RANSOMWARE: Ranzy Locker
On 25 October 2021, the FBI released a report documenting their findings about a ransomware variant known as Ranzy Locker. While Ranzy Locker has not been used as prolifically as Conti or Darkside, it does leverage some of the same old ransomware tricks to attack its victims. In conjunction with CISA, the FBI reported that most victims were breached via brute force attacks against the Remote Desktop Protocol (RDP). Other victims reported that the attackers used known Microsoft Exchange Server vulnerabilities and phishing to gain access. The attackers were also shown to have used a double-extortion technique that is a common practice among cybercriminals.
Ranzy Locker is a rebrand of ThunderX, a type of malware that relied on weak encryption that was, fortunately, decrypted within a month of its launch in August 2020. ThunderX was itself a rebrand of AKO Ransomware. Ranzy Locker shares a domain used for their leak site with its two ill-fated predecessors.
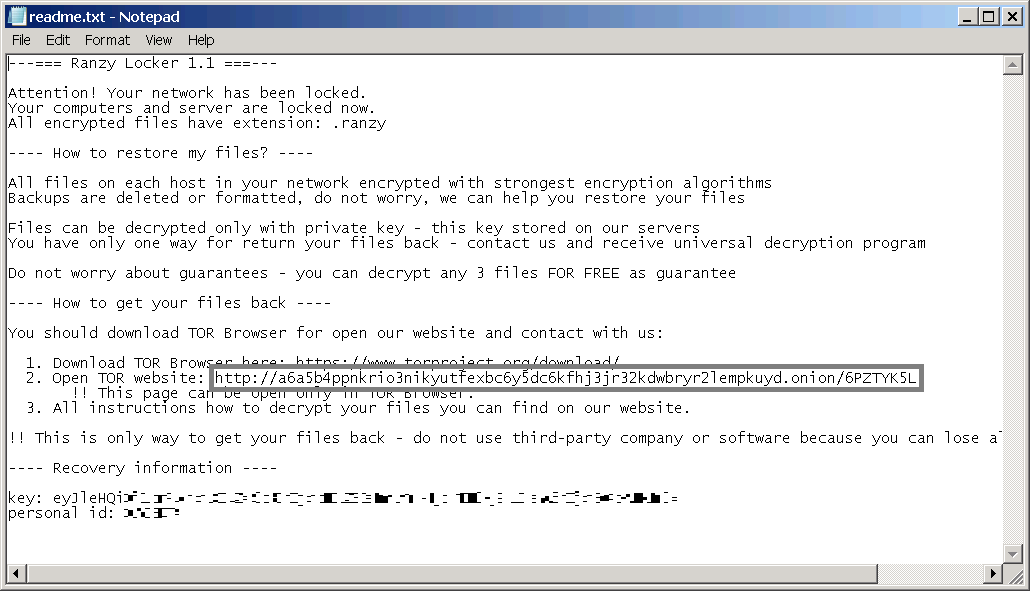
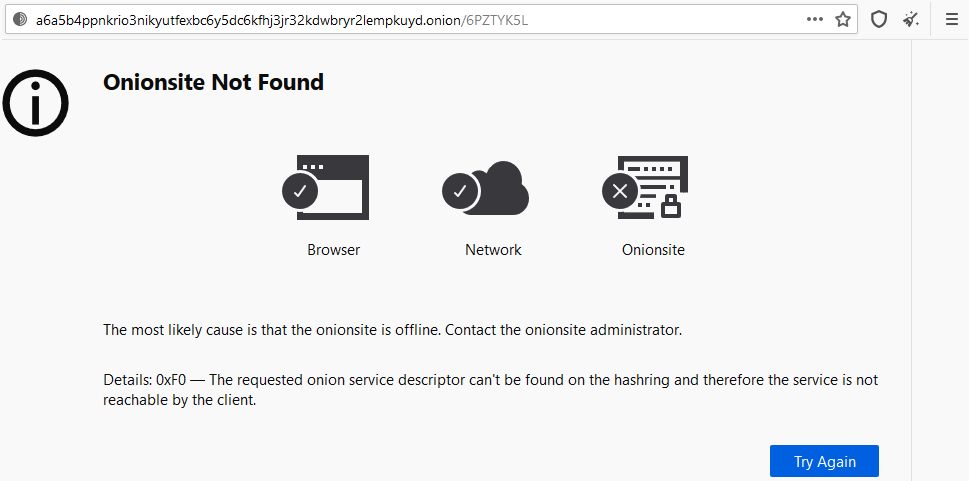
Analysis of multiple samples of Ranzy Locker revealed that the files were quickly recognized as malicious by Qualys’ EDR. Ranzy Locker samples reference a common PDB, which links them to ThunderX. The readme.txt dropped during our analysis provided a .onion link to a ransom site which was inaccessible at the time of our analysis:
Qualys’ analyst noted the following actions on the victim machine:
- Uses RmStartSession, RmRegisterResources, RmGetList, RmShutdown, and RmEndSession APIs for Windows Restart Manager to stop services from keeping critical files open and preventing encryption
- Uses AntiDebug technique via IsDebuggerPresent API to detect the presence of sandbox and analysis environment
- Uses NetShareEnum API to discover network shares
- Uses GetLogicalDrives API to get a bitmap of available disk drives
- Uses WNetGetConnectionW API to map network name for local drives
- Enumerates all available drives (e.g,. USB devices) using a brute-force approach to craft all possible drive names
- Disables shadowcopy notifications:
- wmic.exe SHADOWCOPY /nointeractive
- Deletes shadow volume copies and system backup files:
- vssadmin.exe Delete Shadows /All /Quiet
- wbadmin DELETE SYSTEMSTATEBACKUP
- wbadmin DELETE SYSTEMSTATEBACKUP -deleteoldest
- Appends .ranzy extension to rename encrypted files
- Creates readme.txt ransom note files in each directory with link to Tor-based payment site
This information can be used to create unique queries to be run in a SIEM, as adding queries for such activities as noted above can provide additional protection should signature and heuristic-based EDR fail to identify new variants of Ranzy Locker or other ransomware. For example, being alerted about the use of NetShareEnum would uncover not only use of Ranzy Locker within the corporate environment, but would also identify any spurious use of this otherwise useful API. However, to minimize false positives, it is critical to fine-tune any signatures or alerts that are created.
