2023 Threat Landscape Year in Review: If Everything Is Critical, Nothing Is
As 2023 nears its end, it’s time to pause and reflect. It’s time to assess what worked and what didn’t, what caught our attention and caused disruption, and what went unnoticed. More importantly, we need to know what lessons we learned from 2023 so that we can do a better job of managing risk in the coming year. In line with this, the Qualys Threat Research Unit has prepared a comprehensive blog series to review the threat landscape in 2023.
Key Takeaways:
- Less than one percent of vulnerabilities contributed to the highest risk and were routinely exploited in the wild.
- 97 high-risk vulnerabilities, likely to be exploited, were not part of the CISA Known Exploited Vulnerabilities (KEV) catalog.
- 25 percent of these security vulnerabilities were immediately targeted for exploitation, with the exploit being published on the same day as the vulnerability itself was publicly disclosed.
- 1/3 of high-risk vulnerabilities impacted network devices and web applications.
- Exploitation of remote services, exploitation of public-facing applications, and exploitation for privilege escalation are the top three MITRE ATT&CK tactics.
2023 Statistics
As of this writing, 26,447 vulnerabilities were disclosed in 2023, eclipsing the total number of vulnerabilities disclosed in 2022 by over 1,500 CVEs. This continues the years-long trajectory of more vulnerabilities being found than the year before.
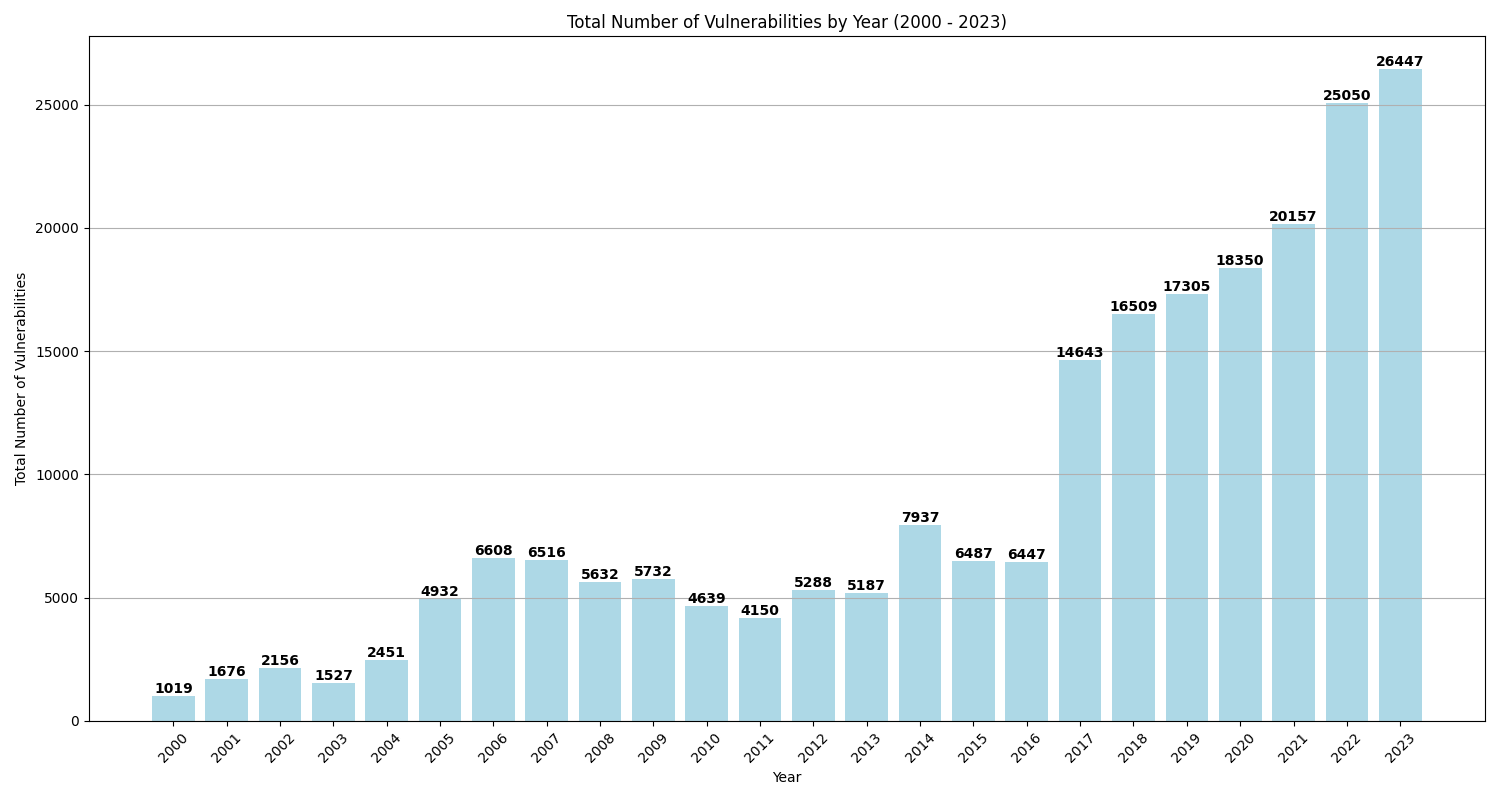
However, not all vulnerabilities present a high risk; in fact, a small subset (less than 1%) contributes the highest risk. These particularly critical vulnerabilities are ones that have a weaponized exploit, are actively exploited by ransomware, threat actors, and malware, or have confirmed evidence of exploitation in the wild. It is these vulnerabilities that we will examine in detail.
2023 Vulnerability Threat Landscape
Let’s take a deeper look into the breakdown of 2023’s vulnerabilities.

The Qualys Threat Research Unit (TRU) analyzed the high-risk vulnerabilities to get more insights and discuss common trends. The TRU inspected which were most exploited, what attack methods and tactics were used, and what strategies we can use to fortify defenses against them. Some highlights of their findings:
- Over 7,000 vulnerabilities had proof-of-concept exploit code. These vulnerabilities could result in successful exploitation; however, the exploit code is typically of lower quality, which may reduce the likelihood of a successful attack.
