Russia-Ukraine Crisis: How to Strengthen Your Security Posture to Protect against Cyber Attack, based on CISA Guidelines
Table of Contents
- Protecting Customer Data on Qualys Cloud Platform
- Urgent: Assess and Heighten Your Security Posture
- Step 1: Monitor Your Shodan/Internet Exposed Assets
- Step 2: Detect, Prioritize and Remediate CISAs Catalog ofKnown Exploited Vulnerabilities
- Step 3: Protect Your Cloud Services and Office 365
- Step 4: Continuously Detect any Potential Threats and Attacks
- Take Action to Learn More about How to Strengthen Your Defenses
CISA has created Shields Up as a response to the Russian invasion of Ukraine. Qualys is responding with additional security, monitoring and governance measures. This blog details how and what our enterprise customers can do to immediately strengthen their security posture and meet CISA’s recommendations.
With the invasion of Ukraine by Russia, the U.S. Cybersecurity & Infrastructure Security Agency (CISA) has created a program titled Shields Up and provided specific guidance to all organizations. The Russian government has used cyber operations as a key component of force projection in the past and has targeted critical infrastructure to destabilize a governments’ response capabilities. Critical infrastructure can include supply chain (including software supply chain), power, utilities, communications, transportation, and government and military organizations.
Protecting Customer Data on Qualys Cloud Platform
Qualys is strongly committed to the security of our customers and their data. In addition to proactive risk mitigation with continuous patch and configuration management, we continually monitor all our environments for any indication of active threats, exploits and compromises. We hold our platforms to the highest security and compliance mandates like FedRAMP. However, given the heightened risk environment around the globe, the Qualys Security and Engineering teams have been at a heightened state of vigilance in recent weeks. We continuously monitor our internal systems in this amplified threat environment. We are working with our security partners to access the latest threat intel. We have implemented additional security, monitoring, and governance measures involving our senior leadership and are committed to ensuring that the Qualys Cloud Platform remains available and secure to support the enterprises we serve worldwide.
Urgent: Assess and Heighten Your Security Posture
Based on high-level guidelines provided by CISA, Qualys is recommending all organizations to establish the following actionable steps to adopt heightened cybersecurity posture to protect critical assets.
