The Rise of Ransomware
Table of Contents
- Ransomware Infection Vectors
- Ransomware Attacks and Exact CVEs To Prioritize for Monitoring
- Unified View of Critical Ransomware Risk Exposures
- Qualys Ransomware Risk Assessment & Remediation Service
- Continuous detection & prioritization for Ransomware-specific vulnerabilities withVMDR
- DiscoverandPrioritizeRansomware Vulnerabilities
- Discover and Mitigate RansomwareMisconfigurationssuch as SMB, Insecure RDP
- Automated Proactive & Reactive Patching for Ransomware vulnerabilities
- Ready to Learn more and see for yourself?
- Resources
- References
With most employees still working from remote locations, ransomware attacks have increased steadily since the early months of the Covid-19 pandemic. According to the FBI’s 2020 Internet Crime Report 2400+ ransomware-related incidents in 2020 resulted in a loss of about 29 million dollars. These numbers are only getting worse and do not include damage from incidents not reported to the FBI.
Ransomware attacks affect various industries worldwide, and ransomware demands continue to increase. Some recent examples include:
- Conti Ransomware: Conti ransomware is spread using spear phishing campaigns through tailored emails that contain malicious attachments or malicious links and via stolen or weak Remote Desktop Protocol (RDP) credentials.
- Netfilm Ransomware: Nefilim ransomware is distributed through exposed Remote Desktop Protocol (RDP) setups by brute-forcing them and using other known vulnerabilities for initial access, such as Citrix gateway devices.
- REvil Ransomware: REvil is a ransomware family that operates as ransomware-as-a-service (RaaS), has been linked to GOLD SOUTHFIELD, a financially motivated group, and was first identified in April 2019 according to MITRE.
- DarkSide Ransomware : DarkSide ransomware performs brute force attacks and exploits known vulnerabilities in the remote desktop protocol (RDP) to gain initial access. DarkSide ransomware, first seen in August 2020 and updated as v2.0 in March 2021, is associated with the DarkSide group and now often operates as RaaS.
- Michigan State University (May 2020) – The MSU administrators were given a week to pay an undisclosed ransom demand to decrypt their files. In case MSU officials refuse to pay or choose to restore backups, the cybercriminals were prepared to leak documents stolen from the university’s network on a special website the group is operating on the dark web.
- DearCry and Exchange vulnerabilities – DearCry ransomware attacks exploited Microsoft Exchange Server vulnerabilities CVE-2021-26855 and CVE-2021-27065. These vulnerabilities were being widely exploited before patches were available. Forcing Microsoft to release out-of-band updates.
- Colonial Pipeline – Colonial Pipeline was most likely target of ransomware attack due vulnerable, outdated version of Microsoft Exchange. Attackers potentially exploited these vulnerabilities, and as a result, Colonial Pipeline took its systems down to contain the threat, limiting gasoline supply to the east coast.
As seen above, industries ranging from education, manufacturing, electronics, research, health and more are impacted by ransomware.
To help organizations combat risks from ransomware, Qualys is introducing Ransomware Risk Assessment service. As outlined in our blog, the Qualys Ransomware Risk Assessment & Remediation service leverages the security intelligence which is curated by Qualys Research experts to map ransomware families to specific vulnerabilities, misconfigurations, and vulnerable software. The Qualys Ransomware Risk Assessment service enables organizations to:
- Get a unified view into critical ransomware exposures such as internet-facing vulnerabilities and misconfigurations, insecure remote desktop gateways (RDP), as well as detection of risky software in datacenter environment along with alerting for assets missing anti-malware solutions.
- Accelerate remediation of Ransomware exposure
swith zero-touch patching by continuously patching ransomware-vulnerabilities as they are detected. The remediation plan also enables proactive patching for prioritized software to help you keep software up to date.
Ransomware Infection Vectors
Although cyber criminals use a variety of techniques to infect victims with ransomware, the most common means of infection are:
- Remote Desktop Protocol (RDP) vulnerabilities: RDP allows individuals to see and control the system remotely. It is a very common practice in organizations as it provides easy access to systems remotely. Once cybercriminals have RDP access, they can deploy malicious software on the system, making it inaccessible to legitimate users unless the victim pays the demanded ransom. Shodan search shows currently open and potentially vulnerable RDP services on the internet, and you can buy RDP access for as low as US$3.
