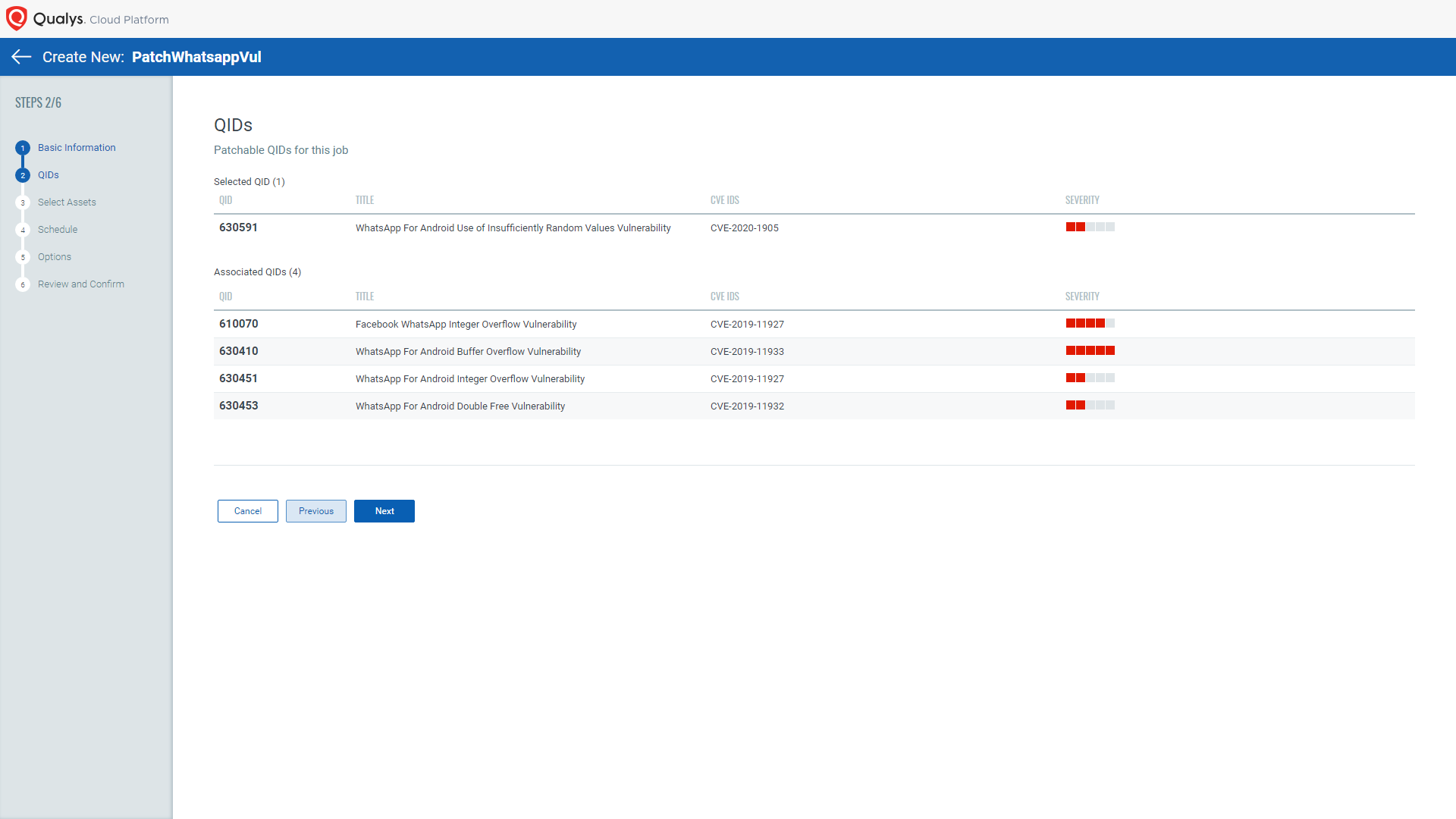
VMDR for Mobile Devices will also detect the app installed from an unknown source and its configurations (available by the end of August). The Pegasus may be introduced or installed through an unknown source in Android and ask the user for the required permission to monitor activities.