- 206 vulnerabilities had weaponized exploit code available. Exploits for these vulnerabilities are highly likely to compromise the target system if used.
- There were 115 vulnerabilities routinely exploited by threat actors, malware, and ransomware groups such as CL0P.
- Of the vulnerabilities observed, 109 had known evidence of exploitation and were listed in the CISA KEV.
- 97 vulnerabilities were exploited in the wild but were not included in the CISA KEV list. Note: Vulnerabilities added to the CISA KEV catalog adhere to the criteria established in BOD 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities. Organizations that prioritize vulnerabilities only based on the CISA KEV may want to consider these CVEs as well.
- Ransomware groups such as LockBit and Cerber exploited 20 vulnerabilities.
- Additionally, 15 vulnerabilities were exploited by malware and botnet groups.
Top Vulnerability Types
More than a third of the high-risk vulnerabilities identified could be exploited remotely. The five most prevalent types of vulnerabilities comprised over 70 percent of the total discovered. This underscores the critical need for a comprehensive vulnerability management strategy that includes remote scanning capabilities, not solely relying on agent-based methods.

Key Insights
Mean Time To Exploit High-Risk Vulnerabilities in 2023
In 2023, we witnessed a critical trend in exploiting high-risk vulnerabilities. Our analysis reveals a startling insight into how quickly attackers capitalize on these vulnerabilities.
The mean time to exploit vulnerabilities in 2023 stands at 44 days (about one-and-a-half months).

However, this average masks the urgency of the situation. In numerous instances, vulnerabilities had exploit available on the very day they were published. This immediate action represents a shift in the modus operandi of attackers, highlighting their growing efficiency and the ever-decreasing window for response by defenders.
Let’s take a closer look at the data between zero to 25 days.
Twenty-five Percent of High-Risk CVEs Exploited on the Day of Publication: A staggering 25 percent of these security vulnerabilities were immediately targeted for exploitation, with the exploit published on the same day the vulnerability itself was publicly disclosed. This statistic serves as a wake-up call for organizations to adopt a proactive stance toward patch management and threat intelligence.

Three-Week Window: The data further shows that 75 percent of vulnerabilities were exploited within 19 days (approximately three weeks) of publication. This timeline offers a crucial window for organizations to prioritize and address the most critical vulnerabilities.