- Email phishing campaigns: Email is a prevalent medium to get malware into the target environment. Cybercriminals use emails to send malicious links to deploy malware on recipients’ machines. It allows cybercriminals to steal sensitive data without breaking through network security and is very common among cybercriminals.
- Software vulnerabilities: Software vulnerabilities are even more prevalent than phishing. Client- and server-side vulnerabilities allow criminals to take advantage of security weaknesses in widely used software programs, gain control of victim systems, and deploy ransomware. Vulnerabilities in VPN systems such as Pulse Secure VPN and Fortinet are common targets as well.
Ransomware Attacks and Exact CVEs To Prioritize for Monitoring
As mentioned above known vulnerabilities and weakness are one of the top infection vectors.
Qualys research team has performed extensive research on 36 prevalent ransomware families and have mapped them to 64 CVEs and the 247 QIDs that can detect them. The following is just a sample list of some of most widely used ransomware in the attacks along with the CVEs leveraged to infect systems.
| Ransomware | Description | CVE (s) | QID (s) |
|---|---|---|---|
| Conti | The Conti ransomware strain will not only encrypt important files but will also exfiltrate them to a location controlled by the attacker. This method of extortion-ware is used to force victims to pay the ransom in order to avoid the sensitive data from being leaked. Conti operators are known to use well-known hacking tools such as Mimikatz and Cobalt Strike leading up to the encryption of files | CVE-2020-1472, CVE-2021-34527, CVE-2017-0143, CVE-2017-0144, CVE-2017-0145 | 91680, 91668, 91785, 91345, 91360 |
| Teslacrypt, PrincessLocker | TeslaCrypt ransomware was uploaded to VirusTotal in November 2014 but was more widely spread in early 2015 and continues to evolve. TeslaCrypt encrypts the files using AES-256 algorithm until the victim pays the ransom in either Bitcoin or Cash Cards. | CVE-2013-2551, CVE-2015-8651 | 168351, 168350, 124422, 168341, 168340, 100271, 124421 |
| Locky, Cerber | Cerber ransomware is ransomware-as-a-service (RaaS), meaning an attacker can distribute the licensed copy of this ransomware over the internet and pay commissions to the developer. | CVE-2016-1019 | 256924, 256922, 177873, 176784, 296029, 296028, 170815, 170724, 170711, 170365, 256256, 170264, 236438, 170119, 256214, 170052, 276628, 236342, 157445, 169942, 169941, 169923, 276572, 169854, 169853, 176004, 196742, 196725, 370320, 276455, 175965, 168848, 168813, 168792, 168696, 168694, 168594, 100282, 124879, 124872 |
| WannaCry, Badrabbit | The WannaCry ransomware — formally known as WanaCrypt0r 2.0 — spreads using an exploit called EternalBlue for a Windows OS vulnerability that Microsoft patched in March 2017. | CVE-2017-0145 | 91361, 91360, 91359, 91347, 91345 |
| DearCRy, BlackKingdom | DearCry takes advantage of compromised Microsoft Exchange Servers with vulnerability CVE-2021-26855. When exploited, cybercriminals gain initial access to the Exchange Server and then install web shells. | CVE-2021-26855 | 50107, 50108 |
Unified View of Critical Ransomware Risk Exposures
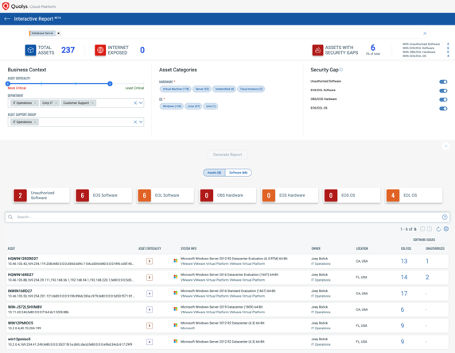
It is a daunting task to get a unified view of multiple critical ransomware exposures together such as internet-facing vulnerabilities, misconfigurations as well as unauthorized software. Qualys Ransomware Risk Assessment & remediation service dashboard enables security teams to see all the internet-facing assets that are exposed to ransomware related vulnerability or misconfiguration and take needed actions in the most impactful way. It also enables users to measure and track their effectiveness at addressing vulnerabilities or misconfigurations before they are used for ransomware attacks.