There are 4 steps necessary to strengthen security posture per CISA’s Shields Up guidance:
- Step 1: Know Your Shodan/Internet Exposed Assets Automatically
- Step 2: Detect, Prioritize, and Remediate CISA’s Catalog of Known Exploited Vulnerabilities
- Step 3: Protect Your Cloud Services and Office 365 Environment
- Step 4: Continuously Detect a Potential Intrusion
Implement CISA’s Shields Up Guidance
Step 1: Monitor Your Shodan/Internet Exposed Assets
Discover and protect your external facing assets
An organization’s internet-facing systems represent much of their potential attack surface. Cyber threat actors are continuously scanning the internet for vulnerable systems to target attacks and campaigns. Often hackers find this information readily available on the dark web or in plain sight on internet search engines such as Shodan.io.
Inventory all your assets and monitor your external attack surface. Qualys CyberSecurity Asset Management (CSAM) provides comprehensive visibility of your external-facing IT infrastructure by natively correlating asset telemetry collected by Qualys sensors (e.g. Internet Scanners, Cloud Agents, Network Passive Sensors) and key built-in integrations such as Shodan.io and Public Cloud Providers.
One of the biggest risks is unknown unknowns. These gaps in visibility happen for many reasons – including shadow IT, forgotten websites, legacy services, mergers & acquisitions (M&A), or simply because a development team exposes an application or database without informing their security team.
CSAM enables you to continuously discover these blind spots and assess their security and compliance posture.
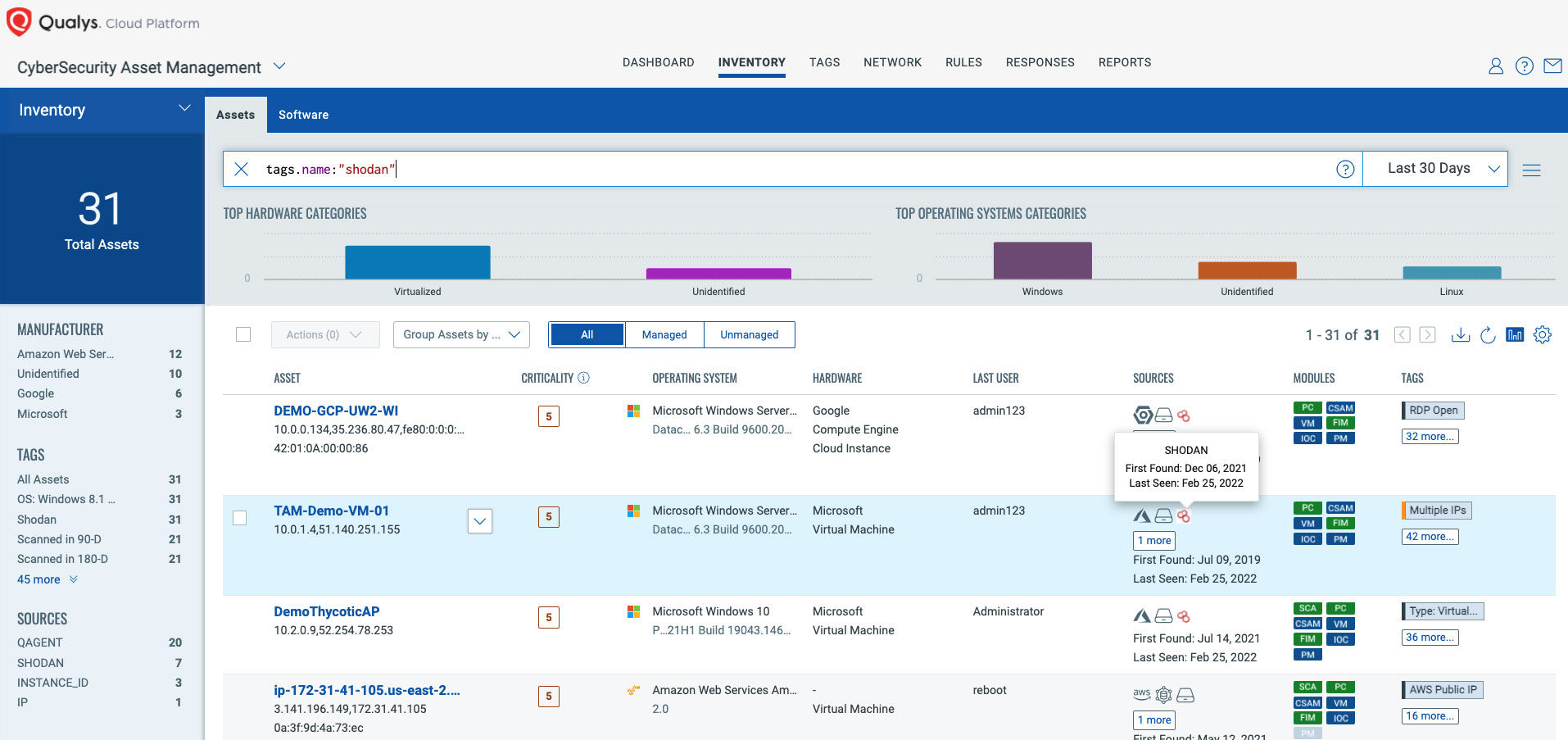
Monitor Industrial Control Systems and Operational Technology
Network segmentation traditionally kept Industrial Control Systems air-gapped. However, the acceleration of digital transformation has enabled more of these systems to connect with corporate as well as external networks, such as device vendors and Industrial IoT platforms. Further, the majority of Operational Technology utilizes legacy, non-secure protocols.
Build full visibility of your critical infrastructure, network communications, and vulnerabilities with Qualys Industrial Control Security (ICS).
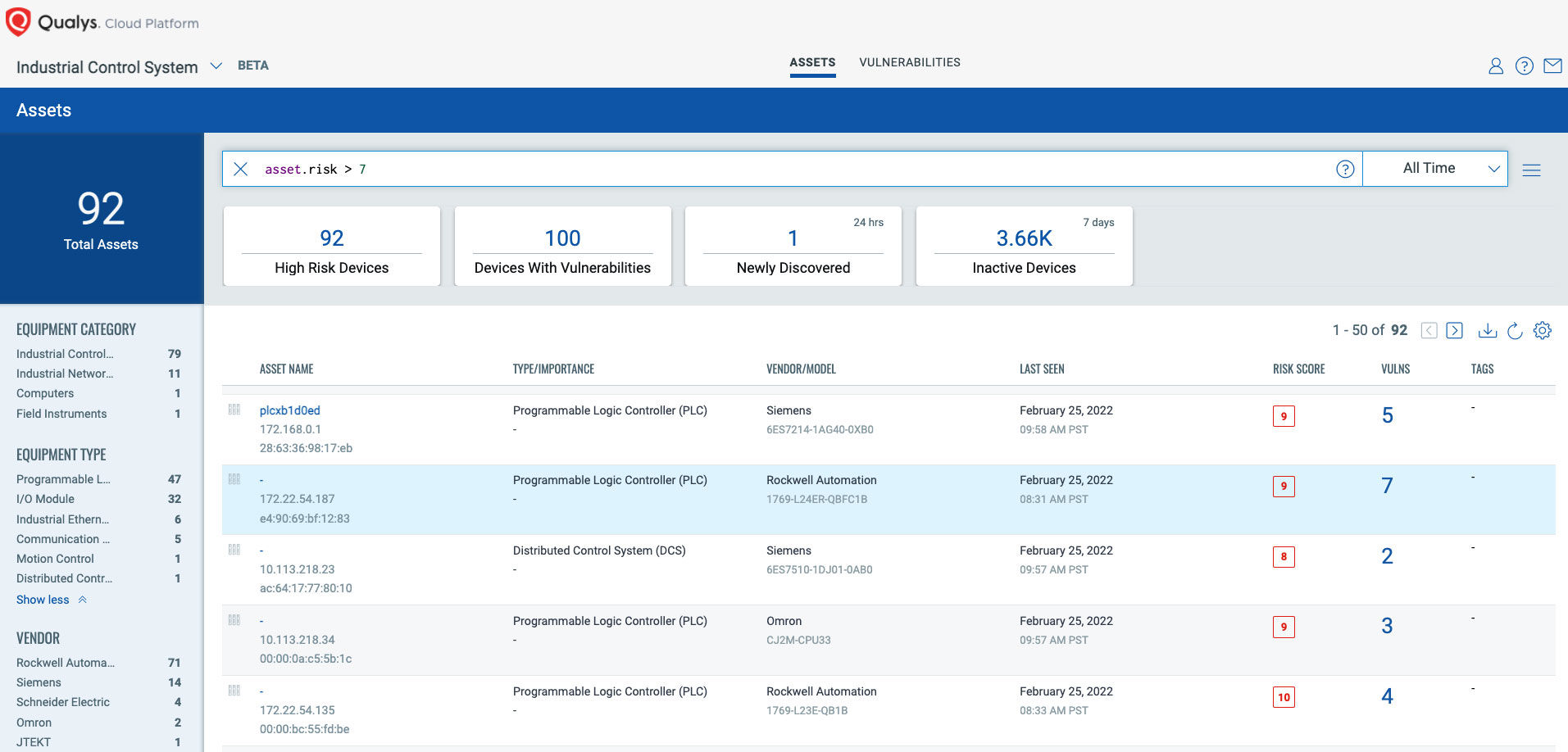
Detect and disable all non-essential ports and protocols, especially on internet exposed assets
Inventory your internal and external-facing assets, report open ports, and detected services on each port. Qualys CSAM supports extensive query language that enables teams to report and act on detected external facing assets that have a remote-control service running (for example Windows Remote Desktop).
