Risk Fact #1: Cloud Migration Exploitation Cloud Security Research Risk Fact
Qualys Blog Series – 2023 TotalCloud Security Insights by the Threat Research Unit
The 2023 TotalCloud Security Insights report from the Qualys Threat Research Unit (TRU) provides research insights, best practices, and detailed recommendations organized by five separate Risk Facts. The insights will enable organizations using cloud technologies to better understand these risks and how they can be prepared to face those challenges in today’s threat landscape.
In this blog, we look at Risk Fact #1 – Cloud misconfigurations enable exploitation by attackers.
Cloud Misconfiguration Is the Most Critical Issue for Security
As stated in the above title, Cloud Misconfiguration is a critical issue for securing cloud environments. Configurations refer to control settings applied to both hardware and software elements within a cloud environment, allowing them to interoperate and communicate. Misconfigurations amplify the risk of data breaches and unauthorized access due to many factors. They can be:
- The complexity of cloud environments
- Lack of expertise in keeping up with evolving technologies
- Insecure settings and permissions caused by human errors
- Rapid deployment compromising security implementation measures
- Lack of control and visibility of cloud-resident unencrypted or sensitive data due to the dynamic nature of cloud environments
Failure to control these security “cracks” can quickly open a cloud environment while exposing sensitive data and resources to attackers. The following analysis presents cloud misconfiguration issues discovered in the three major Cloud Security Providers (CSPs):
Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP).
Misconfigurations across All Clouds
Encryption
Encryption is essential for protecting your organization’s data, but not configuring it properly will mean that your data is still unprotected. Most CSPs offer encryption at zero additional cost. Enabling it is usually as simple as selecting a checkbox in the configuration settings. Despite the simplicity, this essential control is not universally implemented.
Within Azure, 99% of the disks are either not encrypted or are not using a Customer-Managed Key (CMK); with CMKs, 85% of the keys are not rotated. The same level of risk affects GCP environments where an alarming 97.5% of virtual machine disks for critical VMs lack encryption using Customer-Supplied Encryption Keys (CSEKs).
Identity and Access Management
Like encryption, Identity and Access Management (IAM) is a critical security control, ensuring that users are authorized and only have access to the required resources. Poor implementation levels of IAM occur in all three major providers.
For example, multifactor authentication (MFA) in AWS is not enabled for 44% of IAM users with console passwords. IAM Access Analyzer is not enabled in 96% of the accounts scanned by Qualys. In Azure, scans for enabling authentication and configuring client certificates within Azure App Service fail 97% of the time.
External-Facing
All external-facing assets are exposed to attackers unless appropriate controls are implemented correctly. A common misconfiguration by users of all major cloud providers is inadvertently leaving data publicly accessible. Poorly protecting external-facing assets can have a cascading impact on the effectiveness of other cloud services.
Unfortunately, the convenience of working on cloud assets from anywhere without using a VPN suddenly transforms into a potential breach just waiting to happen. For example, 31% of S3 buckets are publicly accessible, exposing them to different potential security vulnerabilities and subsequent attacks.
Public S3 buckets expose more than sensitive data; they may endanger many services. For example, EC2 instances and RDS databases may be compromised if their access keys, credentials, or backup files are stored in an insecure S3 bucket. The misconfiguration of leaving public network access enabled was seen in 75% of the Azure databases.
Planning Remediation Processes with CIS and MITRE ATT&CK
As your organization explores ways to improve the remediation of cloud vulnerabilities with automation, we urge you to consider work by the Center for Internet Security (CIS) and its new process of mapping individual controls across its benchmarks to the MITRE ATT&CK tactics and techniques. Qualys contributed to developing these CIS benchmarks for AWS, Azure, and GCP. The benchmarks will help offer some valuable insight and context for defenders to better prioritize the hundreds of hardening controls available in cloud environments.