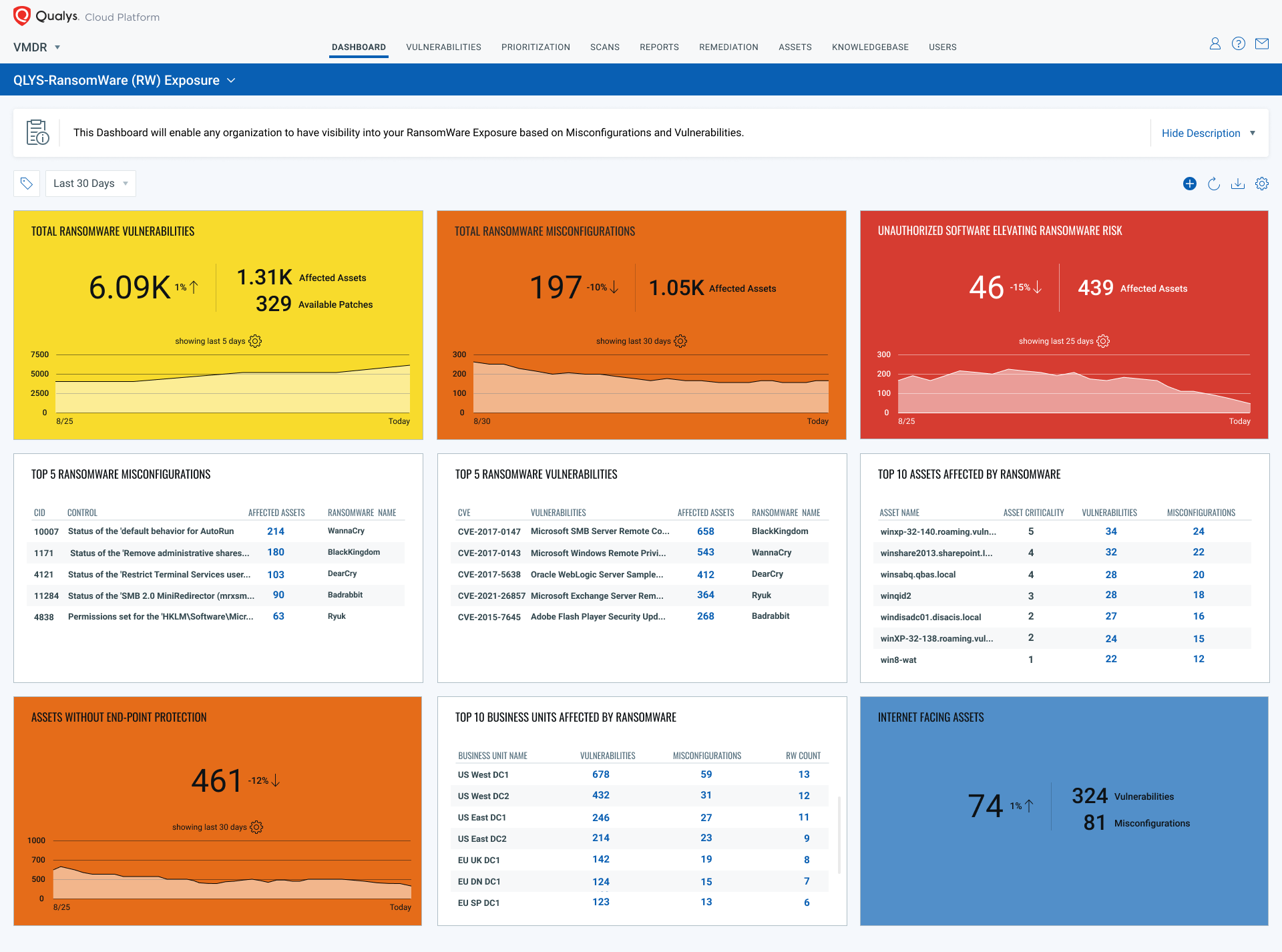
In addition, organizations should implement a good cyber hygiene program to scan vulnerabilities, discovery misconfigurations regularly with sufficient detection capabilities such as QIDs enabled, as well as an efficient automated process to deploy important security patches on targeted assets quickly with the scalability needed.
