Forta GoAnywhere Zero-Day Exploited By Threat Actors
On February 1st, 2023, Forta released an advisory behind an auth wall notifying their customers of a remote code execution zero-day exploit affecting their GoAnywhere Managed File Transfer (MFT) application.
This was picked up by Brian Krebs, an investigative journalist who published this on his Mastodon account, on February 2nd, 2023.
On February 7th, 2023, Forta released GoAnywhere MFT version 7.1.2 to fix this vulnerability. The CVE assigned to this zero-day vulnerability is CVE-2023-0669.
About Forta GoAnywhere
GoAnywhere MFT is a secure managed file transfer solution that provides smooth data sharing between systems, employees, clients, and business partners. It helps process information from files into XML, EDI, CSV, and JSON databases and offers centralized control with a wide range of security settings and complete audit trails. Deployable on-premises, cloud, and hybrid environments, GoAnywhere MFT, encrypts data following industry standard protocols; for example, HTPPS, OpenPGP, and STFP.
Vulnerability Details
CVE-2023-0669 is a remote code execution vulnerability caused due to improper sanitization of serialized data. In order to exploit this vulnerability, the attacker needs to have access to the administrative console. This administrative control is typically accessible only from within a private company network, through VPN, or by allow-listed IP addresses (when running in cloud environments, such as Azure or AWS). However, Shodan shows many of such instances are exposed to the internet. The Web Client interface, which is usually accessible from the public internet, is not vulnerable to this security flaw.
Qualys QID Coverage
Qualys released the following QID in the table below to address this vulnerability
| QID | Title | VulnSigs Version |
|---|---|---|
| 730720 | GoAnywhere Managed File Transfer (MFT) Remote Code Execution (RCE) Vulnerability | VULNSIGS-2.5. 695-2 |
WorkAround
The following workaround can be applied by users who are unable to upgrade to patched versions.
- Disable the LicenseResponseServlet:
- On the file system where GoAnywhere MFT is installed, edit the file [install_dir]/adminroot/WEB-INF/web.xml
- In the screenshot below, locate and delete (or comment out) the following servlet and servlet-mapping configuration.
Before:
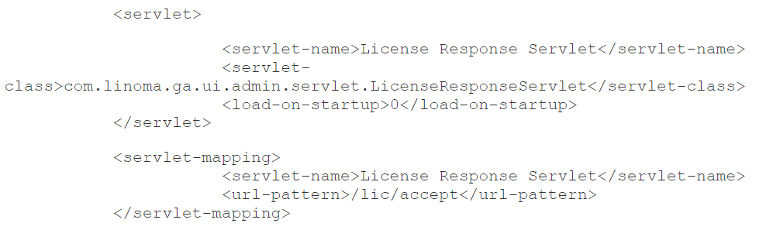
After:
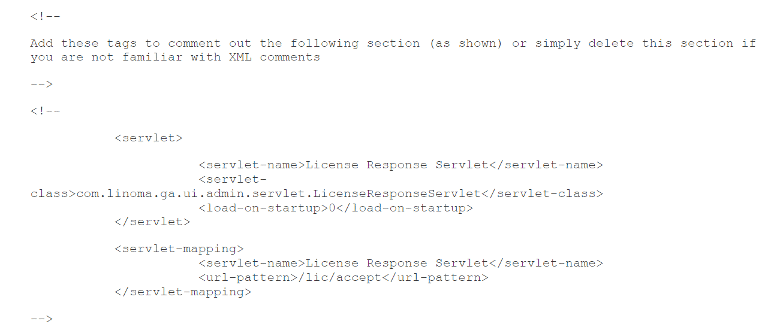
- Restart the GoAnywhere MFT application.
- Reduce unauthorized access to your GoAnywhere MFT management interface using network access controls like firewalls.
Detection of Exploitation Attempts via Qualys Multi-Vector EDR:
Based on multiple threat intelligence sources, adversaries exploiting this vulnerability use Truebot-styled persistence via Scheduled Tasks to achieve coded execution via Rundll32. Qualys Multi-Vector EDR customers keep a lookout for events like the following graphic:
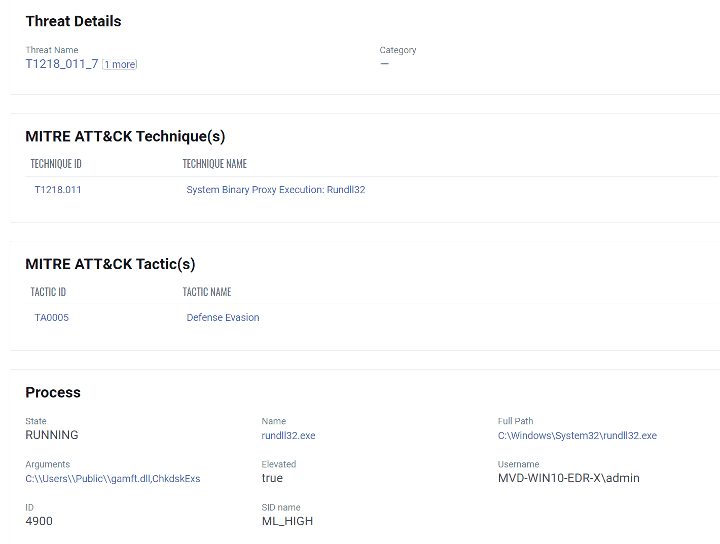
Additional QQL tokens for identifying malicious activity related to this attack:
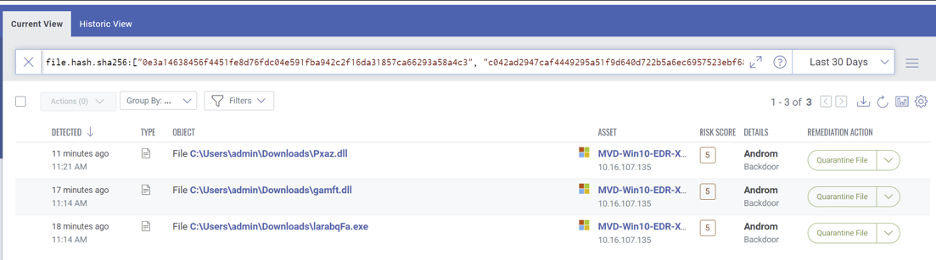
- file.hash.sha256:[“0e3a14638456f4451fe8d76fdc04e591fba942c2f16da31857ca66293a58a4c3”, “c042ad2947caf4449295a51f9d640d722b5a6ec6957523ebf68cddb87ef3545c”, “c9b874d54c18e895face055eeb6faa2da7965a336d70303d0bd6047bec27a29d”]
- file.properties.certificate.issuer:”Sectigo Public Code Signing CA R36″ and file.properties.certificate.hash:”82d224323efa65060b641f51fadfef02″
Events tagged with these IOCs can be seen as follows:
Post-Exploitation IOCs Associated with CVE-2023-0669
- 0e3a14638456f4451fe8d76fdc04e591fba942c2f16da31857ca66293a58a4c3
- c042ad2947caf4449295a51f9d640d722b5a6ec6957523ebf68cddb87ef3545c
- C9b874d54c18e895face055eeb6faa2da7965a336d70303d0bd6047bec27a29d