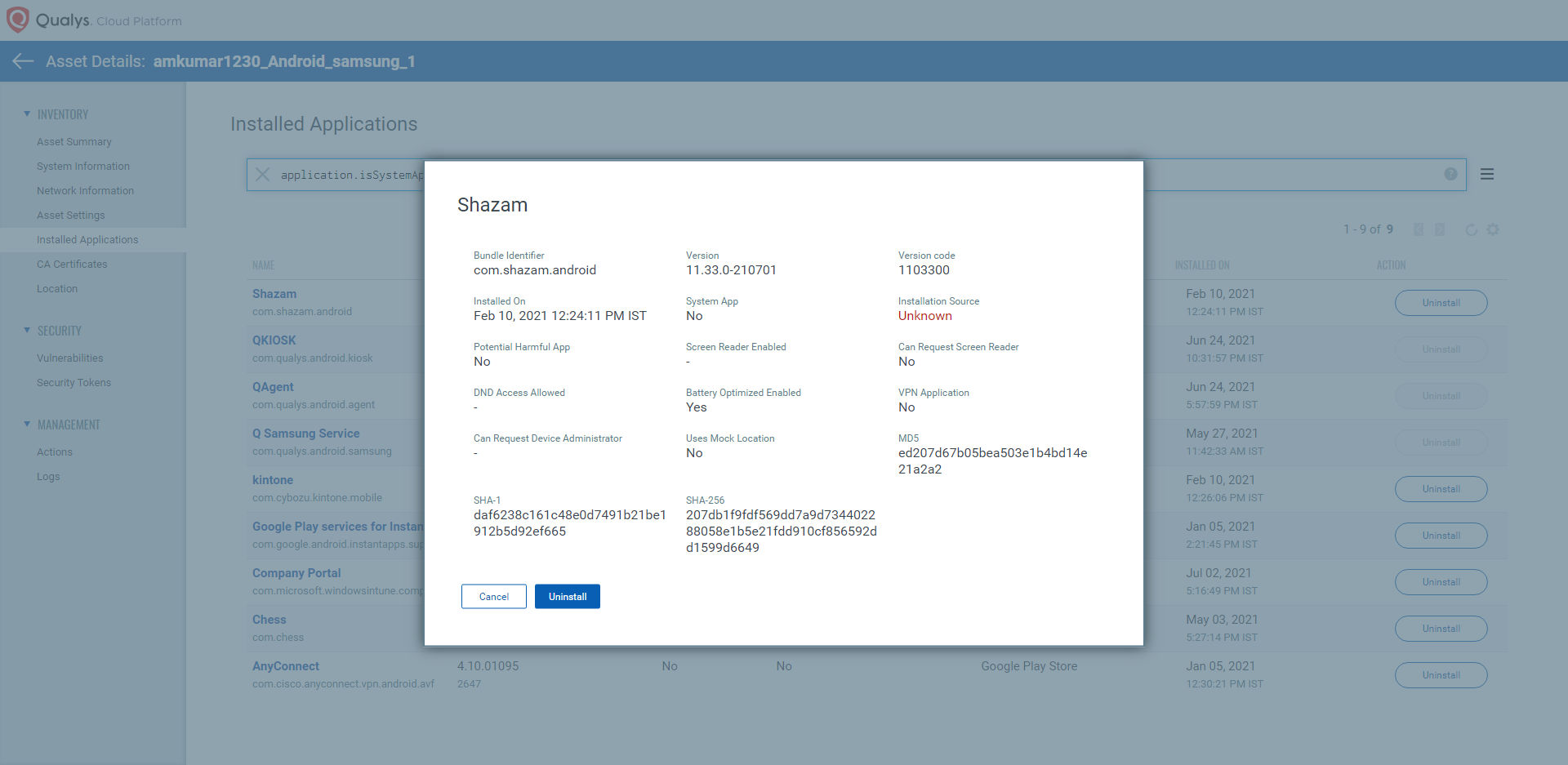
In addition, VMDR for Mobile Devices detects all vulnerabilities of Android and iOS OS vulnerabilities fixed by Apple and Google in their security updates. These vulnerabilities lead Pegasus spyware to take control of the device.