Ensure all systems are protected with up-to-date antivirus/anti-malware software
Flag assets within your inventory that are missing antivirus, or with signatures that are not up to date. CSAM allows you to define Software Rules and assign required software on a specific scope of assets or environment. For example, all database servers should have antivirus and a data loss prevention agent.

Verify that your antivirus/anti-malware engine is up to date with the latest signatures.
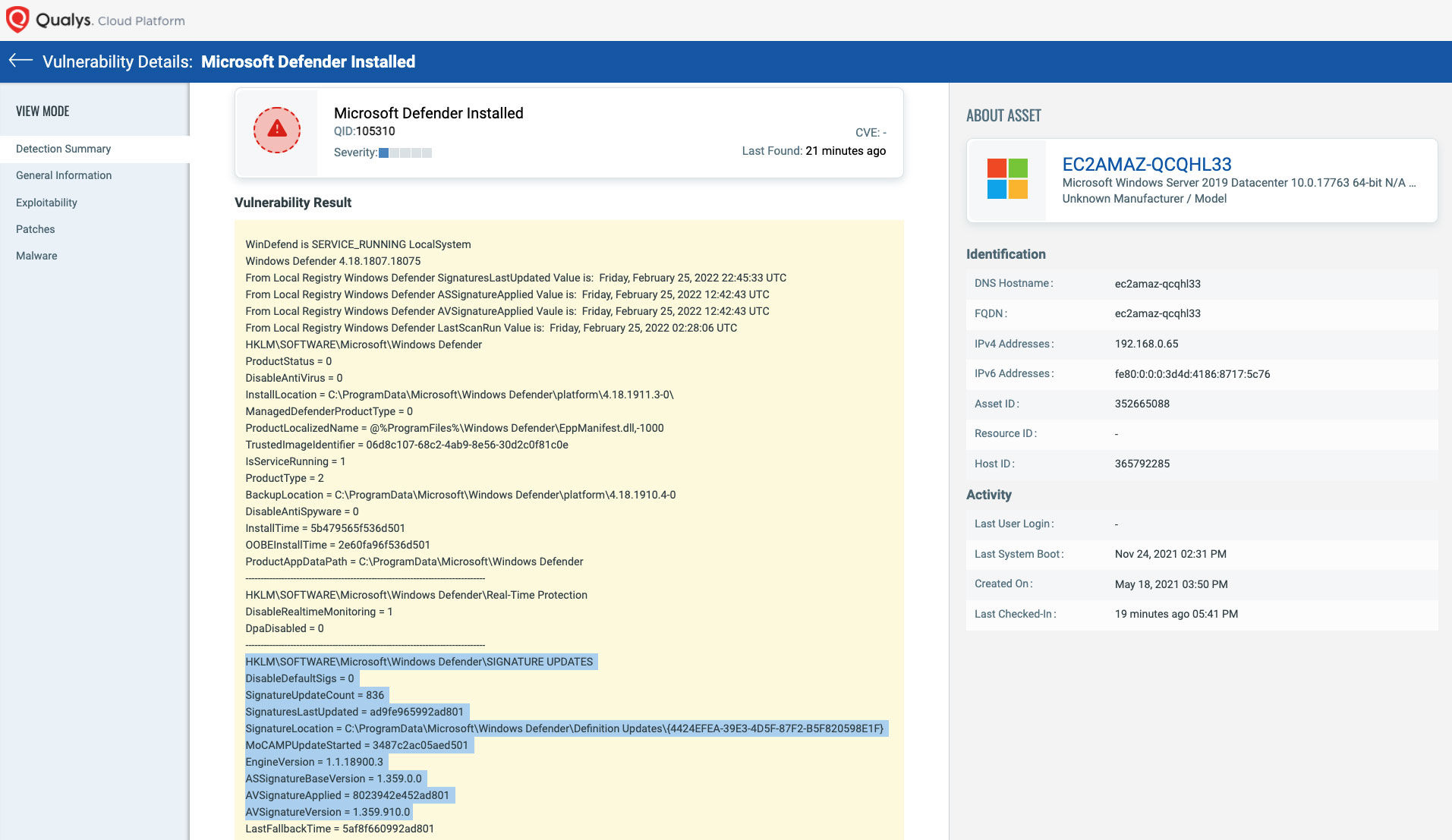
For devices missing antivirus or anti-malware, Qualys Multi-Vector EDR with Integrated Anti-Malware can be easily enabled wherever the Qualys Cloud Agent is installed to provide immediate threat protection. In addition to basic anti-malware protection, Multi-Vector EDR will monitor endpoint activity to identify suspicious and malicious activity that usually bypasses traditional antivirus such as Living-off-the-Land attacks as well as MITRE ATT&CK tactics and techniques.