One-Third of High-Risk Vulnerabilities Found in Network Infrastructure & Web Applications
A substantial 32.5% of the 206 identified vulnerabilities reside within the networking infrastructure or web application domains—sectors traditionally difficult to safeguard through conventional means.
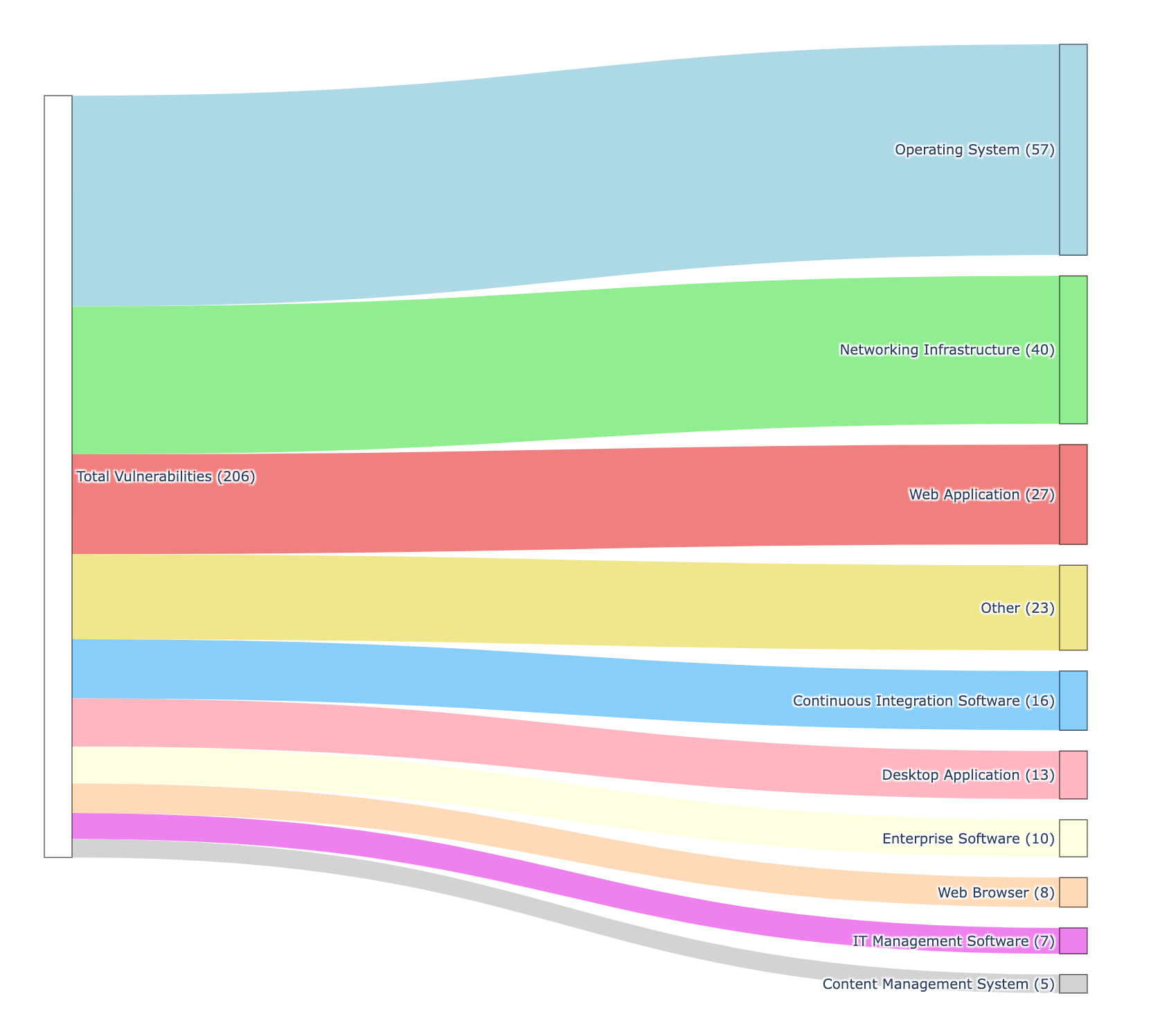
This highlights the necessity of a comprehensive vulnerability management strategy. By deploying a variety of vulnerability management methods, including agent-based, agent-less, and network-based techniques, organizations can ensure extensive and proactive protection across all IT assets. Such a multi-pronged strategy is essential for effectively detecting and remediating threats, thereby bolstering security and compliance in areas particularly susceptible to sophisticated cyber risks. Qualys broadens the scope of protection by encompassing agent support as well as network, external, and passive scanning capabilities, granting organizations a detailed and diverse view of their security posture.