Qualys Ransomware Risk Assessment & Remediation Service
Qualys provides an all-in-one solution to discover, assess, prioritize, monitor, and patch critical vulnerabilities in real time and across your global hybrid-IT landscape. The following sections provide an overview of each of the critical components from Qualys product portfolio and how they can be uniquely valuable in the effort of combatting ransomware attacks.
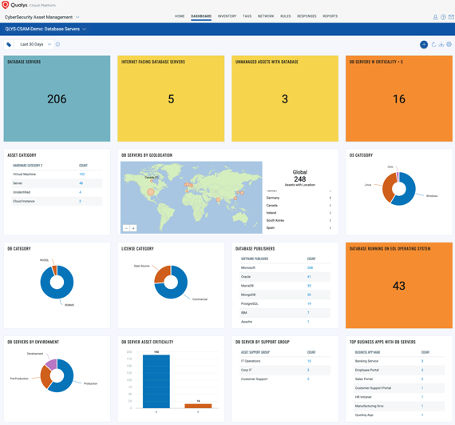
Detect your critical data assets & monitor security blind-spots with CyberSecurity Asset Management (CSAM)
Enables organizations to automatically discover every asset in their environment, including unmanaged assets appearing on the network, inventory all hardware and software, and classify and tag critical assets.
Discover, Inventory and Categorize assets
It is important to know your blind spots to protect against ransomware. Use CSAM to discover all assets, including the ones that are exposed to the internet as well as unknown/unmanaged assets that are connecting to your network.
CSAM automatically organizes your assets by their functional category by analyzing their hardware and installed software. Extends your inventory by incorporating key business information from your CMDB, such as status, environment, ownership, support groups, and business criticality.
Monitor & detect at-risk assets and applications – Assets missing Anti-virus, running unauthorized software
CSAM enriches your asset inventory with in-context, relevant information to help you detect at-risk assets and applications. You can identify and set alerts for assets that are running unauthorized software or are not using anti-virus/endpoint security tools.
- Unauthorized software should be removed to quickly reduce unnecessary attack vectors. With CSAM you can easily define rules to monitor unauthorized software installations.