Step 2: Detect, Prioritize and Remediate CISA’s Catalog of Known Exploited Vulnerabilities
Qualys Researcher analyzed all the 300+ CVEs from CISA known exploited vulnerabilities and mapped them to the Qualys QIDs. Many of these CVEs have patches available for the past several years. A new “CISA Exploited” RTI was added to VMDR to help customers create vulnerabilities reports that are focused on CISA exploited vulnerabilities. Customers can use the VMDR vulnerabilities page or VMDR prioritization page and filter the results to focus on all the “CISA Exploited” open vulnerabilities in their environment.
Following are some of the critical vulnerabilities cataloged by CISA, as specifically known to be exploited by Russian state-sponsored APT actors for initial access include:
| CVE | QID | Title | Release Date | CVSS_V3 |
|---|---|---|---|---|
| CVE-2018-13379 | 43702 | Fortinet Fortigate (FortiOS) System File Leak through Secure Sockets Layer (SSL) Virtual Private Network (VPN) via Specially Crafted Hypertext Transfer Protocol (HTTP) Resource Requests (FG-IR-18-384) | 9/12/2019 | 9.8 |
| CVE-2019-2725 | 87386 | Oracle WebLogic Server Remote Code Execution Vulnerability (Oracle Security Alert Advisory – CVE-2019-2725) | 4/27/2019 | 9.8 |
| CVE-2019-7609 | 371687 | Kibana Multiple Security Vulnerabilities (ESA-2019-01,ESA-2019-02,ESA-2019-03) | 4/18/2019 | 10 |
| CVE-2019-10149 | 50092 | Exim Remote Command Execution Vulnerability | 6/5/2019 | 9.8 |
| CVE-2019-11510 | 38771 | Pulse Connect Secure Multiple Security Vulnerabilities (SA44101) | 8/6/2019 | 10 |
| CVE-2019-19781 | 372305 | Citrix ADC And Citrix Gateway Arbitrary Code Execution Vulnerability(CTX267027) | 12/23/2019 | 9.8 |
| CVE-2020-0688 | 50098 | Microsoft Exchange Server Security Update for February 2020 | 2/12/2020 | 9.8 |
| CVE-2020-4006 | 13215 | VMware Workspace One Access Command Injection Vulnerability (VMSA-2020-0027) | 12/7/2020 | 9.1 |
| CVE-2020-5902 | 38791 | F5 BIG-IP ASM,LTM,APM TMUI Remote Code Execution Vulnerability (K52145254) (unauthenticated check) | 7/5/2020 | 9.8 |