More Than 50 Percent of High-Risk Vulnerabilities Exploited by Threat Actors & Ransomware Groups
Of the 206 high-risk vulnerabilities we tracked, more than 50 percent were leveraged by threat actors, ransomware, or malware to compromise systems.
- 115 exploited by named threat actors.
- 20 exploited by ransomware.
- 15 exploited by malware and botnets.
The vulnerabilities identified span an extensive set of systems and applications, including, but not limited to, PaperCut NG, MOVEit Transfer, various Windows operating systems, Google Chrome, Atlassian Confluence, and Apache ActiveMQ. This breadth showcases that no application is beyond the reach of attackers, who are determined to exploit any vulnerability to compromise systems.
Notably, many of these vulnerabilities, such as those found in MOVEit Transfer, Windows SmartScreen, and Google Chrome, are exploitable remotely, obviating the need for physical access to the targeted system.
Certain vulnerabilities permit attackers to circumvent authentication mechanisms, as observed with the vulnerabilities in PaperCut NG, or to escalate their privileges, such as with the Windows Common Log File System Driver vulnerabilities. These types of vulnerabilities are particularly alarming due to their potential to grant attackers higher levels of access, thereby simplifying system compromise and data exfiltration efforts.
Moreover, vulnerabilities found in platforms like Fortra GoAnywhere MFT and Apache ActiveMQ are capable of facilitating remote code execution or command injection. These allow attackers to run arbitrary commands, which could lead to full system control.
Cybersecurity threats, often targeting specific software versions as seen in MOVEit Transfer, require a dynamic and comprehensive strategy. This includes regular updates, patches, vulnerability assessments, and robust authentication. Proactive and preventive measures are crucial for effective defense against these evolving and complex threats rather than merely reactive responses.
Top MITRE ATT&CK Tactics & Techniques
In 2023, all 206 vulnerabilities in our dataset were weaponized, offering a stark view into the tactics employed by cyber adversaries. Here, we look at the top MITRE ATT&CK techniques and methods used in these exploits, shedding light on the most prevalent avenues of cyberattacks:
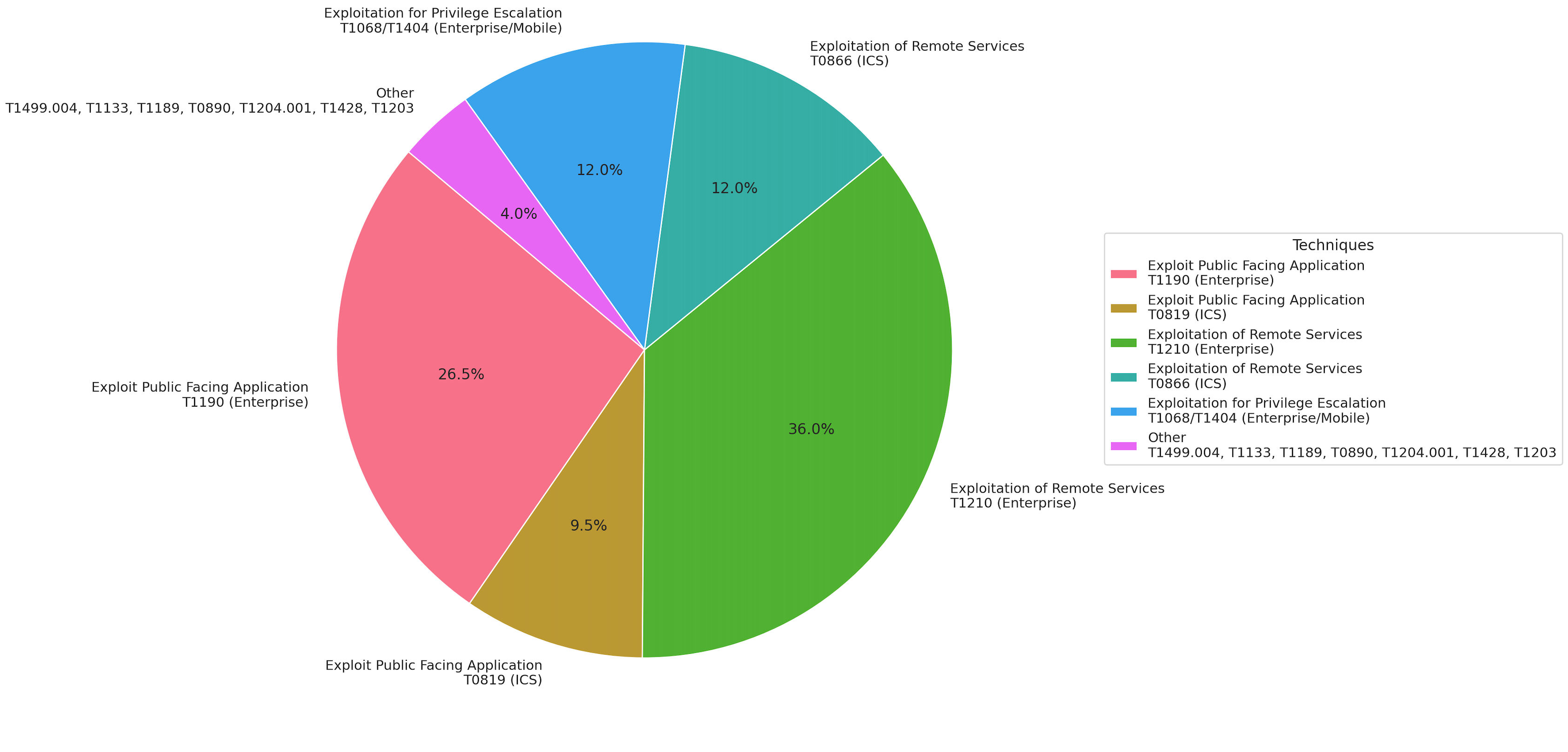