- Identify assets missing required security software, such as Antivirus and Endpoint Protection.
- Identify EOL/EOS software, which can be used as ransomware attack vectors. End-of-Support software is one of the first things hackers look to exploit because they know publishers are no longer providing security updates and patches.
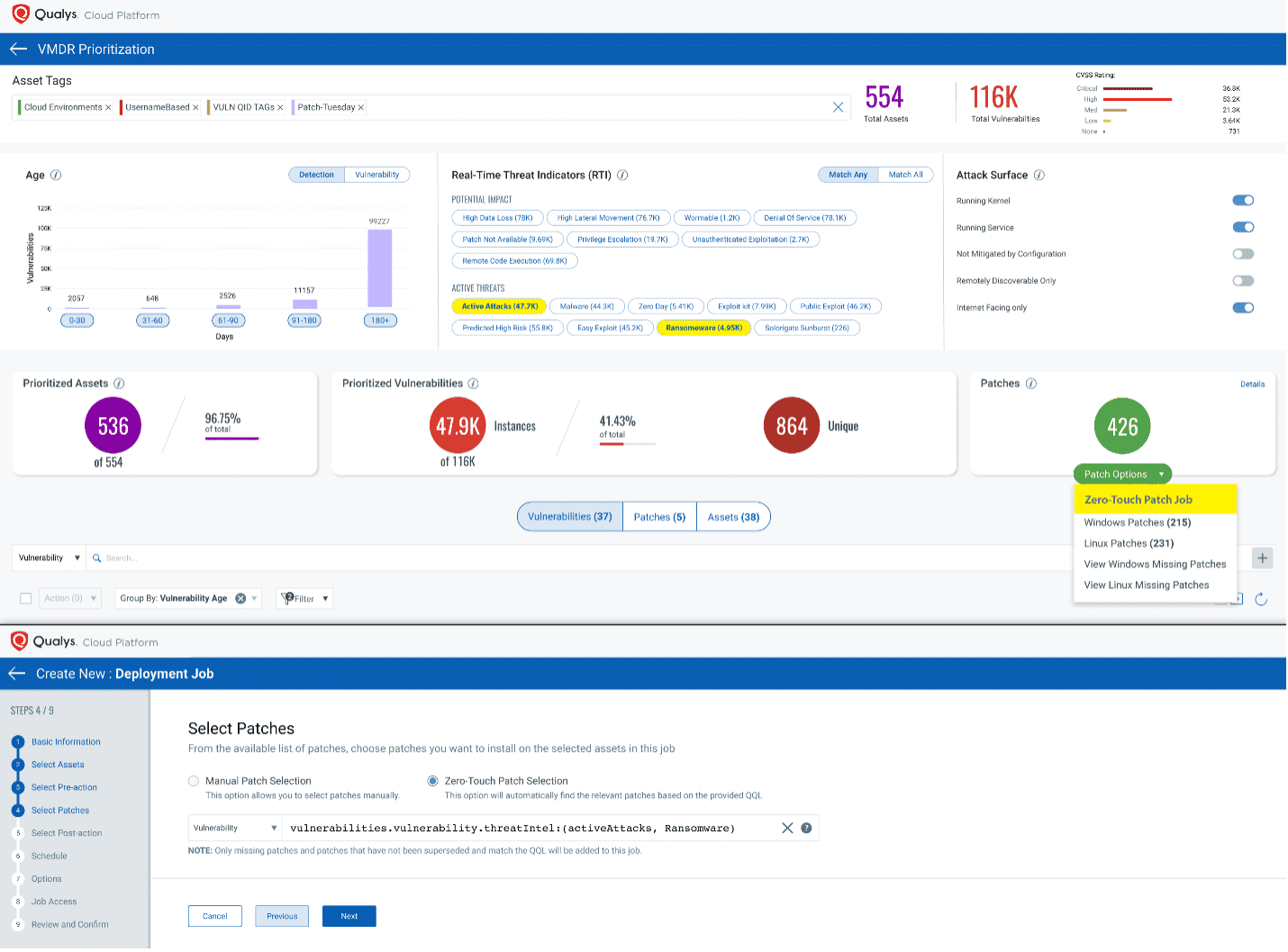
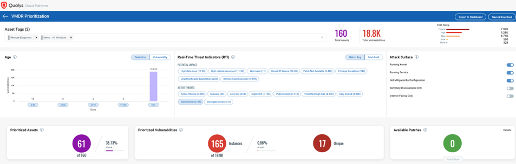
Continuous detection & prioritization for Ransomware-specific vulnerabilities with VMDR
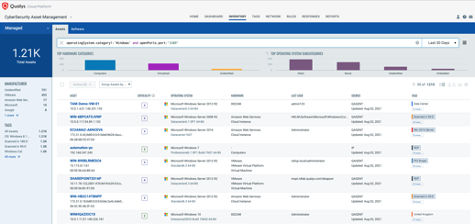
The first step in managing vulnerabilities and reducing risk is identification of assets. Qualys VMDR makes it easy to identify systems with open ports. For example, hosts with Remote Desktop Protocol (RDP) enabled.
operatingSystem.category1:`Windows` and openPorts.port:`3389`
Once the hosts with RDP are identified, they can be grouped together with a ‘dynamic tag’, let us say – “RDP Asset”. This helps in automatically grouping existing hosts with this vulnerability as well as any new hosts that spin up in your environment. Tagging makes these grouped assets available for querying, reporting and management throughout the Qualys Cloud Platform.
Discover and Prioritize Ransomware Vulnerabilities
Now that hosts with “RDP” are identified, you want to detect which of these assets have flagged this vulnerability. VMDR automatically detects new vulnerabilities like Windows RDP, Exchange Server vulnerability and more based on the always updated Knowledgebase.
You can see all your impacted hosts for this vulnerability tagged with the ‘Ransomware asset tag in the vulnerabilities view by using this QQL query:
vulnerabilities.vulnerability.threatIntel.ransomware: true
Or
vulnerabilities.vulnerability.ransomware.name:WannaCry
This will return a list of all impacted hosts.