| CVE-2020-14882 | 87431 | Oracle WebLogic Server Multiple Vulnerabilities (CPUOCT2020) | 10/21/2020 | 9.8 |
| CVE-2021-26855, CVE-2021- 26857 CVE-2021-26858, CVE-2021-27065 | 50107 | Microsoft Exchange Server Remote Code Execution Vulnerability (ProxyLogon) | 3/3/2021 | 9.8 |
See the full list of CISA known exploited vulnerabilities.
Remediate CISA recommended catalog of exploited vulnerabilities
For all CISA cataloged vulnerabilities known to be exploited by Russian state-sponsored actors, Qualys Patch Management customers can create a patch and configuration fix jobs to remediate the risk of all vulnerabilities directly from the VMDR console. Qualys Patch Management maps “CISA Exploited” vulnerabilities detected in the environment to the relevant patches required to remediate those vulnerabilities by downloading the patches without needing to go through the VPN. Customers may use Zero Touch patching to automate the process and ensure all CISA exploited vulnerabilities are automatically fixed including the new vulnerabilities added to the CISA catalog in the future.
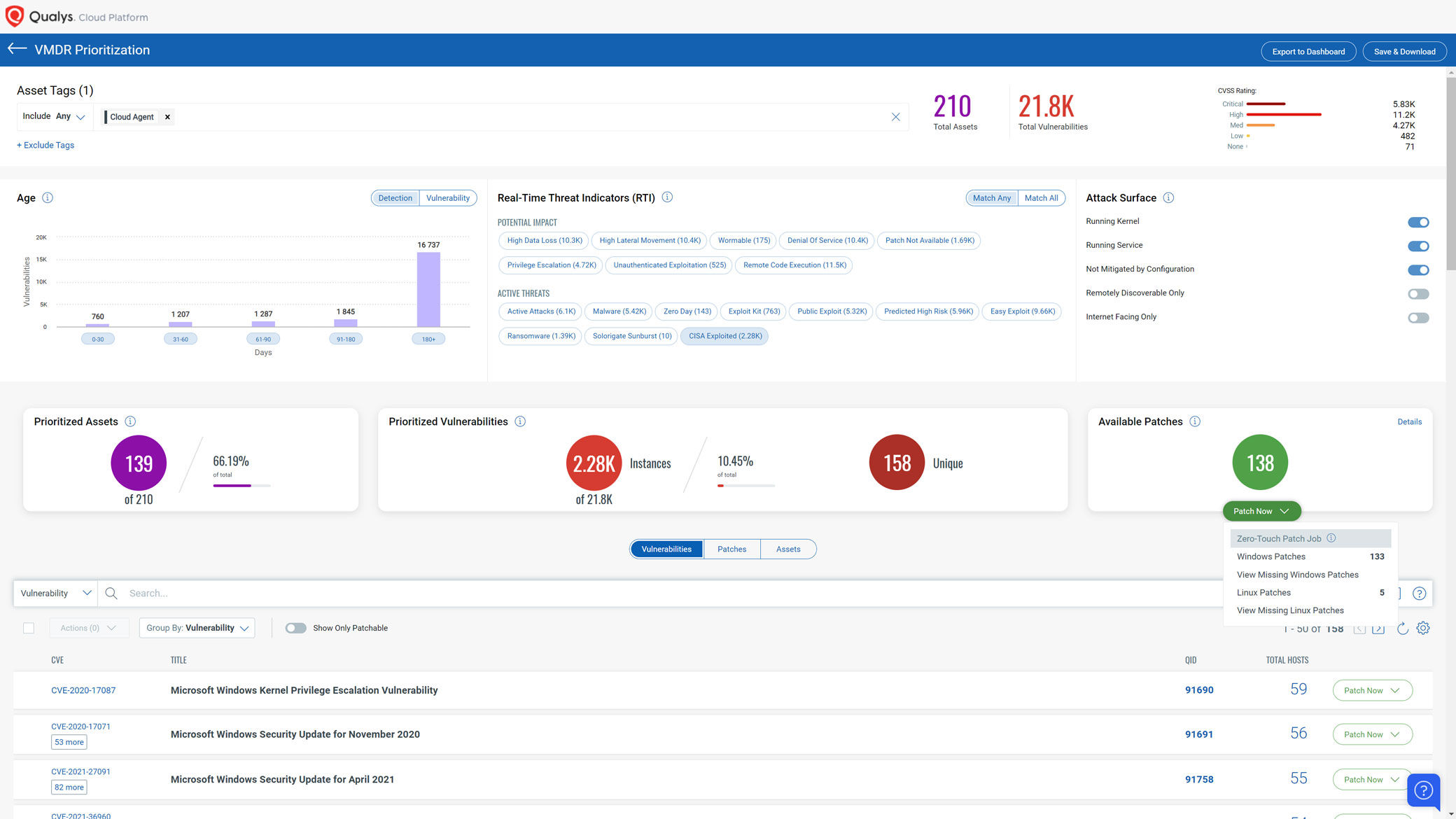
Monitor and ensure your software are always up to date
Immediately know all end-of-support critical components across your environment, including open-source software. Qualys CSAM tracks lifecycle stages and corresponding support status, to help organizations manage their technical debt and to reduce the risk of not receiving security patches from the vendor. Security and IT teams can work together to plan upgrades ahead of time by knowing upcoming end-of-life & end-of-support dates.
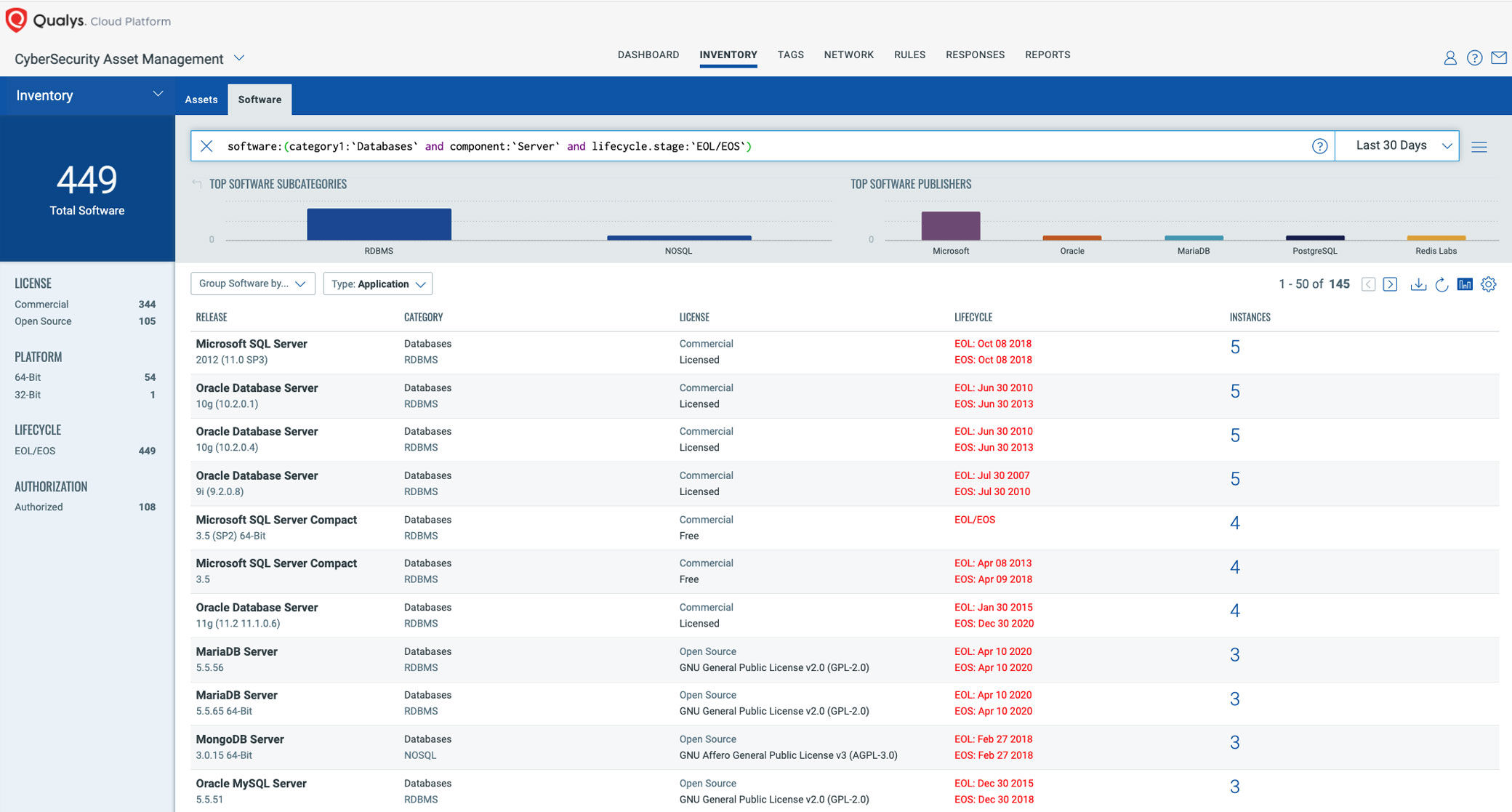
Use the “Prioritize Report” function in Qualys Patch Management to map software in your environment to the security risk opposed. Prioritize your remediation efforts based on software that introduces the most risk. Use this report to create automated patch jobs to ensure that the riskiest software is always up to date. Alternatively, deploy individual patches for the riskiest software.