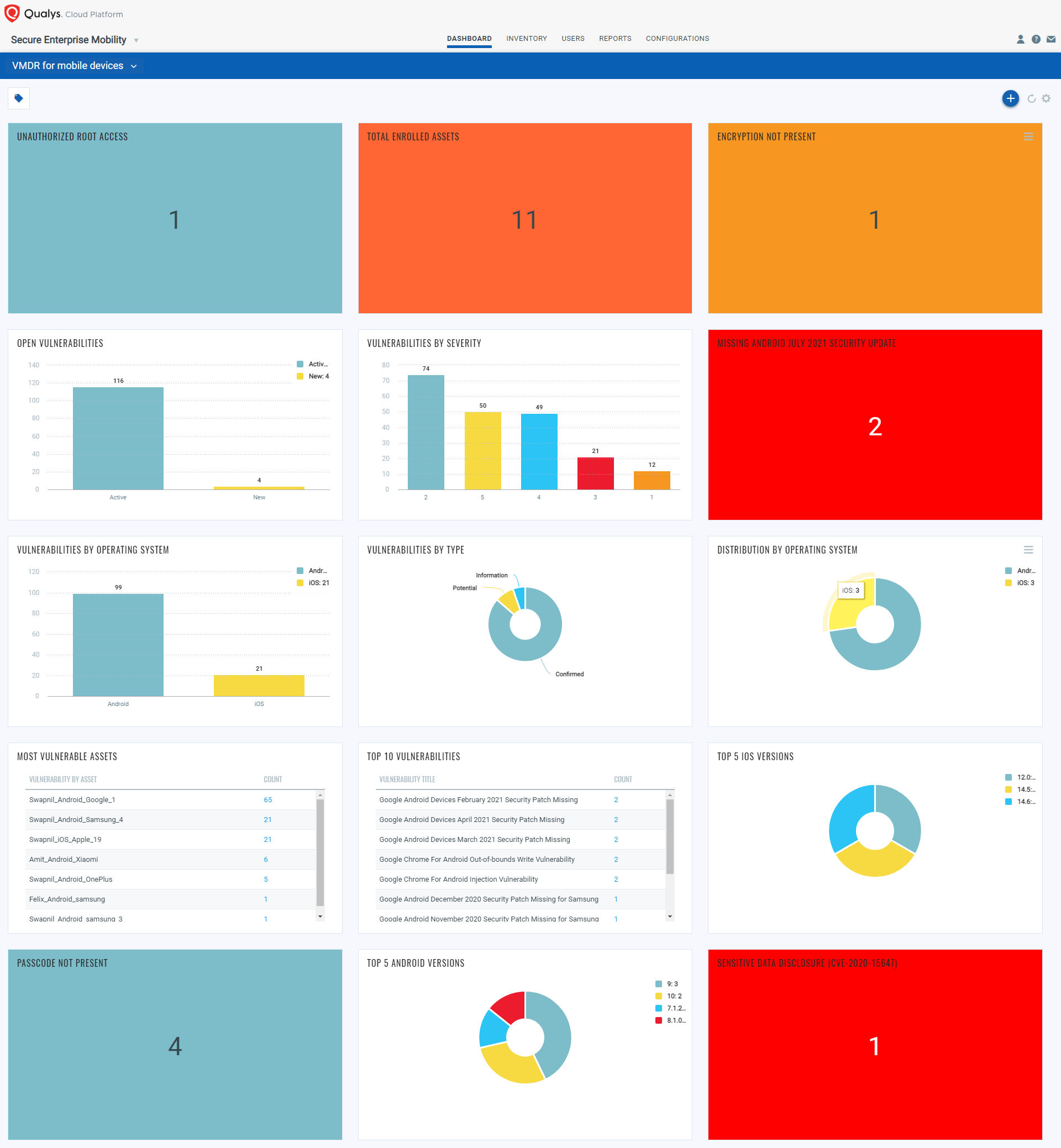
Keep an eye on the vulnerabilities detected by VMDR for Mobile Devices and take appropriate actions. That will help you to secure the devices from Pegasus spyware because the spyware can be installed only if the vulnerabilities are present on the device.
Also, if the devices are jailbroken or rooted, track them through the “Unauthorized Root Access” widget or use QQL (Qualys Query Language) – “asset.hasUnauthorizedRootAccess: Yes” to find the compromised devices.
Get Started Now
Qualys VMDR for Mobile Devices is available free for 30 days to help customers detect vulnerabilities, monitor critical device settings, and correlate updates with the correct app versions available on Google Play Store. You can try our solution by registering for a free 30-day trial.