- Exploitation of Remote Services (T1210 & T0866): This is the most frequently observed method, with 72 occurrences in enterprise environments and 24 in industrial control systems (ICS). This technique, utilized for initial access and lateral movement, highlights the importance of securing remote service protocols against unauthorized access and exploitation.
- Exploitation of Public-Facing Applications (T1190 & T0819): Occurring 53 times in enterprise domains and 19 times in ICS, this technique targets applications accessible from the internet. It’s a favored initial access route for attackers, showcasing the critical need for robust external-facing application security.
- Exploitation for Privilege Escalation (T1068): Noted 20 times, this technique involves attackers exploiting vulnerabilities to gain higher privileges within a system. Its occurrence underlines the need for effective privilege management and monitoring within enterprise networks.
In addition to the dominant methods, 2023 also saw other tactics contributing to the diverse threat matrix, like:
- Exploitation for Client Execution (T1203)
- Privilege Escalation in Mobile (T1404)
- Application/System Exploitation (T1499.004)
- External Remote Services (T1133)
- Drive-by Compromise (T1189)
- Privilege Escalation in ICS (T0890)
- Malicious Link (T1204.001)
- Remote Services Exploitation in Mobile (T1428)
Each of these techniques represents a distinct challenge in cybersecurity, offering insights into the evolving tactics of cyber adversaries. From exploiting public-facing applications to leveraging remote services and executing privilege escalation, these methods paint a picture of a sophisticated and multifaceted threat landscape. Understanding these prevalent attack techniques is crucial for developing more effective defense strategies and reinforcing cybersecurity measures against these prevalent threats.
Most Active Threats
Most Exploited Vulnerabilities
This year, certain vulnerabilities stood out as the most frequently exploited. These include:
CVE-2023-0669, CVE-2023-20887, CVE-2023-22952, CVE-2023-23397, CVE-2023-24880, CVE-2023-27350, CVE-2023-28252, CVE-2023-2868, CVE-2023-29059, CVE-2023-34362
The volume of exploits of these vulnerabilities indicates trending attack vectors and emphasizes the need for targeted defensive strategies.