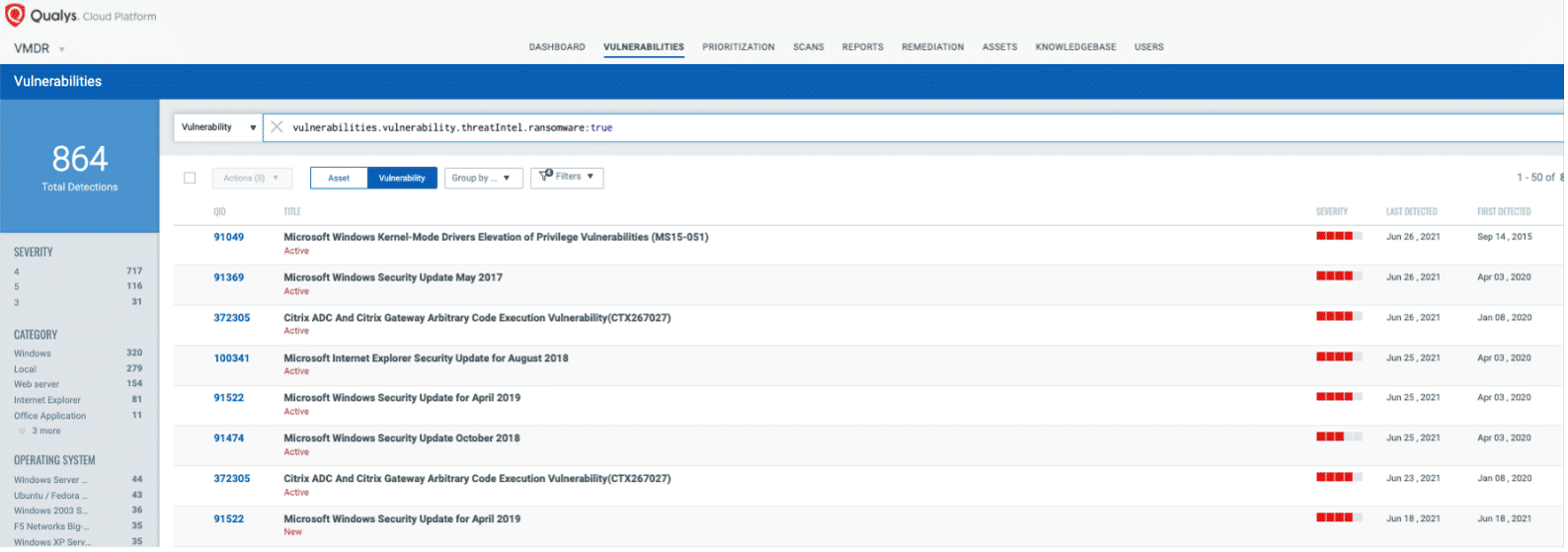
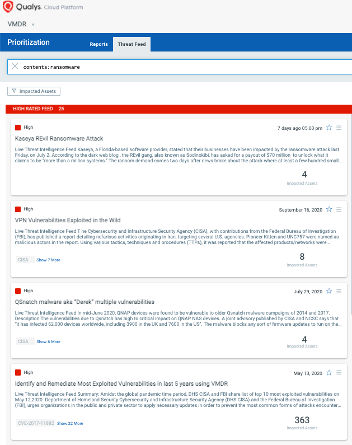
Using VMDR prioritization, the ransomware vulnerabilities can be easily prioritized using “Ransomware” Real-Time Threat Intelligence:
VMDR also enables you to stay on top of these threats proactively via the ‘live threat feed’ provided for threat prioritization. With ‘live feed’ updated for all emerging high and medium risks, you can clearly see the impacted hosts against threats.
Simply click on the impacted assets for the “Ransomware” feeds to see the vulnerability and impacted host details.
Qualys provides the ability for a Unified Dashboard approach with the key metrics across all Apps providing key metrics against your overall security posture against Ransomware Related data points such as:
- Ransomware Related vulnerabilities
- Unauthorized Software
- Misconfigurations leveraged by ransomware
- Internet Facing Hosts with RDP vulnerabilities and many more…
The Unified Dashboard enabled you to track your ransomware exposure, against impacted hosts, their status, and overall management in real-time.
Discover and Mitigate Ransomware Misconfigurations such as SMB, Insecure RDP
Qualys Policy Compliance provides the Ransomware Best Practices policy which contains the critical controls mapped to MITRE ATT&CK mitigations and tactics recommended by CISA and best practices published by Fireye Mandiant. These mitigations are effective across top techniques and can potentially reduce the risk of ransomware attacks. These critical controls can limit attacker initial access and the lateral movement around the network.