Step 3: Protect Your Cloud Services and Office 365
As noted by CISA, misconfiguration of cloud services and SaaS applications like Office 365 are the primary attack vector for breaches.
Detect and Remediate Public Cloud Infrastructure Misconfigurations
Protect your public cloud infrastructure by securing the following services on priority:
- IAM: Ensure all users are MFA enabled and rotate all access keys older than 30 days. Verify that all service accounts are valid (i.e. in use) and have the minimum privilege.
- Audit Logs: Turn on access logging for all cloud management events and for critical services (e.g. S3, RDS, etc.)
- Public-facing assets: Validate that the firewall rules for public-facing assets allow only the needed ports. Pay special attention to RDP access. Place any system with an open RDP port behind a firewall and require users to use a VPN to access it through the firewall.
Automatically detect and remediate cloud misconfigurations using Qualys CloudView.
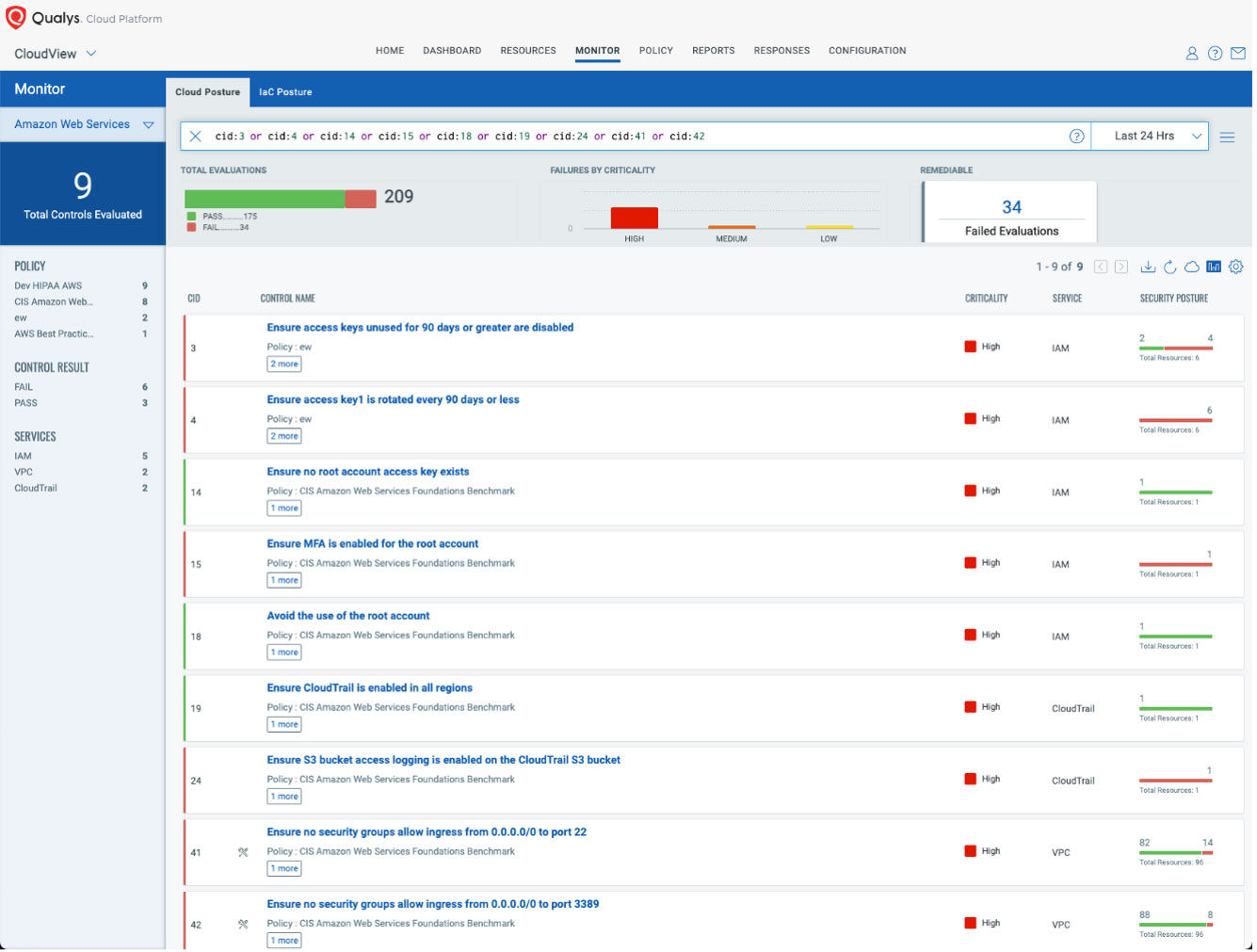
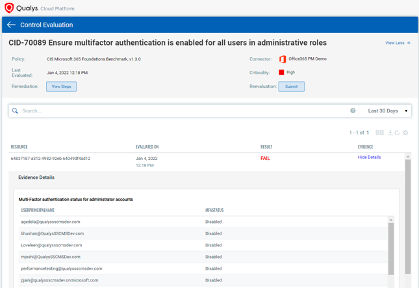
Protect your Office 365 and Other SaaS Services
Enforce multi-factor authentication on all accounts with access to Office 365 tenants. At a minimum, enable MFA for accounts with different admin access rights to the tenant. Qualys SaaSDR lists all such accounts on which MFA is disabled. Further, Qualys SaaSDR enables continuous security posture assessment of Office 365 via the CIS (Center for Internet Security) certified policy for Office, along with automated security configuration assessment for Zoom, Salesforce, and Google Workspace. This is based on an analysis of all security weaknesses, critical vulnerabilities, and exploits leveraged by attackers in historical attacks as well as security assessments based on the MITRE ATT&CK framework.