| CVE | Title | Qualys Vulnerability Score (QVS) |
|---|---|---|
| CVE-2023-0669 | Fortra GoAnywhere Managed File Transfer (MFT) RCE Vulnerability | 95 |
| CVE-2023-20887 | VMware Aria Operations for Networks Command Injection Vulnerability | 95 |
| CVE-2023-22952 | SugarCRM Remote Code Execution (RCE) Vulnerability | 95 |
| CVE-2023-23397 | Microsoft Outlook Elevation of Privilege Vulnerability | 95 |
| CVE-2023-24880 | Windows SmartScreen Security Feature Bypass Vulnerability | 95 |
| CVE-2023-27350 | PaperCut NG/MF Multiple Security Vulnerabilities | 100 |
| CVE-2023-28252 | Windows Common Log File System Driver Elevation of Privilege Vulnerability | 95 |
| CVE-2023-2868 | Barracuda Email Security Gateway Vulnerability | 95 |
| CVE-2023-29059 | 3CX Desktop Client Supply Chain Vulnerability | 95 |
| CVE-2023-34362 | MOVEit Transfer Injection Vulnerability | 100 |
See our blog post for a detailed list of the most exploited vulnerabilities.
Most Active Threat Actors of 2023
In 2023, the cyber landscape was shaken by TA505, also known as the CL0P Ransomware Gang. This group masterminded a high-profile cyberattack by exploiting zero-day vulnerabilities, and they notably exploited zero-day vulnerabilities in key platforms like GoAnywhere MFT, PaperCut, MOVEit, and SysAid. Their sophisticated use of diverse malware types for information gathering and attack facilitation marked them as a significant threat. The severity of their actions prompted advisories from the Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI), highlighting the need for improved cybersecurity measures.
Most Active Malware of 2023
In 2023, LockBit and Clop have been prominent in the ransomware arena. LockBit, using its advanced ransomware-as-a-service model, has targeted a range of organizations, including in the IT and finance sectors. Notably, LockBit exploited vulnerabilities such as CVE-2023-27350 in PaperCut NG and CVE-2023-0699 in Google Chrome, allowing remote attackers to bypass authentication and exploit heap corruption.
Clop, known for exploiting vulnerabilities, has conducted extensive attacks on large enterprises, notably in the finance, IT, and healthcare sectors. Clop’s activities included exploiting CVE-2023-27350, CVE-2023-34362, CVE-2023-0669, and CVE-2023-35036. These vulnerabilities ranged from SQL injection in MOVEit Transfer, allowing database access, to a pre-authentication command injection in GoAnywhere MFT and bypassing authentication in PaperCut NG.
The cybersecurity landscape is evolving, with the proliferation of hacking tools and knowledge allowing less skilled hackers to exploit vulnerabilities once only accessible to highly sophisticated attackers. This broadens the attacker spectrum to include advanced hackers, less experienced malicious cyber actors, and digital activists, marking a significant shift in cyber threat dynamics.
These instances highlight the speed with which vulnerabilities can escalate from publication to weaponized exploit to exploitation and illustrate the immediacy with which cyber threats evolve upon the disclosure of vulnerabilities. This rapid evolution from publication to exploitation and weaponization emphasizes the critical need for organizations to monitor disclosures closely and implement rapid response mechanisms to mitigate potential attacks.
Qualys VMDR with TruRisk streamlines the prioritization of exploited vulnerabilities by providing a clear TruRisk Score (QVS) for each vulnerability. This scoring system, easily understood by technical and non-technical teams, helps identify high-risk issues. Vulnerabilities with a QVS over 90, which TruRisk consistently evaluates, should be prioritized and addressed promptly for effective risk management.
Conclusion
As we conclude our analysis of the threat landscape in 2023, it’s evident that the rapid pace of vulnerability weaponization and the diversity of threat actors pose significant challenges for organizations globally. Here are a few key recommendations to reduce risk:
- To accurately assess the genuine risk presented by open vulnerabilities within their organization, it’s essential that businesses employ a comprehensive set of sensors, ranging from agent to network scanners to external scanners.
- Thoroughly inventory all public-facing applications and remote services to ensure they are not vulnerable to high-risk vulnerabilities.
- Employ a multifaceted approach to the prioritization of vulnerabilities. Focus on those known to be exploited in the wild (start with the CISA KEV), those with a high likelihood of exploitation (indicated by a high EPSS score), and those with weaponized exploit code available.
These recommendations will help reinforce the critical need for a robust, proactive approach to vulnerability and risk management, especially in an increasingly sophisticated and pervasive era of cyber threats.