As organizations look to prevent the attacks from happening in the first place, security teams should focus on implementing these controls proactively and effectively across all assets to reduce the risk. By automating the configuration assessment with Qualys Policy Compliance, organizations can ensure golden images to conform to security baselines and prevent images from ever having misconfigurations and identify configurations drifts to prevent security risks.
Mitigation or Important Precautionary Measures and Controls
The Qualys internal research team has identified top five security measures and configuration controls; a security team should consider for their organization to prevent business interruption from a ransomware attack. Research is based on best practices published by FireEye (Mandiant), Cybersecurity and Infrastructure Security Agency (CISA), and CISA MS-ISAC. Policies/technical controls should be implemented. These configuration checks go beyond typical CIS or DISA benchmarks.
- Enforce Password Policies. e.g.
- Minimum password age should be set,
- Password complexity requirements should be enabled.
- Enforce password history restrictions.
- Employ best practices for use of Remote Desktop protocol e. g
- Disable RDP services if not necessary.
- Close unused RDP ports, Audit the network for systems using RDP.
- Apply Multifactor authentication.
- Disable or block Server Message Block (SMB) protocol and remove or disable outdated versions of SMB.
- RDP account controls
- Employ Network security and Firewalls e.g.
- Enforce firewall policy rules.
- Deny all rule and allow only required networks, access.
- Common ports and protocols that should be blocked.
- Enforce Account Use Policies. E.g.
- Apply account lockouts after a specified number of attempts.
- Admin approval requirements.
- Apply UAC restrictions on network logons etc.
- Least privileges are assigned to users.
- Keep Software Updated
- Ensure automatic updates are enabled.
- Patches, software’s should be installed and updated in a timely manner which includes operating systems, applications, etc.
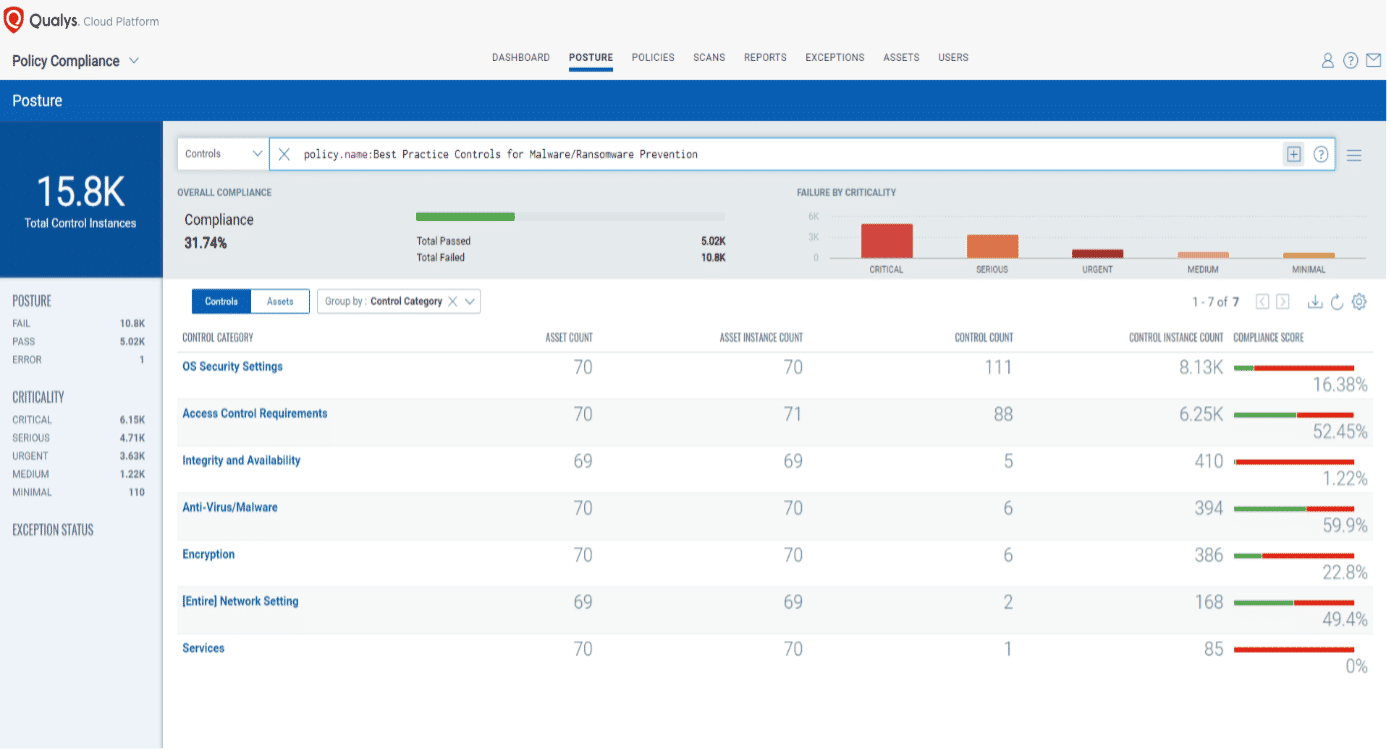
Qualys research has mapped misconfigurations to the relevant MITRE ATTACK techniques (summarized in the table below) to define 237 configuration checks across five security areas such as RDP hardening, user controls, network, protocol and port configuration security, share and password policies and software update policies, essentially helping organizations proactively prevent 20 attack techniques leveraged in ransomware attacks.