Step 4: Continuously Detect any Potential Threats and Attacks
Monitor for increases in suspicious and malicious activities as well as anomalous behavior on all endpoints. With Qualys Multi-Vector EDR, customers can detect Indicators of Compromise (IOC) and MITRE ATT&CK Tactics & Techniques provided by CISA and respond quickly to mitigate the risk by capturing process, file, and network events on the endpoint and correlating them with the latest Threat Intelligence, including new and upcoming Indicators of Compromise (IOC) constantly added by the Qualys Research Team. Anomalous endpoint behavior is detected and identified as MITRE ATT&CK Tactics and Techniques.
The Appendix at the bottom of this post contains a list of Indicators of Compromise (IOC) and MITRE ATT&CK Tactics & Techniques being utilized.
Take Action to Learn More about How to Strengthen Your Defenses
We encourage you to learn more about how to strengthen your defenses consistent with CISA Shields Up guidelines using Qualys Cloud Platform. Join our webinar, How to Meet CISA Shields Up Guidelines for Cyberattack Protection, on March 3, 2022.
Qualys recommends that all organizations, regardless of size, heighten their security posture based on the above actionable steps, to protect critical cyber infrastructure from potential state-sponsored, advanced cyberattacks. Qualys Cloud Platform remains continuously committed to high standards of security and compliance to safeguard customer data. In this amplified threat environment, the entire Qualys team is available to help our customers improve cybersecurity and resilience.
Implement CISA’s Shields Up Guidance
Appendix:
CISA catalog of known exploited vulnerabilities by state attackers
| CVE | QID | Title | Release Date | CVSS_V3 |
|---|---|---|---|---|
| CVE-2018-13379 | 43702 | Fortinet Fortigate (FortiOS) System File Leak through Secure Sockets Layer (SSL) Virtual Private Network (VPN) via Specially Crafted Hypertext Transfer Protocol (HTTP) Resource Requests (FG-IR-18-384) | 9/12/2019 | 9.8 |
| CVE-2019-1653 | 13405 | Cisco Small Business RV320 and RV325 Router Multiple Security Vulnerabilities | 1/29/2019 | 7.5 |
| CVE-2019-2725 | 87386 | Oracle WebLogic Server Remote Code Execution Vulnerability (Oracle Security Alert Advisory – CVE-2019-2725) | 4/27/2019 | 9.8 |
| CVE-2019-7609 | 371687 | Kibana Multiple Security Vulnerabilities (ESA-2019-01,ESA-2019-02,ESA-2019-03) | 4/18/2019 | 10 |
| CVE-2019-9670 | 375990 | Zimbra XML External Entity Injection (XXE) Vulnerability | 8/12/2021 | 9.8 |
| CVE-2019-10149 | 50092 | Exim Remote Command Execution Vulnerability | 6/5/2019 | 9.8 |
| CVE-2019-11510 | 38771 | Pulse Connect Secure Multiple Security Vulnerabilities (SA44101) | 8/6/2019 | 10 |
| CVE-2019-19781 | 372305 | Citrix ADC And Citrix Gateway Arbitrary Code Execution Vulnerability(CTX267027) | 12/23/2019 | 9.8 |
| CVE-2020-0688 | 50098 | Microsoft Exchange Server Security Update for February 2020 | 2/12/2020 | 9.8 |
| CVE-2020-4006 | 13215 | VMware Workspace One Access Command Injection Vulnerability (VMSA-2020-0027) | 12/7/2020 | 9.1 |
| CVE-2020-5902 | 38791 | F5 BIG-IP ASM,LTM,APM TMUI Remote Code Execution Vulnerability (K52145254) (unauthenticated check) | 7/5/2020 | 9.8 |
| CVE-2020-14882 | 87431 | Oracle WebLogic Server Multiple Vulnerabilities (CPUOCT2020) | 10/21/2020 | 9.8 |
| CVE-2021-26855, CVE-2021- 26857 CVE-2021-26858, CVE-2021-27065 | 50107 | Microsoft Exchange Server Remote Code Execution Vulnerability (ProxyLogon) | 3/3/2021 | 9.8 |
See the full list of CISA known exploited vulnerabilities.