During the analysis Qualys reviewed the following samples:
- 393fd0768b24cd76ca653af3eba9bff93c6740a2669b30cf59f8a064c46437a2
- 90691a36d1556ba7a77d0216f730d6cd9a9063e71626489094313c0afe85a939
- ade5d0fe2679fb8af652e14c40e099e0c1aaea950c25165cebb1550e33579a79
- bbf122cce1176b041648c4e772b230ec49ed11396270f54ad2c5956113caf7b7
- c4f72b292750e9332b1f1b9761d5aefc07301bc15edf31adeaf2e608000ec1c9
During our analysis, we also found YARA rules available from malpedia, created by authors Christiaan Beek and Felix Bilstein, which can be downloaded at malpedia.caad.fkie.fraunhofer[.]de/yara/win.thunderx. Navigating to the link will download the YARA rules directly.
For more information about ransomware, read The Rise of Ransomware and join us in discussion. Following are some guidelines to help you detect, prevent, and mitigate ransomware attacks.
Important Safety Measures
- Keep strong and unique passwords for login accounts.
- Turn off the RDP if it is not used. If needed, change the RDP port to a non-standard port.
- Configure firewall in the following way: Deny access to Public IPs to important ports (in the case of Ranzy Locker, RDP port 3389).
- Allow access only to IPs which are under your control.
- Use a VPN to access the network, instead of exposing RDP to the internet; implement Two Factor Authentication (2FA) if appropriate.
- Establish a lockout policy that prevents bad actors from attempting to guess credentials.
- Create a separate network folder for each user when managing access to shared network folders.
Back Up Data Regularly
- Protect systems by backing up important files regularly and keep a recent backup copy offline and encrypt your backup (if a computer gets infected, files can be restored from the offline backup once the malware has been removed).
- Always use a combination of online and offline backup.
- Do not keep offline backups connected to your system as this data could be encrypted during a ransomware attack.
Keep Software Updated
- Always keep security software (antivirus, firewall, etc.) up to date to protect computers from new variants of malware.
- Regularly patch and update applications, software, and operating systems to address any exploitable software vulnerabilities.
- Do not download cracked/pirated software as it may contain backdoors.
- Avoid downloading software from untrusted P2P or torrent sites, which often host malicious software.
Restrict Access Privileges
- Do not provide administrative privileges to users.
- Do not stay logged in as administrator unless strictly required.
- Avoid browsing, opening documents, or other regular work activities while logged in as an administrator.
Detection & Mitigation of a Ranzy Locker Attack
Keep an eye out for attack code, and also be sure to monitor for any evidence of privilege escalation, impaired defenses or data exfiltration techniques described above. To determine whether an organization has been impacted by the ransomware, check client-facing devices and applications for any signs of unauthorized access. To identify potential data exfiltration, look for unusual patterns of outbound traffic.
Qualys Multi-Vector EDR has integrated protection capabilities to deliver holistic security to endpoints for ransomware attacks. Anti-Malware proactively protects endpoints against known threats while EDR augments detection by capturing endpoint activity and telemetry to detect and respond to unknown zero-day threats and living-off-the-land attacks.
When a symptom of a compromise or attack is discovered, Qualys EDR provides in-depth visibility and contextual enrichment for incident responders and threat hunters, giving them a complete picture of the endpoint, thus enabling root cause analysis. Qualys Multi-Vector EDR provides detection, protection, and response capabilities using a variety of capabilities: real-time anti-malware technology, anti-exploit memory protection, endpoint telemetry, and correlations that identify suspicious and malicious behavior incorporating industry-leading threat intelligence and Mitre ATT&CK tactics and techniques.
Ranzy Locker Ransomware TTP Map
| Discovery | Impact |
|---|---|
| T1497.001 – Virtualization/Sandbox Evasion: System Checks • Uses AntiDebug technique via IsDebuggerPresent API to detect presence of sandbox and analysis environment | T1489 – Service Stop • Uses RmStartSession, RmRegisterResources, RmGetList, RmShutdown, and RmEndSession APIs for Windows Restart Manager to stop services from keeping critical files open and preventing encryption |
| T1135 – Network Share Discovery • Uses NetShareEnum API to discover network shares • Uses WNetGetConnectionW API to map network name for local drives | T1490 – Inhibit System Recovery • Disables shadowcopy notifications: wmic.exe SHADOWCOPY /nointeractive • Deletes shadow volume copies and system backup files: o vssadmin.exe Delete Shadows /All /Quiet o wbadmin DELETE SYSTEMSTATEBACKUP o wbadmin DELETE SYSTEMSTATEBACKUP -deleteoldest |
| T1083 – File and Directory Discovery • Uses GetLogicalDrives API to get a bitmap of available disk drives | T1486 – Data Encrypted for Impact • Appends .ranzy extension to rename encrypted files |
| T1082 – System Information Discovery • Enumerates all available drives (e.g., USB devices) using a brute-force approach to craft all possible drive names |