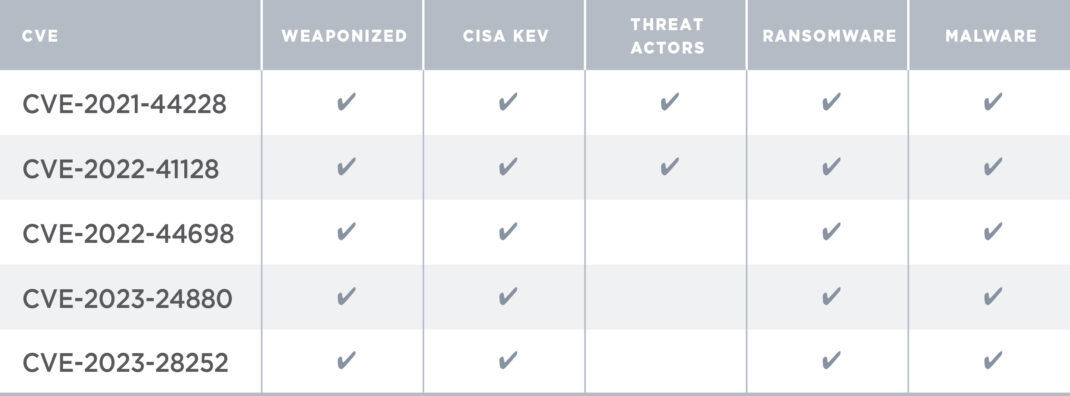
Risk Fact #2: Weaponized Vulnerabilities Cloud Security Research Risk Fact
Qualys Blog Series – 2023 TotalCloud Security Insights by the Threat Research Unit
The 2023 TotalCloud Security Insights report from the Qualys Threat Research Unit (TRU) provides research insights, best practices, and detailed recommendations organized by five separate Risk Facts. The insights will enable organizations using cloud technologies to better understand these risks and how they can be better prepared to face those challenges in today’s threat landscape.
This blog post explores Risk Fact #2 – Weaponized Vulnerabilities Cloud Security Research Risk Fact.
Read the previous blog post from this series: Cloud Migration Exploitation Cloud Security Research Risk Fact.
Vulnerability Analysis of External-Facing Assets
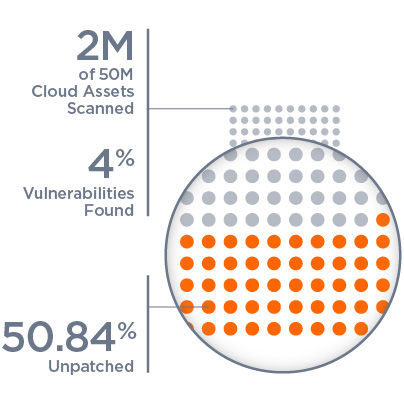
One of the most alarming discoveries within the data was how many cloud assets are externally facing and exposed to the internet. Approximately 4% of cloud assets within the more than 50 million scanned are external facing, which means they have public IP addresses and are visible to any attacker.
While 4% is not alarming, any number greater than zero should be because of cybersecurity concerns. This risk is the equivalent of knowing that petty thieves are prowling your neighborhood and seeking open car doors and unlocked windows — any of which can lead to damage if not addressed.
Having cloud assets with public IP addresses allows attackers to scan your IP space for vulnerabilities and perform other reconnaissance activities that encourage them to actively target your organization’s infrastructure. This risk is compounded when considering the types of vulnerabilities and misconfigurations that are present in your environment.
For example, Log4Shell — an external-facing vulnerability — became a significant threat because it was easy to exploit. Today, patches exist for Log4Shell and its known secondary vulnerabilities. But Log4Shell is still woefully under remediated, with 68.44% of detections being unpatched on external-facing cloud assets.
Covering Risks on Platform-as-a-Service
So far, we have focused on the vulnerabilities associated with computing assets that are publicly facing. However, it is essential to recognize that similar concerns extend to publicly accessible Platform-as-a-Service (PaaS). These services, such as Azure Database for MySQL, Postgres, and MariaDB, have gained popularity for their ability to handle extensive and continuously updated volumes of data. Yet, it has been observed that misconfigurations in such services can expose organizations to significant security threats.
One prevalent misconfiguration involves leaving public network access enabled on PaaS databases hosted on platforms like Azure. While this feature enables remote connectivity, it also opens the door to potential attackers. With public network access enabled, unauthorized users could attempt to gain access to the databases, leading to data breaches, denial of service attacks, and injection attacks.
The 2022 Cost of Data Breach Report findings further emphasize the implications of such misconfigurations, which revealed a concerning trend. The average data breach cost has continued to rise globally, reaching a staggering $4.4 million — an increase of 13% since 2020.
In the United States, the financial toll is even higher, with an average cost of $9.4 million per data breach.
Insights from Risk Fact 2
The vulnerability analysis of external-facing assets has highlighted several critical lessons for organizations to enhance their cybersecurity measures.
Firstly, adopting a proactive security approach is essential, involving regular scanning and patching of vulnerabilities to minimize the risk of potential attacks. Secondly, addressing misconfigurations in publicly accessible PaaS services, like disabling unnecessary public network access, is vital for reducing the attack surface and protecting sensitive data.
Effective patch management remains a top priority, given the high percentage of unpatched vulnerabilities. Continuous monitoring, adherence to industry best practices, and compliance standards are crucial for maintaining a secure infrastructure.
To learn more about the Five Cloud Security Risk Facts and detailed recommendations, download your copy of Qualys 2023 TotalCloud Security Insights.
Read the next blog in this series: External-Facing Vulnerabilities Cloud Security Research Risk Fact
Get the full Qualys 2023 TotalCloud Security Insights and learn about all five Cloud Risk Facts now.