List of IOCs related to Hermetic Wiper aka KillDisk
| SHA256 Hashes |
|---|
| 0385eeab00e946a302b24a91dea4187c1210597b8e17cd9e2230450f5ece21da |
| 06086c1da4590dcc7f1e10a6be3431e1166286a9e7761f2de9de79d7fda9c397 |
| 095c7fa99dbc1ed7a3422a52cc61044ae4a25f7f5e998cc53de623f49da5da43 |
| 0db5e5b68dc4b8089197de9c1e345056f45c006b7b487f7d8d57b49ae385bad0 |
| 1bc44eef75779e3ca1eefb8ff5a64807dbc942b1e4a2672d77b9f6928d292591 |
| 2c10b2ec0b995b88c27d141d6f7b14d6b8177c52818687e4ff8e6ecf53adf5bf |
| 34ca75a8c190f20b8a7596afeb255f2228cb2467bd210b2637965b61ac7ea907 |
| 3c557727953a8f6b4788984464fb77741b821991acbf5e746aebdd02615b1767 |
| 4dc13bb83a16d4ff9865a51b3e4d24112327c526c1392e14d56f20d6f4eaf382 |
| 7e154d5be14560b8b2c16969effdb8417559758711b05615513d1c84e56be076 |
| 923eb77b3c9e11d6c56052318c119c1a22d11ab71675e6b95d05eeb73d1accd6 |
| 9ef7dbd3da51332a78eff19146d21c82957821e464e8133e9594a07d716d892d |
| a196c6b8ffcb97ffb276d04f354696e2391311db3841ae16c8c9f56f36a38e92 |
| b01e0c6ac0b8bcde145ab7b68cf246deea9402fa7ea3aede7105f7051fe240c1 |
| b60c0c04badc8c5defab653c581d57505b3455817b57ee70af74311fa0b65e22 |
| b6f2e008967c5527337448d768f2332d14b92de22a1279fd4d91000bb3d4a0fd |
| c2d06ad0211c24f36978fe34d25b0018ffc0f22b0c74fd1f915c608bf2cfad15 |
| d4e97a18be820a1a3af639c9bca21c5f85a3f49a37275b37fd012faeffcb7c4a |
| dcbbae5a1c61dbbbb7dcd6dc5dd1eb1169f5329958d38b58c3fd9384081c9b78 |
| e5f3ef69a534260e899a36cec459440dc572388defd8f1d98760d31c700f42d5 |
| f50ee030224bf617ba71d88422c25d7e489571bc1aba9e65dc122a45122c9321 |
| fd7eacc2f87aceac865b0aa97a50503d44b799f27737e009f91f3c281233c17d |
List of MITRE ATT&CK TIDs provided by CISA
| Tactic | Technique | Procedure |
| Reconnaissance [TA0043] | Active Scanning: Vulnerability Scanning [T1595.002] | |
| Russian state-sponsored APT actors have performed large-scale scans in an attempt to find vulnerable servers. | ||
| Phishing for Information [T1598] | Russian state-sponsored APT actors have conducted spearphishing campaigns to gain credentials of target networks. | |
| Resource Development [TA0042] | Develop Capabilities: Malware [T1587.001] | Russian state-sponsored APT actors have developed and deployed malware, including ICS-focused destructive malware. |
| Initial Access [TA0001] | Exploit Public Facing Applications [T1190] | Russian state-sponsored APT actors use publicly known vulnerabilities, as well as zero-days, in internet-facing systems to gain access to networks. |
| Supply Chain Compromise: Compromise Software Supply Chain [T1195.002] | Russian state-sponsored APT actors have gained initial access to victim organizations by compromising trusted third-party software. Notable incidents include M.E.Doc accounting software and SolarWinds Orion. | |
| Execution [TA0002] | Command and Scripting Interpreter: PowerShell [T1059.003] and Windows Command Shell [T1059.003] | Russian state-sponsored APT actors have used cmd.exe to execute commands on remote machines. They have also used PowerShell to create new tasks on remote machines, identify configuration settings, exfiltrate data, and to execute other commands. |
| Persistence [TA0003] | Valid Accounts [T1078] | Russian state-sponsored APT actors have used credentials of existing accounts to maintain persistent, long-term access to compromised networks. |
| Credential Access [TA0006] | Brute Force: Password Guessing [T1110.001] and Password Spraying [T1110.003] | Russian state-sponsored APT actors have conducted brute-force password guessing and password spraying campaigns. |
| OS Credential Dumping: NTDS [T1003.003] | Russian state-sponsored APT actors have exfiltrated credentials and exported copies of the Active Directory database ntds.dit. | |
| Steal or Forge Kerberos Tickets: Kerberoasting [T1558.003] | Russian state-sponsored APT actors have performed “Kerberoasting,” whereby they obtained the Ticket Granting Service (TGS) Tickets for Active Directory Service Principal Names (SPN) for offline cracking. | |
| Credentials from Password Stores [T1555] | Russian state-sponsored APT actors have used previously compromised account credentials to attempt to access Group Managed Service Account (gMSA) passwords. | |
| Exploitation for Credential Access [T1212] | Russian state-sponsored APT actors have exploited Windows Netlogon vulnerability CVE-2020-1472 to obtain access to Windows Active Directory servers. | |
| Unsecured Credentials: Private Keys [T1552.004] | Russian state-sponsored APT actors have obtained private encryption keys from the Active Directory Federation Services (ADFS) container to decrypt corresponding SAML signing certificates. | |
| Command and Control [TA0011] | Proxy: Multi-hop Proxy [T1090.003] | Russian state-sponsored APT actors have used virtual private servers (VPSs) to route traffic to targets. The actors often use VPSs with IP addresses in the home country of the victim to hide activity among legitimate user traffic. |