TTP Map
| Initial Access (TA0001) | Credential Access (TA0006) | Privilege Escalation (TA0004) | Execution (TA0002) | Defense Evasion (TA0005) | Lateral Movement (TA0008) | Command and Control (TA0011) | Impact (TA0040) |
| Valid Accounts (T1078) | Brute Force(T1110) | Abuse Elevation Control Mechanism (T1548) | Scheduled Task / Job (T1053) | Impair Defenses (T1562) | Remote Services (T1021) | Non-Application Layer Protocol (T1095) | Data Manipulation: Transmitted Data Manipulation (T1565.002) |
| Supply Chain Compromise (T1195) | Abuse Elevation Control Mechanism: Bypass User Account Control (T1548.002) | Inter-Process Communication (T1559) | Trusted Developer Utilities Proxy Execution (T1127) | Exploitation of Remote Services (T1210) | |||
| Supply Chain Compromise: Compromise Software Dependencies and Development Tools (T1195.001) | Access Token Manipulation (T1134) | Remote Services (T1021) | |||||
| Unsecured Credentials (T1552) | Remote Services: Remote Desktop Protocol (T1021.001) | ||||||
| Remote Services: Remote Desktop Protocol (T1021.002) | |||||||
| Remote Service Session Hijacking (T1563) |
Automated Proactive & Reactive Patching for Ransomware vulnerabilities
To keep the ransomware vulnerability patches always up to date on your assets, we strongly encourage users to take advantage of Qualys Zero-Touch Patch that allows users to automatically patch new ransomware-related vulnerabilities which are actively used in attacks. Qualys Zero-Touch Patch enables businesses to patch and address at least 97% of the ransomware related vulnerabilities. Faster and at scale! For more information on Qualys automatic patch capabilities, refer to blog Automate Vulnerability Remediation with Proactive Zero-Touch Patch.
Following patch management best practices, using Qualys Patch Management, allows organizations to proactively remediate vulnerabilities related to ransomware and therefore minimize ransomware attacks in their environment. A simple and efficient way to use Qualys patch management to remediate ransomware related vulnerabilities is to leverage the VMDR prioritization report, as described in a previous section, this report can be used to detect assets with ransomware related vulnerabilities. The tight integration between Qualys VMDR and Patch Management allows customers to add those ransomware related vulnerabilities directly from the prioritization report into a patch job. The Qualys engine will automatically map the selected vulnerabilities to the relevant patches, in the customer’s environment, that are required to remediate the vulnerabilities. This will allow IT teams to focus on deploying those patch jobs without the need to worry about researching vulnerabilities and manually finding the relevant patches for those vulnerabilities.
Ready to Learn more and see for yourself?
Join the webinar, Combating Risk from Ransomware Attacks, to discuss the current state of ransomware and prevention techniques. Webinar October 21, 2021, at 10am Pacific. Sign up now!
Resources
- Press Release
- Ransomware Assessment Service Video
- Research Powered Qualys Ransomware Risk Assessment & Remediation service
- Try Qualys Ransomware Risk Assessment Service
- Learn more about the research and see the Qualys Ransomware Risk Assessment & Remediation service in action by attending the webinar
Very complete article! During the pandemic, ransomware attacks became more and more common. Every one working with data should be aware about it. This article explains it very well, very useful for anyone interested in cyber security.