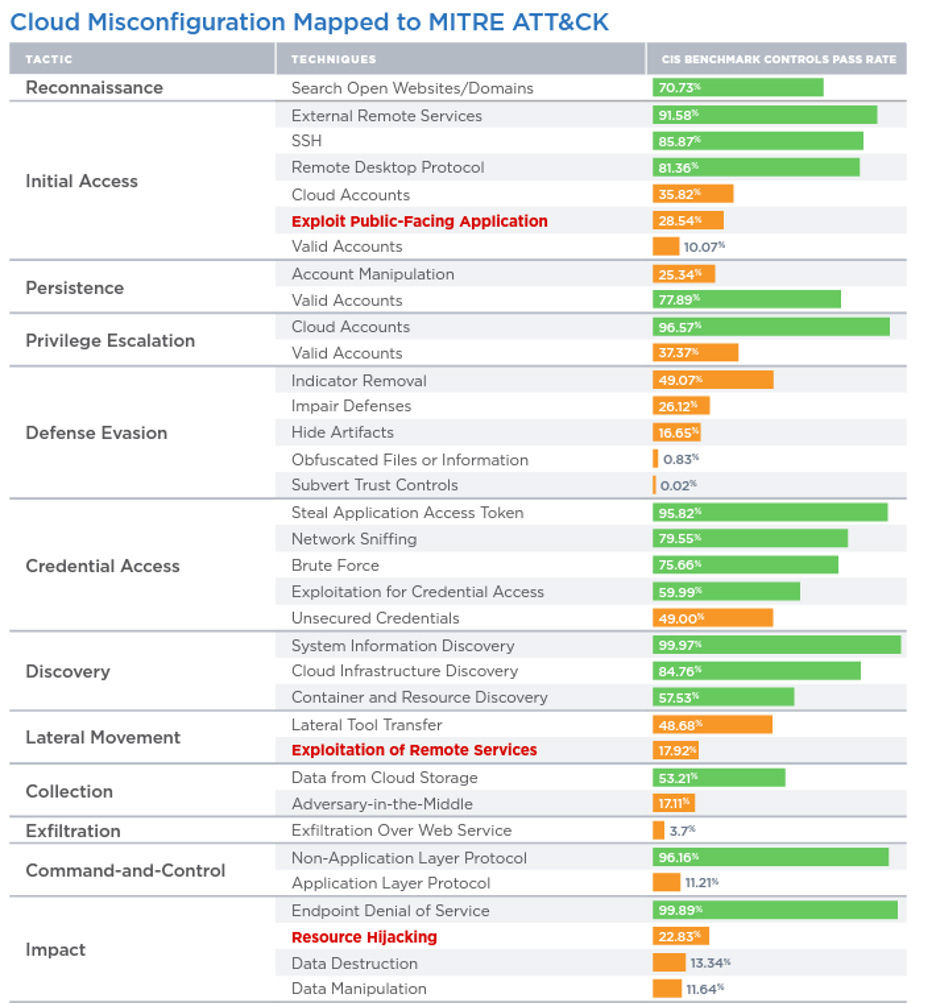
Table 1: Cloud Misconfiguration Pass Rates Mapped to MITRE ATT&CK
From a tactics-hardening perspective, Privilege Escalation (96.03%), Initial Access (84.97%), and Discovery (84.97%) are passing at the highest rates. This shows efforts by organizations to prevent an attack during the earlier stages of the attack chain before progressing to more dangerous tactics such as Impact, which is passing at only 13.67%, or Exfiltration, which passes at just 3.70%.
Deep-diving into it, we see T1190: Exploit Public Facing Application (28.54%) and T1210: Exploitation of Remote Services (17.92%) are failing at high rates. Organizations are relying on other compensating controls, such as applying patches against weaponized vulnerabilities, at a higher rate than for non-weaponized vulnerabilities. Elevated risk is indicated by T1496: Resource Hijacking, which is passing at just 22.83%. Since crypto mining malware is a significant threat to cloud environments, organizations should consider mitigating such controls to reduce their organizational risk in the cloud.
Insights from Risk Fact 1
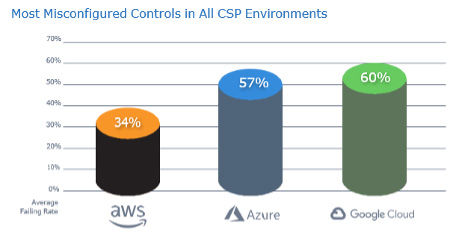
The lesson from these data points is that almost every organization needs to better monitor cloud configurations. Scans for Center for Internet Study (CIS) controls – the gold standard for hardening configurations in CSP environments – fail 34% of the time for Amazon Web Services, 57% for Microsoft Azure, and 60% for Google Cloud Platform. Even if you believe your cloud configurations are in order, the data tells us that not regularly confirming status is a risky bet. Scan the configurations often and make sure the settings are correct. It takes just one slip-up to accidentally open your organization’s cloud to attackers.
To learn more about the five cloud security Risk Facts and detailed recommendations, download your copy of Qualys 2023 TotalCloud Security Insights.
Read the next blog in this series: Weaponized vulnerabilities cloud security research risk fact.
Get the full Qualys 2023 TotalCloud Security Insights and learn about all five Cloud Risk Facts now.